Defining Autonomy, Collaboration, and Isolation
We define a security boundary as a container that cannot be controlled by any higher-level or outside accounts. The administrators for the container do not have to worry that another account can compromise the security of the container and the objects contained within it. Because an outside account can affect the objects and configuration of a domain, the forest becomes the security boundary within the Active Directory structure. The forest root contains accounts that can affect any domain within the forest. Members of the Domain Admins group from the forest root domain have the ability to add accounts into the Enterprise Admins and Schema Admins groups, giving those accounts the ability to make changes that could affect other domains and the configuration of the entire forest.
Active Directory forests and domains are built based on the administrative needs of the organization. For some organizations, all of the resources are controlled by a central group of administrators. Some organizations have identified services and objects that need to be controlled by groups within the organization and have other groups who need rights delegated to them. Still other organizations may require complete isolation of services and resources between divisions. These administrative needs are defined as collaborative , autonomous , and isolated models.
Understanding Collaborative Administration
Although every administrator may not have the same level of control, as a whole, they are able to support all of the services and data for the organization. This has been identified as the collaborative model of administration. This is usually the model you find with a single domain, although you can implement a multiple domain design and allow collaborative administration to be delegated throughout.
Service and data administrators in this design share administrative responsibilities with other administrators. The domain owners have complete control over all of the services and resources within the domain. Delegation of control over the objects within the domain is granted to the data administrators, although in some cases, the service administrators are the only data administrators. Collaborative administration is found in most small companies where a single administrative group is responsible for controlling the objects within Active Directory and making sure it is available for use.
The collaborative model is not restricted to the single domain model, however. Although the single domain model is the easiest to implement collaboration, you can put the mechanisms in place to allow collaboration between domain and forests. For example, if a forest has multiple domains due to security policy requirements, the administrative staff from both domains can be added to the built-in groups that have administrative rights in the other domain. This grants the administrators from both domains the ability to control objects from either domain. Figure 3.1 shows an example of two forests with administrators from each having delegated control. You can see that the Domain Admins global group from both forests has been added to the Administrators domain local group within each domain.
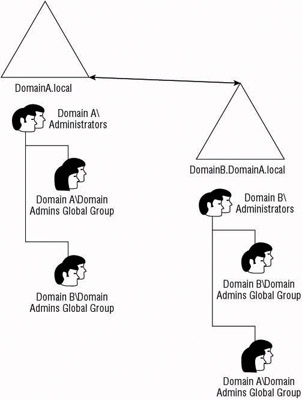
Figure 3.1: Domain administrative collaboration
Collaboration within a multiple forest design is much more difficult, however. Because the two forests do not share the same schema and do not share information between global catalogs, assigning rights between them is difficult. Products such as Microsoft s Identity Integration Services can help tie the forests together until they can be merged. Figure 3.2 is an example of two forests tied together with a forest trust relationship. In this one-domain-per-forest example, members of the Domain Admins global group from each domain have the ability to manage objects from the other domain. If any child domains exist in either domain, you need to consider another solution.
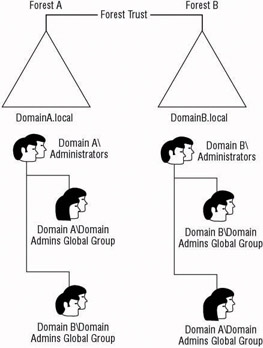
Figure 3.2: Forest administrative collaboration
Understanding Autonomous Administration
The autonomous method of administration identifies the administrators who need to have access to the services and resources for which they are responsible but denies access to others. You usually find this type of administration when you are designing a multiple domain forest or a single domain where specific rights and permissions have been delegated to the service or data administrators at the OU level. Autonomy does not isolate the administrative staff, however. A high-level account that can take control of services or resources is always available. In a forest, that account is the Enterprise Admins group by default, although you can create and delegate control to other groups.
You can delegate service autonomy at the domain level. If you have found a reason why a portion of Active Directory needs a specific group of administrators to manage the domain controllers, you can create a domain for them. Once they have been given their own domain, the service administrators can add and remove domain controllers, control the organizational unit (OU) structure, change the security policy requirements, and control how the domain is structured. The domain administrators need to accept the fact that this is not isolated control however; forest root administrative group accounts will still have the power to control the domain and affect the changes they put into place.
Within a domain, the Domain Admins global group has control over all of the OUs within the domain, and other groups can be delegated control over the OUs if they need to manage them. This is known as data autonomy . Those administrators who need to make changes to objects within Active Directory, or work with the resources that need to utilize Active Directory, can have a domain created for them, or they can have delegated access to OUs.
Figure 3.3 shows a forest with domains that are created for data or service autonomy. You will notice that the two child domains within the forest have their own administrative groups and neither of the administrative groups belong to the forest root. This safeguards the services and data within each of the domains from administrators in the other domain. If the forest root were to hold the service and data administrators for either of these divisions of the company, the service administrators from the forest root would have control over the resources of the other division. As it stands now, a separate administrative body controls the forest root and grants the divisions autonomy from each another.
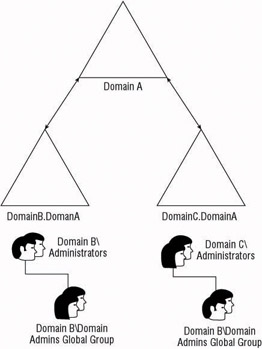
Figure 3.3: Domains built for data or service autonomy
This method of administration is usually found in the decentralized or hybrid administration models. With the decentralized model, you can create domains and delegate administrative control to those administrators who are responsible for their own partition of the directory service.
Understanding Isolated Administration
When you use the isolated administration model, you are essentially creating separate sandboxes where the administrators are selfish and won t share their toys. Although this is a harsh view of the isolated model, it accurately defines how this model functions. With this model, services and data administration needs to be performed by one administrative group and no other group should have any access whatsoever. Although this may seem like a drastic measure to take, some business practices require isolation of services and data.
If data isolation is required, the services that provide the data are also isolated. In this case, the data administrators need to take on the responsibility of the service administrator. This design may require additional staff or additional training for the administrators. Weigh the costs associated with isolation against the reasons for implementing isolation. Political reasons and posturing between departments and divisions within the organization may not be valid reasons, but legal requirements imposed by regulatory commissions are. Figure 3.4 shows an example of a forest created for service isolation.
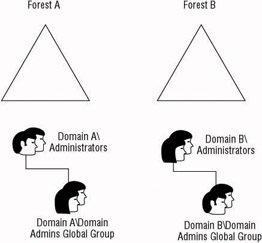
Figure 3.4: Forest designed for isolation
Look back at Chapter 1, Analyzing the Administrative Structure; there we presented the decentralized model and discussed some of its merits and drawbacks. If you need to implement complete decentralization of resources, and those resources should not be controlled by any other administrator, you need to isolate those resources into their own forest. Again, this is a drastic measure and you should investigate other options first.
| |
Cargo Container Cartage is a national delivery firm that has offices in 32 states. They have identified a need to keep each office s administration separate. However, they want to make sure that all of the offices are under the control of the national headquarters office located in St. Louis. Each of the regional offices will have an administrative staff that will be responsible for maintaining their own users and resources. All offices are interconnected via T1 connections using the national headquarters as the hub site. Currently none of the T1 links are being used at more than 30 percent capacity.
-
Question: Using the information provided, determine what type of administrative model is being used. Answer: The administrative model is a hybrid model because the administrators at the headquarters have ultimate control over the resources and the local administrative staff at the regional sites have the ability to control their own resources.
-
Question: Who are the forest owners? Answer: The administrators at the national headquarters.
-
Question: Who are the OU owners? Answer: The regional administrators.
| |
EAN: 2147483647
Pages: 159