8.2 Decisions, Decisions
|
8.2 Decisions, Decisions
So which type of firewall is best for your network? The easy answer to that is that it depends on your security policy. What assets are you trying to protect? What level of protection do your assets require, and are there other countermeasures that sufficiently reduce the risk and are more cost effective? For example, would it be more cost effective in the long run to employ the concept of least privilege for all users on their own hosts, instead of setting up an expensive application layer firewall to screen inbound Web traffic? Can a proxy be configured to reject questionable sites instead for less cost as there are a number of free, robust proxy servers available?
To put things into perspective, however, we will look beyond the needs of our security policy a bit and think logically about the utility of the firewall on our network. It would be helpful to discuss what a firewall cannot do to protect your network.
A firewall will not protect your network against traffic that does not go through it. That seems obvious when printed on the page, but is a fact that is often overlooked in network design. Unless the forwarding behavior of your network can be controlled to an extent that you know where all traffic is being sent, a firewall will only provide a false sense of security. Users who are allowed to connect modems to their desktops are effectively circumventing the security policy by circumventing the firewall put into place to enforce it. Multi-homed networks are another consideration. Care should be taken to ensure that all egress and entry points to the network are configured appropriately. You may believe that the secondary link is only being used in an emergency, but depending upon your routing policies, traffic may indeed be using the link. Furthermore, what would happen if an emergency were to strike? Would users be able to continue their daily operations using the secondary link, or would differing firewall polices prevent this?
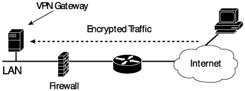
A firewall also cannot protect your data if it cannot understand it (see Exhibit 3). Many companies create holes in their firewalls to allow VPN traffic through the firewall. Unless there is additional checking being done in the encrypted traffic elsewhere in the network, this is a bad idea. A VPN only encrypts data — ensuring confidentiality; it does nothing to ensure that the data being encrypted is good for the health of your network. Because a firewall cannot read encrypted data, companies may be creating an avenue of attack right through their own firewall. Firewalls are a collection of hardware and software that must work together to enforce a security policy. Like any other computer program, there may be flaws in the program that runs the firewall. These flaws need to be patched. Therefore, the firewall itself needs to be maintained. This maintenance also implies regular inspection of the rules. More than once I have visited a customer site to find a firewall that was several patches behind and had a rule set that had slowly changed over the years as new requirements were made of the network. Instead of removing old rules, the network administrators were so afraid of breaking things that they just added rules onto the end. The effective security of the firewalls as they were configured in this state was very low. Old rules that were not removed were allowing access to inappropriate internal hosts and the firewall operating system itself was several patch levels behind, thus increasing the risk of remote compromise.
Exhibit 3: Firewalls Cannot Check Encrypted Traffic
In my role as an educator and consultant, I am often asked the question, "Which firewall do you think is best? Brand X, Brand Y, or Brand Z?" The response is always the same. "Which are you most comfortable using?" is the reply.
This brings me to a final point about the effectiveness of a firewall solution. I am sure that any firewall vendor will be happy to report the pros of their devices compared to those of their competitors, but the most effective firewall is going to be one that users are comfortable using. If the network administrator is not comfortable reviewing the logs, changing the rule sets, and installing patches, then the firewall is going to be an ineffective panacea at best.
The deployment of a firewall is an important issue, especially where other security technologies are included. For the relevant technologies, such as VPN integration, the information will be included in those sections. For now, we will only discuss the firewall alone.
As previously discussed, it is common to point to a box and say "That there is my firewall." From a security point of view, however, it is more accurate to say, "My firewall is created from these technologies."
Every firewall has the idea of the "inside" and the "outside," which allows the network administrator to control the flow of traffic from one side of the firewall to the other. What is the inside and outside, however, may vary, depending on the placement of the firewall. For example, there is no rule that states that firewalls can only be placed on the edge of the network. Internal resources and server farms can also be protected from internal malicious and unintentional damage through the use of a firewall. Your security policy will dictate if this is a requirement.
Many organizations use multiple firewall devices. Sometimes, these are configured in parallel and other times in series. The parallel configuration is the ideal solution to address network availability. This is particularly helpful in multi-homed environments where there are multiple WAN links and availability has a high priority.
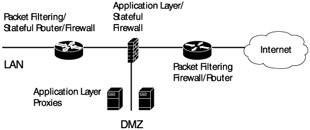
When considering the firewall as a group of devices, typically the first device that a packet hits when it enters the network is the access router at the edge of the customer network. Modern routers sport fairly robust processors, memory, and operating systems. Many can operate as stateful packet filters or even higher layer firewalls in their own right. Because every organization needs a router to connect to the Internet in the first place, this is an excellent place to begin your perimeter security.
As a packet travels into the network, it will typically hit another firewall. This is a firewall that complements the packet filtering that is going on in the router and may include the higher layer functions such as proxy services and application layer filtering. The hardware that supports this second line of defense may have a number of network interfaces, with some network interfaces supporting the internal network and others supporting DMZs. The DMZ area may host a number of application layer firewalls; these will typically be mail relays that can be configured to scan for attachments and viruses.
In situations that require high security, internal firewalls may also separate sections of the network. For the sake of performance, this can be as simple as stateful packet filtering, limiting access to protected hosts by port number (see Exhibit 4). Configuring firewalls in series increases the security of the network by creating multiple hops that the network attacker must jump through to access the network. If you are considering this solution, consider at least two different firewall vendor products for placement in series. If you go through the expense of purchasing and maintaining two firewalls, it would be a shame to have them both felled by a single, previously unknown exploit that bypasses their security features. By using the products of two different vendors, this chance is reduced. Be aware that employing firewalls in a series will also add additional delay to any packet transmissions that are sent through the firewall. In practice, this is only a concern if real-time communications are employed, such as Voice-over-IP (VoIP), which has one-way tolerances of 150 ms.
Exhibit 4: Together, These Devices Operate as a "Firewall"
I do not discuss specific firewall products because the technology and vendor offerings change rapidly enough to render the information in such a section obsolete. When considering which firewall to purchase, refer to the information in previous chapters on evaluating countermeasures. Armed with that information and a complete security policy, you will have all the information you need to ask the right questions. Yes, a firewall can be an expensive product, but there is more than one robust firewall solution that can run as open source software requiring only the hardware to support the product.
|
EAN: 2147483647
Pages: 119