Using Digital Signatures and Encryption
| < Day Day Up > |
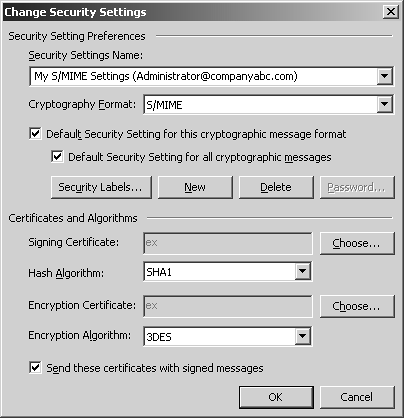
| Secure/Multipurpose Internet Mail Extensions (S/MIME) is used to digitally sign and encrypt messages. Digital signatures provide authentication, nonrepudiation, and data integrity; encryption keeps message contents confidential. NOTE S/MIME for Outlook 2003 and OWA can work with an organization's (for example, Windows Server 2003 Certificate Services) or outsourced Public Key Infrastructure (PKI) solution. The following sections on S/MIME assume that a PKI is in place. For information on implementing PKI for Exchange Server 2003, refer to Chapter 12, "Server-Level Security." Simplified Fundamentals of Using Digital Signatures and EncryptionDigital signatures and encryption are fundamental components to S/MIME. S/MIME is in turn a small subset of PKI which has a large reach into many different security facets. For instance, PKI supports smart cards, SSL, user certificates, and much more. For the purposes of this chapter it is important to have an understanding of S/MIME and how it can be used to secure the messaging environment. X.509 is a digital certificate standard that defines the format of the actual certificate used by S/MIME. The certificate identifies information about the certificate's owner and includes the owner's public key information. X.509 is the most widely used digital certificate and therefore has become the industry standard digital certificate. PKI products, such as Microsoft's Certificate Services included in Windows Server 2003, are products that generate X.509 digital certificates to be used with S/MIME capable clients . The Signing ProcessWhen a user chooses to sign a message, a random checksum is generated from and added to the message. The random checksum is the digital signature (also known as a digital ID). This signature is then encrypted using the user's private signing key. The user then sends the message to the recipient that includes three items: the message in plain text, the sender's X.509 digital certificate, and the digital certificate. The recipient then checks its Certificate Revocation List (CRL) to see whether the sender's certificate is on the list. If the certificate is not on the list, the digital signature is decrypted with the sender's public signing key. If it is on the CRL, the recipient is warned that the sender's certificate has been revoked . Remember that the digital certificate included the sender's public signing key. The recipient's client then generates a checksum from the plain text message and compares it to the digital signature. If the checksums match, the recipient knows the sender is the one who sent the message. If they do not match, the recipient is warned that the message has been tampered with. The Encryption ProcessWhen a user chooses to encrypt a message, the client generates a random bulk encryption key that is used to encrypt the contents of the message. The sender then uses the recipient's public key to encrypt the bulk encryption key. This is referred to as a lockbox . If there are multiple recipients for the message, individual lockboxes are created for each recipient, using his or her own public encryption key. The contents of the lockbox (the bulk signing key) are the same, however. This saves the client the overhead of encrypting the message multiple times and still ensures that the message contents stay secure. For this process to work, the sender must have a copy of the recipient's digital certificate. The certificate can be retrieved from either the Global Address List (GAL) or the sender's Contact list. The digital certificate contains the recipient's public encryption key, which is used to create the lockbox for the bulk encryption key. When the recipient receives the message, he will use a private encryption key to decrypt the lockbox that contains the bulk encryption key used to encrypt the message contents. The bulk encryption key is then used to decrypt the message. Configuring Outlook 2003 for Secure MessagingTo configure Outlook 2003 clients for secure messaging, do the following:
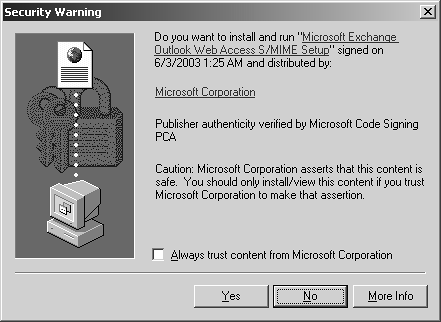
Configuring OWA for Secure MessagingEarlier versions of Outlook supported digital signatures and encryption, but OWA did not. The Exchange Server 2003 OWA version now supports these S/MIME features, using an S/MIME ActiveX control. Users can download the S/MIME ActiveX control from Exchange Server 2003 by clicking on the Download button under the E-mail Security section on the OWA Options page. Two windows prompt the user to accept or decline the installation and execution of the S/MIME ActiveX control, as illustrated in Figure 11.11. Simply selecting Yes to both of these prompts allows the user to enable S/MIME. Figure 11.11. Accepting S/MIME certificates. To configure default S/MIME settings for OWA, do the following:
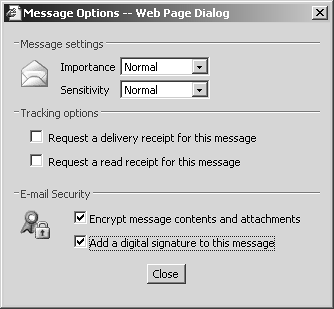
If these options are left unchecked, the OWA user can still use S/MIME on a per message basis. Sending Secure MessagesTo configure S/MIME on a per message basis in Outlook 2003, do the following:
To configure S/MIME on a per message basis in OWA, do the following:
TIP The easiest way to enable secure messaging with users outside of the Exchange 2000 organization is to send the user a digitally signed message. Outlook 2000 and later sends a copy of the sender's certificate with any signed message by default. The recipient of the signed message can then add the sender and certificate to the Contacts folder. When users receive an encrypted message they need to enter their security password to decrypt the message. |
| < Day Day Up > |
EAN: 2147483647
Pages: 393