FIREWALLS: THE FIRST LINE OF DEFENSE
|
|
At the very least, every computer should have a firewall, which acts like a locked door to keep intruders from the Internet out of your computer. A firewall can't provide 100 percent protection against hackers, but it can protect you against a large majority of hackers who simply prowl a range of IP addresses, searching for a vulnerable computer. The moment a hacker finds a computer without a firewall, it's relatively trivial for that hacker to break in. Although computers connected to the Internet through a DSL or cable modem are particularly susceptible to hacker attacks, computers that rely on dial-up access can still be vulnerable.
If you get a firewall, you can choose between hardware or software firewalls. It's possible to use both hardware and software firewalls together, although this will not necessarily give you twice the protection, since the two firewalls may guard (and ignore) the same types of intrusions. Firewalls, like other types of computer equipment and programs, also have their share of bugs, so it's entirely possible to install a firewall only to find that a hacker has found some flaw and managed to bypass it anyway.
How firewalls work
Firewalls work by blocking communication to and from your computer. Many hackers use port scanners to locate potential targets (see Chapter 11), so a firewall can block port scanners to keep the hacker from reaching your computer. At the simplest level, the firewall blocks a port scan, which tells the hacker that a firewall exists. On a more complicated level, the firewall may mask your computer's existence, essentially making it invisible to hackers using port scanners. In this case, the hacker won't know if he found a computer protected by a firewall or just an invalid IP address. In either case, the hacker will likely leave your computer alone and look for an easier target to attack.
Firewalls also serve a second purpose in controlling what your computer can do over the Internet. Many firewalls examine the programs on your computer that connect to the Internet, and allow you to choose the programs that have your permission to connect, such as your browser, your email program, and an instant messenger program. If the firewall detects a program that you haven't specifically approved, the firewall blocks it and notifies you. By blocking unauthorized programs from accessing the Internet, firewalls can stop remote access Trojans (RATs) from secretly connecting to a hacker and giving the hacker control over your computer. Since many spyware programs (see Chapter 17) can transmit records of keystrokes and screenshots of the programs you use to someone who may be spying on you, firewalls can help you detect and block spyware programs, too.
To allow legitimate traffic to pass through a firewall, you may need to tell the firewall what is and is not permissible on your computer. Four criteria that firewalls may use to block illegal traffic are IP addresses, protocols, ports, and specific programs.
IP addresses identify specific computers, so a firewall can either block traffic from certain IP addresses (such as the IP address of Playboy 's website) or conversely, only accept connections from specific IP addresses (such as a trusted corporate computer).
Firewalls may also allow or block certain protocols, which are specific ways that computers send and receive data (see Figure 18-1). For example, a firewall may only allow HTTP (Hypertext Transfer Protocol) through, which sends web pages over the Internet (this is the "http" that appears at the beginning of website addresses). Likewise, a firewall may block FTP (File Transfer Protocol), which can send and receive files. Some other types of protocols that a firewall may block include the following:
-
UDP (User Datagram Protocol) Used for transmitting information that does not require a response, such as streaming audio or video.
-
ICMP (Internet Control Message Protocol) Used to report errors to other computers.
-
SMTP (Simple Mail Transfer Protocol) Used for sending and receiving email.
-
Telnet Used to access and control a remote computer.
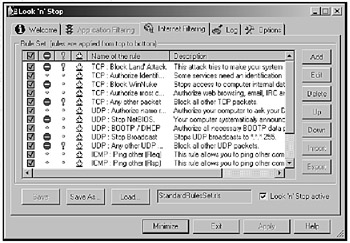
Figure 18-1: You can define the types of protocols that the firewall allows.
By blocking certain protocols, firewalls can prevent certain types of attacks on a protected computer. For example, blocking the Telnet protocol can keep a hacker from controlling and manipulating your computer over the Internet (although it's possible for the hacker to use a different protocol to achieve the same purpose).
Besides blocking certain protocols, firewalls may block certain ports. Ports allow certain types of communication into a computer, so firewalls typically block every port except for the essential ones, such as port 80 (used for browsing web pages) and port 25 (used for sending and receiving email). By shutting down certain ports, a firewall can prevent a hacker from sneaking in through a forgotten open port or from opening an obscure port to transmit information from your computer back to the hacker. Of course, shutting down ports only forces hackers to direct their attacks through the open ports, but it does limit the types of attacks a hacker can use against your computer.
Firewalls may also allow access to the Internet only from certain trusted programs, like a web browser or email program. If any other type of program tries to access the Internet, the firewall blocks its attempt, assuming that the program could be a Trojan horse or hacker trying to send data out from your computer.
Through the combination of filtering IP addresses, protocols, ports, and even specific words or phrases, firewalls can block most unwanted attempts to break into your computer. To find a hardware-based firewall, visit one of the following sites:
| Netgear | http://www.netgear.com |
| TRENDware | http://www.trendware.com |
| D-Link | http://www.dlink.com |
To find a software-based firewall, Windows users can look at these options:
| Tiny Personal Firewall | http://www.tinysoftware.com |
| ZoneAlarm | http://www.zonelabs.com |
| Look ‘n' Stop | http://www.looknstop.com |
| Norton Internet Security | http://www.symantec.com |
| Outpost Firewall | http://www.agnitum.com |
| Sygate Personal Firewall | http://soho.sygate.com |
| Personal Firewall | http://www.mcafee.com |
Many versions of Linux come with a firewall, and if you happen to be using Windows XP, you have a built-in firewall that you can turn on by following these steps:
-
Click the Start button.
-
Click Control Panel.
-
Click Network and Internet Connections.
-
Click Network Connections. A Network Connections window will open.
-
Right-click on the Local Area Connection icon, and when a pop-up menu appears, click Properties. A Local Area Connection Properties dialog box appears.
-
Click the Advanced tab.
-
Click the "Protect my computer and network by limiting or preventing access to this computer from the Internet" check box so a check mark appears.
-
Click OK.
Macintosh users can take a look at these two firewalls: Firewalk (http://www.pliris-soft.com) and NetBarrier (http://www.intego.com). And if you want to contribute your programming skills to developing a firewall for Linux, visit the Falcon Firewall Project (http://falcon.naw.de). By studying the source code to this firewall, you can get a better understanding of how firewalls work and possibly modify the firewall to protect everyone against the latest threats on the Internet.
One of the biggest problems with firewalls is that most novices have no idea how to evaluate them. Besides looking at a pretty user interface, novices aren't likely to understand the capabilities of what each firewall may offer. To learn more about the details of firewalls and how to choose the best one for you, visit the following sites, which offer technical comparisons of the most popular firewalls:
| Home PC Firewall Guide | http://www.firewallguide.com |
| Firewall.com | http://firewall.com |
| Firewall.net | http://www.firewall-net.com |
| Free-Firewall.org | http://www.free-firewall.org |
How firewalls can be defeated
Perhaps the biggest problem with firewalls is that they take time to configure, which means that most novices will likely configure the firewall incorrectly, which either gives a false sense of security while leaving gaping holes open in the firewall's defenses, or causes increased frustration when the firewall winds up stopping legitimate programs from working, such as an email or instant messenger program. If a firewall gets too aggressive in stopping programs from connecting to the Internet, users may be tempted to just shut off or uninstall the firewall altogether.
Another problem with a firewall is that it can only protect inbound and outbound Internet connections; it can't do a thing to stop someone from accessing a computer through a telephone line, through a wireless access point located behind a firewall (see Chapter 11), or through the keyboard if someone is physically sitting in front of the computer, such as a coworker or the janitor.
Even worse, firewalls can be fooled. If a firewall only allows certain programs to access the Internet, a hacker could simply rename a remote access Trojan horse so that it has the same name as your web browser. Then when this remote access Trojan horse tries to access the Internet, the firewall checks the program's name, finds it matches the list of programs allowed to access the Internet, and falsely allows this program to get through the firewall, which is like a thief fooling a police officer by using a fake picture ID.
Perhaps the most curious way to circumvent firewalls is through a technique known as firewall tunneling. Since firewalls may only allow a computer to use certain protocols and ports, firewall tunneling simply uses whatever ports and protocols the firewall allows to sneak data through. This can be as effective as a hijacker sneaking past airport security dressed up as a pilot.
Two products that allow firewall tunneling include RemFTP (http://www.remftp.com) and HTTP-Tunnel (http://www.http-tunnel.com). RemFTP boasts that it is "a program that connects your home and work computers for file transfer, without having to think about firewalls." HTTP-Tunnel advertises that it "allows people behind restrictive firewalls to use previously blocked applications through their firewall." By using either of these commercially available programs, or the firewall tunneling techniques that they're based on, hackers can circumvent practically any firewall with impunity.
Even worse is that you could configure your firewall correctly, and it could still leave gaping holes in your computer's defenses simply because the firewall happens to lack certain vital features that another firewall may offer. Until you buy and try several different firewalls, you may never know how defenseless a particular firewall may actually be. To test the capabilities of your firewall, download some of the following firewall testing programs to determine if your firewall would stop a typical hacker attack:
| LeakTest | http://grc.com/lt/leaktest.htm |
| FireHole | http://keir.net/firehole.html |
| OutBound | http://www.hackbusters.net/ob.html |
| PC Flank | http://www.pcflank.com |
| Port Detective | http://www.portdetective.com |
| YALTA | http://www.soft4ever.com/security_test/En/index.htm |
| TooLeaky | http://tooleaky.zensoft.com |

Figure 18-2: A firewall testing program can tell you if your firewall is really protecting your computer or not.
Hardening your operating system
Besides installing a firewall, make sure you update your operating system with the latest bug fixes or security patches. Hackers quickly learn all the flaws in a particular operating system, and if they find that flaw on your computer, they may be able to exploit the flaw to get into your computer, regardless of any firewall you may have installed.
The most secure operating system is OpenBSD (http://www.openbsd.org), but if you're using Red Hat Linux, the friendly folks at the National Security Agency have developed a special version dubbed Security-Enhanced Linux (http://www.nsa.gov/selinux), which can harden your version of Red Hat Linux from attack.
For another way to battle-harden Red Hat Linux, visit Bastille Linux (http://www.bastille-linux.org). Like Security-Enhanced Linux, Bastille Linux adds extra security to your Linux operating system to make sure that all possible flaws in your operating system have been shut down.
|
|
EAN: 2147483647
Pages: 215