Access Control Models
|
|
Most access control systems are based on several basic access control models. These models define the operating parameters for the access control system and define the manner in which they operate. The access control model also defines the way that permissions are set on access control objects and how authorization is handled in the access control system.
There are four primary access control models. These are the models you are expected to understand in order to pass the SSCP exam. Studying these models also gives a good understanding of the basis for access control models in.
There is an authoritative reference book on the subject of access controls called the "Department of Defense Trusted Computer System Evaluation Criteria" book or the "Orange" book. It is called the Orange book based on the color of the spine in its printed form. This set of guidelines provides the information necessary to classify the security rating of systems and define the degree of trust that they earn.
Using Orange book guidelines, there are four primary security classification grades (A through D) with varying levels in each grade designated by a number. For example, Microsoft Windows NT can earn a C2 grade with the correct patches and hardening procedures performed. Table 2.2 shows the available grades and levels as well as some examples of systems earning each level.
| Grade | Levels | Definition | Examples |
|---|---|---|---|
| A | A1 | Verified Protection | Boeing SNS, Honeywell SCOMP |
| B | B1, B2, B3 | Mandatory Access Control | ACF2 or TopSecret, Trusted IRIX |
| C | C1, C2 | Discretionary Access Control | DEC VMS, Windows NT, Novell NetWare, Trusted Solaris |
| D | None | Minimal Security - Evaluated and failed | PalmOS, MS-DOS |
There are several Orange book definitions that do not work well with current information systems. First, the Orange book requires that the system be configured as standalone. No network connectivity can be allowed, which makes the system more difficult than practical. In addition, it can take anywhere from one to two years to certify a system. In this day of constant technology upgrades, that means that by the time a product is certified, it is outdated. Also, any new patches, service packs, or changes to the product break the certification and require that the system be reevaluated. On top of this, applying for the certification is expensive.
Basically, the main problem with the Orange book guidelines is that they are outdated and do not support current technology such as client-server computing. These guidelines are rarely applied or even paid attention to outside of government environments, but it is important to be aware of them. The first access control systems were were designed for the government; therefore, most models are based on the Orange book guidelines.
There is an upgrade to the Orange book available called the "Red" book. Again, this is due to the spine color of its original printed form (known as the Rainbow series). The Red book is actually two separate books that work together to extend the Orange book's guidelines to include network systems. The two books that make up the Red book are "Trusted Network Interpretation of the TCSEC" and "Trusted Network Interpretation Environments Guideline: Guidance for Applying the Trusted Network Interpretation." The Red book provides guidelines on how the concepts and guidelines from the Orange book can be applied to network environments. The guidelines within this book are as strict as the Orange book itself, but it is designed to work with networked environments.
Discretionary Access Control
The discretionary access control (DAC) model is the most common access control model used. It bases security on the identity of the access control subject. Every access control subject has specific permissions applied to it and, based on these permissions, has some level of authority.
This access control model is called discretionary because individual users or applications have the option of specifying access control requirements on specific access control objects that they own. In addition, the permission to change these access control requirements can also be delegated as a permission. As assigning access control permissions to the access control object is not mandatory; the access control model itself is considered discretionary. Basically, the owner of the access control object is allowed to decide how they want their data protected or shared.
Any system using DAC is considered Orange book C-level at best. DAC is not eligible for A-level or B-level. The primary use of DAC is to keep specific access control objects restricted from users who are not authorized to access them. The system administrator or end user has complete control over how these permissions are assigned and can change them at will.
DAC allows the owner of the access control object to change the access control permission on objects without regard to a central authority. Also, centralized access control systems can be used with this as a single authoritative point of authorization, with the permissions still being applied at the object level. The ability to use different types of access control systems with this model give it a great deal of flexibility.
As previously mentioned, this is a very common access control model. It is used in UNIX, Windows NT/2000, Novell NetWare, Linux, Banyan Vines, and many other NOSs. These systems use an access control list (ACL) to set permissions on access control objects. These ACLs are basically a list of user IDs or groups with an associated permission level. Every access control object has an ACL, even if it is left at the default after the object is created. The operating systems vary in the way the permissions are defined in the ACL, but the SSCP exam is not vendor-specific and does not require you to know how each operating system uses them. However, the SSCP exam does require that you know the basics types of permissions that are defined. These are detailed in Table 2.3.
| Permission | Definition |
|---|---|
| Read | Allows the access control subject to read the data contained in the object |
| Write | Allows the access control subject to write data to the object |
| Create | Allows the access control subject to create new objects |
| Execute | Allows the access control subject to execute the code within the object |
| Modify | Combination of Read and Write, may also include Create and Execute |
| Delete | Allows the access control subject to delete the object |
| Rename | Allows the access control subject to rename the object |
| List | Allows the access control subject to list the contents of a directory - only applicable to directories |
| No Access | Explicitly denies the access control subject access to the object |
| Exam Warning | While the SSCP exam is not vendor-specific and takes a general perspective of information security, you do need to know how DAC works and that many common NOSs use DAC with ACLs as part of their access control security. |
Mandatory Access Control
Mandatory access control (MAC) is based on sensitivity levels rather than ACLs and is frequently used by government systems. In MAC, the security administrator gives every access control object and access control subject a sensitivity level and the object owner or system user cannot change this sensitivity level. Based on the sensitivity levels of the access control objects, the access control system decides how all data will be shared and the data is restricted to the access control subjects with the required matching sensitivity label. For example, if an object has a sensitivity label of top secret, an access control subject with a label of secret will be unable to access the object.
MAC is considered to be a more secure access control model than DAC, as every subject and object must have a label assigned to it. This model ensures that if a subject is not authorized to access data with a specific sensitivity label, they will not be able to access it. This works well in a strictly defined hierarchy such as the military, where subjects are simply not authorized to access any information that is above their level in the hierarchy.
Access control systems using MAC are able to gain a B-level rating if the access control system meets all of the criteria specified in the Orange book. Access control systems using DAC are unable to attain this level due to the additional security requirements that MAC fills.
The major disadvantage to MAC is that it is extremely difficult to implement. There is a great deal of administration involved, as every object must be assigned a sensitivity level by the administrator when it is created. It is also very difficult to program applications to work with MAC due to the way objects are created and used. For example, the guidelines for MAC require that any data or information with a sensitivity level higher than the object that the data is going to should be restricted from completing the operation. This logic is very difficult to work with when designing applications. In addition, whenever output is generated from the data in an object, the output media itself (print job, diskette, CD, and so on) must be labeled with the same sensitivity level. This makes MAC very difficult to work with, which is the primary reason that it is not implemented in most corporate environments. The total cost of ownership for MAC is not justified for most business purposes.
Non-Discretionary
There are several different forms of non-discretionary access control and each of these basically assign specific roles to access control subjects and labels to access control objects specifying which roles are granted access to the object. This access control model is also called role-based access control (RBAC) as it depends on the definition of roles in order to make access control decisions.
RBAC basically assigns users to specific roles and assigns permissions to each role. In addition, there is a hierarchy within RBAC whereby some roles can inherit permissions that are granted to another role (see Figure 2.10).
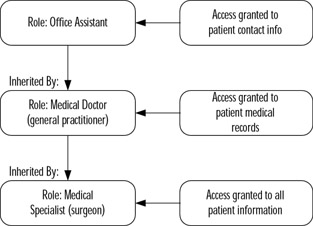
Figure 2.10: RBAC Inheritance
In Figure 2.10 you can see how roles can be inherited. In this example, the Office Assistant role has access to only the patient's contact information. The Medical Doctor role has permission to view the patient's medical records. However, since the Medical Doctor role inherits the permissions of the Office Assistant role, the patient's contact information is accessible as well. The Medical Specialist has been explicitly granted access to all patient , and therefore, has access not only to the contact information and medical records, but also anything else in the patient's files.
In a good RBAC implementation, there is also the ability to block inheritance. There are instances where, for security reasons, the security administrator would want to limit privileges in the access control hierarchy. For example, in a banking situation, they would want to have someone in the Bank Teller role have access to balance out their register at the end of the day. In addition, they would want to have someone in the Floor Supervisor role to have access to verify that the teller's balance matches the actual money shown in the final count. However, they would not want the Floor Supervisor to be able to balance the register as well, because the organization would be open to fraud from a single person. In computer terms, this is considered a single point of failure. You can combat this by blocking inheritance in the hierarchy.
With RBAC, there is less administrative work than MAC, as any objects created by a subject can be accessed by other subjects with the same role in the organization. This behavior can also be overridden in most access control systems using RBAC to increase security.
| Test Day Tip | The best way to think of RBAC is to look at it like an organizational chart. Every person has a specific position and job function and the access control model mimics this organizational structure. |
Formal Models
The formal models of access control are theoretical applications of access control methods. These do not specify specific methods of controlling access, but rather specific guidelines that should be followed. They work best with static environments and are difficult to implement within dynamic systems that are constantly changing, such as those in most enterprise environments. The documentation on how these models are supposed to be implemented is very limited and does not give any specific examples.
The formal models do provide a good baseline to start from when designing access control systems, however. By ensuring that the guidelines within the formal model most closely related to your needs are followed, you ensure that you have a strong foundation on which to build the rest of the access control system.
Bell-LaPadula
David E. Bell and Len J. LaPadula wrote the Bell-LaPadula formal access control model in 1973 for use in government and military applications. This formal model specifies that all access control objects have a minimum security level assigned to it so that access control subjects with a security level lower than the security level of the objects are unable to access the object. Does this sound familiar? The Bell-LaPadula formal model is what the MAC model is based on.
Biba
The Biba formal model was written by K.J. Biba in 1977 and is unique as it was the first formal model to address integrity. The Biba model bases its access control on levels of integrity. It consists of three primary rules. The first rule specifies that a subject cannot access objects that have a lower level of integrity than the access control subject has. The second rule states that access control subjects cannot modify objects that have a higher level of integrity than their current integrity levels. The last rule specifies that an access control subject may not request services from subjects that have a higher integrity level.
Clark-Wilson
The Clark-Wilson formal model was written in 1987 and updated in 1989 by David D. Clark and David R. Wilson. This model is similar to Biba, as it addresses integrity. The Clark-Wilson model is designed to not only address access to objects, but also to ensure integrity by specifying guidelines for processes which occur using the access control object.
One of the most important guidelines to come out of the Clark-Wilson model is that of segregation of duties or separation of duties. The principle of segregation of duty states no single person should perform a task from beginning to end, but that the task should be divided among two or more people to prevent fraud by one person acting alone. This ensures the integrity of the access control object by securing the process used to create or modify the object.
|
|
EAN: 2147483647
Pages: 135