How Does Wireless LAN Work?
The 802.11b standard defines two modes: infrastructure mode and ad hoc mode. In infrastructure mode, the wireless network consists of at least one access point connected to the wired network infrastructure and a set of wireless end stations . This configuration is called a Basic Service Set (BSS) and each BSS has a SSID. An Extended Service Set (ESS) is a set of two or more BSSs forming a single subnetwork that share an SSID. Since most corporate WLANs require access to the wired LAN for services (file servers, printers, Internet links), they will operate in infrastructure mode. Access points typically cover a range of 300 to 500 feet. The number of access points for configuration of a WLAN in infrastructure mode varies depending on the size of the physical area requiring coverage, network configuration, physical limitation of the coverage areas and the number of users per segment.
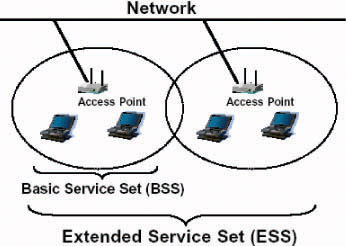
Figure 1: Basic and Extended Service Sets
Ad hoc mode (also called peer-to-peer mode or an Independent Basic Service Set, or IBSS) is simply a set of 802.11 wireless stations that communicate directly with one another without using an access point or any connection to a wired network. This mode is useful for quickly and easily setting up a wireless network anywhere that a wireless infrastructure does not exist or is not required for services, such as a classroom, meeting area, or airport, or where access to the wired network is barred (such as for consultants at a client site). In a classroom setting, the IBSS works well for sharing files with members of a project team or submitting completed work to a central folder on an instructor s computer.
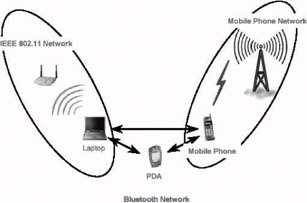
Figure 2: Notional Wireless Network
To take advantage of the 802.11b in either mode you have to have a wireless network interface card (NIC) installed in your device. The NIC is installed in an available PCMCIA slot and configured for use within the WLAN. Newer computers come with Wi-Fi capability as a part of the standard configuration and do not require a NIC.
Users become members of WLAN by means of authentication. The 802.11b protocol has two means to authenticate users: open system authentication and shared key authentication.
There is no authentication required to become a member of a WLAN that is set up as an open system. The client simply responds with a MAC address to gain access. The client, without any true means to authenticate, must trust that it is communicating with an actual access point. Often, clients are not granted access because the SSID is not known or passed properly from the access point. It is important to know the unique identifier in order to ensure access. With most applications this handshake is accomplished automatically and unbeknownst to the user .
In shared key authentication, a challenge-response technique is used to grant access to the WLAN. Karygiannis and Owens (2002) explain that the client, using a cryptographic key that is shared with the access point, encrypts the challenge and returns the result to the access point. The access point decrypts the result computed by the client and allows access only if the decrypted value is the same as the random challenge transmitted. This authentication method is a rudimentary cryptographic technique, and it does not provide mutual authentication. That is, the client does not authenticate the AP, and therefore there is no assurance that a client is communicating with a legitimate AP and wireless network. This is seen as a disadvantage of the current wireless implementation.
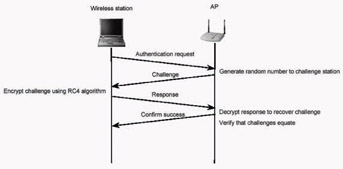
Figure 3: Challenge and Response Handshake
Security is the number one disadvantage of installing a WLAN. Often stated as the wild, wild west of networking, WLANs offer numerous opportunities for intruders to infiltrate the enterprise. Establishing a WLAN is like placing a piece of network cable out of your window with a sign that says free Internet connection . People may want to test the line to see if it is active. Once they find activity on the line they will try to expand their access and privilege as far as the wired LAN s security allows. The disadvantages are overshadowed by the distinct advantages offered by installing a WLAN.
The advantages are:
-
Mobility: Users not tied down to one location and are able to access files, network resources, and the Internet without having to physically connect to the network with wires.
-
Increased Productivity: Users of mobile devices work more for the corporation when they are not physically in the building. You will find mobile users in trains, planes, buses and cars working with their mobile device. Some users are more productive once they move outside the confined spaces of the office and into more comfortable common areas.
-
Rapid Installation: The effort required for installation is reduced because network connections are made almost immediately. No walls are removed, no one is sent into the floors or ceiling to pull wire and no modifications have to be made to the wiring closet.
-
Flexibility: Users can quickly install a small WLAN for temporary needs such as a classroom, conference and other temporary venues .
-
Scalability: WLAN network topologies can easily be configured to meet specific application and installation needs and to scale from small peer-to-peer networks to very large enterprise networks that enable roaming over a broad area.
EAN: N/A
Pages: 113