2.4 Transport-Layer Protocols: TCP, UDP, and SCTP 2.4.1 Transmission Control Protocol Transmission Control Protocol, or TCP as it is commonly referred to, is a transport-layer protocol that runs on top of IP. The best explanation of TCP is from RFC 793: TCP is a connection-oriented, end-to-end reliable protocol designed to fit into a layered hierarchy of protocols which support multi-network applications. The TCP provides for reliable inter-process communication between pairs of processes in host computers attached to distinct but interconnected computer communication networks. Very few assumptions are made as to the reliability of the communication protocols below the TCP layer. TCP assumes it can obtain a simple, potentially unreliable datagram service from the lower level protocols. In principle, the TCP should be able to operate above a wide spectrum of communication systems ranging from hard-wired connections to packet-switched or circuit-switched networks. TCP was specifically designed to be a reliable end-to-end byte stream transmission protocol over an unreliable network. The IP layer does not provide any guarantees that datagrams will be delivered with any degree of reliability. Hence it is up to the upper-layer protocol to provide this reliability. The key functionality associated with TCP is basic data transfer. -
Basic Data Transfer. From an application perspective, TCP transfers a contiguous stream of bytes through the network. The application does not have to bother with chopping the data into basic blocks or datagrams. TCP does this by grouping the bytes in TCP segments, which are passed to IP for transmission to the destination. -
Reliability. TCP assigns a sequence number to each byte transmitted and expects a positive acknowledgment (ACK) from the receiving TCP. If the ACK is not received within a timeout interval, the data are retransmitted. Since the data are transmitted in blocks (TCP segments), only the sequence number of the first data byte in the segment is sent to the destination host. -
Flow Control. The receiving TCP, when sending an ACK back to the sender, also indicates to the sender the number of bytes it can receive beyond the last received TCP segment, without causing overrun and overflow in its internal buffers. This is sent in the ACK in the form of the highest sequence number it can receive without problems. -
Multiplexing. Multiplexing is achieved through the concept of ports. A port is a 16-bit number used by the host-to-host protocol to identify to which higher-level protocol or application process it must deliver incoming messages. Two types of ports exist: (1) Well-known: these ports belong to standard applications servers such as telnet, ftp, and http. The well-known ports are controlled and assigned by the Internet Assigned Numbers Authority (IANA). Well-known ports range from 1 to 1023. (2) Ephemeral: A client can negotiate the use of a port dynamically and such ports can be called ephemeral. These ports are maintained for the duration of the session and then released. Ephemeral ports range from 1024 to 65535. Multiple applications can use the ports as a means of multiplexing for communicating with other nodes. -
Connections. The reliability and flow control mechanisms require that TCP initializes and maintains certain status information for each data stream. The combination of this status, including sockets, sequence numbers, and window sizes, is called a logical connection. Each connection is uniquely identified by the pair of sockets used by the sending and receiving processes. TCP entities exchange data in the form of segments. A segment consists of a fixed 20-byte header and an optional part followed by zero or more data bytes. Figure 2-5 shows the structure of the TCP header. Figure 2-5. TCP header. 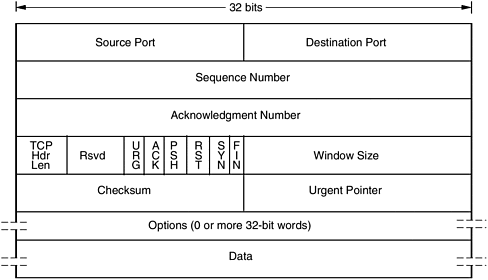 The fields in the TCP header are desribed as follows : -
Source Port and Destination Port: These fields identify the local endpoints of a connection. Each TCP entity decides how to allocate its own ports. A number of well-known ports are reserved for specific applications (e.g., FTP). -
Sequence and Acknowledgment Number: Indicate the sequence number of the packet. The ACK number specifies the next byte expected, and not the last byte correctly received. -
TCP Header Length: Indicates how many 32-bit words are contained in the TCP header. This is required because of the Options field, which is of variable length. -
Reserved: For future use. -
The six 1-bit flags are as follows: URG ” Set to 1 if the Urgent pointer is in use. ACK ” Set to 1 to indicate that the Acknowledgment number is valid. PSH ” Indicates PUSHed data. The receiver is requested to deliver the data to the application and not buffer it until a full buffer has been received. RST ” Used to reset a connection. SYN ” Used to establish connections. FIN ” Used to release a connection. -
Window Size: This field tells how many bytes may be sent starting at the byte acknowledged . Flow control in TCP is handled using a variable-size sliding window. -
Checksum: Provided for reliability. It checksums the header and the data (and the pseudoheader when applicable ). While computing the checksum, the Checksum field itself is replaced with zeros. -
Urgent Pointer: Used to indicate a byte offset from the current sequence number at which urgent data are to be found. -
Options: This field was designed to provide a way to add extra facilities not covered by the regular header. TCP has been the workhorse of the Internet, and a significant portion of Internet traffic today is carried via TCP. The reliability and congestion control aspects of TCP make it ideally suited for a large number of applications. TCP is formally defined in RFC 793. RFC 1122 provides some clarification and bug fixes, and a few extensions are defined in RFC 1323. 2.4.2 User Data Protocol User Data Protocol (UDP) is a connectionless transport protocol. UDP is basically an application interface to IP. It adds no reliability, flow control, or error recovery to IP. It simply serves as a multiplexer/ demultiplexer for sending and receiving datagrams, using ports to direct the datagrams. UDP is a light-weight protocol with very minimal overhead. The responsibility of recovering from errors, retransmission, etc., is up to the application. Applications that need to communicate need to identify a target is more specific than simply the IP address. UDP provides this function via the concept of ports. The format of the UDP datagram is shown in Figure 2-6. Figure 2-6. UDP header. 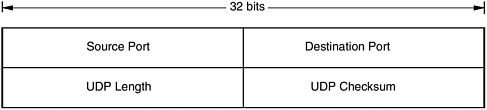 The following is a description of the fields of the UDP header: -
Source and Destination Port: The two ports serve the same function as in TCP; they identify the endpoints within the source and destination nodes. -
UDP Length: This field includes the 8-byte UDP header and the data. -
UDP Checksum: The checksum is computed over the UDP header, the IP header, and the data. Although UDP does not implement flow control or reliable/ordered delivery, it does a little more work than simply to demultiplex messages to some application ”it ensures the correctness of the message via the checksum. UDP uses the same cheksum algorithm as IP. UDP is described in RFC 768. 2.4.3 Stream Control Transmission Protocol Stream Control Transmission Protocol (SCTP) is described in RFC 2960 and is a recent addition to the transport suite. SCTP is a reliable transport protocol operating on top of a connectionless packet network such as IP. The main services offered by the protocol are as follows: -
Acknowledged error-free nonduplicated transfer of user data -
Data fragmentation to conform to discovered path MTU size -
Sequenced delivery of user messages within multiple streams, with an option for order-of-arrival delivery of individual user messages -
Optional bundling of multiple user messages into a single SCTP packet -
Network-level fault tolerance through supporting of multihoming at either or both ends of an association SCTP was primarily designed to carry PSTN signaling messages over an IP network. But the protocol is capable of supporting many different types of applications as well. SCTP can be considered as having the properties of TCP while still being lightweight. The SCTP transport service can be decomposed into a number of functions: -
Association startup and takedown: An association is initiated by a request from the SCTP user. A cookie-based mechanism using four-way handshakes ensures security. It provides for graceful close (i.e., shutdown) of an active association on request from the SCTP user. -
Sequenced delivery within streams: The term stream is used in SCTP to refer to a sequence of user messages that are to be delivered to the upper-layer protocol in order with respect to other messages within the same stream. A user can specify at association startup time the number of streams to be supported by the association (and negotiated with the remote end). The sequencing can be bypassed if required. -
User data fragmentation: When needed, SCTP fragments user messages to ensure that the SCTP packet passed to the lower layer conforms to the path Mean Transfer Unit (MTU). -
Acknowledgment and congestion avoidance : The acknowledgment and congestion avoidance function is responsible for packet retransmission when timely acknowledgment has not been received. Packet retransmission is conditioned by congestion avoidance procedures similar to those used for TCP. -
Chunk bundling: The chunk-bundling function of SCTP is responsible for assembly of the complete SCTP packet and its disassembly at the receiving end. Each chunk may contain multiple messages (or data). -
Packet validation: A mandatory Verification Tag field and a 32-bit Checksum field are included in the SCTP common header to ensure packet validity. -
Path management: The SCTP path management function chooses the destination transport address for each outgoing SCTP packet based on the SCTP user's instructions and the currently perceived reachability status of the eligible destination set. The path management function monitors reachability through heartbeats when other packet traffic is inadequate to provide this information and advises the SCTP user when reachability of any far-end transport address changes. The path management function is also responsible for reporting the eligible set of local transport addresses to the far end during association startup, and for reporting the transport addresses returned from the far end to the SCTP user The SCTP packet format is shown in Figure 2-7. Figure 2-7. SCTP header. 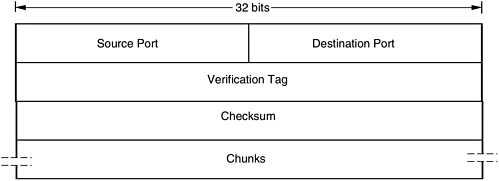 The fields of the SCTP header are described as follows: -
Source Port and Destination Port: These identify the endpoints within the source and destination nodes. -
Verification Tag: The receiver of this packet uses the Verification Tag to validate the sender of this SCTP packet. On transmit, the value of this Verification Tag must be set to the value of the Initiate Tag received from the peer endpoint during the association initialization. -
Checksum: This field contains the checksum of this SCTP packet, which is computed over the SCTP common header and one or more control or data chunks . SCTP is a relatively new protocol, and its implementation is only now beginning to occur. The implementation of SCTP will probably not be as widespread as TCP and UDP in the next few years . |


