Traffic Capture Overview
| [ LiB ] |
For a network IDS to detect intrusions and generate alarms, network traffic must be visible to the IDS. Cisco IDS sensor appliances have a monitoring port that you use to capture network traffic and a command and control port for management, configuration, and communication with other IDS components .
The sensor monitoring port is the port that is connected to another network device, such as a hub, switch, or router, so that the port can capture traffic to send to the IDS sensor for analysis and processing. Recall that hubs broadcast all traffic out to all ports; if the sensor monitoring port is connected to a port on a hub, all traffic traversing the hub is visible to the sensor. If the sensor's monitoring port is connected to a port on a switch, on the other hand, only traffic destined for that particular port is visible to the sensor. The switch associates individual media access control (MAC) addresses with specific ports and uses this information to build entries in its MAC table.
In other words, without any extra configuration, connecting a sensor's monitoring port to a port on a switch does not result in any significant network traffic being visible to the sensor, and potentially no alarms will be generated.
This is where Switched Port Analyzer , or SPAN, comes in. With SPAN, you can configure a switch so that traffic from source ports connected to network devices and hosts can be mirrored to a destination port . You then connect the destination port, or SPAN port, to the monitoring interface of your sensor so that the sensor can analyze traffic, generate alarms, and proactively react to attacks. Figure 4.1 shows source ports on a switch mirroring traffic to a destination port, which then directs the mirrored traffic to the monitoring port on the sensor appliance.
Figure 4.1. Source ports on a switch mirroring traffic to a destination port and sensor monitoring port.
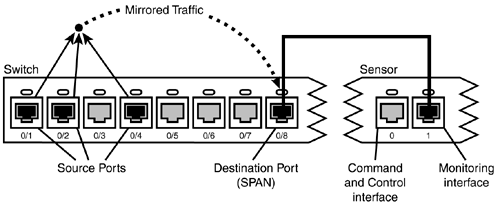
You can control SPAN configurations so that traffic is captured according to port, VLAN membership, or the direction of traffic flow. Traffic received by the source ports or VLAN is called ingress SPAN , whereas traffic sent from the source ports or VLAN is egress SPAN .
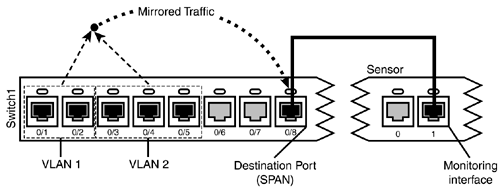
Figure 4.2 shows traffic from VLANs being mirrored to a SPAN port and sensor monitoring port.
Figure 4.2. VLAN traffic is mirrored to the SPAN port and sensor monitoring port.
In certain instances, you can configure sensors to respond to an attack with a TCP reset to terminate a session with an attacking device. During a TCP reset, a TCP packet is sent from the sensor's monitoring port through the switch's SPAN port to the relevant port for the attacking device.
| | The 4250XL appliance has port 1 dedicated to TCP resets, with the monitoring ports on the XL card. |
Not all switches allow the receipt of incoming traffic on a SPAN port in their default configurations, so it's important that you enable this feature on the switch if you're going to configure your sensor to perform TCP resets.
| | The sensor uses a randomly generated MAC address when sending a TCP reset packet through the switch to an attacking device. |
| [ LiB ] |