NetScanTools
|
| < Day Day Up > |
|
NetScanTools is a Windows-based scanning utility (see Figure 4-2). It is a commercial product, but you can download a 30-day trial of the standard version from http://www.netscantools.com/. The download of version 5.10 is around 1.9MB. A more full-featured professional version is also available for purchase.
Figure 4-2: NetScanTools screen
Implementation
NetScanTools is a nice graphical front end for a lot of freely available command-line tools that we cover in Chapters 5 and 14, such as Ping, traceroute, Finger, and whois/fwhois. It also talks with a few outdated “Simple Services” such as echo, daytime, quote, and chargen, which are usually not open to the Internet at large. Many of the tools under the Tools tab on the left, such as TimeSync, Database Tests, WinSock Info, NetBios Info, and Ident Server, are used to view information or manipulate services on the host box running NetScanTools. In addition, the tool has a launching point for telnet, FTP, and HTTP applications. It creates a nice central point for gathering network information and conducting network scans. The three most useful tools are the NetScanner, the Port Scanner, and the TCP Term. NetScanner (see Figure 4-3) can be used to scan a range of IP addresses for hosts that are up, similar to using nmap’s –sP option. Enter a starting and ending IP and click Start NetScan. NetScan will perform Pings, DNS lookups, and even optional whois queries on the hosts in your range. NetScan offers you the ability to save this information to a text file or even update your machine’s HOSTS file with the information you retrieve.
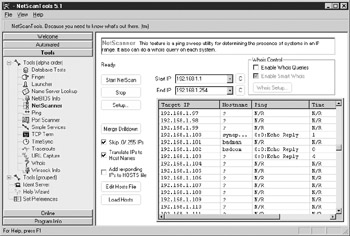
Figure 4-3: NetScanner—find hosts that are alive
The Port Scanner (see Figure 4-4) is the actual port scanning section of NetScan. You can specify a single host or a range of hosts to scan as well as port ranges and timeouts. The scan results are displayed in a tree. The green ports indicate ports that responded and the green “d” ports indicate that NetScan retrieved some data from the port during its scan. Double-clicking the “d” port will allow you to see that data. This is referred to as banner grabbing and can be used to identify the type and version of a listening service. Additionally, you can right-click on a port and attempt to connect to it with Telnet, FTP, or HTTP.
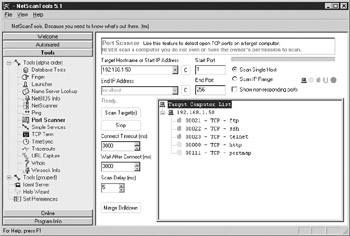
Figure 4-4: Port Scanner—find ports that are listening
NetScanTools doesn’t have as many stealth options as nmap, but it does allow you to scan ranges of IP addresses and ports as well as control timing. If we look at the Unix messages log on 192.168.1.50, however, we see that this tool is much, much louder than nmap. Because NetScan closes its connections with a FIN instead of a RST, the logs were able to capture the scanner’s IP address.
Mar 15 21:31:18 originix in.ftpd[1794]: connect from 192.168.1.101 Mar 15 21:31:19 originix in.telnetd[1796]: connect from 192.168.1.101 Mar 15 21:31:23 originix sshd[1795]: Did not receive ident string from 192.168.1.101. Mar 15 21:31:24 originix telnetd[1796]: ttloop: peer died: Invalid or incomplete multibyte or wide character Mar 15 21:31:24 originix ftpd[1794]: FTP session closed Mar 15 21:32:27 originix in.rexecd[1797]: connect from 192.168.1.101 Mar 15 21:32:27 originix in.rexecd[1797]: connect from badman Mar 15 21:32:27 originix in.rlogind[1798]: connect from 192.168.1.101 Mar 15 21:32:27 originix in.rshd[1799]: connect from 192.168.1.101 Mar 15 21:32:27 originix rshd[1799]: Connection from 192.168.1.101 on illegal port Mar 15 21:32:34 originix rlogind[1798]: Connection from 192.168.1.101 on illegal port Mar 15 21:32:34 originix rlogind[1798]: PAM pam_end: NULL pam handle passed
TCP Term (see Figure 4-5) lets you directly connect to a specific port on a specific host and interact with whatever service is listening behind it. In our previous port scan, many ports returned data (the green “d” circles) that could give us valuable information about the services running behind them. Some services, such as httpd (a web server), will usually return data only if someone first sends it some data. This section allows us to do that. In Figure 4-5, we send the web server on 192.168.1.50 a GET / HTTP command followed by two presses of the ENTER key to retrieve some data from it. We are able to discover the type of web server (Apache), its version (1.3.14 for Unix), and the operating system on which it’s running (RedHat Linux).
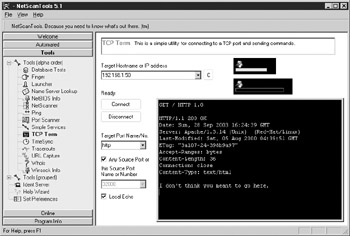
Figure 4-5: TCP Term—talk with a service
A new feature in version 5 is the “Automated” information gathering tool, shown in Figure 4-6. In Step 1, you choose between three levels, or modes, of thoroughness. In Step 2, you enter the IP address or hostname of the host. Step 3 performs the automated information gathering procedures, and a nicely formatted HTML report of the results is generated in Step 4. This can be a quick, simple way to gather information about a host.
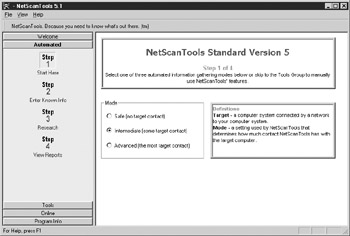
Figure 4-6: NetScanTools Automated information gathering
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 189