5.1 Introduction
| < Day Day Up > |
| EJB technology is a server-side component model for the development and deployment of secure distributed-transaction business programs. The model enables Enterprise Bean Providers to write transactional business logic as a set of components that are deployable in any EJB-compliant container. Among the many services it offers, an EJB container provides for the management of concurrency, transactions, persistence, distributed objects, naming, and security. The EJB component model supports the development of software black boxes that can be aggregated to create larger components or systems. These components are written by the in-house software development groups of a large organization or may be purchased from a third-party vendor specializing in a particular set of business processes, such as human resources, payroll, general ledger, or other forms of financial processing. Like EJB components, servlets and JSP applications can engage in transaction processing. However, there are significant differentiators between EJB components versus servlets and JSP components. The EJB architecture defines a simplified programming model oriented toward transaction processing, which makes it easier for developers to focus on business logic. This includes extensive support for distributed-transaction monitor support. Based on information provided at deployment time, the transaction monitor of the EJB container ensures that the database properties of atomicity, consistency, isolation, and durability (ACID) are preserved:
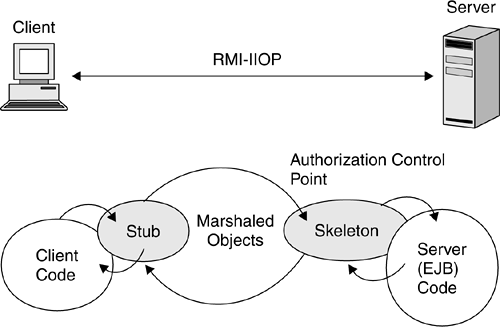
EJB technology is also designed to be a distributed-component model. The deployed components of an application may reside in a single EJB container or can be distributed across any number of EJB containers and transaction monitors . The interaction between distributed, or remote, EJB components can be carried over a variety of transports. RMI-IIOP is the industry-standard method for interoperability. Aside from assisting the distributed-transaction monitor in managing the transactions, the container is responsible for enforcing the security policy, regardless of whether the components reside in a single EJB container or across multiple EJB containers. Enterprise beans are intended to be portable, reusable, black-box software components that can be aggregated to create larger components. The contract between components is defined by the home, local home, local, and remote interfaces (see Section 3.7.2.1 on page 68), as well as the EJB deployment descriptor (see Section 3.2.1 on page 58), for each EJB component. In a distributed computing environment, client code communicates with a server over a communication network, typically using TCP/IP. The protocol required by the EJB specification is RMI-IIOP, which defines the format of a remote method request to a (possibly) remote server object, as shown in Figure 5.1. This format includes the wire protocol , or sequence of bits sent in each message across the network, and the sequence of messages that comprise the remote request and response from the server. Marshaling ”packaging ”of the RMI request is via a piece of code called a stub , which packages the request and calls the RMI-IIOP ORB to send the request to the EJB container hosting the EJB code. The server process's ORB demarshals ”unpackages ”the request via a piece of code called a skeleton , which then calls the requested server code with the appropriate arguments. Aside from the name of the target object being called and the parameters for the call, RMI-IIOP transmits transaction and security attributes in a manner that is transparent to the client and EJB developers. The RMI-IIOP security protocol for EJB containers is based on the Object Management Group 's CSIv2 specification, which includes authentication and authorization of the client, or requester. Figure 5.1. Remote Method Invocation |
| < Day Day Up > |
EAN: 2147483647
Pages: 164