| Keeping your servers physically secure is one of the first aspects of security that you should consider. If a computer can be physically accessed, then with sufficient time it can be compromised. Because servers are shared resources, their security is usually more important because their compromise would more severely affect your organization. There isn't much point in looking after the other aspects of security until you've addressed physical security. Preventing booting from various other devices If your server is in an area where others have physical access to it, they could potentially circumvent the login procedure by power-cycling the computer and restarting in a vulnerable mode. For instance, booting from a system CD, a system DVD, a FireWire hard drive, or a NetBoot drive, the perpetrator will have access to all files on the computer. Booting into single-user mode, the perpetrator will have root access to the computer and all items on that computer. To enable an Open Firmware lock 1. | Launch the Open Firmware Password application, located in /Applications/Utilities/ on the Mac OS X 10.4 installation disk (Figure 10.1).
Figure 10.1. Recognizing the Open Firmware Password application icon. 
For Mac OS X 10.110.3.9, you can download the Open Firmware Password application from www.apple.com/support/downloads/openfirmwarepassword.html.
| | | 2. | In the dialog that appears, click Change (Figure 10.2).
Figure 10.2. Launching the Open Firmware Password application brings up this dialog. 
| 3. | Click the "Require password to change Open Firmware settings" check box, enter and verify your password, and click OK (Figure 10.3).
Figure 10.3. Setting the password for the firmware using Open Firmware Password. 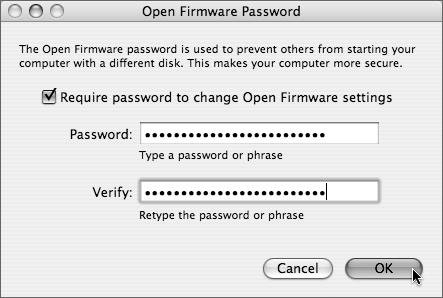
| 4. | Enter an administrator name and password in the standard authentication dialog and click OK.
| 5. | Quit Open Firmware Password by choosing Quit from the Open Firmware Password menu.
|
Startup Keyboard Shortcuts Apple offers the following keyboard shortcuts, which can be executed after the initial startup chime on PowerPCs: Pressing Option + Command +Shift + Delete during startup attempts to start from a disk other than the primary startup disk. Pressing C during startup attempts to start from a CD or DVD. Pressing N during startup attempts to start from a network server. Pressing T during startup attempts to start in target disk mode. Pressing Shift at boot (after chime) attempts to start in safe boot mode. Pressing V during startup attempts to start in verbose mode. Pressing S during startup attempts to start in single-user mode.
|
Determining rack and room security If your server is being used for anything other than personal testing, you must limit physical access to it. Ideally, you have a server room with a locking door to which only a small number of trusted people have keys. If you have a shared server room, you can add security by putting your server in a rack cabinet that locks. If you work in an office that is reasonably secure, a locking rack cabinet may be sufficient, but be sure to review all of the people who have access to the space where your server is, and consider the consequences of a compromised server. What if someone breaks into your building? How critical and/or sensitive is the data on your server? These are questions that should be evaluated in deciding the physical location of your server. Open Firmware Password Workaround Locking Open Firmware is a reasonable deterrent, but it does not encrypt the hard drive(s). This strategy can be defeated by changing the amount of RAM in the computer and zapping the Parameter RAM (PRAM). That's a good thing to know in case you ever lock yourself out. In combination with a case lock (to prevent access to changing the amount of RAM), locking the Open Firmware deters the rapid compromise of a machine. It is a best practice to do this in public access areas, open offices, or wherever unauthorized users may have access to the computer. Power Macs and recent iMacs can be secured from case intrusion with padlocks or locking cables. Older iMacs, PowerBooks, and iBooks only require a screwdriver to change the amount of RAM, defeat an Open Firmware lock, and gain boot variability to the computer. Though the Xserve has a case lock, it uses a hex key and is primarily intended to prevent accidental intrusions. Xserves are most vulnerable to physical intrusion precisely because they are expected to be protected in a secured rack and/or room. |
|


