J2EE.3.2 A Simple Example
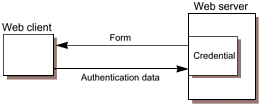
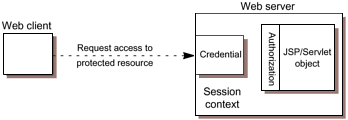
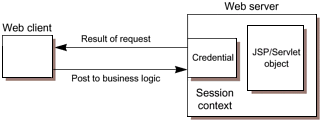
| The security behavior of a J2EE environment may be better understood by examining what happens in a simple application with a web client, JSP page user interface, and enterprise bean business logic. We include here a descriptive example; this example is not meant to specify requirements. In this example, the web client relies on the web server to act as its authentication proxy by collecting user authentication data from the client and using it to establish an authenticated session.
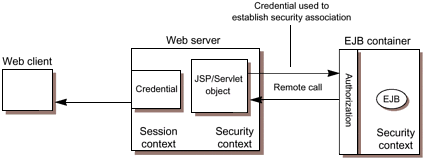
The EJB container is responsible for enforcing access control on the enterprise bean method; it does so by consulting the security policy (derived from the deployment descriptor) associated with the enterprise bean to determine the security roles that are permitted access to the method. Then for each role, the EJB container will use the security context associated with the call to determine if it can map the caller to the role. The evaluation stops with an "is authorized" outcome on the first role that the EJB container is able to map to the caller. A "not authorized" outcome is reached if the container is unable to map the caller to any of the permitted roles and results in an exception being thrown by the container, and propagated back to the caller (in this case the JSP page). If the call "is authorized," the container dispatches control to the enterprise bean method, which then returns a result to the caller. The platform provides two sets of methods for use by security aware applications: the EJBContext methods isCallerInRole and getCallerPrincipal available to enterprise beans through the EJB container, and the HttpServletRequest methods isUserInRole and getUserPrincipal available to servlets and JSP pages through the web container. When an enterprise bean calls the isCallerInRole method, the enterprise bean container determines if the caller (as represented by the security context) is in the specified role. When an enterprise bean calls the getCallerPrincipal method, the enterprise bean container returns the principal associated with the security context. The web container APIs behave similarly. |
EAN: 2147483647
Pages: 399
- Chapter I e-Search: A Conceptual Framework of Online Consumer Behavior
- Chapter II Information Search on the Internet: A Causal Model
- Chapter IV How Consumers Think About Interactive Aspects of Web Advertising
- Chapter XI User Satisfaction with Web Portals: An Empirical Study
- Chapter XVIII Web Systems Design, Litigation, and Online Consumer Behavior