15.5 NEED FOR LAYERED APPROACH AND PROTOCOL STANDARDS
|
| < Day Day Up > |
|
15.5 NEED FOR LAYERED APPROACH AND PROTOCOL STANDARDS
A protocol can be defined as a set of conventions between two entities for communication. As discussed in the previous section, many protocols are required in computer communication to tackle different issues. One way of achieving computer communication is to write monolithic software for all the protocols to be implemented. This approach, being not modular, leads to lots of problems in debugging while developing the software and also in maintenance. On the other hand, a "layered approach" leads to modularity of the software. In a layered approach, each layer is used only for some specific protocols. Layered approach has many advantages:
-
Every layer will perform well-defined, specific functions.
-
Due to changes in the standards or technology, if there are modifications in one layer's functionality or implementation, the other layers are not affected and hence changes are easier to handle.
-
If necessary, a layer can be divided into sub-layers for handling different functions (as in the case of LAN).
-
If necessary, a layer can be eliminated or by-passed.
-
If the protocols for different layers are based on international standards, software or hardware can be procured from different vendors. This multi-vendor approach has a major advantage—because of the competition among the vendors, the prices will be competitive and in the bargain, the end user will be benefited.
| Note | In Local Area Networks, the datalink layer is divided into two sub-layers viz., logical link sub-layer and medium access control sub-layer. A LAN need not have the network layer at all. This type of flexibility is provided by the layered approach to protocol development. |
However, while deciding on the number of layers, the following points need to be kept in mind:
-
If the number of layers is high, there will be too much protocol overhead. Hence, the number of layers should be optimized.
-
The interfaces between two adjacent layers should be minimal so that when a layer's software/hardware is modified, the impact on the adjacent layers is minimal.
For each layer, as shown in Figure 15.5, there will be: (a) service definition that specifies the functions of the layer (b) protocol specification that specifies the precise syntax and semantics for interoperability, and (c) addressing or service access point to interface with the higher layer. These three form the specifications of the protocol layer. International bodies such as International Organization for Standardization (ISO) and Internet Engineering Task Force (IETF) standardized these specifications so that any equipment vendor or software developer can develop networking hardware/ software that will interoperate.
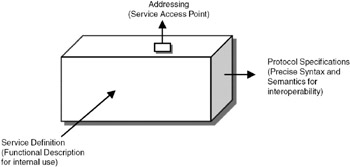
Figure 15.5: Specification of the protocol layer.
The layered approach to protocol development is a very important concept. Each layer does a specific job and interfaces with the layers above and below it. This results in modular development of protocols for computer communication.
To make two computers talk to each other, we run the layered software on both computers. As shown in Figure 15.6, each layer interacts with the layer above it and the layer below it. It also communicates with the peer layer in the other machine. Each layers provides defined services to the layers above and below it.
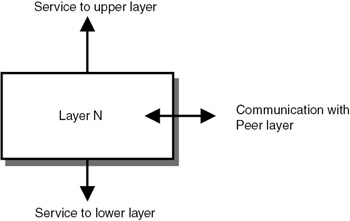
Figure 15.6: Layer's services and protocols.
For computer communication, the layered approach has been well accepted, and the ISO/OSI protocol suite and the TCP/IP protocol suite follow this approach. The ISO/OSI protocol suite is a seven-layer architecture, whereas TCP/IP is a five-layer architecture. The beauty of the layered architecture will be evident when we study the ISO/OSI protocol architecture in the next chapter.
The two important layered architectures for computer communication are: ISO/OSI architecture in which there are 7 layers and TCP/IP architecture in which there are 5 layers.
Summary
In this chapter, we studied the important concepts of packet switching. Packet switching is fundamental to computer networking. In packet switching, the data to be sent is divided into small packets, and each packet is transmitted over the network. In a virtual circuit, the route to be taken by each packet is determined before the data transfer takes place. In a virtual circuit, there will be three phases—call setup, data transfer, and call disconnection. ATM, Frame Relay, and X.25 based networks are based on a virtual circuit. In datagram service, each packet is handled independently, and hence, there is no call setup and call disconnection. The Internet uses datagram service.
We also studied the various issues involved in developing computer networks. Coverage area, services to be provided to end users, computing platforms (hardware and operating systems), error control, flow control, addressing, signaling, networking of networks, real-time communication, segmentation and reassembly, congestion control, and network management are the main issues to be handled. To address all these issues, protocols need to be developed for making computers talk to each other. We introduced the concept of the layered approach to computer networking. Instead of handling all the issues together, each layer can handle specific functions so that the software/hardware for making computers talk to each other can be developed in a modular fashion.
References
-
50th Anniversary Commemorative Issue of IEEE Communications Magazine, May 2002. This issue contains excellent articles on the history of communications as well as the papers that have influenced communications technology developments during the past 50 years.
-
Larry L. Peterson and Bruce S. Davie. Computer Networks: A Systems Approach. Morgan Kaufmann Publishers Inc., 2000. A systems approach rather than a layered approach to computer networking makes this book very interesting.
-
http://www.acm.org The Web site of the Association for Computing Machinery (ACM). If you are a member of ACM, you can access the online education portal, which gives excellent tutorials on different aspects of computing, including computer networks.
-
http://www.computer.org The Web site of the IEEE Computer Society. If you are a member of the IEEE Computer Society, you will have access to excellent online educational material on computer networking.
-
http://www.ieee.org The Web site of IEEE, the largest professional body of electrical and electronic engineers. This site provides access to many standards developed by IEEE on computer networks.
Questions
-
What is packet switching? As compared to circuit switching, what are its advantages and disadvantages?
-
Explain virtual circuit service and datagram service. Compare the two services in terms of quality of service provided, reliability of service provided, and implementation complexity.
-
If you connect two PCs using a point-to-point link, what are the issues involved in providing various applications such as file transfer, chat, and e-mail?
-
When you connect three or more PCs in a network (as a local area network), list the additional issues involved for providing the applications in Question 3.
-
What is the fundamental concept in a layered approach to computer networking? Discuss the pros and cons of developing monolithic software for each application (for file transfer, e-mail, etc.).
Exercises
| 1. | On the local area network installed in your department/organization, find out the address of the computer on which you are working (it is called the IP address). | |
| 2. | When you access a Web site through a browser, you get a message "Connecting to" followed by the IP address of the Web server. What is the use of this address to you? Is it necessary that this address be displayed at all? Discuss. | |
| 3. | The Ethernet LAN uses a maximum packet size of 1526 bytes. An X.25 network uses a maximum packet size of 1024 bytes. In both cases, the packet size is variable. Discuss the pros and cons of having variable size packets as compared to fixed size packets. | |
| 4. | ATM uses a fixed packet size of 53 bytes. This is a small packet as compared to Ethernet or X.25 packet sizes. Discuss the merits and disadvantages of having small fixed size packets. | |
Answers
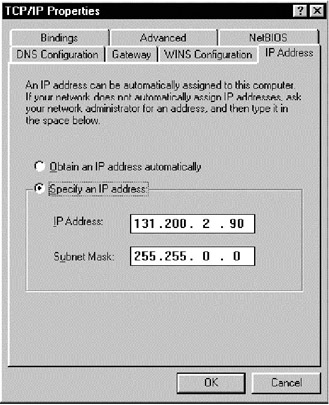
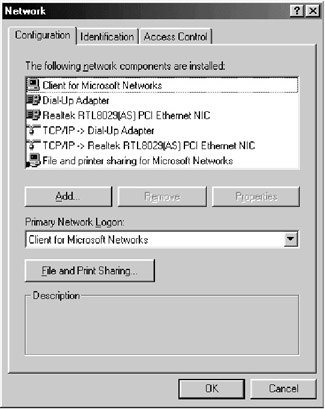
| 1. | Every computer is given an IP address. The IP address is generally assigned by your system administrator. The screen that displays the IP address of a PC is shown in Figure C.8. To obtain this screen, do the following:
|
| 2. | When you access a Web site through a browser, the Domain Name Service of your Internet service provider gives the IP address of the origin server in which the resource is located. Then the TCP connection is established between the client and the origin server. When you see the message Connecting to followed by the IP address of the Web server, it is an indication that the DNS of your ISP has done its job. If the DNS is down, you will not get this message and will not be able to access the URL. Note that the DNS may be working, but still you may not be able to access the resource if the origin server is down. |
| 3. | The Ethernet LAN uses a maximum packet size of 1526 bytes. X.25 network uses a maximum packet size of 1024 bytes. In both cases, the packet size is variable. Variable packet size leads to more processing by the switches. Also, the switches should have variable size buffers. However, if large size packet is negotiated, data transfer is fast, and protocol overhead is less. Fixed-size packets certainly can be switched much faster. In Asynchronous Transfer Mode (ATM) networks, fixed-size packets are used. |
| 4. | ATM uses a fixed packet size of 53 bytes. This is a small packet compared to Ethernet or X.25 packet sizes. The small size causes fast packet switching and fixed size buffers at the switches. The only disadvantage is slightly higher overhead. Out of the 53 bytes, 5 bytes are for header information. |
Projects
-
Install Microsoft NetMeeting software on two systems connected over a LAN in your department/laboratory. Run the NetMeeting application and try different services provided by this application (audio conferencing, video conferencing, white board, etc.)
-
Search the Internet to find various sites that provide free networking software source code with which you can experiment. (You can try the open source sites that provide Linux-based networking software.)
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 313