Appendix B: A Hacker s Gallery of Rogue Tools
|
|
WITH SO MANY HACKER TOOLS AVAILABLE ON THE INTERNET, IT'S QUITE POSSIBLE THAT HACKERS MAY ATTACK YOUR COMPUTER WITH SOME OF THE MORE POPULAR HACKER PROGRAMS ONE DAY. Since most people aren't likely to see, let alone use, these hacker tools, this appendix contains screenshots from a selection of recent and previously popular hacker tools. This will give you a historical and present-day perspective of the tools that hackers use when they attack someone (maybe even you) over the Internet.
INTERNET HACKER TOOLS
Hackers are generally lazy but intelligent, which means they don't like doing something boring that they can program the computer to do for them instead. As a result, hackers have unleashed a variety of tools designed to make their lives easier (but their victims' lives more miserable). Some of these tools include scanners (to find open ports on vulnerable computers), remote Trojan horse programs (to take over a computer through the Internet), and password crackers (designed to exhaustively try out different password combinations until they finds one that works). To see what types of tools hackers may use against you, browse through the following:
AOHell
Released around 1995, AOHell (see Figure B-1) defined the standard for online harassment programs and quickly spawned numerous copycats for harassing other online services including CompuServe, Prodigy, and the Microsoft Network. Written in Visual Basic 3.0, AOHell was a relatively simple program that helped hackers send spoofed email, create phony credit card numbers for making fake AOL accounts, con AOL users out of passwords and credit card numbers, and send insulting messages to others in chat rooms.

Figure B-1: AOHell, the first and original online harassment tool.
Although AOHell initially caused problems for America Online users, the program is now obsolete. Few hackers are currently developing AOHell copycat programs, preferring to channel their energy towards creating more sophisticated Internet hacking tools such as port scanners or harassment tools that cause chaos on IRC or in ICQ chat rooms.
BO2K – Back Orifice
With a name deliberately chosen to mock Microsoft's Back Office program, Back Orifice caused a sensation when released in 1998 as one of the first remote access Trojan horse programs that could remotely control another computer over a phone line or through the Internet (see Figure B-2).
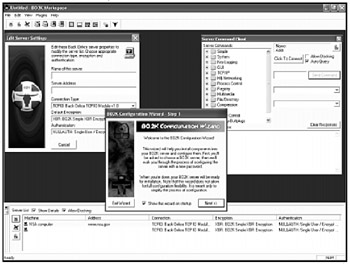
Figure B-2: Back Orifice 2000 is the latest incarnation of the popular and ground-breaking remote access Trojan horse.
Developed by a hacker group calling themselves the Cult of the Dead Cow, Back Orifice (http://www.bo2k.com) made headlines again in 1999 when it was released at DefCon 7.0 with improvements, including the option of adding plug-in programs written by others, and the complete C/C++ source code so that anyone could study and modify the program. Ironically when introduced at DefCon, the Back Orifice 2000 CD was infected by the Chernobyl (CIH) virus.
Although Back Orifice still poses a threat to computers, the buzz surrounding BO2K has faded. Still, the program has spawned numerous remote access copycats programs that have improved upon the original Back Orifice design, and despite its age, Back Orifice still remains a favorite tool for hackers to probe computers connected to cable or DSL modems.
Crack Whore
One of the new breed of website hacking programs, Crack Whore uses a brute force/dictionary attack against a website to find the password to a legitimate account (see Figure B-3). Since so many people use weak, easy to guess passwords, programs like Crack Whore are surprisingly successful far more often than they should be.
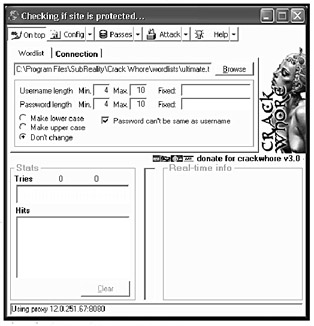
Figure B-3: Crack Whore probes a website for easily-guessed passwords to give a hacker access to a system.
Once hackers have access to a legitimate account, they can either modify web pages and other data directly or attempt to burrow through the system and either gain access to additional accounts or elevate the current account to get greater access to the rest of the computer hosting a particular website.
Death ‘n Destruction
One of the simplest denial-of-service (DoS) hacking tools, Death ‘n Destruction sends endless streams of useless data to a victim's computer port (usually port 139), effectively overwhelming the target computer and causing it to crash or disconnect from the Internet (see Figure B-4).
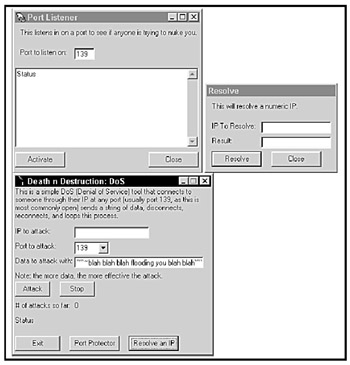
Figure B-4: Death ‘n Destruction can flood a computer with useless data as a primitive, but effective, form of a denial-of-service attack.
ICQ War 2000
With the popularity of instant messaging services (and the dwindling popularity of online services), hackers quickly turned their attention from writing online harassment programs such as AOHell clones and started writing ICQ harassment tools instead (see Figure B-5).
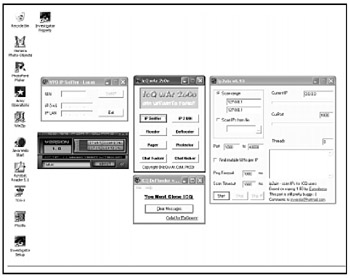
Figure B-5: ICQ War 2000 provides multiple features for harassing someone (and protecting yourself) while using ICQ.
ICQ War 2000 is one of many multi-purpose ICQ harassment programs that can flood a victim with messages, track down a person's IP address, and disrupt chat rooms with insults and obscenity.
John the Ripper
One of the more popular password cracking programs available, John the Ripper runs under UNIX and MS-DOS to crack weak UNIX passwords and systems such as Linux, FreeBSD, OpenBSD, Solaris, Digital UNIX, AIX, HP-UX, and IRIX.
John the Ripper can automatically detect DES, MD5, and Blowfish encrypted UNIX passwords and use a brute force attack to uncover easy-to-guess passwords (see Figure B-6). Once hackers have a password, they can log in to a valid account and establish a foothold on a computer.
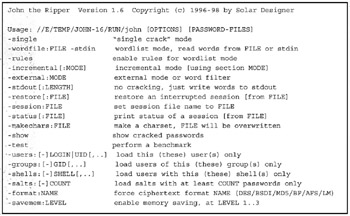
Figure B-6: John the Ripper is a command-line program that can find weak passwords on UNIX-based systems.
NetBus
Originally developed as a remote access Trojan similar to Back Orifice, newer versions of NetBus are now being marketed as a legitimate remote access administrative tool. Despite this change of focus by the NetBus programmers, hackers continue to use earlier versions of NetBus (see Figure B-7) to secretly access other computers. In addition, many hacker websites provide the original Delphi source code so anyone can make modifications to create a new version of NetBus or write an entirely different remote access Trojan horse.
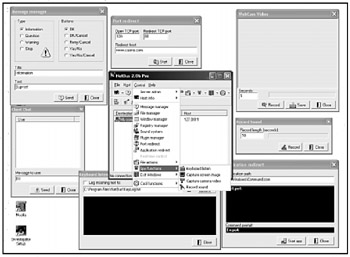
Figure B-7: NetBus is one of the more popular remote access Trojan horse programs.
Nmap
Considered one of the best scanning tools for probing a system, Nmap incorporates almost every scanning technique known into one single program (see Figure B-8). Depending on the scanning option you use, Nmap can offer you speed or stealth (to prevent a target computer from knowing it's being probed) using a variety of different protocols (ICMP, UDP, TCP, etc.). You can safely assume that given enough time, Nmap can find an opening in practically any computer.
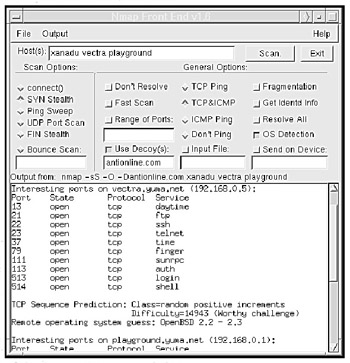
Figure B-8: Nmap provides a variety of scanning techniques to help you probe the vulnerabilities of a computer.
Nmap runs on UNIX-based operating systems such as Linux and FreeBSD, and comes with full C/C++ source code that you can study and modify. With an active programming community behind it, Nmap is likely to continue for some time as the most powerful scanning tool available to both system administrators and hackers.
SubSeven
While development of Back Orifice has slowed to a crawl, a new Trojan horse named SubSeven has taken its place as the most popular Trojan horse to use (see Figure B-9). SubSeven's programmers continue to add new features to the program, such as a text-to-speech module, a spy program for retrieving passwords and other data used by instant messaging programs, and the ability to retrieve a variety of information from an infected computer such as the user's name, address, and even Windows CD key number.
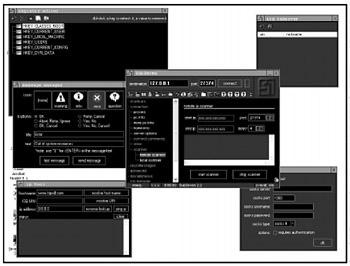
Figure B-9: SubSeven has surpassed Back Orifice as the most popular remote access Trojan horse currently in use.
To help stay in touch with other users, SubSeven's programmers even offer a mailing list and IRC chat room. With the popularity of SubSeven, more computers could eventually be infected by SubSeven than other remote access Trojan horse.
UpYours
For a brief period, email bombs surged in popularity. The idea was to flood a single email account with multiple messages or to subscribe a victim to multiple mailing lists, usually to topics that included child pornography, sexual bondage, or necrophilia.
In 1996, a hacker named "johnny xchaotic" made the headline news when, on two separate occasions, he email bombed various organizations and prominent people including Bill Gates, the Ku Klux Klan, Pat Buchanan, Bill Clinton, the Church of Scientology, and Newt Gingrich.
Email bombing quickly faded as ISPs shut down their mail forwarding services and removed websites that offered email bombing programs. While still an effective tool, email bombing programs like UpYours can reveal an attacker's IP address, further reducing the appeal of attempting a large-scale email bombing attack (see Figure B-10).
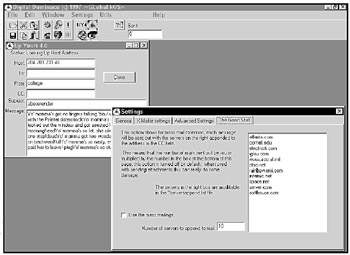
Figure B-10: UpYours was one of the original email bombing programs that provides a variety of options for email bombing a victim.
|
|
EAN: 2147483647
Pages: 215