6.15 Packet Analysis
| < Day Day Up > |
| In this section, we examine a sample packet as captured by a sniffer. It is important to understand how to edit packets at the byte level so that you can understand how fragmentation attacks work. Figure 6-6 shows the hex dump of a sample packet that we have captured. Figure 6-6. Hex dump of a sample packet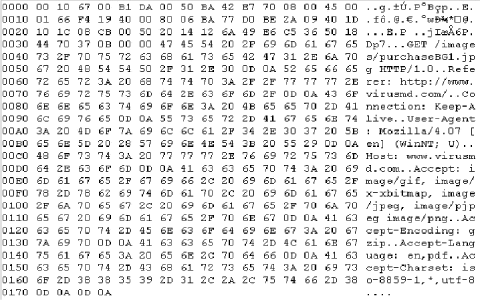 We will focus on the first 54 bytes, which comprise the frame header (14 bytes), the IP header (20 bytes), and the protocol header (20 bytes), as seen here: 00 10 67 00 B1 DA 00 50 BA 42 E7 70 08 00 45 00 01 66 F4 19 40 00 80 06 BA 77 D0 BE 2A 09 40 1D 10 1C 08 CB 00 50 20 14 12 6A 49 E6 C5 36 50 18 44 70 37 0B 00 00 Scanning from left to right, we read the first 14 bytes; they comprise the frame header, which in this packet provides us with the source MAC address ( 00 10 67 00 B1 DA ) and the destination MAC address ( 00 50 BA 42 E7 70 ). The final 08 00 marks the beginning of the IP datagram. The next 20 bytes comprise the IP header, as shown here: 45 00 01 66 F4 19 40 00 80 06 BA 77 D0 BE 2A 09 40 1D 10 1C At the end of this header are the source IP address ( D0 BE 2A 09 ) and the destination IP address ( 40 1D 10 1C ). Converting the destination IP address to decimal gives us the following: 40 1D 10 1C = 62.29.16.28 which is the IP address that resolves to the URL http://www.virusmd.com . The final 20 bytes form the TCP header, shown here: 08 CB 00 50 20 14 12 6A 49 E6 C5 36 50 18 44 70 37 0B 00 00 This section contains the following information:
These are the TCP flags:
|
| < Day Day Up > |
EAN: 2147483647
Pages: 211