0216-0218
Page 216
You might ask, "Why should a tool for my employees be on the Web?" Remember the emerging architecture of intranets and the network computer. If a company builds an internal intranet to standardize software and save money, this Java-based tool will fit in perfectly .
If your company has many manufacturing locations, using the Web is just as safe as using a modem and simple phone lines to dial up a central computer as a "dumb terminal." It is more efficient and easier to use the standard Web browser technology than to install an arcane emulation tool on everyone's PC and worry about the networking and supporting each PC and their different configurations. With a browser, you already buy into a standard way of displaying remote information.
Oracle Web Suppliers
If you build an airplane engine, you must also integrate the order for the engine with many smaller orders, based on requisitions from your engineers to the many suppliers that you use. With Oracle Web Suppliers, you can view the thousands of bolts and screws that you bought from a company by displaying your purchase order online along with the company's inventory and general catalog of parts . As a supplier, you can let the airplane company that wants your engine to view all the supplier agreements and your inventory of existing engines.
Oracle Web Suppliers also allows your suppliers to view the purchase orders that you send to them. This way, fewer mistakes and rejected shipments occur because you can cross-check items before they are shipped. Your suppliers can also view shipping and billing information related to your purchase orders.
Encryption and Electronic Commerce
Everyone worries about Web security because the World Wide Web is a tool that everyone in the world can access. How could you ever consider sending secure financial information over the Web? The concerns are valid, but what about ordering products over an open phone line? The telephone is also available to anyone in the world. If you step back a moment, you understand that Web-based commerce can actually be more secure than previous forms because of the role of computer software and encryption.
Encryption and Decryption: The Spy and Walt Whitman
Basic encryption is simply changing a message, which can be a credit-card number, into gibberish. The method that you use to change your message is the encryption algorithm. The key to using the gibberish that you encrypted is that someone needs another algorithm to decrypt the message back into its meaningful form. He needs a decryption algorithm, as shown in Figure 10.4.
Page 217
Figure 10.4.
To send a secret
message, you need to
first encrypt it and then
decrypt it.
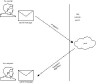
Here is a simple example of a cycle of encryption-decryption. Suppose you want to send a fellow spy the message, "Meet me at 10 tonight." To decrypt, I count the number of letters in that statement: 18. (I do not count spaces.) After this, I use Walt Whitman's Leaves of Grass poem called "Song of Myself." I turn to Chapter 18:
"These are really the thoughts of all men in all ages and"
I now list each letter of the above sentence in its order in the alphabet, but I am going to use only the first 18 letters, since our string length is 18:
1. T - 20 6. a-1 9. r-18 15. t-20 18. t-20 2. h - 8 7. r-18 10. e-5 16. h-8 3. e - 5 8. e-5 11. a-1 17. e-5 4. s - 19 12. l-12 5. e - 5 13. l-12 14. y-25
Now I have a sequence of numbers that I will "add" to the original message to encrypt it. For example, when I encounter the letter E in the third spot of my message, I add the third ordered letter in the list from Walt Whitman's line. I find E, which is the fifth letter of the alphabet,
Page 218
and when I add 5 and 5, I get 10, so I replace the E with the tenth letter, J. If, instead, I had a letter Y, with position 25 in the alphabet, I go "around" the alphabet to the letter D when I add my E. Now, I encrypt a sample of the message with the preceding encryption algorithm:
m 13 + 20 = 33 -26 = 7 = G (Moving around the alphabet) e 5 + 8 = 13 = M e 5 + 5 = 10 = J t 20 + 18 = 38 - 26 =12 = L (Again moving around the alphabet)
In this example, the encrypted file starts as GMJL. Someone who knew to re-create the encryption key from the writings of Walt Whitman could again decrypt this message by subtracting the same numbers using the line from the poem. Without the knowledge that the encryption key was derived from Walt Whitman's poem, it would take the largest computers in the world some time to figure out a series of these messages.
Web Encryption
The problem with basic encryption is that if someone spills the beans about a key, the game is up.
Another problem is that business needs a way to let people encrypt with a key that cannot decrypt. If the key can be used both ways, a customer can steal anyone's credit-card number once he encrypts his own.
The newer methods of encryption such as PGP (Pretty Good Privacy) use two keys, a public key and a private key. If I communicate with a merchant through a computer, I use an encryption algorithm with that merchant's public key. What makes the algorithm more effective is that, unlike the Walt Whitman algorithm, I can encrypt using only this key. I cannot decrypt. This two-key cycle is shown in Figure 10.5.
When the merchant receives this key, he can decrypt using the private key along with the public key. This allows for commerce with a public-key encryption that sends a package of noise that only the merchant with the private key can decrypt. In the first example with Walt Whitman, if the merchant gives me the algorithm to encrypt, I can also decrypt, which lets me steal everyone's messages to that merchant.
Along with message encryption, the consumer needs to know that he or she is giving the credit-card number to a real merchant. The merchant needs to know it is communicating with the actual user of the credit card. You accomplish this with an electronic signature that is certified by a third party. This verification is called a digital signature. Oracle's Internet Commerce Server uses the VeriSign digital signature, which is becoming a standard for electronic commerce.
When a user's browser stumbles onto a secure site where business takes place, the Web site sends a message to the browser, setting it in a Secure Socket Layer protocol. From here, it might even prompt the browser to generate encryption keys that the electronic commerce Web site is later able to decrypt using a private key. (See Figure 10.6.)
EAN: 2147483647
Pages: 391