OSI Reference Model
| Late in the 1970s the OSI Reference model was created to help facilitate data transfer between disparate hosts using different operating systems. The OSI Reference model is a set of guidelines that application developers can use for creating and implementing applications to run on a network. This model provides guidelines or a framework for creating and implementing networking standards, devices, and internetworking schemes. The OSI Reference model has seven individual layers, each with its own responsibility and rules. The OSI Reference model layers are as follows :
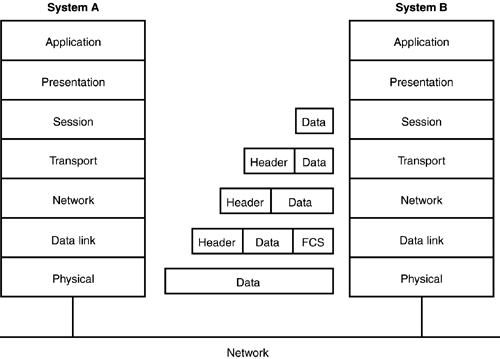
These seven OSI layers can be divided into two different groups (see Figure 2.1). The top three layers define how the applications within the end stations will communicate with each other and with users. The bottom four layers define how data is transmitted from one point to another. The Application, Presentation, and Session layers know nothing about networking or network addresses ”that is the responsibility of the four bottom layers. The Transport, Network, Data Link, and Physical layers define how data is transferred through a physical wire, and through switches and routers. These layers also build a data stream from a transmitting host to a destination host's application. Figure 2.1. The division of the OSI Reference model into upper and lower layers. In Figure 2.1, you can see two different computer systems. In this example, each layer communicates with its peer layer on the other system. The data starts at the Application layer, which is the layer where the user interacts with the machine and the installed software. The following sections of this chapter describe how each layer encapsulates the data so the same layer can be retranslated at the receiving system. The upper layers are responsible for applications communicating between hosts. The following sections describe each of the seven layers of the OSI Reference model in detail. The Application LayerAs you have learned, the Application layer of the OSI model can be remembered as the layer where users communicate with the computer. The Application layer identifies and establishes the availability of the intended communication partner as well as determining what resources are needed for the intended communication and whether those needed resources exist. In some cases, computer applications may require only desktop resources, or applications may unite communicating components from more than one network application. Examples of this include file transfers, email using Simple Mail Transfer Protocol (SMTP), remote access, network management activities, Web browsers, Telnet, and File Transfer Protocol (FTP). The Presentation LayerThe Presentation layer presents data to the Application layer, and as such, functions as a translator providing coding and conversion functions. By providing translation services, the Presentation layer ensures that the data transferred from the Application layer of one host can then be read by the Application layer of another host. This layer of the OSI Reference model has protocol standards that define how data should be formatted. Tasks such as data compression, decompression , encryption, and decryption are associated with this layer. Other Presentation layer protocols provide standards for multimedia and visual image presentation. The following protocols are a few examples of those included in this group :
The Session LayerThe Session layer is responsible for setting up, managing, and then tearing down sessions between the Presentation layer entities. The Session layer is used to coordinate communication between different disparate systems. Some examples of Session protocols and interfaces are Structured Query Language (SQL), which provides a simple way of defining information requirements on both local and remote systems, and Remote Procedure Call (RPC), which is a broad client/server redirection tool. RPC's procedures are created on clients and performed on servers. There are many more examples of protocols used at this layer, which you learn about when studying for the CCNA Exam (those examples appear in CCNA Exam Cram 2 ). Readers of this book have most likely already passed the CCNA Exam. The Transport LayerThe Transport layer is the demarcation point between the upper layers and the lower layers. This layer is known for using segments, and shields the upper-layer applications from having to learn anything about the lower layers. This layer assembles and disassembles information from the upper and lower layers into a data stream also known as a session or virtual circuit. Common examples of protocols used at this layer are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP), which both work at the Transport layer and are used by TCP/IP. TCP is a reliable service and UDP is not. TCP is an example of a connection-oriented protocol . It is the equivalent of sending certified mail. The packet is sent and the receiving device sends an acknowledgement that it received the entire packet. UDP is an example of connectionless or best-effort protocol. The packet is sent on the physical wire without a confirmation of delivery. The sending device sends the data and never knows whether the destination device received the packet. Application developers have their choice of the two protocols when working with TCP/IP protocols. Also used at this layer is Novell's Sequenced Packet Exchange (SPX). You should remember the Transport layer's primary functions, which are
The Network LayerThe Network layer uses packets and is responsible for routing through an internetwork and handling network addressing. Routers work at this layer. Simply put, this is the layer that handles network data between devices that are not locally attached in the same network or subnet. When a router receives a packet on a network attached interface (port), the destination IP address is checked against the router's routing table. The router's routing table is a list of all the routes to other networks. If the router knows where the destination network is located, an exit interface is chosen and the packet is sent to the interface to be framed and sent out on the local network. Framing is the process of placing header and footer information in a layer 2 frame. Alternatively, the packet is sent out through an exit interface to the next router, which is commonly called the next hop. If the entry for the destination network is not found in the routing table, the router will send the packet to the gateway of last resort (if there is one configured). The gateway of last resort is usually the exit to the Internet or another gateway to an upper-level network. The router uses this gateway by default for any destination the router has not yet learned about. If no gateway of last resort is configured, the router drops the packet. Routing tables are also collected and used on the router. Routes called static routes are manually configured on the router. A static route is a route manually entered into a device to route data from one device to another. A route learned by a device on its own is called a dynamic route . Routes are learned dynamically by using a routing protocol. Routing protocols are protocols that dynamically update routes in a router's routing table and send route update packets. A routing protocol uses route update packets to notify neighboring routers about networks that are connected to the routers, as well as networks the router knows about in the internetwork. Some examples of routing protocols are
These are the primary routing protocols used in today's networks and the ones you should know thoroughly to pass the exam.
The Data Link LayerIn the preceding section you learned about the Network layer and how routers use addressing to route packets. Routers do not care where a host is located. A router tracks where networks are located and the number of paths to get to that network so they can decide the best way to reach it. The Data Link layer uses frames and is responsible for uniquely identifying each device on a local network. The Institute of Electronics and Electrical Engineers (IEEE) standard provides two Data Link layer sublayers . The most commonly used in today's networks is called the Media Access Control (MAC) sublayer of the IEEE 802.3 standard. Physical addressing uses six hexadecimal octets to make up a MAC address; the address is assigned to the network interface card (NIC), which connects to the network. The first three octets make up a vendor-assigned number and the last three are similar to a serial number, giving every manufactured NIC card a unique address. The second sublayer of the Data Link Layer is the Logical Link Control (LLC) or the IEEE 802.2 standard. This sublayer is responsible for identifying Network layer protocols and using encapsulation to get frames to the correct destination. Encapsulation is the process of placing header information in a packet. The LLC can provides flow control and sequencing of control bits. This layer adds additional functionality to the Data Link layer itself.
Switches and bridges both work at the Data Link layer. These devices filter data traversing the network, using MAC addresses. Layer two switching is considered hardware-based bridging since it uses specialized hardware called Application Specific Integrated Circuits (ASICs). ASICs are small chips that use hardware to route data. ASICs can run up to gigabit speeds with very low latency. Latency is the term used to describe the time required for a network device to receive a frame or packet and make a forwarding decision, and then for the frame or packet to completely exit the device. A device with a switch that requires a considerable amount of time to decide through which port the data should exit is called a high-latency device . The Physical LayerThe Physical layer converts upper-layer data, headers, and footers to bits. Bits are values of ones and zeros. The Physical layer communicates directly with various types of physical media, such as Unshielded Twisted Pair (UTP), coax, or fiber cabling. The Physical layer is responsible for defining the physical, electrical, mechanical, and procedural functions for activating, maintaining, and deactivating a signal on the actual network cabling.
|
EAN: 2147483647
Pages: 213