ESSENTIAL FILES
In contrast to normal computers, Cisco routers have just two main files:
-
The configuration file
-
The Cisco IOS software
Cisco IOS software contains instructions to the router. IOS acts as the traffic cop, directing activity inside the router. IOS manages internal router operations by telling the various hardware components what to do, much like Windows XP or LINUX with a general-purpose computer. Customers cannot alter the contents of the IOS file.
The configuration file contains instructions to the router input by the customer, not Cisco. It contains information describing the network environment in which the router will run and how the network manager wants it to behave. In a phrase, the configuration file tells it what to do; IOS tells the router how to do it.
As will be covered in the next chapter, routers also use dynamic files, which are not stored in the router's flash memory, NVRAM, or ROM. Dynamic files instead are built from scratch when a router is booted and are strictly reactive in the sense that they only hold live information, not operational instructions.
IOS:The Internetwork Operating System
We usually don't think of an operating system as a file. After all, your PC's operating system is made up of many thousands of files (they sit in your directory with file extensions such as SYS, EXE, DRV, and DLL).
However, IOS is indeed contained in a single file. When you ship an IOS file somewhere, it holds everything necessary to run a router. Depending on the version, an IOS software image will have a footprint from 3 MB to over 10 MB in size.
| Note | Less-sophisticated Cisco internetworking devices get their intelligence in the form of factoryinstalled software called firmware. Firmware is a subset of IOS itself. It can be field-upgraded to keep the device's software current with the rest of the network. |
IOS needs to be tightly constructed because copies of it, referred to as system images, are routinely shipped across internetworks. System images are uploaded and downloaded over routers in order to back up routers, upgrade their capabilities, and restart them after a failure. It wouldn't be practical to send thousands of 50-MB files. Being able to send a single, small, self-contained IOS file makes effective network management possible.
IOS Feature Sets
Feature sets are packages that try to simplify configuring and ordering IOS software. There is no single IOS software product, per se. IOS is actually a common software platform on which a suite of IOS implementations is based, each one packaged to fulfill a specific mission. Cisco calls these IOS packages feature sets (also called software images or feature packs). When you order a Cisco router, you choose an IOS feature set that contains all the capabilities your particular situation requires. Most of these requirements have to do with maintaining compatibility with the various hardware devices and network protocols in the environment in which the router will operate.
As depicted in Figure 3-17, variants of the Cisco IOS software are defined two ways: by feature set and by release. Feature sets define the job a version of IOS can do; releases are used to manage the IOS software through time.
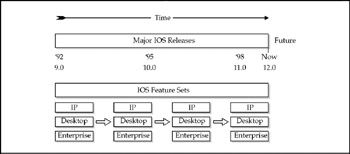
Figure 3-17: IOS is arranged by releases and feature sets
Cisco IOS feature sets are designed to:
-
Be compatible with certain router platforms
-
Enable interoperability between disparate networking protocols (Novell NetWare, IBM SNA, AppleTalk, and so on)
-
Provide functional features in the form of network services and applications for such things as network management, security, and multimedia
Packaging and selling IOS software in this way simplifies things for Cisco and customers alike. For the customer, having a single part number to order simplifies figuring out what software to buy. For Cisco, it helps the company's product engineers to figure out what goes where so that their support personnel figure out who has what. Remember, internetworking can get hopelessly complicated because the nature of the business is to enable disparate computer platforms and networking protocols to interoperate and coexist.
How Feature Sets Are Constructed Because IOS feature sets have dependencies on the router hardware on which they run, two rules of thumb apply:
-
You can't run all feature sets on all router platforms.
-
Sometimes, specific features within a feature set will or will not run, depending on the router platform.
If you look at a Cisco product catalog, understanding Cisco's feature sets can seem tough at first glance. Feature sets do nothing more than put functionality groupings into logical packages that customers can use. All feature sets, in one way or another, derive their functionality from about a dozen categories, listed in Table 3-8.
| Category | Examples of Features |
|---|---|
| LAN support | IP, Novell IPX, AppleTalk, Banyan VINES, DECnet |
| WAN services | PPP, ATM LAN emulation, Frame Relay, ISDN, X.25 |
| WAN optimization | Dial-on-demand, snapshot routing, traffic shaping |
| IP routing | BGP, RIP, IGRP, Enhanced IGRP, OSPF, IS-IS, NAT |
| Other routing | IPX RIP, AURP, NLSP |
| Multimedia and QoS | Generic traffic shaping, random early detection, RSVP |
| Management | SNMP, RMON, Cisco Call History MIB, Virtual Profiles |
| Security | Access lists, extended access lists, lock and key, TACACS+ |
| Switching | Fast-switched policy routing, AppleTalk Routing over ISL |
| IBM support | APPN, Bisync, Frame Relay for SNA, SDLC integration |
| Protocol translation | LAT, PPP, X.25 |
| Remote node | PPP, SLIP, MacIP, IP pooling, CSLIP, NetBEUI over PPP |
| Terminal services | LAT, Xremote, Telnet, X.25 PAD |
Don't worry about the examples on the right side of this table or all the acronyms you don't know. The important thing here is to understand that IOS software's myriad features and functions can be grouped into about a dozen categories.
Cisco IOS feature sets try to combine features into groups most likely to match realworld customer requirements. Cisco offers dozens of point-product feature sets in the form of IOS software product numbers you can put on a purchase order. They are grouped by general characteristics into the four general feature set families shown in Table 3-9. Notice in Tables 3-8 and 3-9 that proprietary computer platforms, such as IBM, DEC, and Apple, and proprietary networking platforms, such as Novell and SNA, drive much of the need for feature sets. Each Cisco router must deal with the customer's real-world compatibility requirements, which means being able to run with legacy hardware and software. Nearly all legacy architectures exist at the "network's edge"-which is to say most of the proprietary equipment with which IP must maintain compatibility sits either on LANs or on computers sitting on the LANs. This is where compatibility issues with proprietary legacy computer architectures or specialized platforms are manifested.
| Feature Set | Target Customer Environment |
|---|---|
| IP Base | Basic IP routing |
| IP Voice | IP voice routing |
| Enterprise Base | High-end functionality for LANs, WANs, and management |
| Advanced Security | Enhanced security features |
| Enterprise Services | Includes the features of the Enterprise Base, along with voice services, ATM, and MPLS support |
| Advanced IP Services | Includes the functionality of IP Base and Voice, along with ATM, MPLS, and security support |
| Advanced Enterprise Services | Same as Enterprise, but with additional security features |
Tables 3-8 and 3-9 also show which software functionality groupings go into what IOS feature set products. For example, multinational enterprises are likely to be interested in IBM functionality, such as NetBEUI over PPP and Frame Relay for SNA, and would probably be interested in one of the Enterprise/APPN feature sets. By contrast, an advertising agency heavy into Apple and Windows would focus on the Desktop feature sets.
Grouping feature sets into families is Cisco's way of bringing a semblance of order to pricing policies and upgrade paths. Ordering a single IOS part number instead of dozens helps everybody avoid mistakes. Figure 3-18 depicts the process of feature set selection.
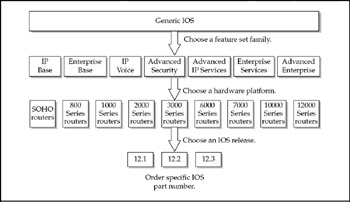
Figure 3-18: The process of configuring a specific IOS feature set involves selecting desired attributes
Last, feature sets are further grouped into software product variants:
-
Basic The basic feature set for the hardware platform
-
Plus The basic feature set and additional features, which are dependent on the hardware platform selected
-
Encryption The addition of either a 40-bit (Plus 40) or a 56-bit (Plus 56) data encryption feature atop either the Basic or Plus feature set
The ultimate goal of feature sets is to guide you through the process of ordering, say, IOS Feature Set Enterprise 56 for a Cisco 7500/RSP running Release 11-without making a mistake that costs your network upgrade project a two-week delay.
The Anatomy of Cisco Release Numbers Cisco IOS software release numbers have four basic parts, as shown in Figure 3-19.
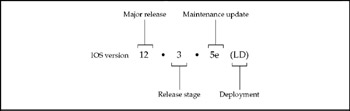
Figure 3-19: There are four major parts in an IOS release number
The first part is a major release-the "12" in Figure 3-19-which marks First Customer Shipments (FCS) of an IOS version of stable, high-quality software for customers to use in their production networks. Major releases are further defined by the following:
-
Stage The "3" in Figure 3-19, which marks FCS of various major release stages (first release, general deployment release, short-lived release, and so on). Stage releases are often referred to in the future tense, when they are still planned but have not yet taken place.
-
Maintenance Update The "5e" in Figure 3-19, which denotes support for additional platforms of features beyond what was available in the major release's FCS.
The fourth part of the release number is the deployment. A general deployment (GD) release is for unconstrained use by all customers. Early deployment (ED) releases are to deliver new functionality or technologies to customers to deploy in a limited manner in their networks. Limited deployment (LD) denotes a limited lifecycle between FCS and GD.
At any given time, there can be several major releases in use in the field. For example, five versions of IOS 12 are available, but 11.2 and 11.3 are still used. Most network managers are content to stick with a release they know works for them. Early adopters use advanced IOS releases because they need platform or feature support not available before. Most users are happy to let the early adopters help Cisco shake things out before general release.
| Note | The terms "version" and "release" are sometimes used interchangeably in connection with editions of IOS software. In this book, version is used to specify a particular release of a particular IOS feature set. |
Using TFTP for IOS Backups and Updates
In the event of a network catastrophe, it is possible for a router's IOS system image to be corrupted or erased from flash memory altogether. Standard procedure is to maintain a backup image of every IOS version in use in the network being managed. These backup IOS images are maintained on TFTP servers or within network management applications, such as CiscoWorks (covered in Chapter 13).
TFTP stands for Trivial File Transfer Protocol. TFTP is a TCP/IP application derived from the early days of the UNIX operating system. As you may have guessed, TFTP is a stripped-down version of FTP, the command many of you have used to download files over the Internet. IOS uses TFTP instead of FTP because it's speedier and uses fewer system resources.
So-called TFTP servers are computer platforms on an internetwork that store and download IOS system images and configuration files. It is recommended that more than one TFTP server be used to back up a network. This is in case the TFTP server itself goes down or the network segment connecting it to the devices it backs up becomes unavailable.
To load a new IOS image to a router's flash memory, use the copy tftp flash command following the procedure, shown here:
Router# copy tftp flash System flash directory: File Length Name/status 1 4171336 c4500-j-mz_112-15a.bin [4171400 bytes used, 22904 available, 4194304 total] Address or name of remote host [10.1.10.40]? 10.1.10.40 Source file name? c4500-j-mz_112-15a.bin Destination file name [c4500-j-mz_112-15a.bin]? <cr> Accessing file 'c4500-j-mz_112-15a.bin' on 10.1.10.40... Loading c4500-j-mz_112-15a.bin from 10.1.1.12 (via TokenRing1): [OK] Erase flash device before writing? [confirm]yes Flash contains files. Are you sure you want to erase? [confirm]yes Copy 'c4500-j-mz_112-15a.bin' from server as 'c4500-j-mz_112-15a.bin' into Flash WITH erase? [yes/no]yes Erasing device... eeeeeeeeeeeeeeee ...erased Loading c4500-j-mz_112-15a.bin from 10.1.1.12 (via TokenRing1): ! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! !!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! [OK 4171336/4194304 bytes] Verifying checksum... OK (0x29D5) Flash copy took 00:00:30 [hh:mm:ss] Router#
You can see that the TFTP server confirmed that it had the IOS system image before overwriting the one in the router's flash memory. Each exclamation point in the display indicates that a block of the file was successfully copied over the network from the server to the router.
| Note | If you are copying a file to a TFTP server, be sure the name of the file that you are attempting to transfer already exists in the TFTP directory. Create the file on UNIX systems using the touch command. On Microsoft platforms, open Notepad to create the file and save it under the file name. |
The Configuration File
Managing a router involves installation, upgrades, backups, recovery, and other eventdriven tasks, but the biggest part of router management is the care and feeding of a router's configuration file. The configuration file is the cockpit from which the network administrator runs the router and all the traffic going through it. As will be detailed in the next chapter, configuration files contain access lists, passwords, and other important router management tools.
Viewing the Configuration File
The most common way to examine the status of a router is to view its configuration file. To view most anything in IOS is to ask for a view of the configuration. The main IOS command for viewing such information is the show command.
The following example uses the show running-config command to view a router's running configuration. There are two types of configuration files. The running configuration file is an image running in DRAM (main memory) at a given time. The backup configuration file is stored in NVRAM and is used to boot the router.
Router# show running-config Building configuration... Current configuration: ! version 12 service password-encryption service udp-small-servers service tcp-small-servers ! hostname Router ! enable secret 5 $1$C/q2$ZhtujqzQIuJrRGqFwdwn71 enable password 7 0012000F ! vty-async ! interface Serial0 no ip address no ip route-cache no ip mroute-cache shutdown ! interface Serial1 no ip address . . .
In the next chapter, we will go into greater depth on what the configuration file does and how to edit it.
Using TFTP for Configuration File Backups and Updates
As with IOS system image backups and updates, TFTP servers are used to back up and update configuration files. For example, the copy running-config tftp command is used to back up the router's running configuration file (named tomtest in this example) to a TFTP server, using the following procedure:
Router# copy running-config tftp Remote host []? 10.1.10.40 Name of configuration file to write [router-config]? test Write file tomtest on host 10.1.10.40? [confirm]<cr> Building configuration... Writing test !! [OK] Router#
The other TFTP commands to back up or update configuration files are:
-
copy tftp running-config Configures the router directly by copying from the TFTP directly into the router's DRAM
-
copy startup-config tftp Backs up the startup configuration from the router's NVRAM to the TFTP server
-
copy tftp startup-config Updates the router's startup configuration file by downloading from the TFTP server and overwriting the one stored in the router's NVRAM
Note that tftp goes in front of the file type-running-config or startup-config-to download (update from the server) and behind the file type to upload (back up to the server). Think of the copy command as copying from somewhere to somewhere.
EAN: 2147483647
Pages: 102