Kevin Mitnick s Session Hijack Attack
| < Day Day Up > |
Kevin Mitnick's Session Hijack AttackProbably the most famous session hijacking attack is that done by Kevin Mitnick against the computers of Tsutomu Shimomura at the San Diego Supercomputer Center on Christmas day, 1994. Because of its historical significance and brilliant approach to session hijacking, it is worth mentioning here. The exploit was accomplished in ten steps:
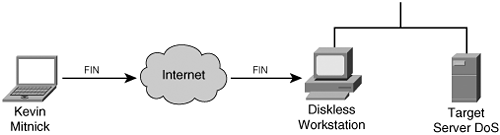
Note Tsutomu Shimomura publicized the attack method in several security newsgroups. You can read his detailed analysis of the attack at http://www.gulker.com/ra/hack/tsattack.html. Mitnick began by launching his attack from a computer on a compromised host on the toad.com network (managed by John Gilmore). From this host, he executed the UNIX commands finger, showmount, and rpcinfo, as illustrated in Figure 6-8. Figure 6-8. Stage One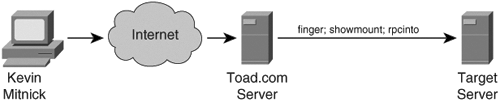 Next, Mitnick sent 30 SYN packets from an unused IP address, as illustrated in Figure 6-9. In doing so, he filled up the server queue with half-open TCP connections (sometimes called TCP embryonic connections). Figure 6-9. Stage Two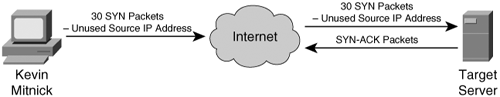 Mitnick then had to determine the ISN to be used in attacking the server of Shimomura. He did this by sending TCP packets to a diskless workstation on the Shimomura network from a compromised host on the luc.edu network. The luc.edu host sends RST packets after every SYN-ACK response from the diskless workstation so as not to fill up the workstation queue and raise suspicion. (See Figure 6-10.) By listening to the SYN-ACK responses from the workstation, Mitnick was able to see that the sequence number incremented by 128,000 each time. Figure 6-10. Stage Three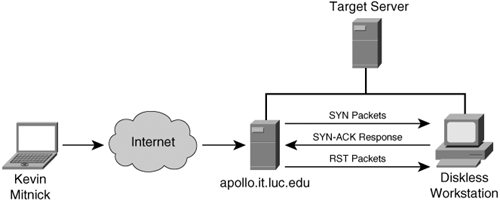 In stage four, Mitnick spoofs the target server and attempts to launch the rshell daemon to the workstation. When the workstation sends a SYN-ACK reply to the real server, the server ignores the packet because its queue is filled (done in stage two). Figure 6-11 illustrates stage four of the attack. Figure 6-11. Stage Four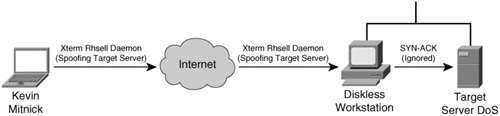 Mitnick continues to spoof the real server and returns an ACK to the workstation. The sequence number is predicted using the information gathered in stage three. This completes the three-way TCP handshake to form a session. Figure 6-12 illustrates stage five of the attack. Figure 6-12. Stage Five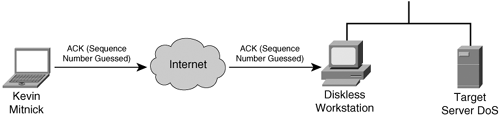 Now that an rshell connection exists from the spoofed server to the workstation, Mitnick launches the following command: #rsh x-terminal "echo ++ >> /.rhosts" The .rhosts file defines which remote hosts can invoke commands without supplying a password. The plus sign signifies that any host is trusted. Mitnick now has full access to the workstation. Figure 6-12 illustrates stage six of the attack. Figure 6-13. Stage Six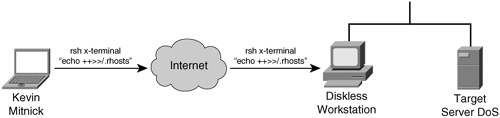 Next, Mitnick has to clear the session from his machine (spoofing as the server) to the diskless workstation. He does this by sending a FIN packet indicating to the workstation that the TCP session should be closed, as illustrated in Figure 6-14. Figure 6-14. Stage Seven In stage eight, Mitnick clears out the queue on the real server so that communication can be established to it. Because he filled the queue with 30 SYN packets (stage two), he now closes it with 30 RST (reset) packets, as illustrated in Figure 6-15. Figure 6-15. Stage Eight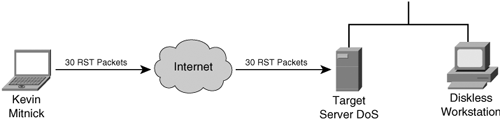 Mitnick now accesses the workstation with the same spoofed address in stage two and seven and compiles and installs a STREAMS module called tap-2.01, as illustrated in Figure 6-16. This kernel module allows Mitnick to perform a session hijack similar to that invoked with TTY-Watcher. Figure 6-16. Stage Nine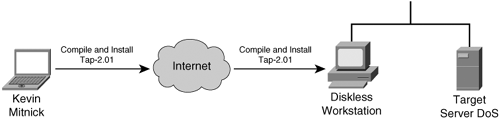 At this point, Kevin looks for an already authenticated session between the workstation and the target server. Using his session hijacking tool, he hijacks a session and gains access to the target server at 2:51 p.m. Christmas day, as illustrated in Figure 6-17. Figure 6-17. Stage Ten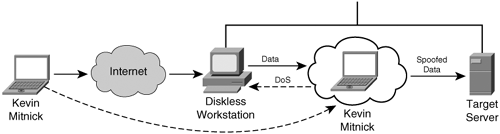 It took a total of 42 minutes for Kevin Mitnick to hijack a system and gain control of the server of Tsutomu Shimomura. |
| < Day Day Up > |
EAN: 2147483647
Pages: 209