Understanding the Administrative Structure: AdministrationModels
Whereas the business models define how a business is organized to perform tasks , the administration models define how the resources are organized, controlled, secured, and accessed. The four administration models are
-
Centralized administration model
-
Decentralized administration model
-
Hybrid administration model
-
Outsourced administration model
Each is supported by Active Directory, with its own advantages and disadvantages.
Identifying the Centralized Administration Model
The centralized administration model is the administrative model that most companies strive to achieve. With the centralized administration model, a core administrative group controls all of the IT assets at one central location.
Although this is the model that many companies wish they could implement, many find that they cannot for several reasons. Whether it is due to business, legal, or cultural reasons, some companies have found that this model will not fit within their organization. For example, some companies provide services or products to military divisions of our government. When these defense contracts are given out, the company that receives the contract must abide by national security regulations. Some of these regulations require that the division to whom the contract was awarded be completely isolated from the rest of the company. This keeps the information safeguarded from those individuals who do not need access to the information. This also means that the administrators of this information will probably need to be isolated from the rest of the company.
Two different structural models exist on which centralized administration is built: centralized administration with centralized resources, and centralized administration with decentralized resources. Both of these pose their own challenges and have definite advantages and disadvantages.
The Centralized/Centralized Approach
The inherent nature of the centralized administration with centralized resources model does not allow for very much flexibility. If a company has a single location with all of the employees accessing the resource from a central location, this is not a problem. As companies grow, merge with, and acquire other companies, the ability to keep all of their assets centralized becomes a challenge. Most companies find that, to reduce costs and ease administrative problems, they have to move to one of the other models discussed later. Figure 1.4 shows a simple version of this approach with all of the resources located at the Chicago office.
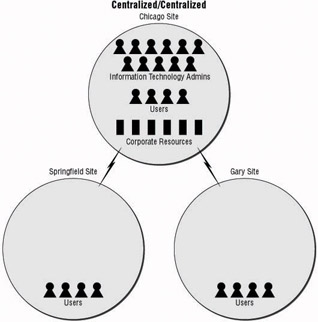
Figure 1.4: Centralized administration with centralized resources
One big advantage of the centralized resources approach is that it is easy to administer. With all of the assets based at one location, administrators have all of the systems at their fingertips. Whenever a security update or a system patch needs to be applied, the systems are close by. Because all of the systems are geographically close to one another, communication problems are usually not an issue. In a local area network, the systems should have plenty of available bandwidth in which to communicate and share data.
The Active Directory design for the centralized/centralized approach is usually an easy one to decide upon. Because the resources are centralized and the administrative staff is usually grouped together, a simple, single forest design usually containing a single domain will suffice. Of course, other design criteria will come into play and may change the forest and domain structure, but it is best to start simple and add complexity as necessary.
The Centralized/Decentralized Approach
When companies discover that centralizing their resources is not efficient, they may want to decentralize their resources, yet maintain a centralized administration group. Whereas this option may not have seemed feasible as few as 10 years ago, advances in remote control administration and system automation have made this administrative model very intriguing. Figure 1.5 shows an example of an organization using this approach.
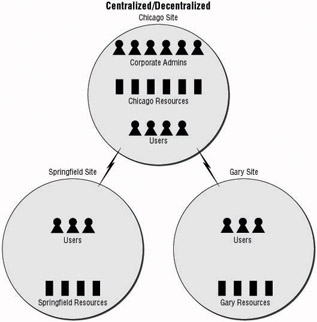
Figure 1.5: The centralized administration/decentralized resources approach
Let s face it, an administrator no longer has to be sitting in front of the system to work with it. Tools as simple as the snap-ins for the Microsoft Management Console (MMC) have made it possible for us to control systems that are located in different cities, states, or countries . Where some of the snap-ins have limitations, other administrative utilities come into play allowing us to remotely administer a system. Microsoft s Terminal Services is a shining example of a remote administration tool. Once the Terminal Services client is started and connects to the remote server, the administrator can perform nearly every task they could perform from a local machine. The only exception is when the administrator needs to physically replace a device or switch out removable media. And now that terminal services allows the client to connect to the console session, a remote administrator can view what is happening on the server and view any messages that may appear within the console session.
Automation tools also make an administrator s job easier and facilitate controlling remote systems from a central location. From backing up servers at predetermined times, to automating the installation of software, these automation tools end up paying for themselves .
Administrators no longer have to travel to the physical location of the system in order to perform most tasks. A good example of this is utilizing Group Policy objects (GPOs) to automate software installation on a client computer or to set security requirements on a server.
The main drawback to the centralized/decentralized method stems from the fact that the administrative staff is geographically distant from the resources. If something happens to a server, the staff has to travel to the location where the resource is located in order to work on it. This means the staff will encounter times when the resource could be offline for an extended amount of time. Due to this reason in particular, companies will not adopt the centralized/ decentralized model and will instead opt to use a different approach to administration. In the next section, you will find the administration theory that is the polar opposite to the centralized administration model.
Identifying the Decentralized Administration Model
Whereas the centralized model uses a core administrative group that resides in one location, the decentralized administration model spreads the administrators out around the organization to take advantage of controlling the resources at their source. An example of the decentralized model is seen in Figure 1.6. Instead of having to rely extensively on remote control or automation software, the administrators have local access to the systems they administer. Although this allows a company to have administrators located close to the systems where they can respond to problems immediately, it adds to the cost of administration. Another thing to consider is that if your organization is spread across multiple time zones, you may need to decentralize your administration. Although some companies run their data centers 24 hours a day, those that do not will need to identify whether or not they want to place administrators in those locations where the resource resides.
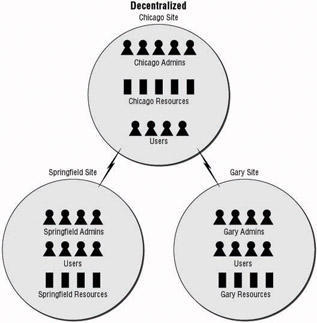
Figure 1.6: The decentralized administration model
Employees are an expensive resource. However, some companies need to have their data available at all times, and having an administrative staff available to take care of any problem that may arise might be a small price to pay. Decentralized administration can prove a little more difficult when designing your Active Directory and network infrastructure. The delegation of administrative control takes more planning than having a centralized group that is responsible for administration. Replication of Active Directory information among the systems takes a toll on the network bandwidth, especially when wide-area connections are concerned .
Identifying the Hybrid Administration Model
As most large companies have found, neither of the previous administrative models fits within their organization. The centralized model is far too restrictive , and response time for problems may take too long. The decentralized model allows too many administrators to have too much control across the board. The hybrid model alleviates some of these issues.
Two different methods may be employed to take advantage of the hybrid model. The first, seen in Figure 1.7, keeps most of the administrative staff centralized where they control the majority of resources, while taking advantage of a technical support staff that has the authority to work with the remote systems. These remote administrators do not have control over system policies or corporate resources. This approach allows the central staff to control all of the systems where required and a remote staff to maintain systems, perform backups , and troubleshoot issues that arise.
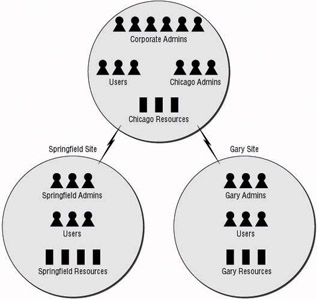
Figure 1.7: Hybrid administration model for delegation of remote resources
The second hybrid administrative method has a decentralized staff that is responsible for completely administering the systems at their locations. They have control over the users, client systems, servers, printers, and all other resources, but they will not have control over the corporate standards. Control over the standards is centralized at the corporate IT headquarters, as seen in Figure 1.8. All of the remote administrative staff will have to follow the standards as they are enforced using tools such as Group Policy.
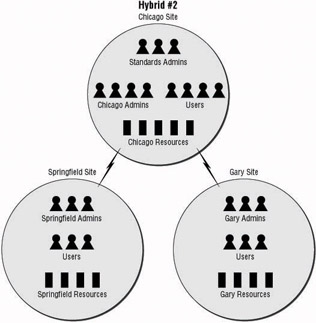
Figure 1.8: Hybrid administration model for control of corporate standards
Designing an Active Directory and network infrastructure for a hybrid administrative group can be tough, yet rewarding . You need to make sure that the correct administrators have the required level of permissions for the resources they need to administer, and the correct rights to perform the tasks for which they are responsible. All the while, they should not have the right to make changes to the system policies that control and maintain the Active Directory requirements. At the same time, the central administrative group needs to have the rights to maintain the system policies that govern resource access and control.
Identifying the Outsourced Administration Model
In many companies, outsourcing the administrative staff is not an option. These companies want to have complete control over their administrative staff. They do not want to entrust their systems to employees from an outside organization, even though the outside organization may have employees who have up-to-date skill sets. For some companies, the security risks are not worth the trade-off.
For other companies, the ability to bring in employees who have a skill set that they need becomes a positive thing. The company does not have to incur the immediate expense of trying to train the employees, and the outsourced administrator can bring a skill set in that may train the current employees on a new technology.
Other companies will utilize an outsourced staff so that they can reduce costs. Paying an outside firm to provide administrative resources allows a company to use the skill sets of individuals who have been trained, but also keep their own employee costs at a minimum. Figure 1.9 shows an example of using outsourced staff to provide administrative control. Human resources are expensive, not only because of the salary they draw, but because benefits they receive can cost the company quite a bit of money.
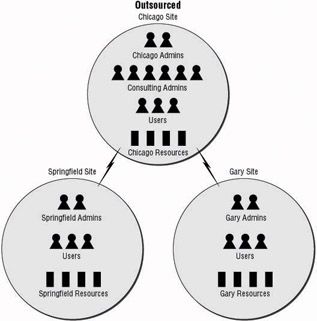
Figure 1.9: Outsourced administration model
The outsourced administration model has some drawbacks. Depending on the contract that is drawn up, the outsourced employee may not be dedicated to your company. They may have other companies that they are working with, and the time that is allocated to your company may be limited. Even if the outsourced employee is dedicated to your company, they may have specific tasks and functions that they are allowed to do and not do.
When you are designing Active Directory and the network infrastructure to take advantage of the outsourced model, remember that security is an utmost priority. The process of delegating the responsibilities the administrators need while securing those resources that they should not have access to needs to be addressed. A good Active Directory design allows you to segregate the resources so that access to them is restricted. However, be aware that if you are using this model, one of the main reasons for using it is to take advantage of expertise that you may not have had in your own organization. Make sure you trust the company that is providing the outsourcing.
In the Identifying the Administrative Model Design Scenario we are going to take a look at an organization and determine which of the administrative models are in use.
| |
Eclectic Importers headquarters is located in San Francisco, California. They have 22 regional offices throughout the United States and 5 foreign offices. Each of the offices has its own staff that is responsible for the systems at their location. None of the offices has any control over the other offices resources. The corporate headquarters does have ultimate control over all of the resources at all of the locations worldwide.
-
Question: Which administrative model is in use at Eclectic Importers? Answer: Having an administrative staff at each location that is responsible for the resources located at that location falls under the decentralized administrative model. However, because the corporate administrative staff has full control over all of the resources from the headquarters, this model falls under the hybrid administrative model.
| |
| |
Franklin County Memorial Hospital (FCMH) decided to cut costs associated with the IT department. One method of achieving this goal involved implementing Citrix MetaFrame XP. This option allowed them to centralize their applications on several servers located in the data center and then utilize thin client workstations. They identified nurses stations and doctors terminals at this point, which reduced the number of backup workstations they needed to implement. The only problem came at system rollout, when they found that they were under-staffed.
Because the current staff was already overburdened with the normal day-to-day activities, FCMH decided to outsource the design, planning, and implementation of the new system. Once the system was put into place, the hospital kept these administrators on to keep the system working efficiently until the staff could be trained to take over their tasks.
| |
EAN: 2147483647
Pages: 159