Reading Other People s Mail
|
Reading Other People’s Mail
Under some circumstances, it might be necessary for you to grant one user access to another’s mailbox. Of course, users can always allow another to read their mail by granting delegate access, but generally when the messaging administrator gets called in, it’s for one of two reasons: managers suspect a user of doing something wrong, or someone needs access to the mailbox of a user who has left the company, died, or gone on sabbatical to Timbuktu.
There are legal implications of reading other people’s mail; my own personal guideline is that I wouldn’t do so unless I had a written request from a properly authorized officer of the organization, and that I would grant that person access and then leave the area (after all, the last thing I want is to see whatever incriminating mail might be in the mailbox). Besides the potential consequences of learning deep, dark secrets, there’s a more practical consideration: people generally trust administrators not to abuse their powers (even though they can easily do so), because an untrustworthy administrator can do a great deal of damage. You have a responsibility to uphold that trust, and to do whatever you can to prevent unauthorized access, including not granting it carelessly to anyone who asks.
Using Message Journaling
Exchange 2000 has the ability to journal messages, or copy them to a location you specify. This is useful for archiving and retention, but it’s also useful for monitoring e-mail. Journaling applies to an entire mailbox database; once you turn it on for that database, all messages sent or received by mailboxes in that database are copied to the journaling location you specify. Of course, this presents a couple of challenges. First, be selective. If you don’t need to capture mail for many users (for example, if you’re just targeting a user or two for monitoring), put them in a separate mailbox database, then enable journaling on the new database. In fact, you can create a database just for journaling and move mailboxes into and out of it as your monitoring requirements change, and when no one’s being monitored you can dismount the database altogether. Second, ensure that the destination location, which can be a mailbox or a public folder, can keep up with the volume of mail you’ll be generating.
Enabling and using journaling is extremely simple: the only thing you have to do is select the Archive All Messages Sent Or Received By Mailboxes On This Store check box, then click Browse and select the mailbox or public folder that should receive the journaled messages (see Figure 9-1). Once you’ve made this small change, you’ll immediately see journaled messages begin to appear in the selected folder. Because these messages are copies of the original, you can modify or delete them without affecting the original users’ copies.
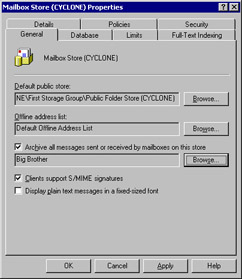
Figure 9-1: Turning on journaling allows you to see copies of all messages sent from or to mailboxes in the specified message store.
Granting Permission to Other Mailboxes
Sometimes journaling isn’t the right solution. Because it only grants access to new messages that traverse the monitored mailbox store, journaling doesn’t help if you need to read mail that’s already been delivered. In that case, the simplest way to get access to the mail that must be inspected is to grant the inspector access to the target mailbox. As I mentioned earlier, this is something that you should be very careful about doing—don’t ever grant your own account such permissions, and do your best to distance yourself from the actual mailbox inspection.
The basic requirement to gain access to another user’s mailbox is simple: the inspector’s account must be granted Receive As and Send As permissions on the target mailbox. As you might remember from Chapter 7, “Installing Exchange with Security in Mind,” when granted together these permissions effectively give complete access to the specified mailbox, so you shouldn’t assign them lightly. The actual steps to assign the permissions are simple:
-
Open the Active Directory Users and Computers snap-in. Choose the View | Advanced Features command and make sure that it’s checked; if it’s not, you won’t see the Security tab that you need to assign permissions on the mailbox.
-
Select the mailbox account you want to grant access to, then right-click it and select the Properties command.
-
In the Properties dialog box, click the Exchange Advanced tab. In that tab, click Mailbox Rights; the Permissions dialog box (Figure 9-2) will appear.
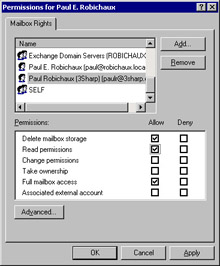
Figure 9-2: Add Send As and Receive As permissions to the mailbox. -
In the Permissions dialog box, click Add to add the inspection account, then grant Read and Full Mailbox Access permissions by selecting the appropriate check boxes. Click OK to close this dialog box; you’ll be back in the Properties dialog box.
-
Click the Security tab, which displays the discretionary access control lists (DACLs) on this particular mailbox. Click Add to create an access control entry (ACE) for the inspection account, then select that ACE and select the Receive As and Send As check boxes to grant those permissions on the mailbox. Click OK or Apply when you’re done.
| Tip | You can’t make these changes unless the account you’re using has administrative privileges in the first place |
There’s a complication to this process. In Microsoft Exchange 5.5, the site service account had permission to read any mailbox. To eliminate this security flaw in Exchange 2000, Microsoft did away with the all-powerful service account, and they also added to an explicit deny ACE for Send As and Receive As for administrator accounts. That means that if you add the Domain Admins or Enterprise Admins groups or accounts that belong to those groups as delegates to a mailbox, the explicit deny ACE trumps your explicit allow ACEs, and the privileged account won’t be able to read the mailbox.
There are two ways to resolve this problem. The first, and best, is not to use administrative accounts for mailbox inspection—leave that to the human resources or legal departments, or to someone in the target’s management chain. If that won’t work, you can remove the deny ACE on the mailbox database, but this is an inferior solution because it allows administrators to give themselves Send As and Receive As permissions on any or all mailboxes in that database.
| Tip | Remember, when a delegate opens a mailbox, if the delegate reads a message that has a receipt request attached (including delivery receipts and return receipts), the client might generate a receipt. This leaves a trail indicating that the mailbox is being monitored—each sender gets two responses to receipts! To prevent this embarrassing problem, make sure the people who are granted delegate access turn off their mail client’s ability to return receipts, and consider using a product like Grinning Shark’s Watch Your Back (http://www.grinningshark.com) to give the mail inspectors fine-grained control over receipt generation. |
|
EAN: N/A
Pages: 169