Conforming to the Rules
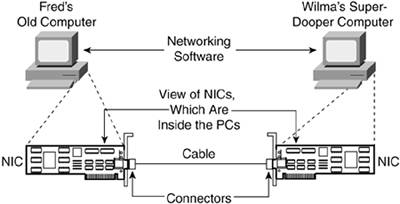
| Anyone who has spent time around a teenagerand I figure most people reading this book have at least been teenagers beforeknows that those years bring out the rebel inside. Instead of conforming, teenagers sometimes think that rules are meant to be broken! In some cases, breaking the rules might be okay. But often times, as all parents know, the wisdom of having rules and conforming to them become obvious after a little thoughteven to a teenager. Standards are rules that make life a lot easier. For example, look at a power socket on a nearby wall. If you live in the U.S., you probably see an electrical socket with three holestwo that accept flat metal prongs, and one that accepts a round metal prong. The flat metal prongs are parallel to each other. If you go to the store and buy a lamp, you'd expect it to come with a power cord, and you'd expect that one end of the power cord would fit into the wall socket. In fact, you'd be pretty ticked off if the power cord wouldn't fit into the power socket. That's one example of a popular standard. If you go to the store and buy a toaster, a can opener, or a stereo, you would expect the vendor to conform to the standards for how the electrical wall socket works in your country. Now imagine that you bought a new lamp. You plug it in, and the light bulb instantly "pops," indicating that the light bulb is broken. You put in a new bulb, and it doesn't light up. You decide that the lamp must be broken, so you bring it back to the store and replace it with an identical lamp. When you get it home, the same thing happens to this lamp. Finally, you call customer service and explain your problem. Now imagine this response: "Oh, you bought our special 'We light up your life' model of lamp. It uses the same kind of power cord you are used to using, but it requires less electrical voltage, saving you money. If you read your instructions for the lamp, you will see that it directs you to get an electrician out to your house to rewire and change the voltage coming out of the sockets you want to use for the lamp. Also, note the disclaimer in the instructions: 'If you plug this lamp into a normal wall socket, the extra voltage will fry the lamp, and it will no longer light up your life.' So, go get a new lamp at the store and get your wall socket changed!" If you're like me, you would return to the store to get your money back and buy a lamp made by some other company. But what does this scenario have to do with networking? A standard tends to define one particular thing, such as the shape of the wall socket and connector used by an electrical socket and electrical power cable. Another standard might dictate how much juice (voltage) flows through the wall socket, whether it is AC or DC, how much current, and the like. Both standards are important and must be followed to prevent exploding lamps. In short, just because you can plug in a lamp does not mean that all the necessary standards have been used. Similarly, networking has standards for physical details so that you can plug in the cables correctly; however, networking devices must support other standards as well for a network to work correctly. Rules, Schmools for NetworkingEven for the simple network with Fred and Wilma in Chapter 2, "A Network's Reason for Existence," several standards were required. To create that network, Fred's PC (the client) and Wilma's PC (the file server) need to be set up to use the built-in networking features of their computer operating systems. Figure 3-1 outlines some of the details. Figure 3-1. Components of a Simple Network
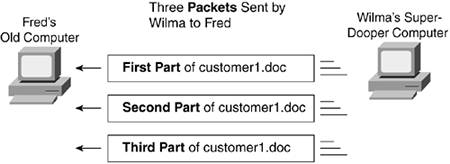
First, the PCs in the network need some form of physical connectivity. Physical connectivity refers to the combination of cabling, networking devices, and network interface cards (NICs) in the computers, which together provide the physical capability to transmit and receive data across a network. Physical connectivity means that the computers have a physical path over which they can send data to each othermuch like having roads so that you can drive your car. Both PCs have a NIC installed, and each card has a receptacle into which a cable can be connected. (The NICs are shown outside the PCs to emphasize their existence.) A NIC is a computer card that gives a computer the ability to send and receive data across a physical network. The words behind the acronym NIC (network interface card) make sense because a NIC is a computer card that provides an interface between the computer and the network. Networking standards define several types of connectors. A connector is the physical endpoint of the cable, with a certain size and shape. For instance, an electrical power plug on the end of an electrical power cable might have two flat prongs and one round one. With networking cables, the end of the cable is not called a plug; it's called a connector. The connector holds the wires that are inside the cable. Also, the standards for the connector ensure that the connector fits the NIC's interface. The networking software on Fred and Wilma's computers must understand messages sent back and forth to each other. These messages mean things like "I want to open file customer1.doc," or "Please print the stuff I'm sending you on printer sameoldprinter." So, the two computers must implement the same standards for how the networking software on each computer tells the other what it wants to do. It's like Fred and Wilma needing to speak the same language to have a useful conversation. Their computers must speak the same networking language to have a useful conversation on the network. Examples of Good Rules for NetworkingNetworks rely on standardsa lot of standardsto be able to do something useful. Before covering more about standards, it's useful to consider a couple of sample networking standards. The next few sections cover the basics of how data is sent between computers, how and why a bunch of bits are sent at the same time, and what to do when the bits experience errors during transmission. But before all that, you need to understand some termsin particular, bits and bytes. Traveling a Roadway for a Bit to Get a ByteTwo humans communicate when one person says something and the other person listens. If you ponder that a little more, the two people need to understand the same language. To communicate, the person speaking has to say a bunch of words. The words themselves are sounds that are combined. From one perspective, two people communicate by speaking the same language, but at the other end of the spectrum, you could think of those same people communicating by making a bunch of sounds. Similarly, computers can communicate with each other using a network, but there are many perspectives. For instance, I'm using Microsoft Word to write the text in this book. When I send the file to my editor at Cisco Press, she uses the same program to open the file and edit the chapter. So, you can think of our computers as speaking the same language. In this case, both of our computers understand files formatted for use with Microsoft Word, which is a word processing program. It is relatively easy to think of a file that contains the text for this chapter. However, at the same time, the file is really just a bunch of bytes, with each byte containing 8 bits. It's a little like when you put a file folder in a real file cabinet, you might be thinking that you're doing simply thatstoring one file in a cabinet. From a different perspective, if the folder contains a bunch of pieces of paper, you are also storing those pieces of paper. Similarly, when a computer stores a file on a disk drive, it is indeed storing one file. However, from a different perspective, the computer is also storing the bits that make up the file. Computer files consist of a bunch of binary digits. Humans normally use decimal numberingyou know, 0, 1, 2, 3… 9, with 10 unique digits. Binary uses only two digits: 0 and 1. That's because computer hardware, at the most basic low level, can store one of two electrical states in its memory, and those represent a binary 0 or 1. And because the phrase binary digits takes five whole syllables when speaking (in English, at least), and it's used so often, someone shortened the term to simply bits. To speak to another person, you use a language, but your voice actually makes a lot of small individual sounds. It's the combined sounds that make up words and sentences in your chosen language. Similarly, a computer might have a Word document or any other file that's useful to a computer, but the contents of these files are just a bunch of small individual pieces of information, called bits. It's the combined bits that make up the parts of the file that the computer has in memory. (By the way, the term byte refers to a set of 8 bits on most computers.) When computers communicate, the application needs to send something to an application on another computer. For instance, when you view a web page, it consists of the contents of one or more files. The application needs to transfer the contents of the file to the other computer. To do so, the computer sends a bunch of bits to the other computer because a file is just a bunch of bits. The next section covers an example of how a standard might define how to send bits. Example Rule for Sending the BitsWhen Fred's computer was using Wilma's computer (the file server) in Chapter 2, the network had to take the file from the hard disk at the server, move it across the network, and deliver it to the word processor on Fred's computer. Before the file server could transmit the contents of the file across the network, it had to read the file from the disk. Then it had to transmit the bits over the network. Any time electricity goes over a wire, you can put a device on the end of the wire that can sense different things about the electricity. One thing that can be sensed is voltage. Voltage refers to the amount of electrical power running over the wire. In networking, to send bits, the sender can change the voltage to one level to mean a binary 0, and another to mean a binary 1. For example, to transmit the bits, the NIC inside Wilma's computer sends some electrical signal over the cable. The device on the other end of the cableFred's PC NIC in this casethen interprets the incoming electrical signal. For this to work, both NICs must agree to some standard means of transmission. For instance, imagine that Wilma's NIC sends a +5 volts electrical signal to transmit a binary 0 and +10 volts to send a binary 1. If Fred's NIC expects to receive a +2 volt signal for binary 0 and +4 volts for binary 1, the network will not work because Fred will not understand what Wilma is sending him. The physical transmission of bits can be a lot more complicated than this example, but the basic idea remains the same. The sending device puts some electricity on the cable, which is interpreted as binary numbers by the device at the other end of the cable. The term encoding refers to the general process of taking a binary value and generating the correct electrical signal to be able to transmit the bits across the network. The encoding rules used to transmit data are defined by networking standards. Sending the Bits a Packet (Package) at a TimeAlthough you've read about one example of a networking standard for the physical transmission of bits, many other standards are required before two computers can successfully communicate. For example, imagine that Wilma is successfully transmitting the contents of the file, but some of the data gets lost, as shown in Figure 3-2. Figure 3-2. Data Transmission Using Packets
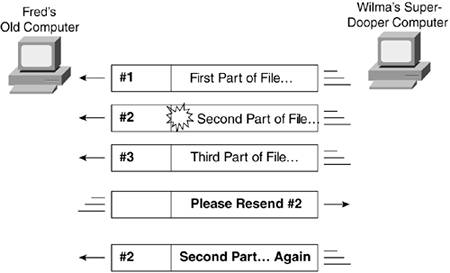
In normal operation, devices in a network send bits in groups, generally called packets. For instance, Wilma sends the first part of the file in the first packet, the next part of the file in the next packet, and so on. A packet is simply a group of bits that are combined for transmission in a network. You can think of a packet as a packageit holds some bits for you while they are being sent across the network. Why do networks use packets? Well, it's sort of like if you worked at a company that sold widgets, and you needed to ship 1,000,000 widgets to a single customer. Would you put them all in one box? Probably not. You would put some in one box, and then another, until you had put all the widgets in several boxes. You would address the boxes to the same place, and you might even ship them all the same day, but it's easier to deliver the packages if the boxes are a more manageable size. Similarly, rather than sending the entire contents of a filepossibly billions of bits long, all at oncecomputers send data in packets, making the delivery of the data a little more manageable. In fact, one of the reasons that networking standards call for the use of packets is for error recovery, which you learn about in the next section. What to Do When the Bits Get BashedNow imagine that the second packet shown in Figure 3-2 had an error. If both NICs think that +5 volts is a binary 0, and +10 volts is a 1, what happens if the voltage is 15 volts? Or 7.5 volts? Certainly, those voltages would confuse the NICs. How do errors occur? Well, something as simple as someone running a vacuum cleaner near the cable could cause the voltage to change while the electricity is passing over the wire, a phenomenon called electrical interference. Formally, electrical interference is the effect of one electrical signal changing because of some other nearby electrical signal. You have all seen or heard electrical interference, such as when your television picture gets a little fuzzy, when you can't hear your AM radio station while you're driving under high-power electrical wires, or when you hear a buzzing noise from your stereo when you are running a blender in your kitchen. Electrical interference happens. The people who create networking standards can do things to minimize the chance that interference causes transmission errors, but ultimately, electrical interference will cause at least some transmission errors. So, Fred might receive all three packets (refer to Figure 3-2), but one packet might have some bits that just could not be understood. Imagine the first packet had the first paragraph of the customer letter, the second packet had the second paragraph, and so on. Would Fred want to see the letter with the second paragraph missing? Of course not. So, there needs to be a standard for how Fred can realize the second packet had an error, and cause Wilma to send that packet again. The solution to the transmission error problem typically happens inside software on the two computers with today's networking standards. To recover the errored packet, both Wilma and Fred's computer software must agree to use the same networking protocola protocol that provides a method to recognize and recover from errors. A protocol is like a standardin fact, in many ways, protocols and standards are the samebut the term protocol typically refers to a process. Figure 3-3 shows a simple protocol that might be used to recover the lost data. Figure 3-3. A Simple Protocol for Error Recovery
A couple of changes were made to make this new protocol work. (In the figure, the features added to make the protocol work are noted in bold letters.) First, this protocol requires that the sender of the packet number the packets. That way, when the receiver (Fred) notices the error, he can send a message back to the sender (Wilma) asking her to send the specific problem packet againin this case, packet 2. Wilma, of course, replies to Fred's request by resending packet 2. Error recovery refers to the general process of not only noticing when errors occur in the transmission of a packet, but also requesting for retransmission of the packet until it is received successfully. By using packets instead of sending all the bits in the file at once, Fred and Wilma could recover by resending just part of the file. |
EAN: 2147483647
Pages: 173