Windows 2000 User Groups
| You need to understand several concepts about user groups in Windows 2000/.NET before you begin to create them. Groups are helpful because they simplify administrative tasks when you have groups of users that must be treated similarly when it comes to rights and permissions. Second, because groups can be limited in scope, they can be useful for security purposes, limiting the computers or domains in which a user can be granted access. Choosing a Group Based on the Group's ScopeGroups each have a scope, which is basically the area of the domain or global forest that the group covers. By having several types of groups, each with its own particular kind of membership and scope, you can put together combinations that should solve most of your administrative needs for managing users with similar needs. The types of groups, and the scope implied by each, are as listed here:
As described previously, groups can be members of other groups just like users, and this is where things can become a little complicated. For example, a domain local scope group can have the following as members:
Note that the domain local group does not have to have just one of the preceding groups (or users) as its members. You can combine any of the preceding and place them into a single domain local scope group, and then use the group to manage the members of these other groups locally in your domain. A domain local group is a very useful management tool. For example, if you have a particular resource that several users share, place the users in the group and grant the group the necessary access to the resource. The resource can be a folder or a file, or perhaps a printer. If the resource changes in the future (for example, you decide to use a new file server for a particular set of files), you have to change permissions only on the group to let the group members access the new resource. Otherwise, you'd have to modify the permissions for each individual user, which in a large environment can be an almost impossible task if your network changes frequently. Unlike domain local groups, global groups can have as members only users or other groups from within a single domain. Yet global groups can be granted access to resources in other trusted domains. This enables you to package a group of users that need similar treatment in other domains when it comes to resource permissions. Universal groups also can be used to grant permissions in multiple domainsthroughout the forest of domain trees. Note that these groups are available only if you have an Active Directory structure that is part of a multidomain forest. They serve no purpose in a single-domain tree because domain local groups and global groups provide the necessary functions in a single-domain tree. The membership of a universal group should not change on a frequent basis. This is because when a universal scope group's membership changes, the entire list of members is replicated to every global catalog in the forest of trees. Use universal groups for grouping users and other groups that are more stable in membership. Although global groups enable you to create groups of users and other groups that can be granted access in trusted domains, their membership must come from a single domain. To make managing a universal group easier, first place users into global groups in their own domains, and then place these global groups into a universal group. Thus, when the membership of a global group changes, there is no need to replicate the universal group membership to every other global catalog. Only the global group has changed. The universal group has as its member the global group, not the individual users who come and go from the global group. Built-In GroupsThere are several kinds of built-in groups, depending on where you look in the directory structure. For example, in Figure 37.10 you can see the list of groups found under the Built-in folder. Simply click the Built-in folder and you'll see the list of built-in domain local groups. As the name implies, each group was designed to give the access permissions to perform specific types of administrative jobs. Figure 37.10. The Builtin folder contains a collection of domain local scope groups you can use.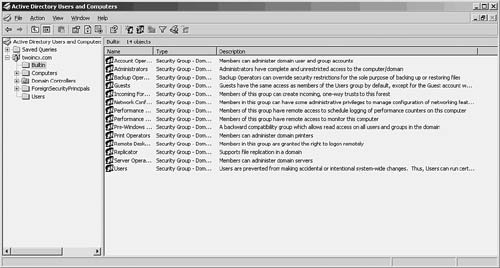 The domain local scope built-in groups can include the following:
In addition to these built-in groups, you can click on the Users folder and see a list of predefined groups, which also can be used to organize users. These are global scope groups, so you can use them to organize users and computers, and then place them in domain scope groups in the current domain or in other domains. If none of the following group names fits your needs, you can create your own groups, which we'll look at next. The Predefined groups found in the Users folder are listed here:
In general, the groups you'll use most in the list will probably be the Domain Computers and Domain Users groups. By default, when you create a user account, the new account is placed automatically into the Domain Users group. Likewise, when you add a computer to the domain, the computer is automatically placed into the Domain Computers group. Looking at the domain from an overall picture, you can use these two groups when you want to make changes that apply to all users or all computers in a domain. The Domain Admins group can be used to give selected individuals administrator-level rights in a domain. It is always a good idea to not use the actual built-in Administrator account for a domain. Instead, create individual accounts for each user, and then place the user into one or more groups that give him the access he needs. If you need to grant a user administrator-level rights, just place him into the Domain Admins groups. The other groups will depend on the services you have installed. Some may not appear if you have not installed that service (such as DHCP). A few notes about these predefined groups in the Users folder:
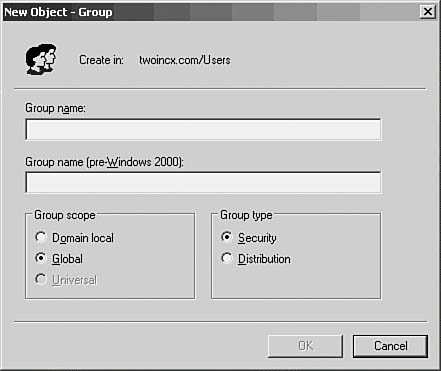
Note User Profiles are never cached locally on any system for members of any out-of-the-box Guest groups. Some of the other groups listed here also can be used to organize users and grant them access to resources on a group basis. However, you can always create your own group and tailor the rights and permissions for the group to match your exact needs. Creating a New User GroupTo start the process, click Action, New, Group. In Figure 37.11, you can see the dialog box that pops up to allow you to enter basic information about the group, such as the new group's name, the scope (Domain Local or Global), and the type (Security or Distribution). Figure 37.11. The New Object-Group dialog box prompts you for basic group information. These are the differences between these two types of groups:
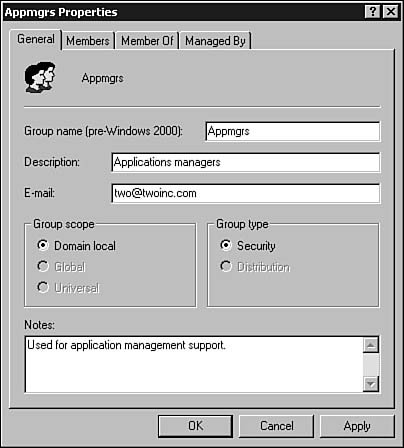
You can probably guess that after you fill in the basic information and click OK, the group is immediately created. In the example, a group was in the Users folder. Just as with User objects and Computer objects in the Active Directory, you can now bring up a properties page for the group and from there configure additional attributes for the group. Right-click on the group and select Properties. You also can highlight the group and select Properties from the Action menu. In Figure 37.12 you can see an example of the properties page for the group we just created. Figure 37.12. You can configure and view additional attributes by using the properties page for the new group. Here you can see fields that allow you to input a description of what the group is used for, as well as an email address that can be used to send email to members of the group. Additionally, you can put in notes about the group that might be helpful in the future. For example, you might create a group to be used only for a short period. You can put notes here to remind yourself to remove the group later. Two other tabs relate to group membership. The first tab, Members, lists current members of the group. On this tab you can click the Add button to bring up a dialog box to use for adding other users or groups to the group. The Member Of tab displays groups of which this particular group itself is a member. You also can use the Add button on this property sheet tab to add the group to other groups. Finally, the Managed By tab is similar to that discussed earlier, and is used to define a responsible contact person for this group. Other Things You Can Do with the Active Directory Computers and Users Snap-InThis utility is not as simple as the User Manager for Domains that was included in previous versions of Windows NT. However, most of the additional functions for which you can use this utility don't directly relate to user or computer management, so it's not relatively important to go into the nitty-gritty details. For example, you can create organizational units and use them to further subdivide the objects managed in your domain. There are other tools you'll find in the Administrative Tools folder that again don't relate directly to user or computer management, but you should be aware of them in case they are used at your site. Some of these utilities won't show up in your Administrative Tools folder unless you've already installed the prerequisite software. For example, the DHCP manager MMC snap-in won't be there if you haven't installed a DHCP service on the server. Some of the more popular tools include the following:
There are many other administrative tools you can use, from the Performance Monitor (and Network Monitor) to utilities used to manage Terminal Services. If you are using components that are not part of the default installation, be sure to examine the administrative tools to find an MMC snap-in utility for those components. |
EAN: 2147483647
Pages: 411