Chapter 8: Hardening Wireless LAN Connections
Wireless LAN (WLAN) connections represent the classic struggle between security and usability. On one hand WLANs were created and are used to simplify the ability of users to connect to and access network resources. With a wireless NIC, a user can connect to a network anywhere on a campus, in an office, or at any neighborhood coffee shop. On the other hand, WLANs are by their very nature insecure . The data is sent over the airwaves, where anyone can potentially receive it. In addition, an illegitimate user can often connect to a WLAN with the same ease that a legitimate user can if the WLAN is left in the default mode. Indeed, no one in their right mind who has any kind of security focus would allow a WLAN in their environment. However, it is not a lost cause. As you will see, there are many things you can do to secure your WLANs.
At the same time, you may already have a WLAN or are planning one. Does this mean you aren t concerned with security? Of course not. To the contrary, this illustrates how important it is to provide usability and functionality to your users. It also illustrates the simple reality that in the struggle between what users want and need and security, security frequently comes in second. This does not mean that we have to accept that we cannot secure our WLANs, though. Instead, it means that we need to take extra measures to ensure that we provide the access our users request while providing the security our network requires.
Banning WLANs WithoutIT/Management Approval
As mentioned in Chapter 1, wireless presents a unique problem to your networks. It is entirely too easy for someone to obtain a rogue WAP, connect it to your network (using DHCP to assign the WAP an IP address), and then allow anyone with a wireless client to be able to connect to your network, even though your wireless security policy should explicitly prohibit such actions.
Preventing Rogue APs
No good, bulletproof technical method exists to prevent a WAP from being connected to your network. By that I mean that if someone wants to bring a rogue AP onto your network, they are always going to have a chance of being successful. This doesn t mean that you should pack up the tent and head home, however. There are a few things you can do to prevent or greatly reduce the odds of a rogue WAP being successfully connected to your network:
-
Implement a wireless security policy. The first thing to do is to have a good wireless security policy. The problem of unauthorized WAPs is largely a people problem that requires a people solution in the form of enforceable security policies. Also, your wireless security policy is one that absolutely must have teeth. If someone brings a rogue WAP online, they need to be subject to termination of employment. Your wireless security policy also needs to define what the response to a rogue AP is. For example, will the AP be confiscated, and, if so, who is responsible for that?
-
Provide for physical security. A WAP has a limited range. You should implement physical security measures that prevent someone from being able to get within range of a WAP running in your organization. Unfortunately, oftentimes this is not a practical measure, and it s useless in regard to people with unauthorized WAPs (they already aren t paying attention to the security policy, so they probably don t care about where they locate their WAP).
| |
Another aspect of your wireless security policy should define the mode of operation permitted for your WLANs. WLANs have two modes of operation. The first mode of operation is infrastructure mode, and it's the conventional WLAN configuration. Infrastructure mode entails the wireless clients being connected to the existing wired infrastructure by way of a WAP or wireless router. The second mode of operation is ad hoc mode, sometimes referred to as peer-to-peer mode . In ad hoc mode, multiple wireless clients are connected to each other in a peer-to-peer fashion, allowing small workgroups of computers to connect to each other without any other infrastructure. You should not allow ad hoc connections in your environment.
You also need to explicitly define the physical WLAN components you will allow in your network. This will assist you in detecting and identifying unauthorized wireless devices. The three primary WLAN components to define in your environment are the following:
-
Wireless access point (WAP) A WAP (sometimes referred to as a base station) is the device that wireless clients connect to. A WAP can typically connect hundreds of wireless clients and effectively operates like a bridge, allowing the client access to the physical LAN segment the WAP is connected to. WAPs are typically used in enterprise environments to provide wireless access.
-
Wireless router Wireless routers combine the functionality of a WAP with a router, allowing wireless clients to connect to the router and then be routed to other networks. Wireless routers often include firewall functionality and are typically used in small office/home office (SOHO) environments to provide wireless access.
-
Wireless client Wireless clients include any device that uses a wireless network card to communicate with a WAP or wireless router.
| |
-
Provide a supported WLAN infrastructure. If people want a WLAN and they don t have one, they might be tempted to implement one on their own. On the other hand, if you make sure you implement a WLAN that supports your users needs, they will be much less likely to decide to go about it on their own. The truth is, most rogue WLANs are implemented by nonmalicious users who simply think that a WLAN will make their lives easier.
-
Implement 802.1x port-based security on your switches. As we will discuss in Chapter 9, you should implement 802.1x port-based security to prevent any unauthorized connections to your network by requiring all connections to be authenticated. This includes preventing an unauthorized WAP from being able to connect.
-
Limit the number of MAC addresses per port to only one. This will prevent switches from passing packets from rogue WAPs because the WAP and the client both have different MAC addresses. This is also a good measure if you want to prevent the users from plugging in a rogue switch or hub as well. You can implement this on many IOS-based switches by running the following command at the CLI:
switch02(config-if)# switchport port-security maximum <max addrs>
| |
I personally know of companies that have rogue WAPs that allow anyone on the freeway to access their internal production network, including potentially granting access to source code. A rogue WAP is a death blow to security because no matter how much you have hardened the perimeter, it has been instantly undermined by the WAP once it connects to your internal network.
| |
Once you have undertaken procedures to prevent unauthorized WAPs, the next step is to implement procedures to detect unauthorized wireless connections.
Implementing WLAN Discovery Procedures
Just because we can t really prevent unauthorized WAPs from being implemented on the network doesn t mean we can t detect and remove them. It just means that we need to get a little creative in how we approach the problem.
You have two primary methods of detecting unauthorized WAPs on your network. The first method attempts to detect them wirelessly . The second method attempts to detect them from the wired network.
Detecting Unauthorized WAPs Wirelessly
The most effective method of detecting unauthorized WAPs is by simply using a wireless client and locating the WAPs broadcasting in your environment. A few caveats must be considered when employing this method, however:
-
You have to be within range of the WAP in order to detect it.
-
It is very difficult to detect a WAP that does not broadcast its SSID.
-
It can be difficult to survey remote sites.
The good news is that because most unauthorized WAPs are not implemented by malicious users (and oftentimes are implemented by nontechnical users), the odds are high that the SSID broadcast has not been disabled. This leaves us with the problems of needing to be within range of the WAP to detect it and trying to survey remote sites. It is often impractical for someone in IT to spend the day walking around trying to determine if they can detect access points. One of the best solutions I have seen for this is to take advantage of someone who on a daily basis must walk around the environment ”the mail delivery person. You can outfit this person with a laptop or handheld carrying extra batteries and while they make their normal rounds delivering the mail, the laptop can sit in the bottom of the mail cart quietly detecting any WAPs. A number of wireless analyzers can be used to detect the presence of unauthorized WAPs, including the following:
-
Airdefense (http://www.airdefense.net/)
-
Airmagnet (http://www.airmagnet.com/)
-
Boingo (http://www.boingo.com/)
-
Netstumbler (http://www.netstumbler.com)
-
Kismet (http://www.kismetwireless.net/)
-
Network Associates Sniffer (http://www.networkassociates.com/us/products/sniffer/home.asp)
-
Wildpackets Airopeek NX (http://www.wildpackets.com/products/airopeek_nx)
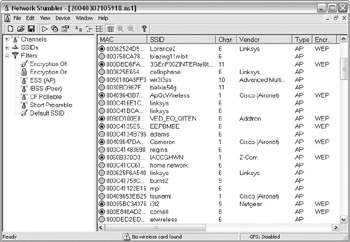
Netstumbler provides one of the easiest methods for detecting a rogue AP over the wireless network. Once you install Netstumbler, the program automatically begins scanning for WAPs with no configuration required on your part (other than providing the wireless NIC, of course). For example, the screen shown next depicts what I was able to capture while driving down a major freeway in the Houston area. I captured 175 WAPs, of which 113 were running no encryption whatsoever, and none of which were running WiFi Protected Access (WPA). Instead, they were all using WEP.
Detecting Unauthorized WAPs from the Wired Network
Detecting unauthorized WAPs from the wired network is generally not as easy a process as it is to detect them wirelessly. After all, it doesn t get much simpler than walking around with a laptop and a wireless card. At the same time, you can t really do much about the biggest problem with trying to detect a WAP wirelessly ”namely ”detecting a WAP that is not broadcasting its SSID.
Using a wired detection process can alleviate some of the disadvantages to trying to detect an unauthorized WAP wirelessly. For example, a wired detection process is not susceptible to missing WAPs that do not broadcast their SSIDs. In addition, a wired detection process can be used to survey remote sites and can even be scheduled and scripted to increase ease of use.
Unfortunately, there are some drawbacks to this method. It can be difficult to locate all the unauthorized access points. This is largely due to the lack of mature or specialized products for this task. Currently, most techniques rely on using MAC addresses (because all vendors are assigned a MAC address range) or OS fingerprinting to identify the WAP, both of which are an imprecise science. Here are two tools that can assist you in identifying an unauthorized AP by monitoring MAC addresses:
-
AP Tools (http://winfingerprint. sourceforge .net/aptools.php) AP Tools not only can discover an access point based on the MAC address, it can also attempt to check to verify that the access point is a WAP.
-
Arpwatch (http://www-nrg.ee.lbl.gov/) Arpwatch can monitor the network and maintain a database of MAC address and IP address pairings.
Here are some tools that can assist you in OS fingerprinting:
-
Nmap (http://www.insecure.org/nmap/index.html) Nmap can be used to identify the OS that a scanned host is running. For more information on using Nmap see Chapter 13.
-
Xprobe (http://www.sys-security.com/html/projects/X.html) Xprobe is similar to Nmap in its ability to identify the OS through the use of fingerprinting.
-
Nessus (http://www.nessus.org) Nessus is discussed in detail in Chapter 13. However, you can find an excellent whitepaper that details the process of using Nessus to detect rogue WAPs at http://www.tenablesecurity.com/wap-id-nessus.pdf.
Both of these methods share the common problem of generating false positives. For example, Nmap recognizes a Linksys WAP54G as a Linux device because it actually runs Linux for the OS. This can make it difficult to determine whether the device is indeed a WAP or just a Linux host running on your network. MAC address tools rely on identifying a device due to it having a MAC address that has been assigned to a wireless vendor. That can make it difficult to distinguish between a Cisco AP and a Cisco switch if the database of MAC addresses has not been accurately updated.
| |
While I was writing this, I got into a discussion with a colleague about the inconsistencies and difficulties of detecting a rogue wireless AP on the network. He mentioned that he was testing an alpha version of Network Associates ePolicy Orchestrator (EPO; http://www.nai.com/us/products/ mcafee /mgmt_solutions/epo.htm ) that has the ability to detect rogue wireless APs. When I asked him how well it worked, he mentioned that he had tested EPO with a number of different wireless APs and that it detected all of them within 5 “8 minutes of being brought online. The technology is definitely improving, and the accuracy of the detection algorithms is getting much better.
| |
Removing Rogue WAPs
Once you have detected a rogue WAP, you have a couple of methods you can use to shut it down. One option is to attempt to physically locate and disconnect the WAP from the network. However, this can be both time consuming and prone to failure. The obvious difficulty in this method is that it can be very difficult to locate the WAP, usually through a trial-and-error process. (Is the WAP here? No. Is it here? No.)
Another option is to locate the switch port that the MAC address is connected to and shut that switch port down. Similarly, you can determine the IP address of the WAP and attempt to block the IP address. Personally, I recommend shutting down the switch port. In many cases, this will cause the person to seek you out, saving you the time and effort of trying to find them.
User: Uh, yes, I can t access anything on the network anymore. I don t know what happened .
You: No problem. We know exactly what is going on. What office are you in?
EAN: N/A
Pages: 125