Understanding Front-End Servers
| Front-end servers are deployed in an Exchange Server architecture that distributes server tasks among front-end and back-end servers. In this architecture, a front-end server accepts requests from clients and proxies them to the appropriate back-end server for processing and management of the information store. Exchange Server 2003 enhances the front-end and back-end server architecture of Exchange 2000 and adds new features and capabilities, such as RPC over HTTP communication, that enables users with Outlook 2003 clients to access their Exchange information from the Internet. In addition, the HTTP communication between front-end and back-end servers is enabled with Kerberos authentication by default; no longer is it necessary to configure and enable IPSec server-to-server communication unless the server is in a public network. Moreover, the scalability of the exchange organization is now enhanced because the topology can grow as the organization grows; back-end servers can easily be added to handle additional users, connections, or processing requests. Finally, the standard version of Exchange Server 2003 can also be configured as a front-end server, reducing initial software costs. Using front-end and back-end server technology also provides the following advantages both for remote users accessing email over the Internet and users who are located on the internal network:
Note
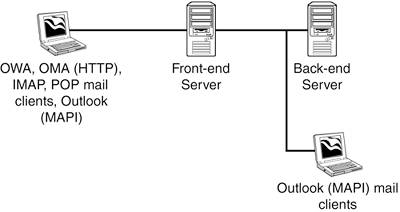
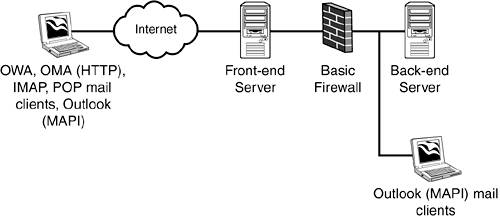
Typical Scenarios for Front-End ServersThere are common implementation scenarios for front-end and back-end server architecture. The first implementation involves email clients (Outlook, POP, or IMAP, OWA [HTTP], OMA [HTTP]) and a network or Internet connection to the front-end server that is serving requests to the back-end server over the internal network. As shown in Figure 2.1 and 2.2, this configuration involves limited security with the front-end server acting as a single layer of protection between the network or Internet and the back-end Exchange server. Figure 2.1. Basic front-end and back-end server architecture with network connection and no firewall.
Figure 2.2. Basic front-end and back-end server architecture with Internet connection and no firewall.
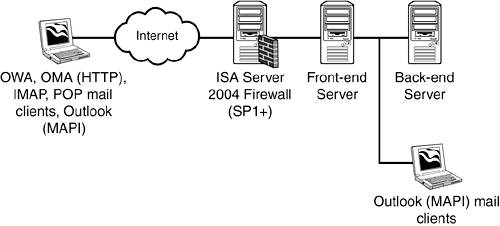
The second scenario, shown in Figure 2.3, involves more security that includes an advanced firewall, such as Microsoft's Internet Security and Acceleration (ISA) service configured with Service Pack 1 and the latest feature packs. The advanced firewall is located between the network or Internet and the front-end server. Figure 2.3. The recommended front-end and back-end server architecture with advanced firewall configuration.
This configuration provides greater security and limits the front-end server's exposure to unwanted intruders. The firewall becomes the focal point for Denial of Service attacks and intrusion/penetration attacks rather than the front-end server. This scenario represents the recommended configuration for front-end and back-end server architecture. |
EAN: 2147483647
Pages: 130