Chapter 2: Managing Access
Even the most secure of systems is vulnerable to compromise if anyone can just walk in, pick up the computer, and walk out with it. Physical prevention measures must be used in conjunction with Information Security measures to create a total solution. Herein, we cover the essential elements every security administrator needs to know about Access Control and management of passwords.
2.1 Access Control
According to the Information Systems Security Association (ISSA) [1], "access control is the collection of mechanisms for limiting, controlling, and monitoring system access to certain items of information, or to certain features based on a user 's identity and their membership in various predefined groups." In this section, we explore the major building blocks that constitute the field of Access Control as it applies to organizational entities and the Information Systems these entities are trying to protect from compromise situations.
2.1.1 Purpose of Access Control
Why should we have access control? Access control is necessary for several good reasons. Information that is proprietary to a business may need to be kept confidential, so there is a confidentiality issue that provides purpose to having Access Controls. The information that an organization keeps confidential also needs to be protected from tampering or misuse. The organization must ensure the integrity of this data for it to be useful. Having internal data integrity also provides purpose to having Access Controls. When employees of the organization show up for work, it is important that they have access to the data they need to perform their jobs. The data must be available to the employees for work to continue, or the organization becomes crippled and loses money. It is essential that data availability be maintained . Access Controls provide yet another purpose in maintaining a reasonable level of assurance that the data is available and usable to the organization. Therefore, the answer to the question asked at the beginning of this paragraph is that there are three very good reasons for having Access Controls:
-
Confidentiality
-
Data integrity
-
Data availability
2.1.2 Access Control Entities
In any discussion of Access Control, some common elements need to be understood by all parties. These elements compose a common body of terminology so that everyone working on security access issues is talking about the same thing. For our purposes, there are four primary elements we will discuss: (1) the Subject, an active user or process that requests access to a resource; (2) the Object, which is a resource that contains information (can be interchanged with the word " resource "); (3) the Domain, which is a set of objects that the subject can access; and (4) Groups, collections of subjects and objects that are categorized into groups based on their shared characteristics (e.g., membership in a company department, sharing a common job title).
2.1.3 Fundamental Concepts of Access Control
There are three concepts basic to implementation of Access Control in any organization. These concepts are establishment of a security policy, accountability, and assurance. We discuss each of these concepts in the following sections.
Establishment of a Security Policy
Security policy for an organization consists of the development and maintenance of a set of directives that publicly state the overall goals of an organization and recommend prescribed actions for various situations that an organization's information systems and personnel may encounter. Policy is fundamental to enabling continuity of operations. When something happens and the one person who knows the answer is on vacation, what is to be done? When policies are in place, administrators know what to do.
Accountability
For any information systems that process sensitive data or maintain privacy information, the organization must ensure that procedures are in place to maintain individual accountability for user actions on that system and also for their use of that sensitive data. There have been cases in industry where individuals who were employees of an organization committed criminal acts (e.g., theft of credit card data, theft of personal information for resale to mailing lists, theft of software or data for resale on eBay) that compromised the integrity of the information system. Such criminal actions cause huge problems for organizations, ranging from embarrassment to legal action. When these criminals have been caught, it has been because procedures were in place to ensure their accountability for their actions with the data. These procedures could be in the form of log files, audit trails for actions taken within an application, or even keystroke monitoring.
Assurance
As discussed previously, information systems must be able to guarantee correct and accurate interpretation of security policy. For example, if sensitive data exists on Machine A and that machine has been reviewed, inspected, and cleared for processing data of that particular level of sensitivity, when Joe takes the data from Machine A and copies it to his laptop to work on when traveling on the airplane, that data has most likely become compromised unless Joe's laptop has been reviewed, inspected, and cleared for processing that particular level of data sensitivity. If his machine has not been cleared, there is no assurance that the data has not been compromised. The policies in place at Joe's organization must be known to Joe in order to be effective, and they must be enforced in order to remain effective.
2.1.4 Access Control Criteria
When implementing security Access Controls, five common criteria are used to determine whether access is to be granted or denied : location, identity, time, transaction, and role (LITTR). Location refers to the physical or logical place where the user attempts access. Identity refers to the process that is used to uniquely identify an individual or program in a system. Time parameters can be control factors that are used to control resource use (e.g., contractors are not allowed access to system resources after 8 P.M. Monday through Friday, and not at all on weekends). Transaction criteria are program checks that can be performed to protect information from unauthorized use, such as validating whether a database query against payroll records that is coming from a user identified as belonging to the HR department is valid. Finally, a role defines which computer- related functions can be performed by a properly identified user with an exclusive set of privileges specific to that role. All of these criteria are implemented to varying degrees across the depth and breadth of a security plan. The policies and procedures used by an organization to make the plan effective determine the interplay among these criteria.
2.1.5 Access Control Models
When an organization begins to implement Access Control procedures, an administrator can choose to implement one of the following three basic models: (1) mandatory, (2) discretionary, and (3) nondiscretionary. Each has its particular strengths and weaknesses, and the implementor must decide which model is most appropriate for the given environment or situation. It is important to point out that most operating, network, and application systems security software in use today provide administrators with the capability to perform data categorization, discretionary Access Control, identity-based Access Control, user-discretionary Access Control, and non-discretionary Access Control. This section provides an overview of each type of Access Control model. Armed with this information, an implementor of Access Controls will be able to make better decisions about which model is most appropriate for specific purposes.
Mandatory Access Control Model
Mandatory Access Control occurs when both the resource owner and the system grant access based on a resource security label. A security label is a designation assigned to a resource [2] (such as a file). According to the NIST Handbook ,
Security labels are used for various purposes, including controlling access, specifying protective measures, or indicating additional handling instructions. In many implementations , once this designator has been set, it cannot be changed (except perhaps under carefully controlled conditions that are subject to auditing). When used for Access Control, labels are also assigned to user sessions. Users are permitted to initiate sessions with specific labels only. For example, a file bearing the label "Organization Proprietary Information" would not be accessible (readable) except during user sessions with the corresponding label. Moreover, only a restricted set of users would be able to initiate such sessions. The labels of the session and those of the files accessed during the session are used, in turn , to label output from the session. This ensures that information is uniformly protected throughout its life on the system.
Security labels are a very strong form of Access Control. Because they are costly and difficult to administer, security labels are best suited for information systems that have very strict security requirements (such as that used by government, financial, and research and development [R&D] organizations that handle classified information or information whose loss would severely or critically degrade the financial viability of the organization). Security labels are an excellent means of consistent enforcement of access restrictions; however, their administration and highly inflexible characteristics can be a significant deterrent to their use.
Security labels cannot generally be changed because they are permanently linked to specific information. For this reason, user-accessible data cannot be disclosed as a result of a user copying information and changing the access rights on a file in an attempt to make that information more accessible than the document owner originally intended. This feature eliminates most types of human errors and malicious software problems that compromise data. The drawback to using security labels is that sometimes the very feature that protects user data also prevents legitimate use of some information. As an example, it is impossible to cut and paste information from documents with different access levels assigned to their respective labels.
Data Categorization
One method used to ease the burden necessary for administration of security labeling is categorizing data by similar protection requirements (data categorization). As an example, a label could be developed specifically for "Company Proprietary Data." This label would mark information that can be disclosed only to the organization's employees. Another label, "General Release Data," could be used to mark information that is available to anyone.
When considering the implementation of mandatory Access Controls with security labels, one must decide between using a rule-based approach, where access is granted based on resource rules, or using an administratively directed approach, where access is granted by an administrator who oversees the resources. Using a rule-based approach is most often preferred because members of a group can be granted access simply by validating their membership in that group. Access levels are assigned at a group level, so all members of the group share a minimum level of access. All files that are created or edited by any one of the members of that group are equally accessible to any other member because the security labels that are instituted have all members of the group sharing equal access to the group resources. Trust is extended to the membership as a whole simply because membership in the group without having proper access would not be allowed. This approach is less administratively intensive than using the approach where an administrator manually oversees resources, granting or withdrawing access on an individual case-by-case basis. There are some instances where this approach is preferable, however. Consider a scenario in which only a few members need access to extremely sensitive information. The owner of this information may choose to manually oversee security label application simply to maintain a personal level of control over access to highly sensitive materials.
Discretionary Access Control Model
According to a document published in 1987 by the National Computer Security Center, [3] discretionary access control is defined as "a means of restricting access to objects based on the identity of subjects and/or groups to which they belong. The controls are discretionary in the sense that a subject with a certain access permission is capable of passing that permission (perhaps indirectly) on to any other subject."
Discretionary Access Controls restrict a user's access to resources on the system. The user may also be restricted to a subset of the possible access types available for those protected resources. Access types are the operations a user is allowed to perform on a particular resource (e.g., read, write, execute). Typically, for each resource, a particular user or group of users has the authority to distribute and revoke access to that resource. Users may grant or rescind access to the resources they control based on "need to know" or "job essential" or some other criteria. Discretionary Access Control mechanisms grant or deny access based entirely on the identities of users and resources. This is known as identity-based discretionary Access Control .
Knowing the identity of the users is key to discretionary Access Control. This concept is relatively straightforward in that an Access Control matrix contains the names of users on the rows and the names of resources on the columns. Each entry in the matrix represents an access type held by that user to that resource. Determining access rights is a simple process of looking up a user in the matrix row and traversing the resource columns to find out what rights are allowed for a given resource.
A variant of this is user-directed discretionary Access Control. Here, an end user can grant or deny access to particular resources based on restrictions he or she determines, irrespective of corporate policy, management guidance, and so on. With the ability to inject the human factor into this equation, you can surmise that the level of protection for an organization depends on the specific actions of those individuals tasked to protect information. One drawback to the discretionary Access Control Model is that it is both administratively intense and highly dependent on user behavior for success in protecting resources. This has led to the creation of hybrid Access Control implementations, which grant or deny access based on both an identity-based model and user-directed controls.
Nondiscretionary Access Control Model
This Access Control model removes a user's discretionary ability and implements mechanisms whereby resource access is granted or denied based on policies and control objectives. There are three common variants of this approach: (1) role based, where access is based on a user's responsibilities; (2) task based, where access is based on a user's job duties ; and (3) lattice based, where access is based on a framework of security labels consisting of a resource label that holds a security classification and a user label that contains security clearance information. The most common of these approaches is Role-Based Access Control (RBAC). The basic concept of RBAC is that users are assigned to roles, permissions are assigned to roles, and users acquire permissions by being members of roles. David Ferraiolo of the National Institute of Standards drafted the "Proposed Standard for Role Based Access Controls," [4] which states
Core RBAC includes requirements that user-role and permission-role assignment can be many-to-many. Thus the same user can be assigned to many roles and a single role can have many users. Similarly, for permissions, a single permission can be assigned to many roles and a single role can be assigned to many permissions. Core RBAC includes requirements for user-role review whereby the roles assigned to a specific user can be determined as well as users assigned to a specific role. A similar requirement for permission-role review is imposed as an advanced review function. Core RBAC also includes the concept of user sessions, which allows selective activation and deactivation of roles.
As an example, Joe is an accountant and serves as the manager of payroll operations at ABC Company. His role in the company as manager of payroll would, in RBAC, allow Joe to see all materials necessary for successful conduct of payroll operations. He is also a member of the whole Accounting Group at ABC Company. In that role, as a member of Accounting, he is given access to all of the general accounting resources that are made available to the Accounting Group, but he does not have access to specific files that belong to the Accounts Payable, Accounts Receivable, or Expense Processing Teams. If the Expense Processing Team decided to make an internal document available to the general Accounting Group, then Joe would be able to see that document because of his membership in the Accounting Group.
The difference between role-based and task-based access is subtle, but distinct. The previous scenario was built around Joe's area of responsibility and his membership in a group. In the task-based Access Control scenario, Joe would see only documents in Accounting that were determined by company work flow procedures to be necessary for Joe to see to successfully manage payroll operations. Based on Joe's current job duties, it is not "job necessary" for Joe to see what is produced by the Expense Department, Accounts Payable, or Accounts Receivable, even if Joe is a member of the Accounting Group. For many companies, this subtle distinction is more trouble than it is worth when the RBAC model can be more easily implemented with the newer computing platforms of today.
In the lattice-based model, Joe's access is based on a framework of security labels. The documents Joe would need to perform his job would have to have their resource label checked to see what security classification (e.g., "general release" or "company proprietary") that resource has, and a user label that contains security clearance information would be checked to ensure that Joe is entitled or "cleared" to access that company proprietary-level information. In a government scenario, working with classified material, this model is much more prevalent than it is in industry. Substitute the words "unclassified," "confidential," "secret," or "top secret" for the words "company proprietary" or "general release," and you get the idea how a government Access Control system works.
2.1.6 Uses of Access Control
There are seven general uses for Access Controls:
-
Corrective, to remedy acts that have already occurred
-
Detective, to investigate an act that has already occurred
-
Deterrent, to discourage an act before it occurs
-
Recovery, to restore a resource to a state of operation before when an act occurred
-
Management, to dictate the policies, procedures, and accountability to control system use
-
Operational, to set personnel procedures to protect the system
-
Technical, to use software and hardware controls to automate system protection
Ideally, management policies and procedures would dictate operational activities that implement technical solutions that deter unauthorized access and, when that fails, detect such access in a manner that allows for rapid recovery using corrective actions. There, I said it. As simplistic as that sentence sounds, it embodies the very essence of the many uses of Access Control in an organization. Why make it more complicated?
2.1.7 Access Control Administration Models
Centralized Administration Model
The Centralized Administration Model is based on the designation of a single office location or single individual as the responsible party tasked with setting proper Access Controls. The advantage to using this approach is that it enforces strict controls and uniformity of access. This is because the ability to make changes to access settings resides with very few individuals in a Centralized Administration Model. When an organization's information-processing needs change, personnel with access to that information can have their access modified, but only through the centralized location. Most of the time, these types of requests require an approval by the appropriate manager before such changes are made. Each user's account can be centrally monitored , and closing all accesses for any user can be easily accomplished if that individual leaves the organization. Because the process is managed by a few centralized resources in an organization, enforcing standard, consistent procedures is fairly easy.
The most obvious drawback to a centralized model approach is the time it takes to make changes when they must be coordinated and approved before being made. Sometimes, when there are many people in an organization, these requests can become backlogged. Most of the time, however, the tradeoff between having strict enforcement and standardized processes is worth enduring the hassle of going through a little bureaucracy to get something done. An example of a centralized access model would be the use of a Remote Authentication Dial-in User Service (RADIUS) server, which is a centralized server used for a single point of network authentication for all users needing access to the network resources. Another example would be a Terminal Access Controller Access Control System (TACACS) server, which is a centralized database of accounts that are used for granting authorization for data requests against a data store or subsystem (e.g., a company-owned CRM product).
Decentralized Administration Model
Using the Decentralized Administration Model, all access is controlled by the specific document or file originator. This allows control to remain with those who are responsible for the information. The belief is that these people are best suited to determine who needs access to a document and what type of access they need; however, there is a great opportunity to suffer the consequences of a lack of consistency among document originators regarding procedures and criteria that are used to make user access decisions. Also, with the Decentralized Administration Model, it is difficult to get a composite view of all user accesses on the system at any given time.
These inconsistencies can create an environment where different application or data owners may inadvertently implement access combinations that create conflicts of interest or jeopardize the organization's best interests. Another disadvantage is that the Decentralized Administration Model needs to be used in conjunction with other procedures to ensure that accesses are properly terminated when an individual leaves the company or is moved to another team within the organization. An example of common use of the Decentralized Administration Model is a domain in which all file shares are accessible in read-only mode, but each file share owner would determine if a user could perform write or execute activities in the file share. In a domain with a few hundred file shares, this lack of uniformity and standardization quickly becomes apparent.
Hybrid Administration Model
The Hybrid Administration Model combines the centralized and decentralized administration models into a single approach. An example would be use of a RADIUS server (centralized login/authentication) for gaining basic access to the network and having resources distributed across the network, where each domain on the network is controlled by a different administrator. This is a typical corporate model where the central administration part is responsible for the broadest and most basic of accesses, that of gaining entry to the network, and the decentralized part is where the system owners and their users (the creators of the files) specify the types of access implemented for those files under their control. The main disadvantage to a hybrid approach is the haggle over what should and should not be centralized.
2.1.8 Access Control Mechanisms
Many mechanisms have been developed to provide internal and external Access Controls, and they vary significantly in terms of precision, sophistication, and cost. These methods are not mutually exclusive and are often employed in combination. Managers need to analyze their organization's protection requirements to select the most appropriate, cost-effective logical Access Controls. Logical Access Controls are differentiated into internal and external Access Controls. Internal Access Controls are a logical means of separating what defined users (or user groups) can or cannot do with system resources.
Internal Access Controls
We cover four methods of internal Access Control in this section: passwords, encryption, Access Control Lists (ACLs), and constrained user interfaces. Each of these four methods of internal access is discussed next .
Passwords
Passwords are most often associated with user authentication; however, they are also used to protect data and applications on many systems, including PCs. For instance, an accounting application may require a password to access certain financial data or to invoke a restricted application. The use of passwords as a means of Access Control can result in a proliferation of passwords that can reduce overall security. Password-based Access Control is often inexpensive because it is already included in a large variety of applications; however, users may find it difficult to remember additional application passwords, which, if written down or poorly chosen , can lead to their compromise. Password-based Access Controls for PC applications are often easy to circumvent if the user has access to the operating system (and knowledge of what to do).
Encryption
Another mechanism that can be used for logical Access Control is encryption. Encrypted information can only be decrypted by those possessing the appropriate cryptographic key. This method is especially useful if strong physical Access Controls cannot be provided, such as for laptops or floppy diskettes. Thus, for example, if information is encrypted on a laptop computer, and the laptop is stolen, the information cannot be accessed. Although encryption can provide strong Access Control, it is accompanied by the need for strong key management. Use of encryption may also affect availability. For example, lost or stolen keys or read/write errors may prevent the decryption of the information.
Access Control Lists
ACLs refer to a matrix of users (often represented as rows in the matrix that include groups, machines, and processes) who have been given permission to use a particular system resource, and the types of access they have been permitted (usually represented in the matrix as columns). ACLs can vary widely. Also, more advanced ACLs can be used to explicitly deny access to a particular individual or group. With more advanced ACLs, access can be determined at the discretion of the policy maker (and implemented by the security administrator) or individual user, depending on how the controls are technically implemented.
Elementary ACLs
The following brief discussion of ACLs is excerpted from the NIST Special Publication 800-12. [5] Elementary ACLs (e.g., permission bits) are a widely available means of providing Access Control on multiuser systems. Elementary ACLs are based on the concept of owner, group, and world permissions (see Figure 2.1). These preset groups are used to define all permissions (typically chosen from read, write, execute, and delete access modes) for all resources in this scheme. It usually consists of a short, predefined list of the access rights each entity has to files or other system resources. The owner is usually the file creator, although in some cases, ownership of resources may be automatically assigned to project administrators, regardless of the creator's identity. File owners often have all privileges for their resources. In addition to the privileges assigned to the owner, each resource is associated with a named group of users. Users who are members of the group can be granted modes of access that are distinct from nonmembers, who belong to the rest of the "world," which includes all of the system's users. User groups may be arranged according to departments, projects, or other ways appropriate for the particular organization.
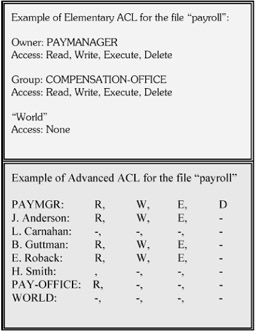
Figure 2.1: Examples of Access Control Lists (ACLs).
Advanced ACLs
Advanced ACLs provide a form of Access Control based on a logical registry. They do, however, provide finer precision in control. Advanced ACLs can be very useful in many complex information-sharing situations. They provide a great deal of flexibility in implementing system-specific policy and allow for customization to meet the security requirements of functional managers. Their flexibility also makes them more of a challenge to manage, however. The rules for determining access in the face of apparently conflicting ACL entries are not uniform across all implementations and can be confusing to security administrators. When such systems are introduced, they should be coupled with training to ensure their correct use.
Constrained User Interfaces
Interfaces that restrict users' access to specific functions by never allowing them to request the use of information, functions, or other specific system resources for which they do not have access are known as constrained user interfaces . They are often used in conjunction with ACLs. There are three major types of constrained user interfaces: menus , database views, and physically constrained user interfaces:
-
Menu-driven systems are a common constrained user interface, where different users are provided different menus on the same system. Constrained user interfaces can provide a form of Access Control that closely models how an organization operates. Many systems allow administrators to restrict users' ability to use the operating system or application system directly. Users can only execute commands that are provided by the administrator, typically in the form of a menu. Another means of restricting users is through restricted shells, which limit the system commands the user can invoke. The use of menus and shells can often make the system easier to use and can help reduce errors.
-
Database views is a mechanism for restricting user access to data contained in a database. It may be necessary to allow a user to access a database, but that user may not need access to all of the data in the database (e.g., not all fields of a record nor all records in the database). Views can be used to enforce complex access requirements that are often needed in database situations, such as those based on the content of a field. For example, consider the situation where clerks maintain personnel records in a database. Clerks are assigned a range of clients based on last name (e.g., A “C, D “G). Instead of granting a user access to all records, the view can grant the user access to the record based on the first letter of the last name field.
-
Physically constrained user interfaces can also limit users' abilities . A common example is an ATM, which provides only a limited number of physical buttons to select options; no alphabetic keyboard is usually present.
External Access Controls
External Access Controls consist of a variety of methods used to manage interactions between a system and external users, systems, and services. External Access Controls employ many methods, sometimes including a separate physical device placed between the system being protected and a network. Examples include Port Protection Devices (PPDs), secure gateways, and host-based authentication.
Port Protection Devices
These devices are physically connected to a communications port on a host computer. A PPD authorizes all access to the port to which it is attached. This is done before and independently of the computer's Access Control functions. A PPD can be a separate device in the communications stream, or it may be incorporated into a communications device (e.g., a modem). PPDs typically require a separate authenticator, such as a password, in order to access the communications port.
Secure Gateways/Firewalls
Often called firewalls , secure gateways block and/or filter access between two networks. They are most often employed between a private network and a larger, more public network such as the Internet. Secure gateways allow network users to connect to external networks, and simultaneously they prevent malicious hackers from compromising the internal systems. Some secure gateways allow all traffic to pass through except for specific traffic that has known or suspected vulnerabilities or security problems, such as remote log-in services. Other secure gateways are set up to disallow all traffic except for specific types, such as e-mail. Some secure gateways can make access-control decisions based on the location of the requester. Several technical approaches and mechanisms are used to support secure gateways.
Types of Secure Gateways
There are various types of secure gateways on the market today. These include packet filtering (or screening) routers, proxy hosts, bastion hosts , dual- homed gateways, and screened-host gateways. Because these secure gateways provide security to an organization by restricting services or traffic that passes through their control mechanisms, they can greatly affect system usage in the organization. This fact reemphasizes the need to establish security policy so management can decide how the organization will balance its operational needs against the security costs incurred.
Secure gateways benefit an organization by helping to reduce internal system security overhead. This is because they allow an organization to concentrate security efforts on a few machines instead of on all machines. Secure gateways allow for centralization of services. They provide a central point for services such as advanced authentication, e-mail, or public dis-semination of information. This can reduce system overhead and improve service in an organization.
Host-Based Authentication
The Network File System (NFS) is an example of a host-based authentication system. It allows a server to make resources available to specific machines. Host-based authentication grants access based on the identity of the host originating the request rather than authenticating the identity of the user. Many network applications in use today employ host-based authentication mechanisms in order to determine whether access is allowed to a given resource. Such host-based authentication schemes are not invulnerable to attack. Under certain circumstances, it is fairly easy for a hacker to masquerade as a legitimate host and fool the system into granting access. Security measures used to protect against the misuse of some host-based authentication systems are often available, but require special steps or additional configuration actions that need to be taken before they can be used. An example would be enabling DES encryption when using remote procedure calls.
2.1.9 Techniques Used to Bypass Access Controls
In the realm of security, the use of common terms enables all parties to understand exactly what is meant when discussing security issues. When talking about attacks, four terms are quite common: vulnerability, threat, risk, and exposure. A vulnerability is a flaw or weakness that may allow harm to an information system. A threat is an activity with the potential for causing harm to an information system. Risk is defined as a combination of the chance that threat will occur and the severity of its impact. Exposure is a specific instance of weakness that could cause losses to occur from a threat event.
Hackers use several common methods to bypass Access Controls and gain unauthorized access to information, principally, brute force, Denial of Service (DoS), social engineering, and spoofing. The brute force method consists of a persistent series of attacks, often trying multiple approaches, in an attempt to break into a computer system. A DoS occurs when someone attempts to overload a system through an online connection in order to force it to shut down. Social engineering occurs when someone employs deception techniques against organizational personnel in order to gain unauthorized access. This is the most common method of attack known. Finally, spoofing is when a hacker is masquerading an ID in order to gain unauthorized access to a system.
EAN: 2147483647
Pages: 153