America Online Client
|
| < Day Day Up > |
|
America Online (AOL) is used by a large number of individuals, especially for home Internet access. Therefore, using AOL’s client to reconstruct e-mail deserves its own section in this chapter.
AOL tends to be the most difficult to reconstruct of all the e-mail programs. This is in part because, depending on what version of AOL data is located on the suspect’s machine, the same version must be installed on the forensic workstation. Because all the investigations we encountered within the past year contained evidence from AOL clients version 5 or higher, we will concentrate on the newer methods of reconstructing e-mail.
AOL uses the term profile to represent the different logon and e-mail addresses used with the AOL client. Each person who shares a family home computer, for instance, has a different profile; this keeps each user’s e-mail separate and confidential. AOL saves all the information for each profile in one large file. Because more than one profile can be used with a single computer, you must reconstruct each file to gain a complete picture of the Internet activity produced on a particular computer.
AOL’s clients can be located at http://www.aol.com, which includes nearly every version ever distributed. The clients are freely downloadable to the public.
Implementation
The data files for AOL are located in the subdirectory “organize” that exists in the installation directory (in this case it is C:\Program Files\America Online 7.0a\organize) for the AOL client. After this directory has been copied from the suspect’s computer and saved to the forensic workstation, you open the e-mail with an AOL client.
Obviously, the AOL client must first be installed on the forensic workstation before the suspect’s e-mail can be reconstructed. You do not need to acquire a valid AOL account to reconstruct the suspect’s e-mail. Therefore, once you start the AOL client, cancel out of any annoying sign-up screens until the screen looks similar to the following:
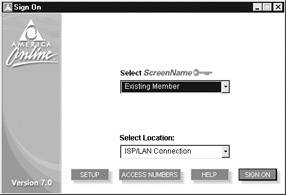
-
Next, copy the “organize” directory to the forensic workstation.
-
Locate the files that do not have filename extensions—fsorensics in the next illustration. These are the account/screen names used with the AOL client. This file will contain the data we will be reconstructing.
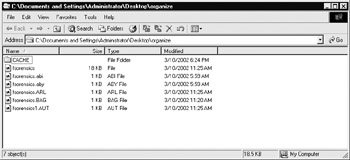
-
Rename the discovered file with an extension of .pfc (fsorensics.pfc in this example). This extension makes the file a personal file cabinet, a file type that AOL clients can open.
-
Choose File | Open within the AOL client. Locate the file that was renamed in step 3 and open it.
-
Repeat steps 2 through 4 for each screen name discovered in the “organize” directory.
After you have accomplished these steps, scroll to the bottom to locate the e-mail folders. The next screen displays the e-mail folders for the account fsorensics@aol.com:
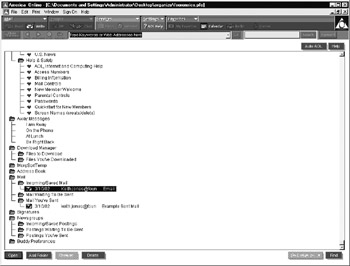
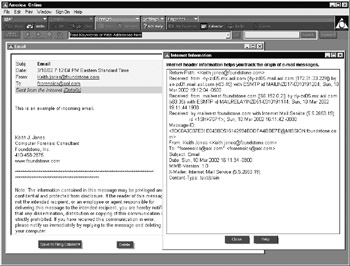
The contents of the e-mail folder can be perused by double-clicking the individual e-mail headers:
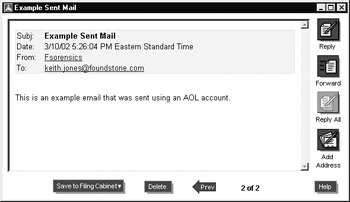
You can view the SMTP headers for received e-mail by clicking the Details button at the top of the individual e-mail message, as shown in the next screen:
An interesting difference between AOL and other mainstream e-mail programs is that AOL can also save favorite web sites visited in the same dataset we just opened. Therefore, you should be certain to review any web sites saved in the Favorites list.
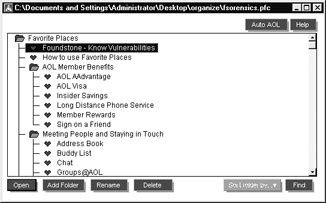
You should also note an additional directory below “organize,” entitled “CACHE,” which may contain older versions of the suspect’s mailboxes. You may find it valuable in many investigations to analyze these files, because as e-mail is added or deleted on the suspect’s computer, the changes would be evident as snapshots in the “CACHE” directory. Using the steps presented earlier, you can reconstruct these files.
|
| < Day Day Up > |
|
EAN: 2147483647
Pages: 189