Chapter 15: Risk Management
In this chapter, we summarize some general remarks about risk management and how the Internet and the WWW have changed (or are about to change) the way we think about it. More specifically , we introduce the topic in Section 15.1, elaborate on formal risk analysis in Section 15.2, address some alternative approaches and technologies for risk management in Section 15.3 and draw some conclusions in Section 15.4. Some parts of this chapter are taken from Chapter 21 of [1].
15.1 Introduction
In practice, it is often important to know the risks one faces when adopting a new technology. This is particularly true for the Internet and the WWW. A company or organization that considers establishing a presence on the Web is very likely (and well advised) to question the vulnerabilities, threats, and related risks.
According to RFC 2828 [2], these terms (and some related terms) can be defined as follows :
-
A vulnerability is a flaw or weakness in a system s design, implementation, or operation and management that could be exploited to violate the system s security policy. [1]
-
A threat is a potential for violation of security, which exists when there is a circumstance, capability, action, or event that could breach security and cause harm.
-
A risk is an expectation of loss expressed as the probability that a particular threat will exploit a particular vulnerability with a particular harmful result.
-
Risk analysis (or risk assessment ) is a process that systematically identifies valuable system resources and threats to those resources, quantifies loss exposures (i.e., loss potential) based on estimated frequencies and costs of occurrence, and ( optionally ) recommends how to allocate resources to countermeasures so as to minimize total exposure.
-
Last but not least, risk management is a process of identifying, controlling, and eliminating or minimizing uncertain events that may affect system resources.
The individual steps in a risk management process are illustrated in Figure 15.1. On the left side, a vulnerabilities analysis must be performed. This analysis has to reveal the vulnerabilities that are relevant for a given situation (i.e., a given IT environment). On the right side, a threats analysis must be performed. A threats analysis, in turn , requires an explicit threat model; that is, a model that elaborates on who is capable and motivated to attack the system in question. In the absence of such a model, one cannot hope to estimate the threats and the corresponding risks. Note that it is something completely different to secure a corporate intranet against foreign intelligence services than it is to secure a corporate intranet against casual attacks. Based on the results of a vulnerabilities analysis and a threats analysis, a risk analysis can be performed. The risk analysis quantifies loss exposures based on estimated frequencies and costs of occurrence.
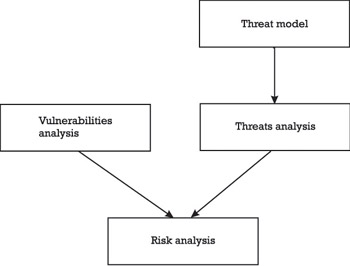
Figure 15.1: The individual steps in a risk management process.
From a more general point of view, everything we do in daily life ”either professionally or privately ”is driven by risk management considerations. If there is no vulnerability or threat (and, consequently, no risk), we generally do not spend any time or money in security and safety. If, however, there are risks and these risks are severe or appear severe to us in terms of expected losses, we are generally willing to spend large amounts of time or money in security and safety. The point is that we are not always aware that some risk management considerations are being performed in our brains . For example, if somebody tells you to jump from a building, the expected loss (i.e., the loss of life) is generally too high to be tolerable. Consequently, you are not going to jump (at least we hope so). If, however, someone asks you for the current time, there is no loss to expect. [2] Consequently, you would tell this person the current time. All these risk management considerations are done subconsciously (as a learned behaviour) and we may not even be aware of them. Also, the same risks are perceived differently by different people. Consequently, risk perception is also an important topic that complements risk management.
In the IT world, we are not yet fully accustomed to making risk management considerations. This is because the field is still new, dynamically changing, and not well understood . Also, there are hardly any statistical investigations we can use to make some long- term claims about relevant risks. Consequently, we have to deliberately consider each risk individually. If this is done, it is usually done in a labor- intensive process called formal risk analysis.
[1] According to this definition, one could argue that a system without a security policy is not vulnerable because there is nothing that could be exploited to violate the policy. On the other hand, one could also argue that there is a policy for every system, even if it exists only in the owner s mind.
[2] There may still be a loss to expect, namely, if the questioner for the current time only wants to distract you so you can be robbed more easily.
EAN: 2147483647
Pages: 142