19.8 Encryption of a Block as a Complete Process
19.8 Encryption of a Block as a Complete Process
Encryption with Rijndael is encapsulated in the following pseudocode according to [DaRi], Sections 4.2–4.4. The arguments are passed as pointers to fields of bytes or 4-byte words. The interpretation of the fields, variables, and functions employed is provided in Tables 19.15-19.17.
| Variable | Interpretation |
|---|---|
| Nk | length Lk of the secret user key in 4-byte words |
| Nb | block length Lb in 4-byte words |
| Nr | round number Lr according to the table above |
| Variables | Size in bytes | Interpretation |
|---|---|---|
| CipherKey | 4*Nk | secret user key |
| ExpandedKey | 4*Nb * (Nr+1) | field of 4-byte words to hold the round key |
| Rcon | 4*Nb * (Nr+1)/Nk | field of 4-byte words as constant c(j) := (rc(j), 0, 0, 0) |
| State | 4*Nb | field for input and output of plain text and encrypted blocks |
| RoundKey | 4*Nb | round key, segment of ExpandedKey |
| Function | Interpretation |
|---|---|
| KeyExpansion | generation of round key |
| RotByte | left rotation of a 4-byte word by 1 byte: (abcd) → (bcda) |
| ByteSub | S-box substitution S of all bytes of the passed field |
| Round | regular round |
| FinalRound | last round without MixColumn |
| ShiftRow | ShiftRow transformation |
| MixColumn | MixColumn transformation |
| AddRoundKey | addition of a round key |
Key generation for Lk < 8:
KeyExpansion (byte CipherKey, word ExpandedKey) { for (i = 0; i < Nk; i++) ExpandedKey[i] = (CipherKey[4*i], CipherKey[4*i + 1], CipherKey[4*i + 2], CipherKey[4*i + 3]); for (i = Nk; i < Nb * (Nr + 1); i++) { temp = ExpandedKey[i − 1]; if (i % Nk == 0) temp = ByteSub (RotByte (temp))^ Rcon[i/Nk]; ExpandedKey[i] = ExpandedKey[i − Nk] ^ temp; } } Key generation for Lk = 8:
KeyExpansion (byte CipherKey, word ExpandedKey) { for (i = 0; i < Nk; i++) ExpandedKey[i] = (CipherKey[4*i], CipherKey[4*i + 1], CipherKey[4*i + 2], CipherKey[4*i + 3]); for (i = Nk; i < Nb * (Nr + 1); i++) { temp = ExpandedKey[i − 1]; if (i % Nk == 0) temp = ByteSub (RotByte (temp)) ^ Rcon[i/Nk]; else if (itemp = ByteSub (temp); ExpandedKey[i] = ExpandedKey[i − Nk] ^ temp; } } Round functions:
Round (word State, word RoundKey) { ByteSub (State); ShiftRow (State); MixColumn (State); AddRoundKey (State, RoundKey) } FinalRound (word State, word RoundKey) { ByteSub (State); ShiftRow (State); AddRoundKey (State, RoundKey) } Entire operation for encrypting a block:
Rijndael (byte State, byte CipherKey) { KeyExpansion (CipherKey, ExpandedKey); AddRoundKey (State, ExpandedKey); for (i = 1; i < Nr; i++) Round (State, ExpandedKey + Nb*i); FinalRound (State, ExpandedKey + Nb*Nr); } There exists the possibility of preparing the round key outside of the function Rijndael and to pass the key schedule ExpandedKey instead of the user key CipherKey. This is advantageous when it is necessary in the encryption of texts that are longer than a block to make several calls to Rijndael with the same user key.
Rijndael (byte State, byte ExpandedKey) { AddRoundKey (State, ExpandedKey); for (i = 1; i < Nr; i++) Round (State, ExpandedKey + Nb*i); FinalRound (State, ExpandedKey + Nb*Nr); } Especially for 32-bit processors it is advantageous to precompute the round transformation and to store the results in tables. By replacing the permutation and matrix operations by accesses to tables, a great deal of CPU time is saved, yielding improved results for encryption, and, as we shall see, for decryption as well. With the help of four tables each of 256 4-byte words of the form
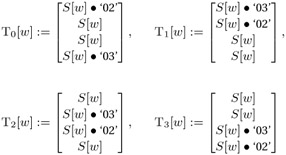
(for w = 0,..., 255, S(w) denotes, as above, the S-box replacement), the transformation of a block b = (b0,j, b1,j, b2,j, b3,j), j = 0,..., Lb − 1, can be determined quickly by the substitution
![]()
with d(i, j) := j − ![]() mod Lb (cf. ShiftRow, Table 19.14) and kj = (k0,j, k1,j, k2,j, k3,j) as the jth column of the round key.
mod Lb (cf. ShiftRow, Table 19.14) and kj = (k0,j, k1,j, k2,j, k3,j) as the jth column of the round key.
For the derivation of this result, see [DaRi], Section 5.2.1. In the last round the MixColumn transformation is omitted, and thus the result is determined by
![]()
Clearly, it is possible to use a table of 256 4-byte words, in which
![]()
with a left rotation r(a, b, c, d) = (b, c, d, a) by one byte. For environments with limited memory this can be a useful compromise, the price being only a slightly increased calculation time for the three rotations.
| Team-Fly |
EAN: 2147483647
Pages: 127