STEP-BY-STEP ROUTER CONFIGURATION
A router can be configured by one of the following:
-
Entering changes directly to a router's running-config file
-
Downloading a new config file from a TFTP server
-
Setting up the config file from scratch
The best way to learn how to configure a router is to set one up from scratch. We'll step through setup mode here, not because the procedure is performed that often, but because it's an excellent way to review the fundamentals of router configuration.
Setup Mode
Setup is, essentially, an interactive script run to get the router up to a basic level of operation. If the device is new (and therefore has never been configured), or if the config file in NVRAM has been corrupted, the IOS software defaults into setup mode to rebuild the config file from scratch. Once that's accomplished, setup mode can be exited and the router rebooted in normal IOS mode, whereupon a complete config file can be built. Setup mode doesn't run by itself; a network administrator must be present to respond to setup's long sequence of questions about how to configure the router. Also, given that the router isn't configured, you cannot run setup through a network connection. Setup must be run through either the console or AUX port.
A router doesn't have to be new or corrupted to run setup. Setup can also be useful in non-emergency situations. Network administrators sometimes use setup when a config file has become so jumbled that it makes more sense to start anew-sort of like a blank sheet of paper. Used in this way, the parameter settings given as answers during a setup session overwrite the existing config file.
Setup mode is entered using the setup command. But before starting, hook your PC's COM port to the router's console port. Then start whatever terminal emulator software you prefer to use (remember, you'll be logged into the router's operating system, not your PC). The following instructions assume you're running on a Microsoft Windows PC. If you're not, you'll need to know how to start your terminal emulator. This shouldn't be a problem, because if you're running Apple, you're a survivor; if you're running X-Windows from a UNIX computer, you don't need our advice on such a trifling technical issue in the first place:
-
Click the Start button.
-
Select Programs | Accessories | Communications | HyperTerminal.
-
A HyperTerminal window will open, with a blinking cursor in the upper-left corner.
-
Enter the name of the connection you wish to make.
-
Select TCP/IP from the drop-down menu.
-
Enter the router's IP address and connection port.
-
Press ENTER, and you should be looking at the router's prompt.
-
Go into Privileged EXEC mode by entering enable and then the Enable Secret password ( setup is essentially a configuration command, and config files cannot be modified from the user EXEC level of IOS).
-
Type setup, and setup mode is started.
Once setup is started, a banner appears with command instructions, an option to quit, and an option to review a summary of the interface modules on the router.
The following code Router#set *Mar 3 04:58:46.167: %SYS-5-CONFIG_I: Configured from console by con- soleup ---System Configuration Dialog --- Continue with configuration dialog? [yes/no]: y At any point you may enter a question mark '?' for help. Use ctrl-c to abort configuration dialog at any prompt. Default settings are in square brackets '[]'. Basic management setup configures only enough connectivity for management of the system, extended setup will ask you to configure each interface on the system Would you like to enter basic management setup? [yes/no]: y Configuring global parameters: Enter host name [Router]:
If you decide to proceed, setup starts by configuring global parameters. This is basic information, such as giving the router a name and passwords. If it's a new router, or if the config file in NVRAM has been corrupted, you must enter new parameters for these things, as shown in the following:
Configuring global parameters: Enter host name [Router]: MyRouter The enable secret is a password used to protect access to privileged EXEC and configuration modes. This password, after entered, becomes encrypted in the configuration. Enter enable secret: test The enable password is used when you do not specify an enable secret password, with some older software versions, and some boot images. Enter enable password: test1
Looking at the following example, setup automatically detects interface modules physically present in the router's slots. It presents the available interfaces and asks which one we want to use to connect to the management network. In this case, we've chosen the Fast Ethernet connection.
Current interface summary Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset administratively down Serial0/0 unassigned YES unset administratively down Serial0/1 unassigned YES unset administratively down Enter interface name used to connect to the management network from the above interface summary: FastEthernet0/0 Configuring interface FastEthernet0/0: Use the 100 Base-TX (RJ-45) connector? [yes]: Operate in full-duplex mode? [no]: Configure IP on this interface? [no]:
Once this selection has been made, the router shows the completed command script. The following configuration command script was created:
hostname MyRouter enable secret 5 $1$gAi3$BXI873YTi..MOL0NIl5X11 enable password test1 line vty 0 4 password test2 no snmp-server ! no ip routing ! interface FastEthernet0/0 no shutdown media-type 100BaseX half-duplex no ip address no mop enabled ! interface Serial0/0 shutdown no ip address ! interface Serial0/1 shutdown no ip address ! end [0] Go to the IOS command prompt without saving this config. [1] Return back to the setup without saving this config. [2] Save this configuration to nvram and exit. Enter your selection [2]: 2
If you go ahead, setup then takes a few seconds to "build" the config file (as we said earlier, config files are not edited interactively, like a word processor file). Once the build is done, you're delivered to IOS in "normal mode" and advised that if you want to continue configuring, you must do so using the config command:
[OK]
Once the setup session is done, a basic configuration file has been created. From there, you would follow normal procedure and use the configure command to input a complete configuration file.
Giving a Router an Identity
Taking the time to name and document each router properly helps make networks easier to manage. Identifying information can be assigned by:
-
Giving the router a meaningful name
-
Individually documenting router interfaces
-
Putting a message of the day (MOTD) on the router
You will frequently see the example name "Router" used in configuration examples. Don't let that confuse you; "Router" is not a mandatory part of the Cisco IOS prompt. A router could just as easily be named "MainOffice" or "R23183" or anything else. Routers should be given meaningful names that inform network administrators where the router is and what it does. You must be in global configuration mode and use the hostname command to change the device name, as shown here:
Router(config)# hostname MyRouter MyRouter(config)#
Because the new name was input into the running-config file, the new router name MyRouter is used immediately in the next command prompt. However, unless you use the write or copy command to store the new name (or any other change) in NVRAM, if the router were rebooted, IOS would come back up using the old name.
| Note | The term "host" can confuse computer industry veterans new to internetworking. In the computer applications world, a host is a full-fledged computer system acting as a server, and network devices are nodes. In the internetworking context, host can mean any networked device, including routers, switches, and access servers, in addition to servers. We try to keep all this clear by referring only to computers as "hosts" and calling network equipment "devices"-but beware, the term "host" can take on different meanings in internetworking documents. |
A router interface can be specifically documented using the description command. Using descriptions is a great way to keep track of the network (and users) serviced by an interface. This may not sound like much, but big networks have thousands of interfaces, and they are reconfigured frequently. To enter an interface-specific description, you must first go to that interface-in this example, FastEthernet0/0:
MyRouter(config)#interface FastEthernet0/0 MyRouter(config-if)#
Then enter the description command followed by the description:
MyRouter(config-if)# description Fast Ethernet for finance department MyRouter(config-if)#
Descriptions can be up to 240 characters in length. To close the loop, the description can be seen in part of the config file for the interface:
MyRouter(config-if)# MyRouter# show running-config . . . interface FastEthernet0/0 description Fast Ethernet for finance department
Router names and interface descriptions are only seen by network administrators. A third router identification tool-the message-of-the-day banner-is a way to announce information to all terminals connected to a router. MOTD banners are a good way to make sure housekeeping announcements are seen by all users on the network. Banners are commonly used to warn against unauthorized use, announce scheduled system downtime, and make other types of announcements. Use the banner motd command to put a banner on a router:
MyRouter(config)# banner motd $MyRouter will be down tonight$
The dollar sign was arbitrarily chosen for use here as the delimiter marking the start and end of the banner message. Any character can be used; just make sure to use a character that will not appear in the banner text itself.
The banner will display whenever someone either logs directly into the router or hits the router from a Web browser:
MyRouter will be down tonight User Access Verification Password:
Fancy multiline banners can be built using extended mode commands for VT terminals. VT is a de facto standard for terminal programming from Digital Equipment Corporation (now part of Compaq Computer).
| Caution | Do not put any sensitive information in MOTD banners, because anybody can see them. In addition, there could be both security and legal implications if a "Welcome to …" message greets a hacker who is breaking into your network. |
Examining Device Status
Examining network interfaces is a basic technique for getting critical status information. The show interface command does this. Figure 4-7 shows example output.
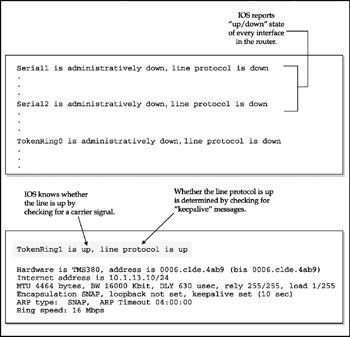
Figure 4-7: The show interface command reports current information
Keepalive messages are sent by interfaces to one another at the data link layer to confirm that the virtual circuit between them is still active.
Table 4-4 summarizes what the various status reports mean (using an interface named Ethernet1 as an example).
| Message | Meaning |
|---|---|
| Ethernet1 is up, line protocol is up | Running okay |
| Ethernet1 is up, line protocol is down | Interface okay, but no active connection |
| Ethernet1 is down, line protocol is down | Interface problem |
| Ethernet1 is administratively down, line protocol is down | Disabled |
Cisco Discovery Protocol
Cisco has a proprietary troubleshooting tool called the Cisco Discovery Protocol (CDP). It ships with all Cisco equipment, including routers. CDP is used by devices to discover and learn about one another. It is mediaand protocol-independent. Cisco devices use CDP as a way to advertise their existence to neighbors on a LAN or on the far side of a WAN connection. Think of CDP as a sort of "show configuration" command for a neighborhood of Cisco routers and other devices-a way for devices to tell anyone who will listen about their version (both software and hardware), host name, number, and type of interface information (IP address, duplex, VTP domain, VLAN power draw).
CDP runs at the data link layer in order to be compatible with devices running different network layer protocols (IPX, IP, AppleTalk, and so on). CDP can communicate with any physical media supporting the Subnetwork Access Protocol (SNAP), including LANs, Frame Relay, and ATM media. SNAP is a protocol designed to let devices pass messages within a subnetwork, allowing them to keep track of what's operating in the neighborhood.
CDP is automatic. You can connect any combination of Cisco devices, power them up, stand back, and let them automatically identify one another-even prior to being assigned network addresses. CDP is able to do this using a proprietary standard called the Cisco Proprietary Data-Link Protocol. Figure 4-8 shows how CDP spans otherwise incompatible protocols.
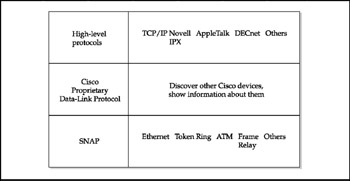
Figure 4-8: CDP bypasses incompatible protocols to keep track of networks
CDP is enabled by default in all Cisco devices. It works by having all Cisco devices in a directly connected network pass CDP frames to one another. The key to understanding
CDP's outer limit lies in the words "directly connected." CDP can discover devices beyond a LAN, but only as long as the WAN connection does not go through any nonCisco (and therefore non-CDP) devices to make the connection. CDP frames must be able to pass through internetwork connections in order to keep extending its map of what's connected to its home LAN.
Use the show CDP command to see what its current operating settings are.
MyRouter>show CDP Global CDP information: Sending CDP packets every 60 seconds Sending a holdtime value of 180 seconds
Asking for command-syntax help for the show CDP command displays the kind of information CDP can provide:
MyRouter>show CDP ? entry Information for specific neighbor entry interface CDP interface status and configuration neighbors CDP neighbor entries traffic CDP statistics <cr>
The most common usage of CDP is to show other devices directly connected to the device requesting the CDP information:
vsigate>show cdp neighbors Capability Codes: R - Router, T - Trans Bridge, B - Source Route Bridge, S - Switch, H - Host, I - IGMP, r - Repeater Device ID Local Intrfce Holdtme Capability Platform Port ID tacacsrouter Fas 0 168 R 3640 Fas 0 Switch.velte.com Eth 1 129 S WS-C2924M Fas 0/1 vsitest7 Fas 1 169 R RSP2 Fas 6/0
To look in greater detail at a specific neighbor, use the show cdp entry command:
vsigate>show cdp entry vsitest7 ------------------------- Device ID: vsitest7 Entry address(es): IP address: 10.1.12.2 Platform: Cisco RSP2, Capabilities: Router Interface: Ethernet1, Port ID (outgoing port): Ethernet6/0 Holdtime : 138 sec Version : Cisco IOS Software, 3600 Software (C3640-JK9O3S-M), Version 12.4(3b), RELEASE SOFTWARE (fc3) Technical Support: http://www.cisco.com/techsupport Copyright (c) 1986-2005 by Cisco Systems, Inc. Compiled Thu 08-Dec-05 22:10 by alnguyen
As you can see, CDP is able to gather fairly detailed configuration information on devices remotely. It was designed to be an efficient, low-overhead protocol so as not to gobble precious bandwidth and thereby render Cisco's entire product line slow. Because CDP is proprietary, it is able to gather a lot of information using a tiny amount of overhead. Other tools exist for discovering "locally connected" devices. The SNMP network management tools are great for centralized management, but gather lessgranular configuration information than CDP can on Cisco devices (SNMP is covered in Chapter 13).
EAN: 2147483647
Pages: 102