Hack87.Intercept and Record a VoIP Call
Hack 87. Intercept and Record a VoIP Call
This is the ultimate sneaky way to intercept and record VoIP calls. I'm going to demonstrate why people say VoIP isn't secure. If you've got a laptop and a patch cable, you can record calls from a Cisco CallManager IP telephony network or even from a Vonage subscriber. More specifically, you'll be doing so without the need for port spanning on the switch [Hack #86] and without installing a recorder or sniffer on the device you're trying to record [Hack #85]. Instead, you'll be resorting to a tactic that's, well, unnatural. In fact, if you do this outside the test lab, it could be considered unethical, too, so be careful. I am about to teach you how to secretly listen in on other users' VoIP calls without having any direct contact with their VoIP phones or PCs and without being the administrator of the local network. Be advised, though, I'm not recommending that you ever do this in the field. I'm just passing on some knowledge I picked up while working as a networking consultant. 6.17.1. Get to Know Cain & AbelWhile you're here, make sure you've read "Log and Record VoIP Streams" [Hack #86], which introduces the software tool I'll be using to make all this happen: Cain & Abel. If you don't know Cain & Abel, go back a hack, read it through, and you'll be able to proceed with confidence. Now, on to the hack. An Ethernet switch has anywhere from 4 to 48 ports where Ethernet devices like PCs and IP phones can connect. Each device connected to the switch has a 32-bit hexadecimal address, called a MAC address. Ordinarily, the switch knows which port to send a particular packet to because address resolution protocol (ARP) has been used by the sender (or by the closest router) to address the packet to the correct MAC address. All the switch has to do to get the packet to the right destination is transmit it on the port where the device with a matching MAC address is connected. The secret to recording another person's VoIP calls is in making the switch think your MAC address is a valid destination for the VoIP traffic that's bound for that person's VoIP device. Specifically, when the sending device uses ARP to resolve the IP address of the intended recipient, your PC must respond by saying, "I am the holder of that IP address; send the data to me!" This hack, which rather goes against the prescribed way an Ethernet LAN is supposed to work, is called ARP poisoning. The result is that your PC intercepts the packets destined for the intended MAC address, so you can do with them whatever you like. Once intercepted, the packets must be forwarded to the correct MAC address, or a denial of service will occur on the device you're snooping. In the case of VoIP, your PC can record (or play in real time) the media stream before passing the packets to the actual intended receiver. A classic man-in-the-middle hack, this technique is simplified by the outstanding network tool, Cain & Abel. To get started, use Cain & Abel's host-discovery tool. Click the Sniffer tab and then the Hosts tab at the bottom of the GUI. Then, click the + in the toolbar. This will pop open a dialog where you can tell Cain & Abel to discover all of the devices on your network. I used it to discover the IP and MAC addresses of my Cisco 7960 phone (10.1.1.104) and my Asterisk server (10.1.1.10). Both are listed in Figure 6-16. Figure 6-16. Cain & Abel's list of discovered hosts on the LAN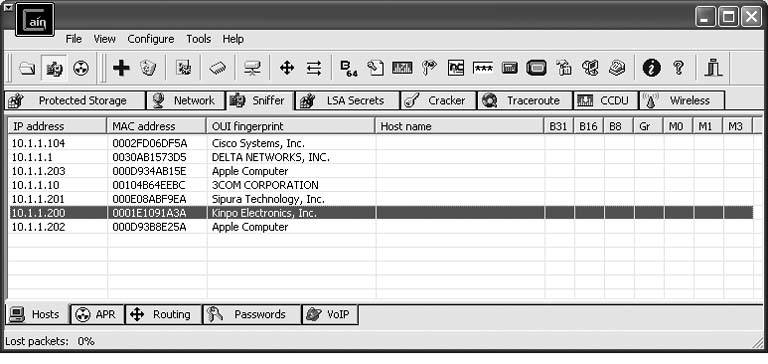 You're discovering all of these hosts and resolving their actual MAC addresses because Cain & Abel will need these details to perform the ARP poisoning. Once you can see the host you want to monitor in the list, click the ARP tab and then click the + toolbar icon again. You'll see the New ARP Poison Routing dialog, as shown in Figure 6-17. Figure 6-17. Cain & Abel's ARP Poison Routing dialog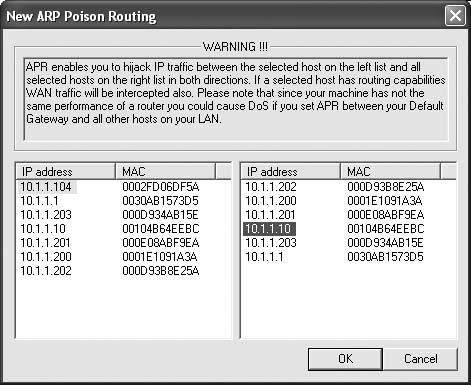 Select the host you want to snoop on the left, and then select one or more of the destinations related to that host on the right. This way, you'll be poisoning ARP requests for the snooped hosts only if they're sent from certain IP addresses. I don't recommend that you ARP poison a large groupthis could cause difficulties on the network, including a rather comprehensive denial of serviceso stick to one IP address on the left and one on the right until you've got the hang of it. Ideally, the address on the right will be the host on the other end of the call, but it doesn't have to be. If the VoIP call is to a user on the Internet somewhere (via the default gateway), you would choose the IP address of your Internet router on the right side. In fact, if you wanted to sniff your Vonage calls, you would pick the address of your Vonage ATA on the left, and the address of your Internet router on the right. Once you've got a pair of addresses selected for monitoring, click OK. Now, start the sniffer and the ARP poison router by clicking the Start/Stop Sniffer icon and the Start/Stop APR icon (which looks like a radiation symbol). Wait for a VoIP call to be placed on the targeted hostor place one yourself on that hostand watch the call list in the VoIP tab. In a moment, an entry will pop up, indicating that the call is in progress and is being recorded into a WAV file by Cain & Abel, as shown in Figure 6-18. Figure 6-18. A call has been logged and recorded in Cain & Abel using ARP poisoning to intercept it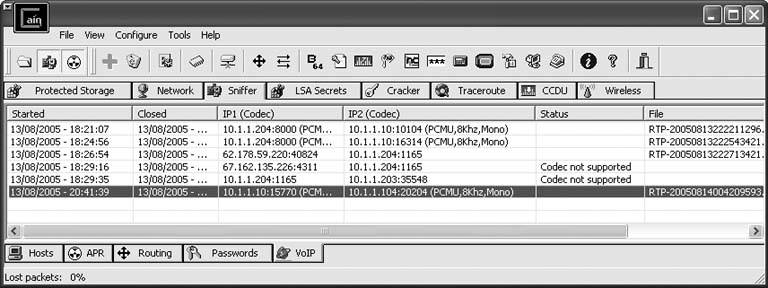 Pretty amazing, eh? One more thing: I can't emphasize enough how unethical this hack would be if performed in an environment where you aren't authorized to take these actions. I strongly urge you to be responsible with this type of hack and keep yourself out of trouble while you learn about VoIP security. Unless you have administrative authorization and the express right to monitor users' calls on the network where you're working, you should keep ARP poisoning confined to the test lab. |
EAN: 2147483647
Pages: 156