Understanding Kerberos Basics
| Kerberos provides secure authentication to a variety of network services. It also supports SSO, so users can access all of these resources by logging in just once. While extremely interesting, the background of Kerberos won't help you learn how to integrate Mac OS X with Kerberos and troubleshoot problems. Instead, let's take a look at how Kerberos works. Note To further your background knowledge of Kerberos, refer to the "References" section, at the end of this lesson. Meeting Requestor NeedsIn a directory-services environment, servers on the network provide services; then clients request those services. Requestors like Login Window or the Mail application need to authenticate file or mail servers, authorize particular tasks, and centralize password management so that each person has to remember only a single password to access all network services. That provides a better user experience, but it still does not address the fact that the password may be used on each server to authenticate the usersomething that is not in the best interest of keeping your network secure. But Kerberos addresses that issue, as well. This figure illustrates how Mac OS X leverages identification information from one source while obtaining authentication information from another source. A third source can also be leveraged for additional information required by Mac OS X. 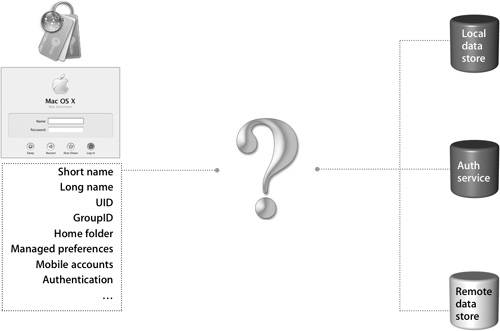 One comprehensive solution is to configure Mac OS X to use Kerberos for authentication. Kerberos provides secure authentication services using a ticket system, allowing for a seamless end-user experience. Also, Kerberos authentication works cross-platform, meaning that your Mac OS X computers can use existing Active Directory Kerberos services and vice versa, even if those services are served from another platform. That provides a tremendous level of flexibility and compatibility when configuring various services that come from different servers on different platforms. The open architecture of Kerberos permits all this to take place, regardless of whether your users exist in the Mac OS X Server Lightweight Directory Access Protocol (LDAP) database or the Active Directory domain. This piece of Kerberos, called cross-platform integration, will be explored in more detail in Lesson 9, "Integrating With Kerberos." Defining Kerberos TermsThere are three main players in a complete Kerberos transaction:
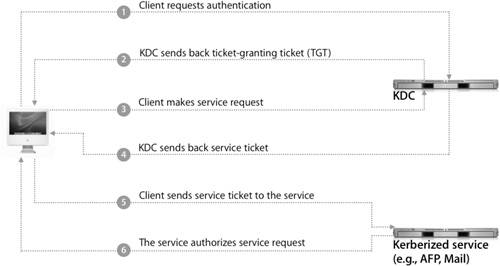
Within Kerberos there are different realms, specific databases or authentication domains. Each realm contains the authentication information for users and services, called Kerberos principals. For example, if you have a user with a long name of John Significant and a short name of johnsig on a KDC with the realm of PRETENDCO.COM, the user principal would be johnsig@pretendco.com@PRETENDCO.COM. For a service to take advantage of Kerberos, it must be kerberized, which means that it can accept tokens from a client. While the service does not talk directly to the KDC, it is an integral part of the Kerberos structure. Not only can Mac OS X Server provide a KDC when configured to host a shared LDAP directory, but it can also provide a kerberized Login Window, HTTP, Mail, File Transfer Protocol (FTP), AFP, virtual private network (VPN), XGrid, Windows (SMB), and Secure Shell Protocol (SSH) services. When a user account in the LDAP directory is configured to use the Open Directory password type (in Workgroup Manager), the keys pertaining to that user account exist solely on the KDC. Those keys are used to encrypt and decrypt any messages sent over the network. The Kerberos implementation in Mac OS X is based on Kerberos version 5 (Kerberosv5). Using KerberosWhen a computer running Mac OS X binds to an LDAP directory on Mac OS X Server, it will, by default, also bind to the Mac OS X Server KDC. Then kerberosautoconfig (located in /sbin) uses the values found in the Config attribute in any LDAP directory in the directory search path to create the configuration file, edu.mit.Kerberos, on the Mac OS X computer. However, before a user can start using kerberized services, the account must receive a ticket-granting ticket (TGT) from the KDC. When using Mac OS X Server as the KDC and using an account in the LDAP directory, the authentication process works as follows:
|
EAN: 2147483647
Pages: 258
- An Emerging Strategy for E-Business IT Governance
- Measuring and Managing E-Business Initiatives Through the Balanced Scorecard
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Governance in IT Outsourcing Partnerships
- Governance Structures for IT in the Health Care Industry