D.5 Cardholder verification mechanisms
D.5 Cardholder verification mechanisms
The cardholder verification mechanism implements the entity authentication service when the proving entity is the cardholder. A cardholder verification mechanism is intended to prove the link between the actual user of a card (or, generally , the user of a payment token) and the legitimate cardholder to which the card was issued.
D.5.1 Manual signature
Manual signature is the only cardholder verification mechanism the result of which can be assessed by a human operator, like, for example, the attendant of a POS terminal. The POS attendant asks the actual user of the card to perform a manual signature on a receipt stating the conditions of the current transaction. The attendant compares the signature of the actual user of the card against the witness signature of the cardholder written on the tamper-evident stripe added on the back side of the card. The verification is passed if the two signatures resemble . Even though this method is simple, it is always biased by the graphological skills of the attendant. The false acceptation rate (FAR), which represents the probability that a false signature passes as adequately resembling the witness signature, is greater than zero. The manual signature is still widely in use for credit cards implemented with magnetic stripe. Note that EMV ¢ allows defining the manual signature as the preferred or even the only allowed cardholder verification method for a card product [3]. However, since the FAR of the manual signature is high and since other cardholder verification methods have gained ground, the manual signature will gradually become a fallback method used for the cases when the chip, terminal, or issuer host functionality is degraded.
D.5.2 Enciphered PIN verified on-line
On-line PIN verification is the cardholder verification mechanism performed directly by the issuer host, based on the PIN typed in the terminal at the point of service during the current transaction. This mechanism is based on the comparison between the PIN image control value , which is produced from the PIN actually captured by the terminal, with the PIN image stored value , corresponding to the cardholder that is stored in the cardholders' database managed by the issuer host. The PIN image is produced with a one-way function, which can be implemented with a MAC. This CVM is suitable if there is an on-line connection between the point of service and the issuer.
The user of a payment card types the PIN into the PIN pad of an ATM or POS terminal. This PIN is transmitted from the terminal to the issuer. During its transmission, the confidentiality service is implemented with a symmetric encryption mechanism. First, the PIN pad encrypts the PIN using the transportation key TK1 known to the tamper resistant device of the terminal, which is also referred to as a SAM. After receiving this cryptogram, the SAM uses the transportation key TK1 to decrypt the PIN. Then, the SAM encrypts the PIN under a different transportation secret key TK2 . If between the acquirer, which is responsible for managing cryptographic parameters in the SAM, and the issuer of the card there is a bilateral agreement, then TK2 is accessible to the issuer's host. In this case the cryptogram containing the PIN is tunneled to the issuer's host via the acquirer's host and the card association payment network without any other conversion. Otherwise, for each different security domain the communicating parties share a separate transportation key. The cryptogram containing the PIN is decrypted and encrypted again under a different transportation key for each separate security domain it traverses: from the SAM to the AH, from the AH to the network processor of the card association, and finally from the network processor to the issuer host. Once the secure module of the issuer host decrypts the actual PIN captured at the point of service, it can produce the PIN image control value, which is compared against the PIN image stored value corresponding to the presumed cardholder, as it is stored in the cardholder database.
Appropriate key management procedures must be adopted in order to provide the suitable secret keys needed by the communicating parties. The on-line PIN cardholder verification method is widely used for magnetic stripe debit/credit payment cards operated at unattended terminals that can establish an on-line connection to the issuer host. The method is also operable with debit/credit payment cards implemented with chip cards [3].
D.5.3 Plaintext PIN verification performed by the chip card
Plaintext PIN verification is the cardholder verification mechanism based on the direct comparison between the PIN captured at the terminal with the witness PIN corresponding to the cardholder that is stored in the chip of a card [3, 15]. This cardholder verification method is suited in case the card has a chip with tamper-resistant EEPROM where the witness PIN is stored by the issuer during the personalization stage. The method is widely applied when there is no on-line connection between the point of service and the issuer ”the reason for which it is sometimes referred to as off-line PIN verification.
If the terminal environment is secure enough against eavesdropping, the terminal submits the PIN to the chip card as plaintext. After receiving it, the chip compares it with the witness PIN stored in it. If the comparison is positive, the chip card has successfully identified the cardholder, and the payment application is activated.
If the terminal environment is susceptible to eavesdropping, the terminal first encrypts the PIN and sends the corresponding cryptogram to the chip card. This cardholder verification method is referred to as off-line encrypted PIN verification. Depending on the encryption mechanism used, this cardholder verification method can have two different implementations , as explained in the following sections.
D.5.4 Symmetric enciphered PIN verification
If the terminal has a SAM where a secret PIN encryption key PEK was stored by the acquirer in agreement with the issuer, then the PIN can be securely transmitted to the card using a symmetric encryption mechanism, following the procedure described below.
Since the personalization stage, the issuer has already stored in the chip card the key PEK . When a symmetric enciphered PIN verification is performed, the card generates a random number r intended to counter replay attacks, which is transmitted to the terminal. With the participation of the SAM, the terminal encrypts the PIN with the encryption algorithm E parameterized by the key PEK (i.e., Out1 = E ( PEK )[ PIN ]). The terminal performs an XOR operation between r and Out1 , and the result is once again encrypted with the same algorithm parameterized by the same secret key PEK (i.e., C = E ( PEK )[ r XOR Out1 ]). The cryptogram C is sent to the card undergoing the cardholder verification process. After receiving C , the card decrypts it with the decryption algorithm D parameterized by PEK , obtaining C1 = D ( PEK )[ C ]. An XOR operation is performed between the result C1 and the random r (i.e., C2 = r XOR C1 ). Finally, the card applies once more D parameterized by PEK to C2 in order to obtain PIN = D ( PEK )[ C2 ]. This value of the decrypted PIN is compared to the witness PIN stored in the chip, and if the comparison holds "True", the user of the card is the legitimate cardholder.
D.5.5 Asymmetric enciphered PIN verification
If the acquirer managing the terminal has not established an agreement with the issuer of the card, then the PIN can be securely transmitted from the terminal to the card following the procedure described below.
Referring to Figure D.1, assume that the sender is a payment terminal and the receiver is a chip card. The cardholder types in the PIN using the PIN-pad of the terminal, which has to transmit it to the chip card for performing locally the cardholder verification. Since the issuer of the card and the acquirer responsible for the management of the terminal did not establish a business relationship beforehand, there is no symmetric key stored in the terminal that has a correspondent in the chip card. But the issuer has generated in connection with the card a pair public encryption key/private decryption key, ( KE card , KD card ), and has certified the public encryption key KE card with a CA, recognized as a TTP by both the issuer and the acquirer. This certificate Cert CA ( KE card ) provides the authenticity of the public encryption key KE card and the fact that it is linked to the card. (Note that certification is discussed in Section D.4.) The issuer has downloaded the key pair and the corresponding certificate in the card during the personalization stage. The issuer does not trust the environment where the terminal is installed and assumes the eavesdropping threat, requiring the encryption of the PIN during its transmission from the terminal to the card. Moreover, the replay threat is also considered , since an attacker could register the cryptogram containing the PIN and later retransmit it to the card. In this case the following steps describe the protocol established between the card and the terminal, which is schematized in Figure D.5:
-
The chip card generates a random number r , called a challenge, and transmits it together with the public encryption key of the card KE card and its certificate Cert CA ( KE card ) to the terminal.
-
The cardholder types in his or her secret PIN using the PIN-pad of the terminal. The terminal verifies the authenticity of the certificate Cert CA ( KE card ). If the verification passes, the terminal uses the key KE card for the encryption of a message consisting of the concatenation of the PIN, the confidentiality of which is to be protected, and the challenge r , which guarantees that each execution of the protocol is unique, countering eventual replay attacks. The inclusion of the random r in the cryptogram also protects against mounting a dictionary attack, since the PIN is chosen from a restricted domain and the cryptogram is produced with a public key. It results in the cryptogram C = E ( KE card ) [PIN r ], which is sent to the chip card.
-
Using the private decryption key KD card , the chip card computes M = D ( KD card )[ C ]. The last significant part of M is compared against r to check that the received cryptogram is not replayed from a previous execution of the protocol. The most significant part of M is compared against the PIN stored in the card since the personalization stage. If the comparison is positive, the cardholder is considered legitimate by the card's payment application.
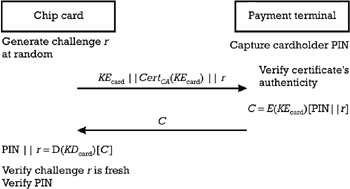
Figure D.5: PIN encrypted with a public key cryptosystem.
D.5.6 Cardholder verification based on biometrics
Biometrics represents another possible cardholder verification mechanism. Instead of using a PIN to locally identify the cardholder at the point of service, the cardholder's biometrics can be used instead, through comparing the biometrics captured at the terminal with the corresponding digitized witness stored in the card since the personalization stage. Suitable biometrics include fingerprints , hand geometry, retina diffraction features, voice recognition, and face recognition. An important advantage is that biometrics cannot be forgotten, stolen, or forged. The FAR, however, representing the probability that an attacker is accepted as the legitimate cardholder, and the false rejection rate (FRR), representing the probability that the legitimate cardholder is rejected, are greater than zero. (In this context it is worth noticing that the FAR and the FRR for the plaintext/enciphered PIN verified either off-line or on-line are also grater than zero, even though they have the smallest false rates among the cardholder verification mechanisms.) When this disadvantage is combined with the high price of terminals including a biometrics reader, one can see why, at present, there is no encouraging business case for biometrics, at least in electronic payment systems. It is also important to mention that an attacker that successfully recorded the biometrics captured by a terminal during its transmission to the chip card for comparison can mount any attack as those described for a wiretapped PIN. In order to avoid this attack, several projects were launched for adapting the biometrics reader directly on the card. This is actually the case for fingerprints, which becomes the favorite biometrics for this type of cardholder verification mechanism.
EAN: 2147483647
Pages: 131