Password Security
|
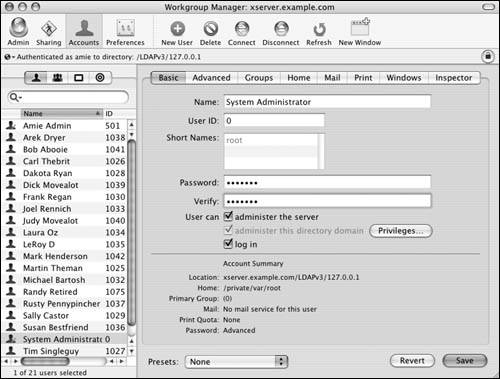
| It's unfortunate that this book must discuss this topic, but poor passwords or no passwords can lead to an insecure server. When you set up a server for the first time, you enter an initial administrator account. This account's password is also the password for the root account, which is enabled on Mac OS X Server by default. This situation presents several issues and several possible ways you can help reduce the risk of someone cracking or guessing your password. For the user's short name, use a name that's difficult to guess. For example, you might make the administrator's short name q9tr73m1. It's a combination of both letters and numbers, which makes guessing the username even more difficult. Set the password using the same complex method of combining letters and numbersboth uppercase and lowercase in this case. You can even add an exclamation point in the mix to make the password harder to guess. After the server is set up, you may wish to change the root password to something even more complex. Making the root password and the initial administrator account password different also increases security. In some circumstances, you might even disable root: for instance, if you have a server in your room, and you'd rather use sudo s as an admin to become root rather than log in directly as root. To change the root password:
|
|
EAN: 2147483647
Pages: 105