Deploying VPNs in WLANs
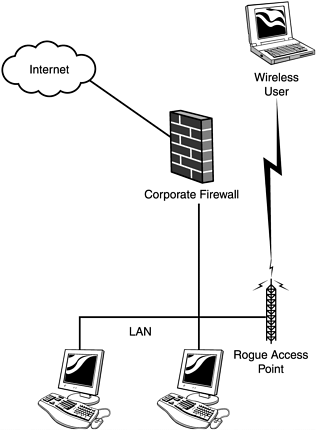
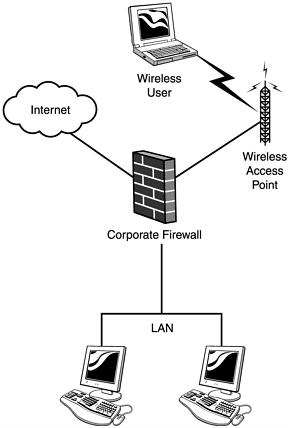
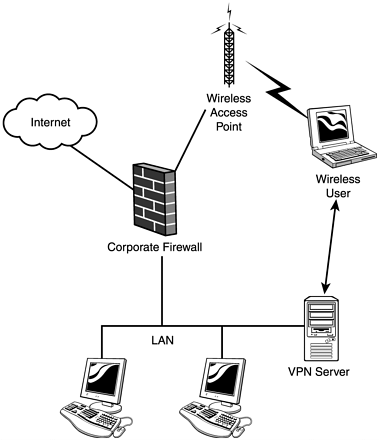
| Figure 13.1 shows the most common business configuration of wireless access points in use today. In this case, a rogue access point installed on a user machine sits inside perimeter defenses and allows the hacker a wide- open backdoor. The rogue access point is often installed by an employee who wants wireless access at work, or a network administrator who has forgotten about a prior test installation. If after reading this book you get "owned" by such a configuration, you have only yourself to blame. Grab your iPAQ right now and go "war walking" around the perimeter of your building. Figure 13.1. A rogue wireless access point. Figure 13.2 shows a better configuration. In this case, the wireless access point is placed outside the corporate firewall. Thus, wireless users have to pass through the corporate firewall ruleset, the same as hardwired ( landline ) users must. However, as you learned earlier in the book, such a configuration is still open to attack. For example, a hacker could sniff the connection from the wireless user to the firewall and walk away with a username and password. The fact that the sniffing was done wirelessly makes it all the more dangerous. Figure 13.2. A slightly better (yet inadequate) solution. Figure 13.3 shows the best configuration. In this case, the wireless user still has to pass through the corporate firewall. However, in order to do so, he must now also authenticate with the VPN. Because the communication passes through an encrypted tunnel, it is resistant to sniffing from nearby hackers. Figure 13.3. You should require all wireless users to authenticate through a VPN. There are numerous solutions for implementing VPNs, but a full discussion is beyond the scope of this chapter. At the time of this writing, a number of vendors publicly advertised VPN solutions specifically for mobile users, but when contacted, none were able to produce actual working models. |
EAN: 2147483647
Pages: 171
- Using SQL Data Definition Language (DDL) to Create Data Tables and Other Database Objects
- Using SQL Data Manipulation Language (DML) to Insert and Manipulate Data Within SQL Tables
- Working with Functions, Parameters, and Data Types
- Writing External Applications to Query and Manipulate Database Data
- Understanding Triggers