Security vs. Functionality (A Business Justification)
| | ||
| | ||
| | ||
So back to the theories behind vulnerability assessments The information technology world has come to know a very inversely proportional concept when it comes to security: the more secure an organization's information technology (IT) infrastructure is kept, the less functional it becomes. In a perfect world, there would be no miscreants and IT services could be kept open for the world to use. In this same perfect world, there would be no locks on doors or fences at perimeters . Since we do not live in such a world, organizations must find the appropriate balance between security and functionality. This concept is reflected in a common saying used by security analysts: "Security and functionality lie on opposite sides of the same balance."
In order to achieve the appropriate balance, an organization's approach should consider every aspect of a solution or initiative prior to deployment. Instead of focusing solely on lockdown , organizations and security firms servicing organizations alike must determine an optimal solution that balances security and functionality. Organizational impacts must be analyzed based on other key competencies besides security. Functionality has been mentioned but scalability, performance, and, of course, budget are all factors that must be considered in addition to security.
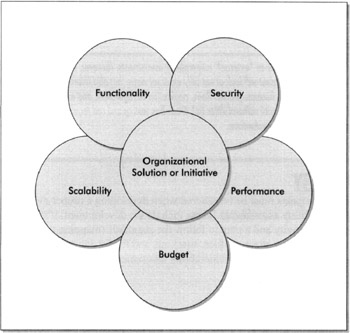
As you can see, security is only one competency to consider. The remaining four areas must also be accounted for when securing IT services and assets. A "completely secured" application or service most likely will not serve its intended purpose because it will be utterly unusable from a business perspective. In other words, once an application or service has been protected completely, it likely won't accept any input or provide any feedback, making it useless. Therefore, the concept of the "balance" holds true; security engineers are always looking for the right balance of security and functionality.
Keeping this in mind, security becomes even more challenging because compromises must be made to attain an acceptable level of security and functionality. Just as securing an organization's services is important, verifying that security is just as, or arguably more, important for ensuring ongoing protection. Vulnerability assessments conducted on an ongoing basis assist organizations with ensuring acceptable security controls are in place while maintaining the functionality required. Today, factors such as the Health Insurance Portability and Accountability Act (HIPAA), Sarbanes-Oxley, and Gramm-Leach-Bliley mandate that some degree of validation is conducted within organizations. These types of mandates increase the business justification for assessments purely from a legal standpoint. Organizations' management teams now realize securing the organization is not enough; ongoing assessments must also be conducted to ensure the organization is living up to its standards and policies, thereby staying secure.
The remainder of the chapter will outline the secrets of success when conducting vulnerability assessments. You will learn a winning methodology to be used while gathering information, building a theatre of war, determining attack profiles, conducting attacks, and defending your organization's infrastructure.
| Note | Chapters 1315 focus on "external" vulnerability assessments. However, we should mention that a complete vulnerability assessment will look at not only external views, but also internal views, internal system and host configurations, business process flows, application configuration, and even software coding standards (which is where the real vulnerabilities lie). Black box testing and red teaming are not completely effective measures of security evaluations. |
| | ||
| | ||
| | ||
EAN: 2147483647
Pages: 120