Funk s Steel-Belted Radius
Funk's Steel-Belted RadiusFunk Software is one of the most widely used RADIUS servers. As a result of the popularity of this product, we have included this segment to show the capabilities of a good RADIUS server product. If nothing else, the following information will give you a baseline from which to judge other products. We thank Funk Software for their kind permission to include their information here. Overview
Straight from the data sheet on http://www.funk.com, this brief intro manages to consolidate into a few words the many features and functional aspects provided by their Steel-Belted Radius software. Funk's product is a functional software package that provides a central point of administration for all remote users, regardless of how they connect. In other words, users will not need separate systems to provide accountability, authorization, and authentication for WLAN, LAN, VPN, dial-up, or Internet-based connections. In addition to multifaceted connection support, this product also supports various operating systems and networking software, including NT/2000, Solaris, and Netware. In particular, Steel-Belted Radius earns a second look because it provides extra security for WLAN users by increasing the level of security and access by working with existing access points to ensure only authorized users are allowed access. The following will detail the many features of Funk's Steel-Belted Radius. Central User AdministrationSteel-Belted Radius manages remote and WLAN users by allowing authentication procedures to be performed from one database. This relieves you of the need to administer separate authentication databases for each network access or WLAN access point device on your LAN. Steel-Belted Radius performs three main functions:
When a user connects to the network via a remote access server, firewall, router, access point, or any other RADIUS-compliant network access device, that device queries Steel-Belted Radius to determine whether the user is authorized to connect. Steel-Belted Radius accepts or rejects the connection based on user credential information in the central security database, and authorizes the appropriate type of connection or service. When the user logs off, the network access device informs Steel-Belted Radius, which in turn records an accounting transaction. Central Hardware AdministrationSteel-Belted Radius works with the remote and wireless access equipment and methods you already have in place. Whether you have set up dial-up, Internet, VPN, outsourced, WLAN, or any other form of access, Steel-Belted Radius can manage the connections of all your remote and wireless users. This includes the following:
Moreover, Steel-Belted Radius supports a heterogeneous network, interfacing with remote and wireless access equipment from different vendors simultaneously . Steel-Belted Radius automatically communicates with each device in the language it understands, based on customized dictionaries that describe each vendor's extensions to the RADIUS protocol. Authentication MethodsSteel-Belted Radius not only works with a wide variety of remote and wireless access equipment, but it also makes it possible to authenticate remote and WLAN users according to any authentication method or combination of methods you choose. In addition to Steel-Belted Radius's native database of users and their passwords, Steel-Belted Radius supports "pass-through" authentication to information contained in the following:
Steel-Belted Radius can simultaneously authenticate many users. If you are combining authentication methods, you can even specify the order in which each is checked. The result is streamlined administration, as well as one-stop authentication. Securing Your Wireless LANIn addition to authenticating wireless LAN users, Steel-Belted Radius also plays a pivotal role in securing their connections. To perform these functions, Steel-Belted Radius supports the following:
In addition, Steel-Belted Radius provides additional security on a WLAN by
For example, you could specify that WLAN access can only occur during business hours, or force re-authentication after a specified amount of time. This allows for more granular and robust security on your WLAN. Steel-Belted Radius also makes it possible to manage both wireless LAN and remote users from a single database and console, greatly reducing your administrative burden by eliminating the need for two separate authentication systems. RADIUS AccountingSteel-Belted Radius logs all authentication transactions, so you'll be able to view the entire history of authentication requests and the resulting responses. If your network access device supports RADIUS accounting, you'll also be able to track how long each user stays connected ”with the additional security of being able to see exactly who's connected at any time and on which port. Accounting data can be exported to spreadsheets, databases, and specialized billing software. Or, you can choose to log data directly to your SQL database. System RequirementsSteel-Belted Radius is available in three versions:
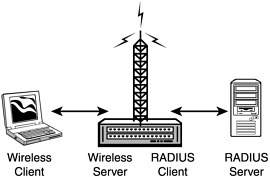
In short, a RADIUS server listens for incoming authentication requests from an access point that is acting on behalf of a client computer. The server verifies that the user is in the accounts database, and returns a go/no-go message to the access point, which then determines how much access a client should have (see Figure 12.12). What makes a RADIUS server so universal is that it is standardized. Therefore, if vendor Y builds in RADIUS server support, it should work smoothly with vendor X's RADIUS server. In addition to hardware support, RADIUS servers often include the capability to link into existing user account databases, such as a Windows NT user database or a even a SQL Server database. Figure 12.12. Typical setup of a RADIUS server. In addition to authenticating users, a RADIUS server can be used to authenticate access points. This additional feature forces all existing access points to "log in" before they become part of the network. This means a hacker can't simply plug an access point into some remote hub or switch and expect to be able to immediately use it as a relay point to hack the network. The rogue access point would not be able to communicate with the network because it hasn't been authenticated. Another benefit of a RADIUS server is its capability to control various aspects of authorization, such as time limits and re-keying schedules. In addition, many RADIUS servers support EAP, which is a way of using anything from smart cards to digital certificates to authenticate a user instead of a username and password. |
EAN: 2147483647
Pages: 171