An Example
The functionality required to communicate with a rootkit controller over a low-level TDI connection is implemented by creating two new files and modifying three existing files. In addition, this example requires a controller.
The new files are as follows:
commManager.c commManager.h Following are the modified files:
Ghost.c hookManager.c SOURCES The controller for the Ghost rootkit is aptly named GhostTracker.
GhostTracker is a multi-threaded C# application using the .NET framework’s TCPClient and TCPListener classes. Chapter 12 is devoted to this controller, but right now you don’t need to know how it works, you only need its functionality. If you have a C# build environment, feel free to skip ahead and build the GhostTracker project. Otherwise, just grab the supplied executable from the Chapter12 GhostTracker directory and use it as required.
At the time of this writing, you can go to http://msdn.microsoft.com/vstudio/express/visualcsharp/download to download and install C# Visual Studio. When you open the GhostTracker solution, you need to convert it into a 2005 Express C# solution, but after that you can compile and run normally.
Compiling GhostTracker yourself will ensure proper operation with your specific operating environment. In addition, you’ll be able to run in debug mode and add your own functionality to the project. Moreover, if you’ve been procrastinating learning C#, this would be a great way to jump in!
One more change will be required before running the example. When Ghost was configured in Chapter 2, an Internet address and a communication port were thrown into the file c:\config32. At that time “123.456.789.012:01234” was good enough to show how alternate data streams work, but for this chapter you will need to use the computer’s actual IP address. This can be found using the “ipconfig” command from a command prompt. You may have several adapters, some real and some virtual, but if you have only one network interface card (NIC), you should have only one named adapter with a valid IP address. This is the address you will need to put into c:\config32. GhostTracker is configured to use port 80 and the IP address of the machine it is running on, so adding “:00080” to your IP address is required. Once again, use the command “echo xxx.xxx.xxx.xxx:00080 > c:\config32”, but this time use your computer’s actual IP address. In addition, remember to use all three spaces for each section of the address and all five spaces for the port number; Ghost does not parse this information intelligently. The ipconfig command is shown in Figure 6-1.
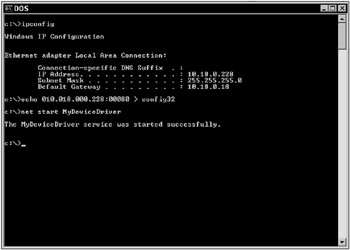
Figure 6-1
EAN: 2147483647
Pages: 229