| 1. | A principle of the BellLa Padula model was not mentioned in this chapter. Called the tranquillity principle, it states that the classification of a subject or object does not change while it is being referenced. Explain the purpose of the tranquillity principle. What are the implications of a model in which the tranquillity principle is not true? |
| 2. | Subjects can access objects, but they can also access other subjects. Describe how a reference monitor would control access in the case of a subject acting on another subject. Describe how a reference monitor would control access in the case of two subjects interacting. |
| 3. | List the source and end of all information flows in each of the following statements. sum := a+b+c; if a+b < c+d then q:=0 else q:=1; write (a,b,c); read (a,b,c); case (k) of 0: d:= 10; 1,2: d:= 20; other: d:= 30; end; /* case */ for i:=min to max do k:=2*k+1; repeat a[i]:=0; i:=i-1; until i  0; 0;
|
| 4. | Does the system of all subsets of a finite set under the operation "subset of" (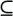 ) form a lattice? Why or why not? ) form a lattice? Why or why not? |
5.Can a user cleared for <secret;{dog, cat, pig}> have access to documents classified in each of the following ways under the military security model? <top secret;dog> <secret;{dog}> <secret;{dog,cow}> <secret;{moose}> <confidential;{dog,pig,cat}> <confidential;{moose}>
|
| 6. | According to the BellLa Padula model, what restrictions are placed on two active subjects (for example, two processes) that need to send and receive signals to and from each other? Justify your answer. |
| 7. | Write a set of rules combining the secrecy controls of the BellLa Padula model with the integrity controls of the Biba model. |
| 8. | Demonstrate a method for limited transfer of rights in the GrahamDenning model. A limit of one is adequate. That is, give a method by which A can transfer to B right R, with the provision that B can transfer that right to any one other subject. The subject to which B transfers the right cannot transfer the right, nor can B transfer it again. |
| |
| 9. | Explain what is necessary to provide temporal separation. That is, what conditions must be met in order for two processes to be adequately separated? |
| 10. | Does the standard Unix operating system use a nondiscretionary access control? Explain your answer. |
| 11. | Why is labeling of objects a security requirement? That is, why cannot the trusted computing base just maintain an access control table with entries for each object and each subject? |
| 12. | Label integrity is a technique that ensures that the label on each object is changed only by the trusted computing base. Suggest a method to implement label integrity for a data file. Suggest a method to implement label integrity for a callable procedure. |
| 13. | Describe a situation in which you might want to allow the security kernel to violate one of the security properties of the BellLa Padula model. |
| 14. | Explain the meaning of the term granularity in reference to access control. Discuss the tradeoff between granularity and efficiency. |
| 15. | Explain how a semaphore could be used to implement a covert channel in concurrent processing. Explain how concurrent processing primitives, such as fork and join, could be used to implement a covert channel in concurrent processing. |
| 16. | The Unix operating system structures files by using a tree. Each file is at a leaf of the tree, and the file is identified by the (unique) path from the root to the leaf. Each interior node is a "subdirectory," which specifies the names of the paths leading from that node. A user can block access through a node by restricting access to the subdirectory. Devise a method that uses this structure to implement a discretionary access policy. |
| 17. | In the Unix file system described in this chapter, could a nondiscretionary access policy be defined so that a user has access to a file only if the user has access to all subdirectories higher (closer to the root) in the file structure? What would be the effect of this policy? |
| 18. | I/O appears as the source of several successful methods of penetration. Discuss why I/O is hard to secure in a computing system. |
 0;
0;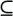 ) form a lattice? Why or why not?
) form a lattice? Why or why not?