What Is a Domain Tree? What Is a Forest?
| The Active Directory gives you one single enterprise-wide namespace. This namespace is used for user accounts, resource objects, application configuration information, and so on. What you decide to store in the directory, beyond the default objects set up by the installation process, is up to you. The namespace can be global, provided you organize your domains into a domain tree. A domain tree is nothing more than a method of organizing the domains in your enterprise into a structure so that they all share a common directory schema and a contiguous namespace. Although a domain tree is a structure formed by a collection of domains, a forest is a collection of domain trees. The namespace in the forest does not have to be contiguous , as it does in the tree, so a forest can be used to link disparate domain trees in the organization so that trust relationships still can be used to allow a single user logon in the network. To understand what a domain tree or a forest is, you must know what it is replacing in the Windows NT networking scheme. Domain Models ”May They Rest in PeaceIn Windows NT, the domain was used to group users and resources with a common security policy to simplify administrative tasks . In large organizations, a single domain was not sufficient to hold all the users and resources, and was not an efficient method of administering user rights and privileges or resource protections . Because of this, multiple domains were created and linked in what is termed a trust relationship . This trust relationship allowed users from one domain to be granted access rights to resources in another trusting domain. A trust relationship in earlier versions of Windows NT could be a one-way or a two-way relationship. In a one-way trust relationship, one domain would trust the users that had been authenticated by another domain. The administrator in the trusting domain could grant users (or groups of users) from the trusted domain access rights in the local trusting domain. In a two-way trust relationship, the relationship existed in both directions. The trust relationship is not transitive. That is, if domain A has a trust relationship that allows its users to be assigned rights in domain B, and if domain B has a trust relationship that allows its users to be assigned rights to resources in domain C, a user in domain A cannot be granted rights in domain C by use of these trust relationships. That would require that domain A establish a separate trust relationship with domain C. The way domains were organized into user or resource domains, and how the trust relationships were set up, led to the development of several domain models that could be used, depending on the size of your enterprise and the methods used to administer them. These were the single domain, multiple domain, master domain, and multiple-master domain models. Because the domain essentially was the boundary for the security accounts manager (SAM) database, you had two basic choices. You could put all your user accounts into a single master domain, and then grant them access rights to objects in resource domains, or you could put users into separate domains, depending on your organization, and maintain a complicated set of trust relationships and administrative policies. The headache associated with managing multiple trust relationships ”and moving users to and fro when reorganizations occurred ”is one of the major drawbacks of the SAM-based domain models. Partitioning the Active Directory into DomainsWhen you install Windows 2000/Server 2003 and create a new domain, you are given several choices that decide how the domain will fit into an Active Directory tree. You can create a new forest or become part of an existing forest and create a new tree, making this new domain the first domain in the new tree. Or you can make the new domain a child domain in a domain tree that already exists in the forest. Each domain in the domain tree is a security boundary in the Active Directory, just as it is in previous versions of Windows NT. However, you no longer have to create one- or two-way trust relationships between domains for users to be granted access rights and privileges in other domains that are in the same domain tree. When a Windows domain joins a domain tree, a two-way transitive trust relationship , based on the Kerberos security authentication method, is automatically established between the child domain and its parent domain in the tree. Because the trust relationship is transitive (two-way), there is no need to manually configure additional trust relationships with other domains that exist in the domain tree. This means that after your domain is created and joined to a domain tree, your users can be granted access rights to resources in any other domain in the tree without the need to further create a complicated set of trust relationships with other domains.
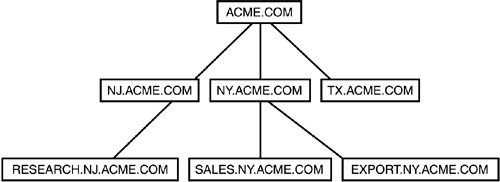
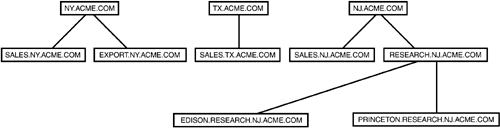
Each domain in the tree holds the portion of the Active Directory database that represents the objects found in that domain. However, the namespace is contiguous throughout the tree. Each domain controller in the domain holds a complete replica of the directory for that domain. And, to help reduce network traffic and administrative overhead, you can create additional replicas of the domain's portion of the directory and place it close to users in other domains that frequently access the resources in your domain. You only need to create an additional domain controller. This may seem similar to the primary domain controller/backup domain controller mechanism that Windows NT 4.0 uses. However, you no longer have to promote a backup domain controller (a BDC) to become a primary domain controller should the PDC fail. Instead, any peer domain controller can handle all authentication requests, and other Active Directory requests , within a domain, without operator intervention. A Domain Is Still a DomainThe domain in Windows 2000/Server 2003 is still a security boundary, just like it was in Windows NT. Domain administrators can still take command and exert their authority over all users and resources in the domain. From that perspective, nothing has changed. However, the management of your relationships with other domains is now much easier. The two-way transitive trust relationships are set up automatically, so you don't have to coordinate managing this with other administrators throughout the network. If you upgrade from a previous version of Windows NT, all your groups and users are migrated into the Active Directory under your same domain. You can manage them as you always have, although there are new tools (using the MMC interface) that are used instead. For more information about how to manage users (and computers) in the Active Directory, see Chapter 41. Active Directory Trees and ForestsAs discussed earlier in this section, a domain tree is a collection of domains that have a contiguous namespace, whereas trees in a forest can have a noncontiguous namespace. Contiguous namespace means that the object in each child domain in the tree has the name of its parent domains prefixed to its distinguished name . This also means that the names used to identify each child domain will have the names of the parents prefixed. Figure 31.1 shows an example of a domain tree. The domain tree starts at the top and flows down the tree, rather than from the bottom up. Figure 31.1. A domain tree is a contiguous namespace. In this domain tree, the most senior parent in the tree is the acme.com domain. Beneath that are three child domains, nj.acme.com, ny.acme.com, and tx.acme.com. Under the New York child domain, you can see a sales domain (sales.ny.acme.com) and another domain called export.ny.acme.com. This tree could be further expanded by adding additional child domains to any of the domains in the tree. The way you construct the fully qualified domain name for a domain positions it in the tree structure. In the best of all possible worlds , each enterprise would have exactly one domain tree and one large contiguous namespace. However, in this rapid-paced business world, nothing remains the same for long, including business organizational units. Corporate mergers and acquisitions, for example, can bring in large numbers of users and resources that must be incorporated quickly into the network structure. In this situation, it might not be possible to easily include the acquired assets into the naming structure. However, you can still join two disparate domain trees. You can't put them into the same tree because the naming for all objects would not be contiguous. You can, however, join domain trees into a structure called a forest. A forest is like a domain tree, but the namespace does not have to be contiguous throughout the forest. The directory schema is still common for all domains, and you can establish trust relationships between the trees. Users can still use a single logon to access resources in domains that reside in different domain trees (see Figure 31.2). Figure 31.2. Domain trees with disjointed namespaces can exist in a forest. |
EAN: 2147483647
Pages: 434
- Integration Strategies and Tactics for Information Technology Governance
- Linking the IT Balanced Scorecard to the Business Objectives at a Major Canadian Financial Group
- A View on Knowledge Management: Utilizing a Balanced Scorecard Methodology for Analyzing Knowledge Metrics
- Governance in IT Outsourcing Partnerships
- Governance Structures for IT in the Health Care Industry