Methods of Attack
|
|
When securing an access control system, one thing that a security administrator must keep in mind is the possibility of an attack. These attacks can come in many forms or in combinations of different attacks. When providing access control security, the security administrator should be aware of the different types of attacks, how they work, and how to defend their system from them.
This section covers several of the most common attacks and discusses how they are performed, how to defend a system from them, and how to perform them as part of access control system penetration testing.
| Exam Warning | The SSCP exam requires that you know how some of the basic attacks work and what they do. The SSCP exam takes a non-vendor-specific approach, so you need to know the basics of how the attack works technically. |
Dictionary Attack
Even if a user does not use a password that is easy to guess, they sometimes still use common words that are easy to remember. This brings into play a simple method of cracking passwords known as a dictionary attack. A dictionary attack basically uses a flat text file containing most of the words out of the dictionary (sometimes in multiple languages) and many other common words. These words are then systematically tried against the user's password until one of them works. In addition, most dictionary attack applications also support adding numerical prefixes or suffixes to the password in case the user tries to obfuscate the password by adding digits to the beginning or end.
Brute Force Attack
Even if the user uses a secure password that is a random or pseudo-random generation of numbers, letters, and symbols, their password can still be broken. A technique for doing this is known as a brute force attack. In this type of attack, every conceivable combination of letters, numbers, and symbols are systematically tried against the password until it is broken. Does this take an incredibly long time? Perhaps not as long as you might think. Work through Exercise 2.02 to examine this process using a common password-cracking program for Windows NT/2000 passwords called L0phtCrack.
Exercise 2.02: Brute Force Cracking with L0phtCrack
In this exercise, you will be using a password cracking utility from @stake called L0phtCrack. This utility allows you to audit your network security by determining how difficult it is to decrypt network passwords. It has a built-in network sniffer as well as other tools to gather password hashes from remote systems. A trial version is available for download at www.atstake.com/research/lc/download.html.
For the purposes of this exercise, you will be using a sample file of hashed passwords to test the cracking utility. The contents of this file are as follows:
TestEasy:1001:A80F6E6A87BA6AC2AAD3B435B51404EE:75C06256F58D0 7A18B239E4CC39A382D::: TestDict:1002:129AFF2466F0BE25765AC06A3A33CD4F:9D87BF03182BD 62F53FB8358707EE8CE::: TestHard:1003:53217B5B4F0ACA5A258C2ECB5DCBAC31:EE793B0684047 B9EA4EF162775E746B0:::
The data shown in this file is the output of the PWDUMP utility included with L0phtCrack. The PWDUMP utility was run on a test system using Windows NT 4 Server. In this exercise, you will import this file into L0phtCrack and find how long it takes to crack the passwords Results will vary based on the properties of the system used. In addition, a licensed version of the software was used, which allows for brute force cracking. Brute force cracking is disabled in the trial version and the trial version is limited to 15 days of operation.
-
Download and install L0phtCrack 4.
-
Open L0phtCrack and close the initial Wizard screen.
-
Click on File | New Session to open up a new audit session. You will be presented with the screen shown in Figure 2.12.
Figure 2.12: L0phtCrack Main Screen -
Click on Import | Import from PWDUMP File and select the file with the password hashes. This will import the file into L0phtCrack and show you the accounts found on the main screen, as shown in Figure 2.13.
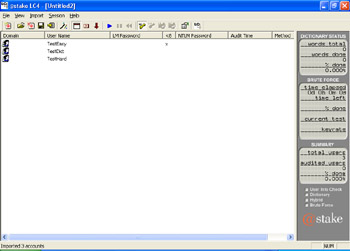
Figure 2.13: L0phtCrack Accounts View -
Click on Session | Session Options to bring up the options screen. Change the Brute Force Crack Character Set to A - Z, 0 - 9 and !@#$%^&*()-_+= as shown in Figure 2.14.
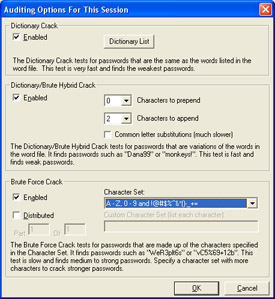
Figure 2.14: L0phtCrack Session Options -
Click OK on the Session Options screen, and then click Session | Begin Audit. L0phtCrack will now begin performing a dictionary attack, followed by a hybrid attack, and finally a brute force attack. Due to the types of passwords used in our sample accounts, L0phtCrack will take varying amounts of time to crack each password. The "TestEasy" and "TestDict" accounts have very simple passwords and are cracked very quickly, as shown in Figure 2.15.
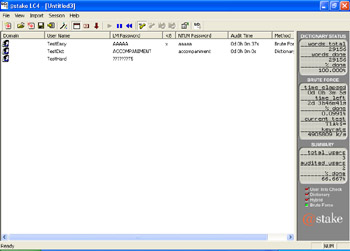
Figure 2.15: L0phtCrack Passwords Cracked -
At this point, continue to let the utility attempt to crack the password. When it is done, you will have the result shown in Figure 2.16.
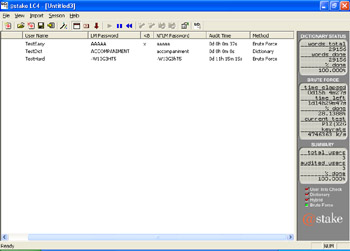
Figure 2.16: L0phtCrack All Passwords Cracked -
As seen from these results, the "hard" password was cracked in only 11 hours and 15 minutes. This was only a nine-character password and had only one special character, but it shows how quickly a password can be compromised using the right tools.
Denial of Service Attacks
A DoS attack is not so much an attack against the passwords used by access control subjects as it is an attack against the availability of the access control objects. These attacks attempt to render a network inaccessible by flooding it with network packets to the point that it is no longer able to accept valid packets. This works by simply overloading the processor of the firewalls, switches, or routers by making them attempt to process a number of packets far past their limitations. By performing a DoS attack directly against a firewall, the attacker can sometimes get the firewall to overload its buffers and start letting all traffic through without filtering it. This is one method used to access internal networks protected by firewalls. If the security administrator is alerted to an attack of this type occurring, they can block the specific Internet Protocol (IP) address that the attack is coming from at the router.
An alternative attack that is more difficult to defend against is the distributed denial of service attack (DDoS). This attack is worse because the attack can come from a huge number of computers at the same time. This is accomplished by either the attacker having a large distributed network of systems all over the world (unlikely), or by infecting normal users' computers with a Trojan horse, which allows the attacker to force the systems to attack targets that they specify without the end user's knowledge. These end-user computers are systems that have been attacked in the past and infected with one of these Trojan horses by the attacker. By doing this, the attacker is able to set up a large number of systems (called Zombies) to each perform a DoS attack at the same time. This type of attack constitutes a DDoS attack. Performing an attack in this manner is more effective due to the number of packets being sent. In addition, it introduces another layer of systems between the attacker and the target, making the attacker more difficult to trace.
| Test Day Tip | A DoS or DDoS attack is designed to impact the access control system's availability. It is important to know which part of the access control system is affected by the different attacks. |
Spoofing
Spoofing is a form of attack where the intruder pretends to be another system and attempts to obtain data and communications that were intended for the original system. This can be done in several different ways including IP spoofing, session hijacking, and Address Resolution Protocol (ARP) spoofing. Each of these methods allows an intruder to access data that they would normally be restricted from viewing.
IP spoofing is a fairly simple attack where an intruder configures his or her system to work with the same IP address as a valid system on the network. The intruder then fools any routers or switches into thinking that their system is the actual destination machine. This is done by poisoning the ARP cache of the switch or by sending out Windows Internet Naming Service (WINS) broadcasts on the network. In this way, the intruder is able to have any packets intended for the original destination routed to their system. This is not very useful by itself, but this attack can be combined with other techniques to make it very powerful.
Session hijacking is similar to a normal spoof attack except that this type of attack is intended to intercept specific packets that the source and destination systems are using to maintain a communications session. An example of this is a Telnet connection to a host. When the intruder spoofs the address for the user's system, they can continue communications with the host via the same Telnet session. By doing so, the intruder effectively bypasses any authentication procedures and is able to access the remote system as if they were the original end user.
The last type of spoofing is ARP spoofing. Aside from being part of IP spoofing, ARP spoofing is also a standalone technique of its own. An ARP spoof is performed by sending an ARP packet to a switch containing the machine name of the target, and the MAC address of the attacker. By doing an ARP spoof, the intruder can hijack sessions that a client was previously using. This can also be used as a Man-in-the-Middle (MITM) attack between two network devices.
Man In The Middle Attacks
A MITM attack is performed by effectively inserting an intruder's system in the middle of the communications path between two other systems on the network. By doing this, an attacker is able to see both sides of the conversation between the systems and pull data directly from the communications stream. In addition, the intruder can insert data into the communications stream, which could allow them to perform extended attacks or obtain more unauthorized data from the host system.
Figure 2.17 shows the communications path used for normal communications and how this is changed during a MITM attack. The following steps illustrate how to perform a MITM attack by using ARP spoofing.
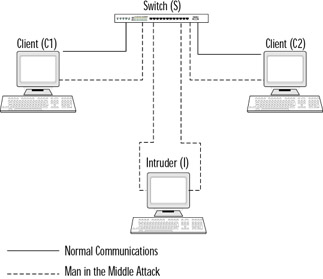
Figure 2.17: MITM Attack
-
The intruder (I) sends an ARP packet to a client (C1) using the IP address of another client (C2), but the MAC address for the intruder (I).
-
The intruder (I) sends an ARP packet to a client (C2) using the IP address of another client (C1), but the MAC address for the intruder (I).
-
Now both clients have ARP cache entries for each other's IP address, but the MAC address for these entries point to the intruder. The intruder routes packets between C1 and C2 so that communications are not interrupted.
-
The intruder sniffs all packets that it is routing and is able to see all communications between the clients.
This process allows an intruder to view all traffic between two clients, but ARP spoofing can potentially be more damaging than this. By performing a MITM attack between a router and the switch, an intruder could see all data coming through the router. In addition, if an intruder replies to every ARP request sent out by the switch, it could intercept traffic going to all clients. This gives the intruder the option of performing a DoS attack by not allowing any client to communicate with the switch, or routing traffic to the intended client and sniffing the data being communicated via the MITM attack.
Spamming
Spamming or the sending of unsolicited e-mail messages is typically considered more of an annoyance than an attack, but it can be both. When a mail server is hit with a huge number of messages, it can cause the system to slow down making it unable to process legitimate messages. In addition, mail servers have a finite amount of storage capacity, which can be overfilled by sending a huge number of messages to the server. Finally, if the mail server does active virus scanning on incoming messages, the system can be slowed to a crawl as it attempts to examine all of the incoming spam.
The best way to defend against spam attacks is to set a limit on the amount of space that any account can use on the system. This prevents the system from becoming overfilled due to a spam attack. Also, spam-filtering software is available for various types of mail servers, which may be able to help curb some of the messages. Another good way to protect systems from a spamming attack is to close any open Simple Mail Transfer Protocol (SMTP) relays. These relays can be used to forward spam to the intended target while making it look like it is your system doing the spamming.
Sniffers
A sniffer is either a dedicated device or a system configured with special software and a network card set in promiscuous mode. A sniffer basically sits on the network and listens for all traffic going across the network. The software associated with the sniffer is then able to filter the captured traffic allowing the intruder to find passwords and other data sent across the network in cleartext. Sniffers have a valid function within information technology by allowing network analysts to troubleshoot network problems, but they can also be very powerful weapons in the hands of intruders.
The most obvious method of defending a network from sniffer attacks is to use switches as part of the network architecture. Switches route packets directly between the systems attached to the switch rather than broadcasting all of the data out to all ports like a hub. This prohibits the use of sniffers, as they are unable to retrieve any data except for that going to their specific port. This can be worked around by using the switch's switched port analyzer (SPAN) or mirroring feature. To use SPAN, the switch is configured to route a copy of all packets going to or from one or more ports to a specific port. A sniffer is then placed on the port that the copy is being routed to and can read all packets going through the switch.
Software is available that can detect network adapters that are in promiscuous mode. Several network intrusion detection systems have this capability, which is covered later in this chapter.
Using Sniffers to Attack
Sniffers are generally benign tools that are used to troubleshoot networks and trace problems. They can also be used to capture data to perform extensive network analysis. However, when used in combination with other attacks, they can be one of the most dangerous pieces of software on a network. Many "root kits" or groups of hacking tools either contain small sniffers or use existing sniffer software found on the network. When these sniffers are used with remote access software, Trojan horses, or other hacking tools, they have the ability to compromise an entire network in a matter of a few hours.
The reason these are so dangerous is that there is the possibility that every packet going across the network will be captured and forwarded to the intruder. This can contain IDs and passwords in cleartext, architectural information for the network, and information on the routers and switches on the network. This can provide an intruder with a plethora of useful information that they can use for their next attack on the system.
Two good defenses are to use switches to eliminate sniffers' ability to obtain data from all over the network, and to use good monitoring tools to alert the administrators if a switch's SPAN feature is enabled. This will help limit the damages that can be caused by a sniffer on a network being controlled by an intruder.
|
|
EAN: 2147483647
Pages: 135