GNOME Lokkit
|
GNOME Lokkit allows you to configure firewall settings for an average user by constructing basic iptables networking rules. Instead of your having to write a rule, this program asks you a series of questions about how you use your system and then writes it for you in the file /etc/sysconfig/iptables.
You should not try to use GNOME Lokkit to generate complex firewall rules. It is intended for average users who want to protect themselves while using a modem, cable, or DSL Internet connection. To disable specific services and deny specific hosts and users, refer to Chapter 21.
To start GNOME Lokkit, type gnome-lokkit at a shell prompt as root. If you do not have the X Window System installed or if you prefer a text-based program, use the command lokkit to start the text-mode version of GNOME Lokkit.
Basic
After starting the program, choose the appropriate security level for your system:
-
High Security — This option disables almost all network connections except DNS replies and DHCP so that network interfaces can be activated. IRC, ICQ, and other instant messaging services as well as RealAudio will not work without a proxy.
-
Low Security — This option will not allow remote connections to the system, including NFS connections and remote X Window System sessions. Services that run below port 1023 will not accept connections, including FTP, SSH, Telnet, and HTTP.
-
Disable Firewall — This option does not create any security rules. It is recommended that this option be chosen only if the system is on a trusted network (not on the Internet), if the system is behind a larger firewall, or if you write your own custom firewall rules. If you choose this option and click Next, proceed to the “Activating the iptables Service” section. The security of your system will not be changed.
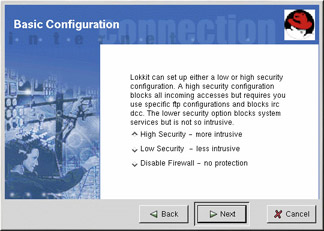
Figure 22-2: Basic
Local Hosts
If there are Ethernet devices on the system, the Local Hosts page allows you to configure whether the firewall rules apply to connection requests sent to each device. If the device connects the system to a local area network behind a firewall and does not connect directly to the Internet, select Yes. If the Ethernet card connects the system to a cable or DSL modem, it is recommended that you select No.
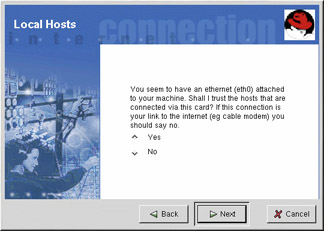
Figure 22-3: Local Hosts
DHCP
If you are using DHCP to activate any Ethernet interfaces on the system, you must answer Yes to the DHCP question. If you answer no, you will not be able to establish a connection using the Ethernet interface. Many cable and DSL Internet providers require you to use DHCP to establish an Internet connection.
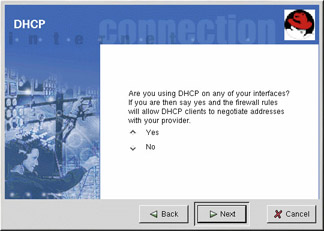
Figure 22-4: DHCP
Configuring Services
GNOME Lokkit also allows you to turn common services on and off. If you answer Yes to configuring services, you are prompted about the following options:
-
Web Server — Choose this option if you want people to connect to a Web server such as Apache running on your system. You do not need to choose this option if you want to view pages on your own system or on other servers on the network.
-
Incoming Mail — Choose this option if your system needs to accept incoming mail. You do not need this option if you retrieve email using IMAP, POP3, or Fetchmail.
-
Secure Shell — Secure Shell, or SSH, is a suite of tools for logging in to and executing commands on a remote machine over an encrypted connection. If you need to access your machine remotely through ssh, select this option.
-
Telnet — Telnet allows you to log in to your machine remotely; however, it is not secure. It sends plain text (including passwords) over the network. It is recommended that you use SSH to log into your machine remotely. If you are required to have Telnet access to your system, select this option.
Cross-Reference To disable other services that you do not need, use Serviceconf, ntsysv, or chkconfig. See Chapter 21 for all three options.
Activating the Firewall
Clicking Finish will write the firewall rules to /etc/sysconfig/iptables and start the firewall by starting the iptables service. It is highly recommended that you run GNOME Lokkit from the machine, not from a remote X session. If you disable remote access to your system, you will no longer be able to access it or disable the firewall rules. Click Cancel if you do not want to write the firewall rules.
Mail Relay
A mail relay is a system that allows other systems to send email through it. If your system is a mail relay, someone can possibly use it to spam others from your machine. If you chose to enable mail services, after you click Finish on the Activate the Firewall page, you will be prompted to check for mail relay. If you choose Yes to check for mail relay, GNOME Lokkit will attempt to connect to the Mail Abuse Prevention System website at http://www.mail-abuse.org/ and run a mail relay test program. The results of the test will be displayed when it is finished. If your system is open to mail relay, it is highly recommended that you configure Sendmail (or any other mail transfer agent you’re running) to prevent it. You must have the iptables service enabled and running to activate the firewall. Refer to the “Activating the iptables Service” section of this chapter for details.
|
EAN: 2147483647
Pages: 278