WAR-DIALING
|
|
The most common way to access another computer is through the Internet, but just cutting off Internet access won't stop a hacker. After installing firewalls and intrusion detection systems, many companies essentially circumvent their own defenses by installing modems connected to outside telephone lines so that sales people or telecommuting workers can access that computer from any telephone line in the world.
Individuals may also be vulnerable if they run remote access programs such as pcAnywhere on their computers. Whenever you connect a computer to a modem and an outside telephone line, that telephone line suddenly opens a doorway into your computer.
To prevent unauthorized people from accessing these computers, corporations and individuals keep the telephone numbers of their computers secret and unlisted. While this may stop the majority of people, it won't stop a hacker.
To find a telephone number leading to a computer, hackers start out by using educated guessing. If they want to attack a specific target, they first find out the telephone numbers that a company may use. For example, if a hacker wants to find the telephone number to a computer that belongs to the local corporate office, he just looks in the telephone book to find all the phone numbers that lead to that particular building. Generally when the telephone company assigns numbers to a corporate office, all the telephone numbers share the same prefix, such as 234-1090 and 234-3582.
So if there's a vulnerable computer with a modem stored anywhere in this company, chances are nearly 100 percent that the telephone number that reaches this computer also begins with the same 234 prefix. While a hacker could spend all night dialing different telephone-number combinations until he reached a modem on the other end, hackers simply let their computers do this tedious work instead, by running a special program called a war-dialer or demon dialer (see Figure 11-1).
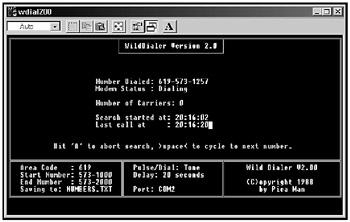
Figure 11-1: A war-dialer dials a range of telephone numbers and keeps track of all numbers that lead to a computer.
If a hacker knew that a certain company's telephone numbers all started with 234, he could program his war-dialer to dial every number from 234-0000 to 234-9999. Each time the war-dialer finds a telephone number that leads to a computer modem (such as 234-3024), the war-dialer saves that number for the hacker to examine later. This means that if there's a telephone number that allows others to access a computer, it's only a matter of when, not if, a hacker will find that telephone number.
After a war-dialer finds all the telephone numbers that connect to a computer, a hacker can then probe each telephone number individually. Before a computer will allow access through a telephone line, it usually asks for a password. All the hacker needs to do now is guess the correct password, and the computer will open its gates and let the hacker inside.
One of the simplest defenses against war-dialing is a call-back device. The moment someone (a valid user or an intruder) calls the computer, the call-back device hangs up and dials a prearranged telephone number that only a valid user would be at. Of course, a determined hacker would simply find out the phone number that the call-back device will dial and then use call forwarding on that number to reroute the call to the hacker's phone number.
|
|
EAN: 2147483647
Pages: 215