Tips and Tricks for Hardening Windows
| < Day Day Up > |
Tips and Tricks for Hardening WindowsExchange Server 2003 and its client counterparts are only as secure as the underlying operating system that supports them. The good news is that by default both Windows Server 2003 and Windows XP Professional are more secure than any other Windows operating system. Despite this fact, default installations are not going to magically secure any environment, so security customizations are almost always going to be recommended. NOTE Entire books have been dedicated to securing Windows operating systems, so it is unrealistic to assume that this chapter can thoroughly examine allor even mostof the critical security policies, methodologies, and practices that should be considered for implementation in order to protect the network environment. Securing Windows Server 2003 or Windows XP Professional can be broken down into smaller, more manageable components , includingbut not limited toauthentication, access control, patch management, and communications. Organizations of all sizes should at least take these focal areas into consideration, especially when implementing new services or technologies. Windows Server 2003 Security ImprovementsOut of the box, Windows Server 2003 reduces its attack surface, making it more difficult from the start to gain unauthorized access. This reduction in the attack surface area stems from many improvements, includingbut not limited tothe following:
Windows XP Professional Security ImprovementsWindows XP Professional complements Windows Server 2003 from the client-computer perspective and supports the security features that are built in to Windows Server 2003. Among the notable security improvements built into Windows XP Professional are:
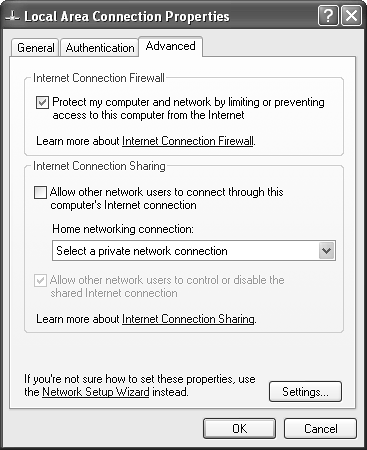
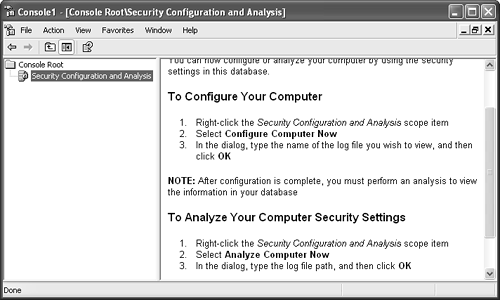
Internet Connection Firewall ProtectionExchange Server 2003 for many environments is intended to provide access to messaging anytime and virtually anywhere . Many users must securely access their mail from not only corporate office locations but also from hotels, client sites, and other locations. As a result, users are often more susceptible to viruses and intrusions. To minimize security risks, client computers should have the Internet Connection Firewall (ICF) enabled (as shown in Figure 11.1), especially when they are directly connected to the Internet. Figure 11.1. Enabling ICF to protect Windows XP. As the name implies, ICF serves as a firewall for a single computer or a group of computers if the computer with ICF is also running Internet Connection Sharing. More specifically , ICF uses stateful packet inspection to monitor all communications to and from the computer and records which traffic originates from the computer or computers it is protecting (that is, outbound traffic). Consequently, ICF allows outbound traffic while stopping unsolicited inbound traffic. Standardizing Security with Security TemplatesSecurity templates are a practical and effective means to standardize an environment on security policies and configurations. These security templates can be customized to adhere to security requirements of the organization, and these security templates can be applied to client computers as well as to servers using the Security Configuration and Analysis Microsoft Management Console (MMC) snap-in. TIP Microsoft provides several security templates based on functional roles within the network environment that can easily be applied to client computers and the server. However, as a best practice, always customize the security template to ensure that application and operating system functionality is not broken or negatively affected. This not only ensures that computers are identically configured with the same security configurations, but it also is an easy way to configure appropriate security measures for those computers that are not managed using Group Policy Objects (GPOs). Using the Security Configuration and Analysis ToolThe Security Configuration and Analysis tool, shown in Figure 11.2, is a utility that can apply security templates to computers. It compares a computer's security configurations with a security template. When the computer's security configuration does not conform to the settings in the security template, it can be used to apply the modifications and standardize the computer's security configuration. Figure 11.2. Using the Security Configuration and Analysis tool. This utility has two modes of operation; analysis and configuration. It is always a good idea to analyze the computer prior to making any modifications, because it enables administrators to manually compare the differences and select which settings to change. To analyze a computer, do the following:
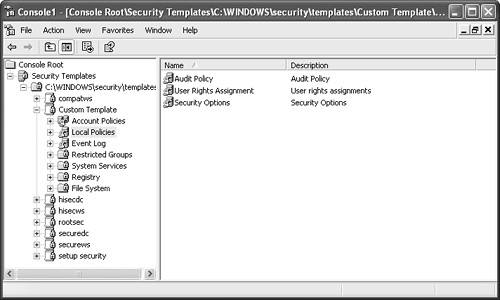
The tool displays which security settings are and are not in compliance with the security template settings. When the analysis is reviewed, you can choose to configure the system with the template setting by right-clicking the snap-in and choosing Configure Computer Now. Customizing Security TemplatesOne of the primary purposes of customizing security templates is to ensure that the organization's specific security requirements are met. It is also a way to ensure that business requirements and goals that are supported through the use of applications and systems' functional roles are not compromised. Typically, the larger the organization, the more systems it has and thus there might be a need for more customized security templates. For instance, if there are different security and business requirements for the various Exchange Server 2003 functional roles, administrators can customize a security template for each of those roles. TIP Use security templates provided by Microsoft, the National Security Agency (NSA) or the National Institute of Standards and Technology (NIST) as baselines for customizing the organization's security templates. Windows Server 2003 and Windows XP Professional are equipped with the Security Templates MMC snap-in that enables administrators to quickly and easily customize security templates to fit the requirements for specific systems. To begin using this tool, add the Security Templates MMC snap-in by following the steps outlined in the previous section "Using the Security Configuration and Analysis Tool." When the Security Templates snap-in is expanded, it displays the default search path to where the built-in security templates are stored, which is the %SystemRoot%\security\templates directory. Other paths can be opened to display other security templates that may reside on the system. Either select New Template after right-clicking on the path, or as a best practice use the Save As selection after right-clicking an existing or baseline security template to create a new, customized template. After creating and naming the new security template, expand it to display all the security settings that can be modified, as shown in Figure 11.3. When the security template has been customized, save it to a network share and use the Security Configuration and Analysis tool to apply the template to the appropriate systems. Figure 11.3. Using the Security Template MMC snap-in to customize a security template. Keeping Up with Security Patches and UpdatesService packs (SPs) and hotfixes for both the operating system and applications are vital parts to maintaining availability, reliability, performance, and security. Microsoft packages these updates into SPs or as individual updates (hotfixes). There are several ways an administrator can update a system with the latest SP: CD-ROM, manually entered commands, Windows Update, or Microsoft Software Update Services (SUS). NOTE Thoroughly test and evaluate SPs and hotfixes in a lab environment before installing them on production servers and client machines. Also, install the appropriate SPs and hotfixes on each production server and client machine to keep all systems consistent. Windows UpdateWindows Update is a Web site that scans a local system and determines whether there are updates to apply to that system. Windows Update is a great way to update individual systems, but this method is sufficient for only a small number of systems. If administrators choose this method to update an entire organization, there is an unnecessary amount of administration. Software Update Services (SUS)Realizing the increased administration and management efforts administrators must face when using Windows Update to keep up with security updates for anything other than small environments, Microsoft has created Software Update Services (SUS) to minimize administration, management, and maintenance of mid- to large- sized organizations. SUS communicates directly and securely with Microsoft to gather the latest security updates. The security updates downloaded onto SUS can then be distributed to either a lab server for testing (recommended) or to a production server for distribution. After these updates are tested , SUS can automatically update systems inside the network. NOTE You can find more information on SUS and download the product from http://www.microsoft.com/windows2000/windowsupdate/sus/. Client-Based Virus ProtectionViruses might be one of the most dangerous threats faced by computer systems. Many viruses are written to exploit specific vulnerabilities that might be present in clients and servers. Due to the large percentage of companies that use Microsoft products, many such viruses are specifically written to attack the Windows operating system. Consequently, it is extremely important to consider using an enterprise antivirus solution on all clients and servers. All the major antivirus manufacturers include robust scanners that detect, quarantine, or remove viruses. An aggressive plan should be in place to keep antivirus signature files and engines up to date. Because virus outbreaks can wreak havoc worldwide in a matter of hours, rather than days, it is wise to have the antivirus solution check for updates daily. Windows Lockdown Guidelines and StandardsMicrosoft has gone to great lengths to provide secure and reliable products. Moreover, it has worked closely with companies, government agencies, security consultants , and others to address security issues in the computer industry. Through this concerted effort and teamwork, secure standards and guidelines have been developed for not just Microsoft products but also other leading vendors as well. In addition to Microsoft security standards and guidelines, it is advisable that organizations use recommended best practices compiled by the National Institute of Standards and Technologies (NIST) and the National Security Agency (NSA). Both NIST and NSA provide security lockdown configuration standards and guidelines that can be downloaded from their Web site (http://www.nist.gov and http://www.nsa.gov respectively). |
| < Day Day Up > |
EAN: 2147483647
Pages: 393