VIRTUAL PRIVATE NETWORKS
What is a virtual private network (VPN)? As so often happens in the computer business, marketing hype can muddle an otherwise clear term. In the case of VPNs, some confusion exists over what's virtual in a VPN-the privacy or the network? Here's the two-part definition of a virtual private network:
-
VPN topology runs mostly over shared network infrastructure, usually the Internet, and has at least one private LAN segment at each end point.
-
VPN sessions run through an encrypted connection.
To operate through encrypted connections across the Internet, the network segments at each end of a site-to-site VPN must be under the administrative control of the enterprise (or enterprises) running the virtual network. In practical terms, this means that the endpoint routers must be under a common security and operational regimen. Above all, the endpoint routers in a VPN must operate a common encryption scheme.
Traditionally, long-distance connectivity to an internetwork relied on a WAN with a leased line. Furthermore, a leased line is simply not an option for an individual who is traveling and cannot be in one place long enough for a leased line to be justified. The following are some reasons why VPNs are making an impact on the leased-line market:
-
Lower costs Leased lines require expensive transport bandwidth and backbone equipment. In addition, VPNs don't need in-house terminal equipment and access modems.
-
Network agility Relatively speaking, VPN links are easy and inexpensive to set up, change, and remove. Because of this, an organization's communications infrastructure won't be traumatized when a VPN is installed, reconfigured, or removed. Furthermore, the availability of the Internet ensures that you can connect your VPN nearly anywhere.
-
Access Because of its availability, subscribers anywhere on the VPN have the same level of access and view of central services (like e-mail, internal and external Web sites, security, and so forth).
What Composes a VPN?
Think of VPNs as wide area networks that operate at least partly over insecure networks such as the Internet. Like most WANs, a VPN could provide a mixture of access types, as shown in Figure 7-16.
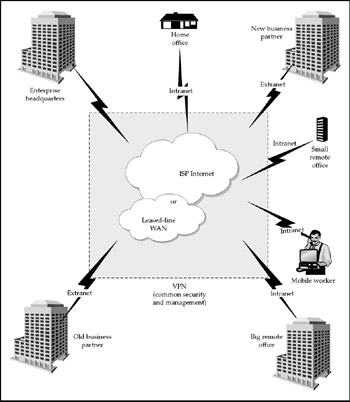
Figure 7-16: VPNs are encrypted WANs that come in variations
VPNs are steadily taking over the role of WANs in enterprise networking. All or part of a VPN can be an intranet, an extranet, or a remote access vehicle for telecommuters or mobile workers. A significant number of new VPNs are owned and operated by Internet service providers, who parcel out VPN bandwidth to enterprises. Outsourcing VPNs is becoming a standard practice for all but the largest enterprises, because it's less expensive and the enterprise can rely on the ISP to manage VPN infrastructure for them.
Encryption and other security measures largely define a VPN. This is for the simple reason that running enterprise WANs over the Internet is easy and inexpensive, but not feasible without appropriate security. Thus, security is part of what makes up a VPN. It is also defined by a suite of Internet-compatible access servers, network appliances (such as firewalls), and internetwork management techniques.
| Note | Encryption is a technique that scrambles the format of data in such a way that it can only be read by a system holding an authorized key with a mathematical formula needed to unscramble the payloads. (Packet headers are left unscrambled so that they can be routed.) In the context of our discussion in this section of the book, encryption and decryption take place between two peer encrypting routers, called peer routers. (Note that firewalls can also handle encryption.) Peer routers share a secret algorithm key used to unscramble the payload. Peer routers must authenticate each other before each encrypted session using Digital Signature Standard (DSS) keys (unique character strings). When a signature is verified, the peer router is authenticated and the encrypted session begins. The actual scrambling is done using a temporary Data Encryption Standard (DES) key, which must be exchanged in the connection messages between the peer routers. When the encrypted session is over, the DES key is discarded. |
The components making up a VPN are:
-
Tunneling Point-to-point connections over a connectionless IP network-in essence, a set of predetermined router hops taken through the Internet to guarantee performance and delivery.
-
Encryption The scrambling of an IP packet's contents (but usually not the header) to render it unreadable to all but those with a key to unscramble it. (Keys are held by authorized VPN senders and receivers only.)
-
Encapsulation Placing a frame inside an IP packet to bridge dissimilar networks (the IP packet is unpacked on the other side), effectively allowing tunneling to take place across otherwise incompatible VPN network segments.
-
Packet authentication The ability to ensure the integrity of a VPN packet by confirming that its contents (payload) weren't altered en route.
-
User authentication User authentication, authorization, and accounting (AAA) capabilities enforced through security servers, such as TACACS+, RADIUS, or Kerberos.
-
Access control Firewalls, intrusion detection devices, and security auditing procedures used to monitor all traffic crossing VPN security perimeters.
-
Quality of Service (QoS) Cisco's QoS is a set of internetwork management standards and functions to assure interoperability of devices and software platforms, and to leverage the platform to guarantee end-to-end network performance and reliability.
This list shows how a VPN is as much about seamlessness as security. Forcing network administrators or users to go through multiple steps to accomplish simple tasks would make using a VPN as infeasible as poor security. In practical terms, therefore, a VPN must be configured using hardware and software devices with these required characteristics.
Cisco's Solution
To deliver VPN functionality, Cisco has used a broad sword to make a name for itself. Rather than focus on just the hardware side of the issue, Cisco developed an integrated solution relying on both hardware and software.
The Cisco solution doesn't put all of its VPN eggs in one basket. In addition to routers and PIX firewalls enabled with VPN functions, they have software designed to make use of that extra functionality. The following sections take a closer look at Cisco's hardware and software, and how the two can be used together to deliver VPNs for remote access, intranets, and extranets.
Hardware
To deliver VPN functionality, Cisco has built VPN features into a number of its router models. For instance, the Cisco 1721 VPN Access Router is used to connect small remote sites to a VPN. The 1721 is packaged to perform high-speed encryption and deliver tunnel-routing services in a single package. VPNs have traditionally been softwarebased solutions. However, by building equipment with VPN functionality in mind, VPN services are improved over software solutions. For example, by adding VPN functionality to Cisco 2600 and 3600 series routers, VPN functionality is ten times greater than software solutions alone.
Some of Cisco's VPN-enabled hardware is listed in Table 7-4.
| Product | Description |
|---|---|
| Cisco VPN 3000 Concentrator Series | Remote-access, scalable, aimed at the enterprise level. Features up to 100-Mbps 3Des-encrypted throughput. |
| Cisco Secure PIX Firewalls | Built-in software encryption; up to 425 Mbps of encrypted throughput. |
| Cisco 800 Series Routers | For the SOHO market, up to 128-Kbps ISDN, broadband. |
| Cisco 1700 Series Routers | Small office market, up to T1/E1. |
| Cisco 2600 Series Router | For the branch office market, up to dual T1/E1. |
| Cisco 3600 Series Router | For the large branch office, scalable T1/E1 connectivity. |
| Cisco 3800 Series Router | For the large branch office, scalable T1/E1 connectivity. |
| Cisco ASA 5500 Series Adaptive Security Appliances | For medium-sized businesses, built to counter a host of security threats. |
Cisco VPN Client
Though Cisco is building VPN functionality into its hardware, they haven't forsaken the software end of the solution. Cisco's VPN solution can start at a piece of equipment that has no earthly connection to a piece of Cisco hardware. When Cisco Secure VPN Client version 4.8 is installed on a Windows-based PC, a telecommuter, remote office, or traveler can connect across any internetwork with its own VPN tunnel.
The client-which can be placed on a PC anywhere in the world-whose traffic traverses the Internet just like any other traffic, finds its way to its home router or PIX firewall.
Requirements The VPN client is available for Windows 9 x, NT, 2000, Millennium Edition, XP, 2003 Server, and Vista. The client also runs on Mac OS X, Linux, and Solaris.
Installation is a simple process of double-clicking an icon on the installation CDROM. Once the client is installed, it sits quietly in an icon at the bottom of the screen until it is needed.
Features Under the hood, Cisco's VPN client features a number of tools aimed at ensuring safe, stable IPSec tunneling. Some of the major features include
-
The network administrator can export and lock the security policy.
-
The client is IPSec-compliant. It also supports:
-
Tunnel Mode or Transport Mode security.
-
DES, 3DES, MD-5, and SHA-1 algorithms.
-
IKE using ISAKMP/Oakley Handshake and Key Agreement.
-
-
It's compatible with most Windows communications devices, including LAN adapters, modems, PCMCIA cards, and so on.
-
It's centrally configured for ease of use.
-
It's compatible with X.509 Certificate Authorities, including:
-
Windows 2000 Certificate Services.
-
Verisign Onsite.
-
Netscape Certificate Management System.
-
GUI to make security policy and certificate management user-friendly.
-
-
It's transparent when in use.
Digging a Tunnel
When a combination of Cisco's VPN-enabled hardware and software come together, that's when the strength of the Cisco VPN solution is evident. For instance, by using a Cisco Secure PIX 515E Firewall along with the PIX 7.2 software, the PIX can create and/or terminate VPN tunnels between two PIXs, between a PIX and any Cisco VPN-enabled router, and between a PIX and the Cisco Secure VPN Client.
The following scenarios explain how different VPN needs can be met.
Remote Access The most basic VPN comes when a user needs to access the network from a remote location. For instance, if a salesman is traveling and needs to access information on the company's network, he need only initiate a VPN back to the home office.
Let's look at how a remote access connection can be made. Figure 7-17 shows a pet food company's headquarters located in St. Paul, Minnesota, and a salesman, who is on a business trip in Boise, Idaho. To access his company's network, the remote user will be connected through a secure tunnel that is established through the Internet. This allows the salesman to access internal information as if his computer was physically connected to the corporate LAN.
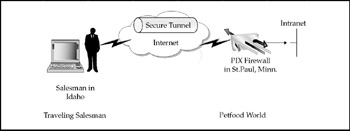
Figure 7-17: A remote user utilizes a VPN to access the corporate network
In Figure 7-18, we add the hardware elements that will make the VPN possible.
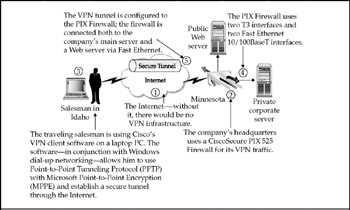
Figure 7-18: These are the hardware components of a remote access VPN connection
In this scenario, we used a PIX firewall as the VPN device on the company's end. This same scenario can be configured with a router in place of the PIX firewall. Using the same construction, one of Cisco's VPN-enabled routers could be used in place of the PIX.
Note: Refer back to Table 7-4 for a list of Cisco's VPN-enabled hardware.
Of course, your internetworking needs and your means will feature prominently in your decision between a PIX firewall and a router. For maximum security, you should use the firewall. A VPN-enabled router or concentrator provides much-increased performance over software-only VPN solutions.
This configuration works well for the "traveling salesman" scenario, but VPN functionality can also be established between two companies or a company and a branch office.
Site-to-Site Access Even in an environment where a WAN is the preferred mode of connectivity, a substantial cost savings can still be realized by employing a VPN. Site-to-site VPNs extend the classic WAN by replacing existing private networks utilizing leased lines, Frame Relay, or ATM to connect business partners and branch offices to the central site.
In this capacity, VPNs don't change the requirements of private WANs, such as support for multiple protocols, reliability, and extensibility. Rather, they meet these requirements, but are more cost-effective and flexible. To deliver private WAN-style capabilities on a budget, site-to-site VPNs can use the Internet or Internet service providers by utilizing tunneling and encryption for privacy, and, in some cases, Quality of Service for reliability. The following scenario shows how a VPN can be established between a company's headquarters and a remote office (intranet) or between two business partners (extranet).
In this example, let's show how two business partners can link their respective networks together across the Internet. Figure 7-19 shows the headquarters of HydroDynamics, which needs to provide network access to extranet partner, Johnson Pneumatics. The two offices are connected through a secure IPSec tunnel, which connects through the Internet. Employees at Johnson Pneumatics are able to access the Web server of their business partner across the country. Figure 7-20 shows the hardware and software details of the VPN link between HydroDynamics and Johnson Pneumatics.
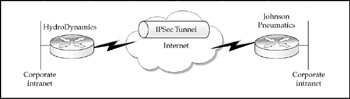
Figure 7-19: Business partners can use VPNs to link their organizations
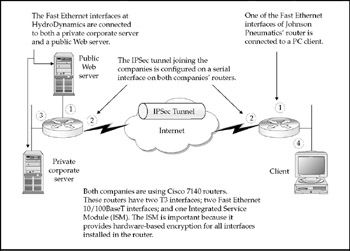
Figure 7-20: These are the hardware components of a site-to-site VPN solution
As you can see, connecting two business partners or a branch office through VPN is much easier and less expensive than a WAN. By safely and securely tunneling though the Internet, connectivity can be delivered without taking too much of a bite out of an organization's bottom line.
EAN: 2147483647
Pages: 102