Day 1: Thoughts and Recon
It was a Friday evening and Flir was in his dorm, sitting at his computer. He set the computer to plan a random collection of Trance music and began to think about how he could gain social security numbers. The dormitory desk guards had a resident roster of students, listing social security numbers , name , sex, and birthdays for the students who actually lived on campus. Flir wasn t that fast a talker “ he didn t think he could convince the desk guards to give him the list. Besides, only 20% of Pacific Tech s students lived on campus “ Flir wanted more than that. He thought about the doors on campus that opened only with a student ID. He might be able to intercept the communications from the door readers to the authorization computer. Since the door s card readers simply sent out the student ID number (social security number), he could intercept these easily, though this would get him far fewer IDs than raiding the dorm s resident roster. Then he remembered where he d seen his student ID number most recently: the computer, when he was viewing his class schedule and his transcript.
Pacific Tech had recently begun allowing students to use the Web to sign up for classes, view their class schedule, apply for graduation, upgrade their meal plan, change their address, pay their tuition, and even view their transcripts. As in many universities and government institutions, this was provided by a custom-built web application on a middleman server. This server functioned primarily as a client to the old mainframes, which still kept the data. Pacific Tech had transitioned much, but not all, of its data from the mainframes to a SQL database, so the web application there actually talked to both the mainframes and a newer UNIX machine running an SQL server.
What Flir had noticed the very first time he used the system was that the Web server used a self-signed certificate.
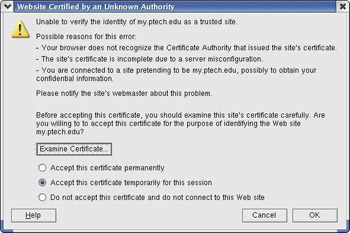
Dialogue in his Mozilla Browser
He clicked the Examine Certificate button to see the details of the certificate.
Someone in Computing Resources was trying to save money in a stupid way. They d created their own web certificate instead of buying one from a known certificate authority. They, like many people, didn t understand how SSL, the technology behind the misnamed secure [web]servers, worked.
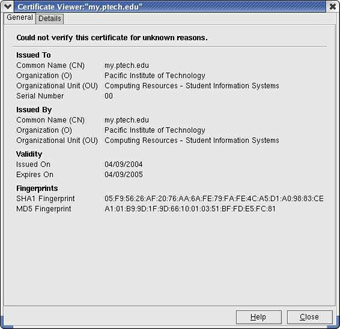
Details of Certificate
Flir was so exasperated by the bad decision that he had to tell someone about it. He got up from his computer and promptly tripped and fell over a Japanese auto disk-brake assembly. His girlfriend, an equally intelligent 19-year old with a thin frame and short black hair hopped over to him. Jordan, he fumed, why do you have to work on your car in here? The parts of a Toyota Prius lay strewn about the room. She had disassembled the car down to small subsystems with some friends and carried it inside.
I m sorry, but I wanted to mod the car and it s too cold to work outside, much too cold. It s really freezing! Your room has much more floor space, Jordan explained at high speed. She, like so many other smart people at Pacific Tech, seemed to always talk fast, as if she was impatient with how fast her mouth could convey her brain s thoughts.
He couldn t pursue the argument. That s only because you keep so much junk in yours, he grumbled, as she helped him back up. I was thinking about the fact that the my Ptech site uses a self-signed certificate.
A what, she asked? Jordan knew her way around a computer, even knew UNIX, but she was a mechanical engineer and didn t delve much into networking issues.
A self-signed certificate. Let me explain.
Self-signed Certificates “ Certifying the Man in the Middle
To prevent an eavesdropper on the network from intercepting, and possibly modifying, a communication between a web browser and a Web server, the browser and server would have to encrypt all of their communications. Normal encryption, called symmetric encryption, involves both parties knowing a shared secret and using it as a key in a known algorithm that turns meaningful message into gobbledygook and then gobbledygook back into meaningful message. Getting a unique shared key for a communication to each party before beginning the communication is logistically difficult. The only way around this is to generate a key at the start of the communication. But that solution creates a pair of problems. First, how do you get that secret key to each party to the communication without eavesdroppers reading it? Second, how does each party know they re sending their communications to the right party?
The popular solution now involves a second kind of encryption, using private-public keypairs. In essence, through some wonderfully simple mathematics, the key used to encrypt the communications comes in two pieces: a public key and a private key. A client who wants to send a communication to the Web server encrypts it with a widely-circulated public key. This public key can t be used to decrypt the communication “ this requires the never-circulated private key. The server uses its private key to decrypt the communication. The entire communication isn t done this way for several reasons, not the least of which is that this asymmetric encryption is too slow.
Instead, the client just sends a freshly-created shared key encrypted with the server s public key. The server uses its private key to decrypt the shared key, which serves as the key for this one session. The server s public key is used only once, just to get the client-created session key safely to the server. Now the problem with this, of course, is that the client s web browser has to either have a public key for every SSL d Web server in existence, or instead, it needs a secure way to get that public key. The former is impossible “ there are new servers going up every day. Instead, another feature of the public-private key encryption can be used: signing.
Suppose you want to sign a message, to certify to the recipient that the message is authentic , you know, actually from you. You can compute the hash of the message (a kind of fingerprint) and then encrypt that fingerprint with your private key. If you attach that to a message, you ve created a kind of signature. If the recipient wants to confirm that the message is both from you and has not been tampered with in transmission, he can decrypt the signature with your public key and check his own hash of the message against the one you encrypted. Since no other party has your private key, only you could have created that hash.
So how does this apply to certificates? Jordan asked.
Well, public keys in SSL land are contained in certificates. Every web browser is populated with the public keys of a number of certificate authorities, which are just companies who make and sign certificates. When you start up a communication with an SSL server, it sends you its public key, its certificate. To confirm that the certificate is authentic, the browser checks the signature using the public key of that appropriate certificate authority, Flir explained.
It s a kludge of a system, but it works. Every Web server can give away its own certificate, so they don t have to be centrally stored. The web browsers only have to ship with 70 or 80 certificate authority public keys and they can just check Web server certificates against them.
So what s so stupid about the myPtech website? Jordan asked.
Basically, they ve created their own certificate, which isn t signed by any pre-populated certificate authority s key. So the students browsers can t authenticate that certificate. And if they can t authenticate it, someone could man-in-the-middle it ! Anybody could just put a computer between the users and the myPtech server, make a certificate that looks just like the one on the myPtech site, and run their own Web server or custom proxy. All they d need was some way of redirecting the traffic to that computer, but that s not tough. Then everyone would send their passwords and data to that computer, not realizing it was the wrong server! I ve got to whiteboard this
He had trailed off, but Jordan had gotten confused by Flir s last explanation. She wasn t sure how you d redirect the traffic away from the real Web server or how the proxy would work. She was pretty sure this was another famous Pacific Tech prank in the making, like the time they d moved someone s car into their dorm room by taking it apart and reassembling it there or the time some MIT students had temporarily changed the last three words of the marble inscription on the inside of the campus s main dome building so the inscription read Established for Advancement and Development of Science and its Application to Industry the Arts Entertainment and Hacking [i] The pranks took extreme planning and Mitch had started scribbling diagrams and sentences onto the whiteboard. She d let him think it all out and help him with the resulting prank if it ever turned into that.
Jordan went back to reassembling the Toyota Prius from parts strewn about the room. Flir had purposefully trailed off, remembering that he wasn t allowed to tell anyone about what he was doing, even Jordan. He d need to be more careful, especially since Jordan now knew that Flir had been thinking about how to attack the vulnerability. If the school realized what had happened and told students, Jordan would probably figure out that Flir had been involved. Then again, if Pacific Tech was like most organizations, the school would never reveal any major compromise to the students, even if the attacker had gotten their personal information. Still, Flir reminded himself to keep quieter about his plans.
As he looked around his room, he was annoyed at the mess, but he knew that Jordan needed that outlet for her energy. Anyway, he was already busy formulating his plan. He needed to sniff traffic from students to the web application without being detected . He didn t even think about setting up the sniffer in the dorm room, because he really didn t want it to be that easy to trace back to him if it was discovered . He could pick the lock on a dorm networking closet, but the dorms were the wrong place for this. He d be changing the network flow patterns for the local network and bringing a whole lot of traffic through his one system. Given the huge amount of bandwidth being used by peer-to-peer music sharing, this could be dangerous. No, the computer lab would be a much better environment. There was virtually no peer-to-peer there, it would be hard to trace back to him, and he d get to sniff traffic from a much larger group of students. Flir stepped over the car s tremendous rechargeable battery pack, nearly tripped onto a 3- foot solar panel, and kissed Jordan goodbye . He left the dorm room to begin his trek to the computer labs.
Computer Lab Recon
Flir walked through the lobby of his dorm, completely oblivious to an attractive coed carrying on a conversation with two boys, while clothed only in a pair of towels. Strangely, no one else seemed to notice that she was dressed any differently than her peers. If Flir wasn t so over-focused, perhaps he d realize that his dorm was fairly extraordinary. In the meantime, he just needed to get to the computer lab.
It was dark outside now, approaching night. The main computer lab wasn t far from the dorms. Flir didn t have much to do tonight “ he was just coming by to recon the lab environment. Hackers spent far more time doing reconnaissance than any movie ever gave them credit for and Flir was no exception. Tonight he just wanted to observe how the labs were set up. He walked in and looked around the lab. Forty-eight computers were set up on six long room-length desks. Flir sat down at one of the many computers. Each was more or less identical. A standard beige box PC sat on top of the table, with a network cable and power cable leading into a grommet on the top. The front of the table obstructed view into the inside, where the power and network cables went. Excellent.
He traced each cable, illuminating the path through the 3-inch wide grommet with an LED flashlight. The power cable was a standard black cable leading to a fully-populated power strip. The network cable was orange “ he d have to remember that “ and led off into the darkness . He rose and walked around the long table, examining the floor. He didn t find the power cables leaving the tables. They must plug into the floor, he thought. He did find that the eight network cables all left the table in a electric tape-bound cluster. The cluster ran, taped-down, along the floor and ended in a closed networking closet. How odd, Flir thought, as he realized that each closet probably contained a single managed switch. Then again, with the University s budgets , it might even be an unmanaged switch or hub. He began to wonder how many labs might be connected to a large switch before they hit the first router. Even the best- funded universities can be extremely thrifty on general computing resources “ Ptech probably wouldn t have any routers separating the labs. He d test that later with standard tools. It would be a simple matter to run a traceroute from a machine in one lab to a machine in another, checking to see if the packet s TTL (time-to-live) was decremented by an intermediary router.
His on-site reconnaissance finished for the night, Flir left the lab to continue his plan. He walked back to his dorm, contemplating the details and wondering if Jordan would be asleep yet. He stopped in the lobby to use a public computer and ran a few quick traceroute commands. He traced the path of routers to two computers in two different labs in the same computing building. As he d hoped, both computers had the same router as their last hop. This meant that only a switch separated the two, not a router, and was very, very good news.
Pacific Tech was saving money on both routing hardware and the staff time required to keep the router configured and patched. Knowing what the school charged non-scholarship students, Flir had once been surprised by how frugal Pacific Tech tended to be. A friend who had transferred from another school had explained that many expensive schools were still fairly frugal with computing services departments. Part of the reason was that better-run computer labs just didn t seem to attract new students the same way that other services might. That department was also, politically speaking, one of the easiest to apply budget cuts to. Few professors on campus would fight the cuts, especially since those whose research depended on computers often bought and staffed their own computer clusters with grant money.
Flir left the lobby and headed to his room. When he arrived at his room, Jordan was cutting a sunroof into the Prius top with a circular saw. Flir couldn t believe the sheer amount of noise that she got away with and plugged in his headphones. Though he d left Physics behind completely after his intense and traumatic freshman year, he d used the theory to create a noise-cancellation patch to xmms, his Linux machine s mp3 player. It read in sound signals from microphones mounted on his headphones and modified the headphone s output sound waves to cancel much of the noise created by Jordan s constant use of power tools.
Flir s headphones cranked out the creations of DJ CMOS, one of his favorites. CMOS had somehow blended 80 s songs into a fast, driving house mix. For some odd reason, Flir had an affinity for 80 s music, as if he d lived much of his life through the era. In truth, it being 2004, Flir was only alive for the last two years of the 80 s. Those two years must have made an impression upon him!
Preparing the Plant “ There s No Offense without a Good Defense
On to the plan. He d need to control a machine in the computer lab to sniff traffic. He could hack one the machines there, but the IT staff might notice that and shut it down. Even if they didn t, many schools re- imaged the lab system s hard drives once per month, week or even day, replacing their contents automatically with a known good operating environment. No, he d need to introduce his own system into the lab.
Flir pulled out one of the new Sony Vaio laptops that Knuth had bought him, which he decided to call Rogue. It had just the qualities he needed. It measured 8 by 10 by 1 and, at 3 pounds , it was light enough to duct tape under a desk if he needed to. He d already installed Linux on it and run Bastille Linux on it to lock it down, hardening the OS and the firewall rules. He sat down to configure it for this particular job.
The system would need to intercept people communicating with the myPtech system. It would need to collect usernames and passwords. Finally, Flir needed to control it remotely “ he should never have to touch the machine again once he d planted it, unless he wanted the hardware back when he was done. He set about to work on his control mechanism.
Flir would ssh into the system over a wireless 802.11b link from his other laptop, which he d call controller. That would allow for stealth and make it much harder to trace the system back to him. He plugged a wireless card into the system and used Linux s iwconfig command to configure the card. First, he set the card to function on channel 3. Few people used channels other than 1,6, and 12, so few, if any, people would find his system addressable.
# iwconfig eth1 channel 3
Next , he wanted to set the card to encrypt all its communications with a wired equivalent privacy (WEP) key. First, Flir had to choose the key. WEP keys were hexadecimal strings, usually 32 characters long. To choose digits somewhat more randomly , he had used a piece of overhead transparency to create an overlay for a Twister spinner. With an overhead pen, he had divided the circle into sixteen pieces, with the digits 0,1,2,3,4,5,6,7,8,9, A, B, C, D, E and F. He spun it 32 times to get: 458E 50DA 1B7A B137 8C32 D68A 5812 9012. He set the card s WEP key to that:
# iwconfig eth1 enc on # iwconfig eth1 key 458E50DA1B7AB1378C32D68A58129012
Finally, he d need to set an ESSID, an ID for the wireless network of two machines that he d use.
# iwconfig eth1 essid lazlosbasement
He set an IP address for the system next of 2.3.2.1 for the wireless link.
# ifconfig eth1 2.3.2.1 netmask 255.0.0.0 up
That number was reserved and wouldn t route on the Internet, but it didn t matter “ this was a network of just two systems, connected by a radio link without any routers in between.
He d control the system over an ssh link. He could write his own remote login program, but this was easier. He modified the ssh daemon s configuration file, sshd_config, though, setting it to only listen to the wireless card and not to theEthernet card:
ListenAddress 2.3.2.1
He also set the ssh daemon to disallow password authentication out of habit, leaving password-protected RSA keys in place instead. Flir hated passwords “ they were almost always the weakest link in computer security, since they could be guessed or brute-forced by a determined attacker. Using an RSA keypair for authentication, encrypted with a passphrase, was much stronger.
Finally, he added three custom rules to the beginning of the iptables firewall:
# iptables I INPUT 1 i eth1 -m mac --mac-source ! AA:BB:DD:EE:55:11 j DROP # iptables I INPUT i eth1 p tcp --dport ssh s 2.3.2.20 j ACCEPT # iptables I INPUT 3 i eth1 j DROP
The first line told the kernel to drop any packets that did not come from a single specific wireless network card. The second line allowed ssh access in from a single IP address. The third line caused the kernel to drop any other packets from the wireless interface.
Flir had now hid his control channel slightly, by using a different channel. He had also placed some nice access control on that channel by forcing all control connections to come from a specific IP address and from a specific network card hardware (MAC) address. Finally, he had encrypted his communications with WEP.
Of course, any other attacker could fake his MAC address, set the particular IP address, and perhaps even crack the WEP key if he was able to observe enough traffic. Flir s actions served to raise the bar, locking out all attackers except for the rare ones with the knowledge and determination to find his wireless network and attack it. He could even keep his WEP key hard to crack if he didn t communicate a great deal with the rogue laptop ” WEP crackers require a healthy number of packets before they can brute force a key.
Even if an attacker cracked the WEP key and discovered the key to the firewall policy, the real authentication step still happened in the ssh daemon. Since Flir was using a private/public keypair instead of a password, the attacker couldn t get access by guessing passwords “ any attacker would have to find a vulnerability in the ssh daemon itself. Since Flir was using privilege separation, it was highly likely that any exploits in the ssh daemon wouldn t even get the attacker Flir s root access - the attacker would have to work hard to escalate privilege to root.
Flir was being very careful. He could add additional measures to this, but he believed he had gone far enough. He had taken multiple measures, remembering what he read about Defense In Depth, but also remembered not to take security so far as to render the machine or network useless. Striking this balance between convenience or usability and security is difficult in any environment. It was especially difficult here, because if someone broke into the laptop, Flir s entire plan could fail.
Flir stopped for a moment to consider that he wasn t just defending his rogue laptop from normal attackers. Ironically, he was also defending it from any Pacific Tech computer security staff! It was bizarre what Agent Knuth had called upon Flir to do for his country.
Now that Flir had prepared the rogue laptop for remote control, he wanted to place it in the lab as soon as possible. Once it was in place, he could configure it to steal passwords. He put it into a sleep mode. With the headphones still on, he packed the laptop and A/C adapter into his backpack , along with two orange network cables, a palm- sized hub, a patch-style directional antenna, a network card, a USB wireless adapter, and a roll of black duct tape. He placed the backpack aside for tonight ”he d go back to the lab tomorrow. In the meantime, he d try to convince Jordan to come to bed.
When Flir removed his headphones and rejoined the world around him, he found Jordan using a drill to screw the solar panel into the sunroof slot she d cut into the Prius roof. She wasn t fitting the panel into a sliding assembly, like on most sunroofs “ she was actually screwing it directly into the car s body. Jordan, it s 1 am . Let s go to sleep!
Her words came out rapid fire, as they always did when Jordan was solving problems out loud. The solar panel will allow me to push the motor much further, much faster! But it leaks. It shouldn t leak! I cut it just right! I put the same rubber around it that all the other sunroofs have. But it leaks! It can t leak. I m going to have to make a sealant and that takes chemicals! I have chemicals
Jordan went on for some time, eventually sitting down to research sealants, designing her own. Later, she d go back to her room and mix chemicals from the supply in her closet. Jordan seemed to take everything way too far. She d built a wine rack in her closet filled with bottles of liquid chemical agents . Adjacent to the rack, a number of boxes sat, filled with chemical solid components . Next to those boxes, wedged against the wall, was her floor-sander, which she used twice a year to clean her dorm room s floors. Flir had first thought the machine was evidence of extreme overkill, but he began to understand the need for such a device as he learned that Jordan s dorm room was more workshop than sleeping area. Jordan almost never slept, though she worked incessantly on these extracurricular engineering projects. Oh well, he thought, most guys would kill for a woman who enjoyed power tools this much.
[i] http://hacks.mit.edu/Hacks/by_year/1994/entertainment_and_hacking/eh.html from the MIT Hack Gallery at http://hacks.mit.edu/Hacks.
EAN: N/A
Pages: 105