Access Point-Based Security Measures
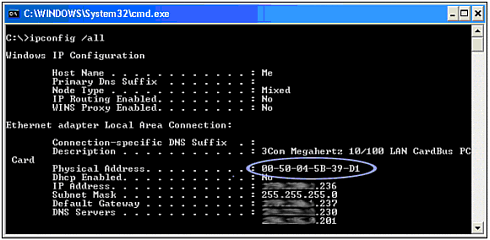
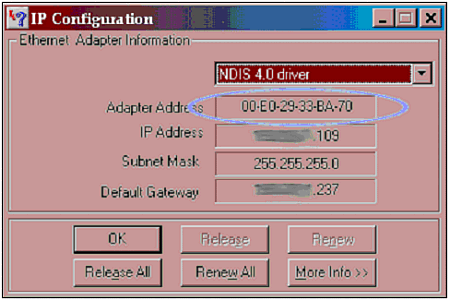
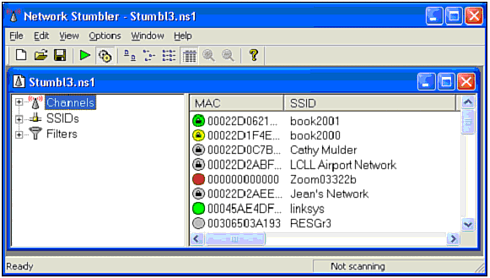
| For WLANs, the first step in security hardening is to focus on the access point. Since the AP is the foundation of wireless LAN data transfer, you must ensure that it is part of the solution, instead of the problem. WEPAs we have exposed it ad nauseam in this book, you might be wondering why we have listed WEP as a method of protection. Although it has many palpable weaknesses, there is still one major advantage to enabling WEP: It will thwart the casual hacker to the point where he goes looking for an easier target. It is true that the current version of WEP is crackable. However, most of the people who would attempt to access your wireless network will not want to put forth the effort required to crack WEP. The curious hacker will see that your network is using WEP and bypass it for an open network next door. The script kiddie will also bypass the WEP-protected WLAN because she will not have the patience or the aptitude to successfully penetrate the protection. Using a popular program such as NetStumbler, a hacker can easily spot the WEP-protected networks as well as your neighbor's open one. Which network do you think would be the victim (see Figure 12.1)? Figure 12.1. NetStumbler showing user WEP-protected and unprotected WLANs. In other words, by enabling a protection that is minimally effective, you can eliminate 99% of your threat. Similar to a car lock, WEP will protect your network from passers-by; however, just as a dedicated thief will quickly bypass the lock by smashing a car window, a dedicated hacker will put forth the effort to crack WEP if it is the only thing between him and your network. MAC FilteringEvery device on a wireless network, by default, has a unique address that's used to identify one WNIC from another. This address is called the MAC address, which stands for Media Access Control. In theory, because every WNIC has been pre-assigned a 100% unique MAC address by the hardware vendor, an access point can be set up to only allow a preselected list of WNICs to connect. For example, the Linksys WAP11 includes a MAC filtering option in its software that will enable an administrator to define who can connect to the WLAN by listing all the allowed MAC addresses (see Figure 12.2). Figure 12.2. MAC filtering in WAP11. As you can see, this is fairly straightforward. To determine the MAC address of a network card, a user only has to go to Start To determine the MAC address of a network card in Windows NT/2000/XP/.NET, follow these steps:
To determine the MAC address of a network card in Windows 95/98/ME, follow these steps:
To determine the MAC address of a network card in Linux (do not attempt to find Start
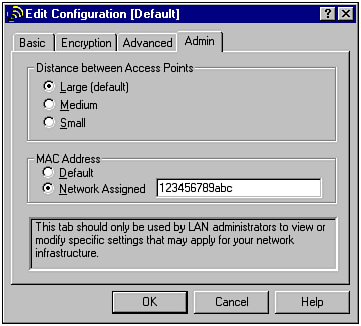
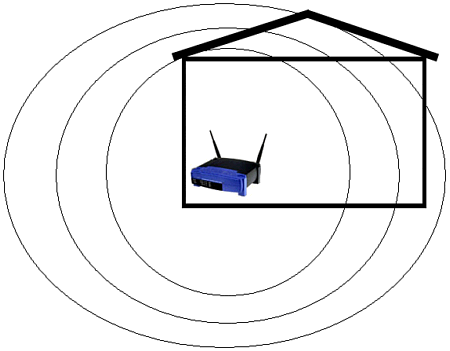
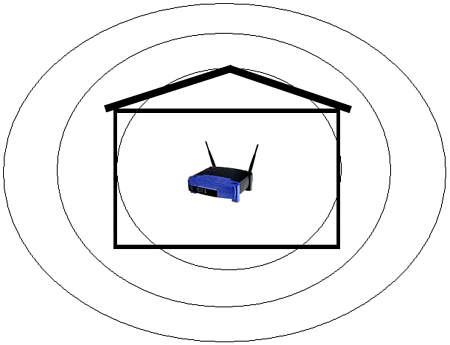
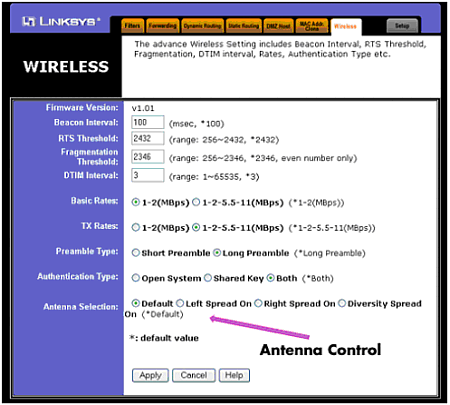
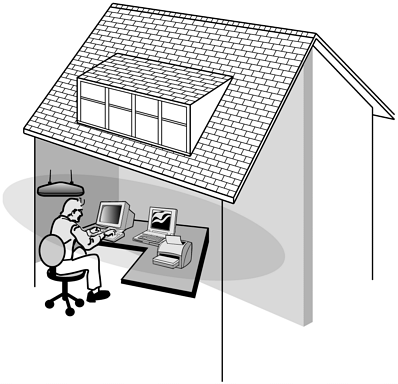
Once you have the MAC addresses of all the connecting WNICs, you can set up the MAC filtering and enable it accordingly . This will stop any connection attempts made by unauthorized addresses. However, while this in theory is an excellent way to stop hackers from accessing your WLAN, there is a serious flaw in MAC filtering. The problem with MAC filtering is that MAC addresses can be spoofed by changing WNIC settings. For example, the Dell TrueMobile includes software that will enable a hacker to alter her MAC address to any she chooses (see Figure 12.5). Thus, this option is about as useful as trying to keep people from accessing a chat room by restricting chat handle names . To bypass such a restriction, a person only has to change her name . The same applies to MAC filtering. Figure 12.5. Dell TrueMobile MAC address field. Why would a software/hardware vendor want to allow a user to change a MAC address? Having the power to adjust a MAC address can provide a network administrator more tools to keep control over her network. However, this increased power could also enable a malicious person to have just as much control. This is one example of how the ancient power struggle between user needs and security often plays right into a hacker's hands. Regardless, if MAC filtering is an option, you should implement it on your WLAN. Just as with enabling WEP, MAC filtering does require a modicum of sniffing and network expertise. Thus, it can also serve as an intellectual barrier to most of the potential intruders of your wireless network. Controlling the Radiation ZoneWhen a wireless network is active, it broadcasts radio frequency (RF) signals. These signals are used to transmit the wireless data from an access point to the WNIC and back again. The same signal is also used in ad-hoc networks, or even between PDAs with 802.11 WNICs. Although this particular use of RF technology is relatively new, the use of the radio wave is very old. In fact, one of the closest relatives to the wireless network is the wireless phone. Ironically, some wireless phones have started to incorporate the 2.4GHz range, which is the same frequency used by 802.11b WLANs. When using a radio wave, there is a range limit imposed by the signal. Because of interference from various obstacles, including sunlight and air, the signals weaken the farther one travels from the broadcasting unit. If you could see these signals, you might see a circular, deteriorating globe that is strongest at the center. This virtual globe is known as the radiation zone . What many people do not realize is that the radiation zone can be quite large, depending on the location and strength of the base unit. Although solid walls, metal beams, and electrical wiring can impede the signal, these zones are often much larger than advertised on the WLAN's documentation. To illustrate this, you can perform a simple test using a wireless phone. Place your phone base near an open window and call someone you know. Then start walking. You might find that you can walk several hundred yards down the street and still maintain a relatively clear connection. In fact, depending on weather, hanging wires, and the strength of your phone's antenna, you could travel up to twice the distance advertised by the phone's documentation. This applies to your WLAN as well (see Figure 12.6). Figure 12.6. WLAN leakage due to a fully powered access point located at the side of a building. In addition to the fact that a radiation zone might extend far beyond an office's or home's physical boundaries, the tools and technology used by hackers can amplify the signal. Using a positional antenna discussed in Chapter 1, "Wireless Hardware," a hacker can narrow the window of detection and pick up signals from farther away. These same antennas are used to legitimately "push" wireless signals up to 20 miles or more. In other words, you will not be able to look out your window and see this hacker; he will probably be several blocks away. As a bonus for the hacker, the wireless signals have a tendency to bounce around in metropolitan areas, which means that even an unamplified signal can be detected several blocks in any direction. Fortunately, there are several methods with which you can control this signal bleeding . The first method is to place the access point in a central location in your office. Although this might be obvious, many access points are set up on an outside room next to a wall, and worse , near a window. If there is a need to install several access points across a large space, try to position them as close to the center of the building, or as far away from outside walls, as possible. For example, in our house example, a simple movement of the access point has an obvious impact on the leakage of the wireless signals (see Figure 12.7). Figure 12.7. WLAN bleed reduced because of central positioning. In addition to managing the physical position of the access point, you can also control the signal sent out from the access point. In particular, you can control the power of the signal, which determines how far the signal travels. You can also control the direction of the signal by positioning the antenna and disabling one antenna to cut off one side of the access point. For example, in the Linksys BEFW1154, you can completely turn off the signal on either the right or left antenna (see Figure 12.8). This option is very handy in eliminating interference between access points and in restricting unneeded signals. Figure 12.8. Antenna control. Although this particular access point does not have the power option, such a feature comes with a few higher end models. If you are only going to use the access point in a small conference room, you do not need a high-powered, top-of-the-line access point. A low-budget model will suffice. By using antenna management techniques, you can control the range of your WLAN. In high-rise buildings or apartment complexes, this can be a serious issue. Interferenceand nosy neighborscan quickly become a problem. By removing one antenna, reducing the output, and adjusting the position of the antenna, you can effectively keep the signal within a tight range (see Figure 12.9). Figure 12.9. Minimized leakage inside a residence. Regardless of how much you control the radiation zone, there is a high chance that it will bleed slightly. In other words, this method of protection should be used in conjunction with other methods to completely secure the WLAN. Defensive Security Through a DMZA DMZ , or demilitarized zone , is a concept of protection. A DMZ typically defines where you place servers that access the Internet. In other words, a Web server or mail server is often set up in a DMZ. This allows any Internet user to access the allocated resources on the server, but if the server becomes compromised, a hacker will not be able to use the "owned" computer to search out the rest of the network. Technically, a DMZ is actually its own little network, separate from the internal network, and separate from the Internet. A firewall will often protect the DMZ from external threats. However, because the server must communicate to the outside world, the firewall will be configured to ignore many types of connections. In addition to isolating the servers, the DMZ is often set up to be easily accessible to internal network users. This is accomplished by the firewall hardware and software, which usually comes with a port set aside just for such a DMZ. For example, NetScreen has three ports: one for the Internet connection, the second for the internal connection, and the third for a DMZ into which a hub or switch can be connected to allow multiple servers. This same port could be used to connect an access point, which is really nothing more than a wireless hub/switch. By doing this, you are basically placing the WLAN in a semi-trusted zone that is expected to be attacked by hackers. By operating with the mentality that your WLAN could already be owned, you can more appropriately plan who and what you allow to access the internal network. However, while this type of protection can help protect internal resources, it will not protect the wireless network users. Therefore, the DMZ should be just one part of your wireless security plan. |
EAN: 2147483647
Pages: 171
 Run and perform the steps in the following sections, depending on the operating system.
Run and perform the steps in the following sections, depending on the operating system.