STOPPING A TROJAN HORSE
|
|
To protect yourself against Trojan horses, use a combination of different protective tools and a little common sense.
First of all, make sure you know who has access to your computer. Lock it up, password protect it, or disconnect it from a network if you're not using it.
Second, be careful where you get your software. Anytime someone tries to give you a program through email, a chat room, or an instant message, watch out! That program could be infected with a Trojan horse, either with or without the sender's knowledge.
When downloading software, download only from the software publisher's official website. If you download a program from another website, someone could have inserted a Trojan horse into that program. Many hacker websites even post pirated software and hacker tools for others to download, and some of those files could also be infected with a Trojan horse.
But no matter how careful you may be with your computer, someone could also slip a Trojan horse on your computer in your absence. To further protect yourself, consider installing a rollback program, an antivirus program, a firewall, and an anti–Trojan horse program.
Rollback programs
One of the biggest problems with today's software is that much of it, once installed, seems to muck up even perfectly fine computers. Rollback programs guard against these problems by tracking changes made to your hard disk and taking periodic "snapshots" of the contents of your hard disk. That way, if a newly installed program crashes your computer, you can run the rollback program to undo the changes you made to your hard disk and return your computer to its prior condition.
Although originally designed to protect against software conflicts, rollback programs can also protect your computer against viruses or Trojans. The moment a Trojan wipes out your data, run your rollback program to return your computer to the state it was in before the Trojan horse wiped out your hard disk.
While rollback programs can recover your computer from damage caused by a Trojan horse, virus, or even hard disk crash, they can't prevent problems from happening in the first place. But when used together with frequent backups, a rollback program can provide valuable insurance for your important data and reduce the chance that a Trojan horse attack will prove catastrophic.
Some of the more popular rollback programs that you can buy include ConfigSafe (http://www.imagine-lan.com), FlashBack (http://www.aladdinsys.com), GoBack (http://www.roxio.com), EasyRestore (http://www.powerquest.com), and Undelete (http://www.execsoft.com).
Antivirus programs
Although antivirus programs are designed to detect and remove computer viruses, many can also detect and remove the client files of the more common RATs. However, antivirus programs may only recognize the most popular Trojans, so they may not protect you against lesser-known, destructive Trojans, RATs, or custom Trojans. Consider an antivirus program a supplement to the defense of your computer, but not your sole defense against Trojan horses.
Firewalls
A firewall can isolate your computer network from any outside threats (see Figure 8-4). While a firewall can't remove a Trojan horse, it can monitor and shut down external traffic flowing through any open ports on your computer. By shutting down a port, a firewall prevents hackers from accessing your computer through a RAT. Firewalls can also track and log all attempts to access your computer, trace an intruder probing your computer for openings, and sound an alarm whenever someone tries to access your computer without your permission.
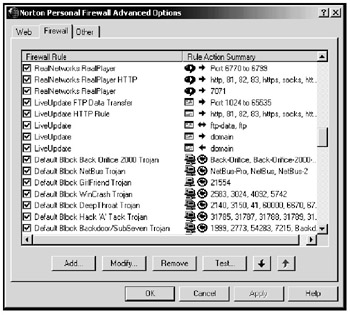
Figure 8-4: A firewall can monitor specific ports and notify you if any are being used without your knowledge.
Some of the more popular firewalls include: BlackICE PC Protection (http://www.iss.net), Personal Firewall (http://www.mcafee.com), Norton Internet Security (http://www.symantec.com), Outpost and Jammer (http://www.agnitum.com), and ZoneAlarm (http://www.zonelabs.com).
Anti–Trojan horse programs
Your best defense against a Trojan horse is to install a program specifically designed to scan and remove any Trojans from your computer. Anti–Trojan horse programs contain a database of Trojan horse signatures that are unique to particular Trojan horses (see Figure 8-5). The program scans the hard disk and checks whether the content of any file matches a known Trojan horse signature stored in its database. If the programfinds a match, it knows it has found a Trojan horse, and it can then remove the offending program and fix any changes it might have made to other parts of the hard disk, like the Windows registry.
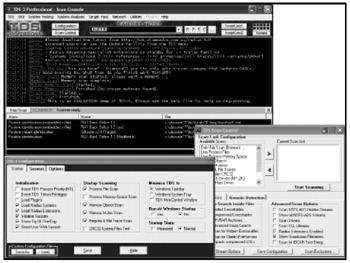
Figure 8-5: An anti–Trojan horse program knows how to detect and remove dangerous Trojan horses before they have a chance to attack your computer.
Unlike firewalls that can block ports that would allow access to your computer through a network or the Internet, anti–Trojan horse programs can monitor open ports for suspicious behavior associated with Trojan horse activity. The moment a RAT tries to access or open a port on your computer, an anti–Trojan horse program can detect the activity, find the Trojan horse, and kill it.
Like antivirus programs, anti–Trojan horse programs must be constantly updated to protect against the latest Trojans. Some popular anti–Trojan horse programs include: Hacker Eliminator (http://hacker-eliminator.com), Tauscan (http://www.agnitum.com), TDS-3: Trojan Defence Suite (http://tds.diamondcs.com.au), NetSpyHunter (http://www.netspyhunter.com), Anti-Trojan (http://www.anti-trojan.net), and The Cleaner (http://www.moosoft.com).
Hacker anti-Trojan tools
Since hackers often target each other, many hackers have written their own tools to remove specific Trojan horses from their computers. Unlike general purpose anti–Trojan horse programs that scan for all known Trojan horses, hacker Trojan horse–removing programs are meant to detect and remove a specific Trojan horse. (Just be careful that some malicious hacker doesn't infect an anti–Trojan horse program with a real Trojan horse and trick you into downloading it.)
To find a hacker anti–Trojan horse program, look for programs with names such as Back Orifice Eradicator, Busjack, NetBus Remover, Nemesis, Anti Socket, Anti BD, Backfire, BO2K Server Sniper, TW-Trojan Scanner, or Toilet Paper.
|
|
EAN: 2147483647
Pages: 215