Case Study
|
| < Day Day Up > |
|
You should give yourself 20 minutes to review this testlet, review the table, and complete the questions.
Overview
Towely Incorporated designs, manufactures, and markets industrial strength towels. Towely Inc. is currently the largest supplier of towels to hotels in the world.
Physical Locations
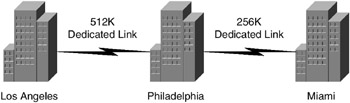
The organization has three offices, as shown in the following table. The main office is in Philadelphia, and there are branch offices in Los Angeles and Miami. Employees and the business units are distributed as referenced in the table.
| Office Locations | Employee Quantity | Business Units | Onsite IT support |
|---|---|---|---|
| Philadelphia | 5,000 | Executive, Marketing, HR, and IT | IT staff |
| Los Angeles | 750 | Accounting and Research and Development | 5 IT administrators |
| Miami | 100 | Manufacturing | 1 IT administrator and 1 help desk operator |
Existing Environment
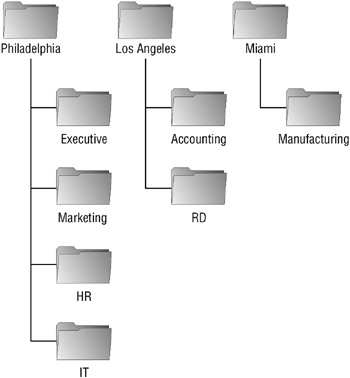
Directory Services Towely Incorporated consists of a single Active Directory domain named TowelyInc.com. The company’s organizational unit (OU) structure is shown in the OU structure exhibit (in the section “Case Study Exhibits”).
There are domain controllers in each of the offices: Philadelphia, Miami, and Los Angeles.
A global security group named PHLExecs contains all of the executive employees in the Philadelphia office. A global security group named MIAManufacture contains all of the manufacturing employees in the Miami office.
Network Infrastructure All of the servers are running Windows Server 2003, Enterprise Edition. All of the client workstations in all of the sites are running Windows XP Professional. All computers have the most recent service packs applied. Client workstations access websites through a proxy server.
Towely Incorporated uses an internal website to handle most of the human resources as well as other organizational business. Only employees should be allowed to access the intranet and the organization’s information.
There is also a perimeter network. The perimeter network houses a server named ExServer4. ExServer4 is not a member of the Active Directory domain. ExServer4 hosts a website that is used by the various hotel chains to order more towels for their respective hotels. The website is maintained in Internet Information Services 6.0 running an ASP .NET application.
All of the Research and Development data is located on a single server named RD_Data, located in Los Angeles.
Problem Statements
The following organizational problems must be considered:
-
Whenever a significant outage occurs, the help desk operator in Miami gets inundated with calls.
-
The employees in the Los Angeles office have a history of installing unsupported drivers on their workstations. In addition, you have discovered that unauthorized software has been installed on some of the workstations by employees. Some of applications that have been installed have caused incompatibilities with some of the line-of-business applications.
-
Users frequently forget to lock or log out of their client computers. This is a security risk and should be prevented from happening.
Interviews
Chief Information Officer We plan on implementing a secure infrastructure to prevent our competitors from gaining access to our research information.
On occasion, we monitor logon traffic to our domain controllers and inspect the logs randomly. This inspection needs to occur on a more regular basis.
Chief Operating Officer The last time the IT department implemented a widespread policy shift, it took the users several weeks to adjust and production decreased significantly. Any changes that are made that affect production need to have a minimum impact on the bottom line.
Network Administrator We need to test software and make sure that it is compatible with our current desktop image. Users should not be able to install software on their own client computers without administrative oversight.
Last year more than 10 users had their passwords compromised because they were easily guessed. Our team spent weeks recovering from each of the incidents and we want to, at least, minimize the occurrence of passwords being compromised.
Currently there are no logon policies in place.
Business Requirements
Organizational Goals Currently the IT Staff manages user, group, and computer accounts centrally in Philadelphia. The help desk operator in Miami needs to have the authority to manage the users in Miami only.
Security The company’s security policy contains the following requirements:
-
Manufacturing data must not be accessible over the network through shared folders. The highest level of authentication must be used for all access to the data.
-
Access to the RD_Data folder must be restricted to only members of the research team. The research team should be able to make all types of changes to the contents of the files.
-
Before business partners are allowed to access the partner site, the source IP address needs to be recorded and be in a specific list of allowed source addresses.
The following security requirements apply specifically to the websites and servers for the organization.
-
IIS cannot be installed on domain controllers.
-
All access to the internal website should be restricted to only allow authenticated users in the domain.
Case Study Exhibits
The following shows the physical locations and connectivity diagram:
The following shows the Active Directory organizational unit structure:
Case Study Questions
| 1. | You need to give permissions to the employees in the research team so that they can access the research data. Which of the following tasks should you complete? (Choose all that apply.)
| |
| 2. | You decide to implement strong password requirements for all of the users in the Miami office. You need to make sure that no password cracking utility can access LM hashes on the local machines. What additional steps should you take? (Choose all that apply.)
| |
| 3. | Towely Incorporated has hired some new research and development employees that need to have access to the research data. What must you do to assure that the new employees can access the data to perform their job?
| |
| 4. | Towely Incorporated has just acquired Leaf Soap LLP. Leaf Soap runs a Windows 2000 Active Directory domain that is running in Native mode. You need to configure the two domains to talk to each other so that resources are available to users in both domains. You need to configure the trust relationship to use Kerberos v5. What additional tasks must you perform? (Choose all that apply.)
| |
| 5. | With the acquisition of Leaf Soap, your IT staff now must secure additional servers. After auditing the new network, it is determined that Exchange Server is running in the Leaf Soap domain. The service accounts for Exchange are running in the context of the LocalSystem account. You would like the service to run custom scripts that record log information to a remote share. You need to make sure that accounts have only the absolute minimum permissions that they require in order to function. Which one of the following should you do?
| |
| 6. | You fear that the accounts in the Leaf Soap domain are less secure due to weak password requirements. Which of the following policies should you enable in order to require stronger passwords? (Choose all that apply.)
| |
| 7. | You want to make sure that users in the Philadelphia office can only log on during normal business hours. What can you do in order to enforce this rule?
| |
| 8. | Your security team has alerted you that in the early morning hours, several attempts are made to authenticate as various accounts and these attempts are obviously not being made by employees. What additional security policies must you enable to prevent this from being exploited into a brute force password attack? (Choose two.)
| |
| 9. | In your organization, a user, Winston Smith, whose logon is wsmith, attempts to set his password to WiNsTOn98. You have configured the default password filter by enabling the Passwords Must Meet Complexity Requirements policy. The password is rejected citing password requirements. Why?
| |
| 10. | One of your partners needs to provide resources to some of your users. The partner runs Unix and has a Kerberos realm configured. You need to make sure that your organizational resources cannot be accessed by your partner’s accounts. What should you do?
| |
| 11. | To prevent users from being able to install software on their workstations, which one of the following tasks should you complete?
| |
Answers
| 1. | A, E. The proper way to assign permissions to resources is to use the AG(G)DLP technique. Put accounts in Global groups, optionally nest Global groups, place Global groups into Domain Local groups, and assign permissions to the Domain Local group. Option B is incorrect because accounts shouldn’t be added to a Domain Local group. Option C is incorrect because permissions shouldn’t be assigned to Global groups. Option D is incorrect because accounts shouldn’t be added directly to Universal groups. Options A and E fall into the AG(G)DLP rule. |
| 2. | B, E. To prevent LM hashes of passwords from being stored, you will need to modify the local security policy of all the workstations in Miami. To do this in the most effective manner, you should create a Group Policy Object (GPO) that prevents the storing of LM hashes locally and link it to the Miami OU. Or, you can require that passwords be more than 14 characters long, which also prevents the LM hash from being stored. Therefore options B and E are correct. Options A, C, and D are incorrect because none of them have any effect on the storing of LM hashes. |
| 3. | C. To give the new employees access to the appropriate resources, you should add them to the Global group for the research users. Accounts should be added to Global groups, not Domain Local or Universal groups. All users are automatically added to the Domain Users group, which doesn’t have access to the specific resources for the Research and Development department. |
| 4. | B, D. For the trust relationship to use Kerberos v5, both domains must be running Windows 2003 Active Directory in Native mode. The Leaf Soap domain controllers must be upgraded to Windows Server 2003 in order to facilitate the Kerberos trust relationship. Once you’ve upgraded Active Directory in the Leaf Soap domain, you should create a two-way trust relationship between the two domains. Option A is incorrect because a Windows 2000 Active Directory domain cannot be converted to a Kerberos realm. Option C is incorrect because there is no Registry setting that provides this functionality and bridgehead servers are the primary path connecting sites for replication; they do not play a direct role in trust relationships or Kerberos authentication. |
| 5. | C. To make sure that the account has only the permissions that are required, it should be a domain user account that is assigned the minimum permissions to run the service. Option A is incorrect because the LocalSystem account should not be used for services that could be targets for attack. Option B is incorrect because a local account is not sufficient to access the remote share. Option D is incorrect because giving the account administrator privileges is giving excessive permissions and causes the attack surface to widen instead of become smaller. |
| 6. | B, E. Only options B and E will force the passwords to be stronger. Setting a maximum or minimum password age or setting the Enforce Password History policy will make the accounts more secure but not make the passwords stronger, which is the requirement in the question. |
| 7. | A. To restrict when users are allowed to log on, you will need to configure the logon hours using the Active Directory Users And Computers tool and configure the policy in the account’s properties dialog box. Option B is incorrect because there is no Logon Hours domain policy. Nor is there a Store Logon Hours With Credentials option, and therefore option C is incorrect. Option D is incorrect because account lockout settings don’t enforce logon hour rules. |
| 8. | A, D. You must configure the Account Lockout Duration option and the Account Lockout Threshold option in order to prevent a brute force attack against your accounts. Option B could be configured, but it isn’t required. In the current configuration, an administrator will need to unlock the account manually rather than let it automatically unlock itself after a prescribed time period. Option C is incorrect because enforcing password history won’t prevent a brute force attack. |
| 9. | C. The default filter requires that a password meet three of the four required character types, which the supplied password does. Therefore option A is incorrect. The password does not contain the user’s logon name, which is wsmith. The minimum number of characters for a password as defined in the default filter is 6, and the supplied password exceeds 6 characters. The only possibility is that the user’s name is Winston (either first or last). |
| 10. | A. Option B is incorrect because you should configure a one-way trust only where the Unix realm trusts your Active Directory domain. Option C is wrong because the trust is going in the wrong direction. Option D is wrong because the resources are located at the partner site, not yours, and therefore the partner needs to assign the permissions to the resources, not your organization. Option A is correct because you need to create a trust relationship between your Windows domain and a non–Windows domain, in this case UNIX, using a Kerberos realm trust. The question states that you need to make sure that the resources in your domain are not to be accessible to the users of the UNIX realm therefore the trust should only go one way: from the UNIX realm to your Active Directory domain. |
| 11. | C. The users are able to install software because they have excessive permissions on their workstations. Option A is incorrect because all users should be members of the global Domain Users group. Answer B is incorrect because, if the users aren’t members of the local Users group, they won’t have the required permissions to use their client computer. Option D is incorrect because there is no Restricted group on local workstations. |
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 168