See
A program associated with the UNIX operating system that runs in the background and performs some task without instigation from the user. An example of a daemon is the telnet daemon, which runs continuously in the background, waiting for a connection request from a telnet client. The telnet daemon facilitates the remote connection and makes it possible for the user to control the machine. Another example is the HTTPd daemon for the Apache Web server, which waits for Hypertext Transfer Protocol (HTTP) requests from Web browser clients and fulfills them.
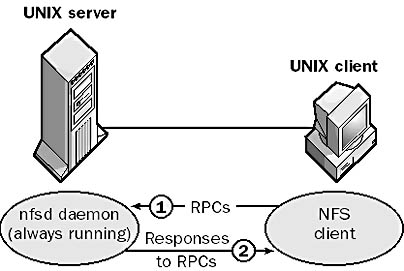
A third example of a daemon is the nfsd daemon, which supports the remote file access aspect of the Network File System (NFS) in a UNIX environment. The nfsd daemon runs in the background on UNIX servers, waiting for remote procedure calls (RPCs) from NFS clients.
Daemons typically use RPCs for communication with clients. Because NFS is implemented as daemon processes at the user level instead of at the kernel level, NFS is thread-safe for execution, allowing multiple NFS processes to run as independent threads of execution.
NOTE
The Microsoft equivalent of “daemon” is “service.” For example, the Workstation service of Microsoft Windows NT would be known in UNIX as a daemon instead of a service.

Graphic D-1. The nfsd daemon.
A backup type in which only files and folders that have changed on that day are backed up but the archive attribute is not marked for each file and folder. A daily copy backup is not a common type of backup operation. It is typically used only if a user wants to take home copies of the files he or she has been working on during the day. Few administrators would be willing to schedule and run the system backup software just to make copies of these files, so users taking advantage of this backup type usually have a locally attached backup device along with a similar device attached to their systems at home. Daily copy backups are likely to be performed on media such as Iomega Zip or Jaz disks rather than on tape.
NOTE
Daily copy backups are supported by the Microsoft Windows NT and Windows 2000 Backup utility.
See also backup, backup type
See Digital Advanced Mobile Phone Service (D-AMPS)
See Data Access Objects (DAO)
See Directory Access Protocol (DAP)
Any fiber-optic cabling or fiber device such as a repeater that is installed but not currently in use. Since no light is being transmitted through the cabling, it is called “dark.” The term “dark fiber” is not generally used to refer to a problem in the fiber-optic cabling system; it simply means that the fiber media and components are waiting to be used.
However, various problems can occur in a fiber-optic cabling system that can cause it to remain dark once the system is turned on. These can include the following:
Microfractures in the glass core or cladding caused by improper installation techniques, such as excessive bending or stretching of a segment of cable
Improper terminations for the fiber or loose connectors
Malfunctioning repeaters
Before dark fiber is activated, the system is usually tested using an optical time domain reflectometer (which measures and analyzes a fiber link) and other measuring devices to determine whether the system has integrity, and to measure its bandwidth and attenuation parameters.
See also fiber-optic cabling
A Microsoft technology that enables you to use a programming language to access and manipulate data stored in both local and remote databases. Data Access Objects (DAO) lets you access and manage databases, along with their structure and objects, by providing a framework called an “object model” that uses code to create and manipulate different kinds of databases.
DAO supports two different interfaces, which are known as workspaces:
The ODBCDirect workspace, in which you can access database servers such as Microsoft SQL Server through open database connectivity (ODBC). This workspace lets you execute queries or stored procedures against a database server, perform batch updates, and execute asynchronous queries. ODBCDirect makes it possible for you to take advantage of Remote Data Objects (RDO) technology in your DAO code.
The Microsoft Jet workspace, in which you can access databases based on Jet technology or on installable indexed sequential access method (ISAM) data sources in other formats such as Paradox, dBase, and Btrieve. You use this workspace to access a single database, such as a .mdb database from Microsoft Access, or to join together data originating from several different database formats.
DAO and RDO are both available now, but these technologies are being superseded by Microsoft ActiveX Data Objects (ADO) and Remote Data Service (RDS). All these components can be found in the Microsoft Data Access Software Development Kit.
A device for alerting network administrators to network problems. Some vendors use the term “data alarm” to describe a device that senses network problems associated with the flow of data.
These devices typically monitor serial lines such as RS-232 connections for the presence or absence of certain signals. For example, you can monitor the connection between a print server and its attached printer or between an access server and a modem or a Channel Service Unit/Data Service Unit (CSU/DSU).
A data alarm can be a simple device that monitors one serial line for the presence or absence of data. If the data flow stops, a flashing LED or audible alarm signals the problem to the administrator. More complex data alarms can support multiple serial lines or other serial interfaces such as RS-449 and V.35, can have programmable functions and menu-driven commands, and can monitor other devices, such as Time to Live (TTL) devices. These more complex devices can be configured to dial a remote station when a problem arises and to generate a report of the condition or even activate an alphanumeric pager.
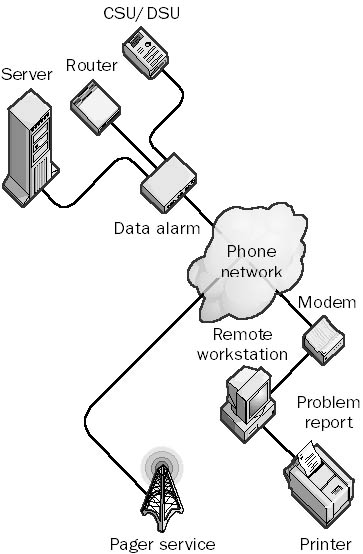
Graphic D-2. Data alarm.
A file used to store records of information, with each record containing multiple data fields. The most popular type of database is the relational database, in which the records are stored in tables that are related to each other using primary and foreign keys. A primary key is the field in each record that uniquely defines the record. (For example, a part number might be used as the primary key in a table that holds the price of each item a company sells.) A foreign key is a field in another table that matches the first table’s primary key, creating a relationship between the two. An application for creating and managing relational databases is called a relational database management system (RDBMS).
How It Works
Records are like the rows of a table. Each record is a collection of information about some physical system or logical object. Field names are like the column names of a table. Each field name represents a property or attribute of the system or object. Databases are widely used by businesses for storing information about inventory, orders, shipping, accounting, and so forth.
Microsoft SQL Server is Microsoft’s enterprise-level RDBMS. SQL Server databases are stored on devices. Each computer running SQL Server has four system databases plus one or more user databases installed on it. The system databases are as follows:
The master database, which is used for tracking system-wide information.
The tempdb database, which is used for temporary working storage and sort operations.
The model database, which is a template for creating new databases.
The msdb database, which is used to store system data and transaction logs and to support the SQL Server Agent service and its scheduling information. The msdb database is stored on two devices, the Msdbdata system device and the Msdblog system device.
NOTE
The term “database” can have different meanings for different vendors. In Oracle products, for example, “database” refers to the entire Oracle DBMS environment. In SQL Server, databases provide a logical separation of data, applications, and security mechanisms, while in Oracle this separation is achieved using “tablespaces.”
A wizard included with Microsoft SQL Server version 6.0 and later that lets you configure and schedule core maintenance actions for databases. You can schedule actions such as
Backups of databases and their transaction logs
Updates of optimizer information
Checks for damaged data
Redistribution of data and free space to make the database more efficient
You can use the wizard to schedule maintenance tasks at daily or weekly intervals. You run the Database Maintenance Plan Wizard from the toolbar of the SQL Server Enterprise Manager administrative tool. You can delete or disable scheduled maintenance tasks if they are no longer required.
See Systems Management Server Database Manager
In Microsoft SQL Server, the user account that created the database and is responsible for managing administrative tasks related to a SQL Server database. Each SQL Server database is considered a self-contained administrative domain and is assigned a database owner (DBO) who is responsible for managing the permissions for the database and performing tasks such as backing up and restoring the database’s information.
Essentially, the DBO can do anything within the database. By default, the SA (system administrator) account is also a DBO account for any database on a computer running SQL Server. The database owner has full permissions inside a database that it owns.
TIP
To avoid the complexity of managing separate DBO accounts for each SQL Server database, you might want to perform all administration tasks—both server-wide and specific to the database—using only the SA account.
Any device that supports data transmission over a serial telecommunications link. Typically, data communications equipment (DCE) refers to modems, Channel Service Unit/Data Service Units (CSU/DSUs), multiplexers, and similar devices. The purpose of a DCE is to provide termination for the telecommunications link and an interface for connecting data terminal equipment (DTE) to the link.
The term “DCE” specifically refers to serial transmission, which generally occurs over links such as a local loop Plain Old Telephone Service (POTS) connection, an Integrated Services Digital Network (ISDN) line, or a T1 line. An example of a DCE is an analog modem, which provides a connection between a computer (the DTE) and the local loop POTS phone line (the serial transmission line). A DCE accepts a stream of serial data from a DTE and converts it to a form that is suitable for the particular transmission line medium being used. The DCE also works in reverse, converting data from the transmission line to a form the DTE can use.
A U.S. government standard for encrypting information. In 1972, the National Bureau of Standards called for proposals for an encryption standard. IBM responded with an algorithm called Lucifer, which was accepted, renamed Data Encryption Algorithm (DEA), and then further developed by the National Security Agency (NSA) and the National Bureau of Standards. In 1977, DEA was adopted as the Data Encryption Standard (DES). It is now the official encryption standard of the Department of Defense. DES is the name of the Federal Information Processing Standard FIPS 46-1, which explains the operation of the Data Encryption Algorithm.
How It Works
DES is a symmetric encryption scheme in which both the sender and the receiver need to know the secret key in order to communicate securely. DES is based on a 56-bit key (actually a 64-bit key with 8 parity bits stripped off) that allows for approximately 7.2 x 1016 possible keys. When a message is to be encrypted using DES, one of the available keys is chosen and applied in 16 rounds of permutations and substitutions to each 64-bit block of data in the message.
The large number of keys makes DES fairly secure, but in 1997 a DES key was cracked using the idle processing cycles of 14,000 computers cooperating over the Internet.
A more secure variant of DES, Triple DES, encrypts each message using three different 56-bit keys in succession. Triple DES thus extends the DES key to 168 bits in length.
NOTE
The U.S. government controls the export of encryption standards and technology. A new encryption standard called Advanced Encryption Standard (AES) is expected to replace DES soon because DES is no longer considered secure enough for some government purposes.
A term sometimes used as a synonym for “packet,” but most often meaning a packet that is sent across a network using connectionless services, where the delivery doesn’t depend on the maintenance of specific connections between computers. Networking protocol suites such as TCP/IP generally support both connection-oriented and connectionless delivery services. In TCP/IP, the Transmission Control Protocol (TCP) is responsible for providing connection-oriented services that guarantee delivery of Internet Protocol (IP) packets. In contrast, the User Datagram Protocol (UDP) handles connectionless services that guarantee only “best-effort” delivery of datagrams. For networking services that use connectionless datagrams, higher-layer protocols must ensure delivery. Datagrams are generally small packets sent over the network to perform functions such as announcements.
The correctness and consistency of data stored in a database. Maintaining integrity is essential, because a database is only useful if its contents can be retrieved and manipulated as expected. For example, without data integrity, data could be input into the system and then be inaccessible. Data integrity must be enforced on the database server. The following items are among those that should be verified:
Individual field contents during insertion, updating, or deletion of data
The values of one field relative to another (especially for primary keys) and of data in one table relative to another (especially for foreign keys)
Successful completion of database transactions
Database systems employ many features to ensure data integrity. For example, Microsoft SQL Server 7 makes use of data types, constraints, rules, defaults, declarative referential integrity (DRI), stored procedures, and triggers. All these play a role in keeping the integrity of the database intact.
A general term for a type of network device that protects serial equipment from voltage surges. If two pieces of data terminal equipment (DTE) are connected by a long serial line, voltage differences with respect to ground between the devices can cause surges over the line that can damage the devices. This can be a problem in a mainframe environment when you connect terminals to asynchronous mainframe hosts using long RS-232 cables. The problem is especially troublesome when the cabling has to run outdoors between buildings or when nearby generators or other equipment induce voltages.
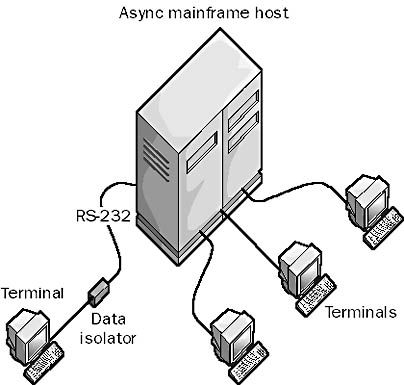
Graphic D-3. Data isolator.
The solution to these problems is to insert a data isolator between the mainframe host and the terminal. This isolator provides electrical isolation between the two devices, somewhat like an opto isolator for fiber-optic cabling. Data isolators typically use transformers to electrically isolate the two connected circuits from voltage surges. Data isolators can support high data transfer speeds, and they come with a variety of interfaces, such as RS-232, RS-422, and Time to Live (TTL) connections.
A device that provides surge protection for network cables carrying data. Data line protectors prevent voltage spikes and surges from damaging costly hubs, switches, routers, and other devices. They are essentially surge protectors that are placed inline between stations on the network and concentrating hubs or other devices in the wiring closet. Data line protectors are available from different vendors for virtually every kind of networking connection, including RJ-45 connections for Ethernet networks, RJ-11 connections for telephone lines, and RS-232 connections for serial lines.
You connect a data line protector directly to one of the two connected devices, and then you attach the ground wire to a good ground connection so that there will be a path for voltage surges to flow down. For Ethernet networks using unshielded twisted-pair (UTP) cabling, data line protectors are available with multiple ports that are attached directly to the hub or the switch. Additional 10BaseT surge protectors can also be installed directly on the stations on the network for more protection.
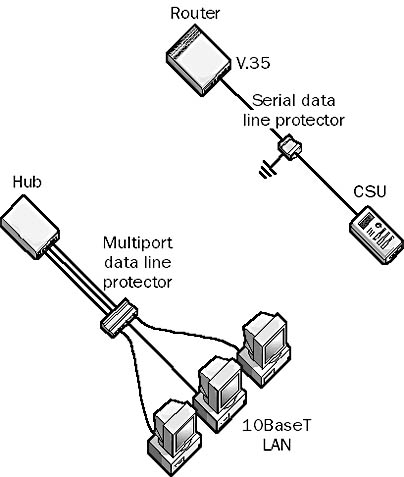
Graphic D-4. Data line protector.
NOTE
Most newer hubs, switches, routers, and other networking devices include built-in data line protection circuitry, which eliminates the need for additional data line protectors.
Generally, the services that the data-link layer of the Open Systems Interconnection (OSI) reference model provides to adjacent layers of the OSI protocol stack. Specifically, a Data Link Control (DLC) is a specialized network protocol that is used primarily for two purposes:
To provide connectivity with IBM mainframe or AS/400 environments, such as Systems Network Architecture (SNA), which are configured to run DLC. DLC complements SNA because SNA operates only at higher levels of the OSI model.
To provide connectivity for network print devices (such as certain Hewlett Packard printers that have their own network cards and are connected directly to the network).
DLC is not used as a network protocol in the usual sense of enabling communication among computers on the network. It is not used by the redirector in the Microsoft Windows NT and Windows 2000 operating systems and so cannot be used for session-level communication over a network. DLC is not routable; it is designed only to give devices direct access to the data-link layer. DLC is supported by most Windows operating systems, including Windows 95, Windows 98, Windows NT, and Windows 2000. Windows 95 OSR2 includes both a 16-bit and a 32-bit version of DLC.
TIP
To use DLC on Windows NT or Windows 2000 to connect to a Hewlett-Packard network print device, perform the following steps:
Connect the printer to the network, and run the self-test routine to obtain the MAC address of the printer. Also think of a friendly name for the printer.
Install the DLC protocol on the Windows NT or Windows 2000 server that will be used as a print server for the network print device. (Use the Network utility or the Windows 2000 Network and Dial-up Connections utility in Control Panel.)
Run the Add Printer Wizard on the print server, choosing My Computer, Add Port, Hewlett Packard Network Port, and New Port. Enter the friendly name for the printer and select its MAC address from the list (or type it if the print device is offline). In Windows 2000, run the Add Printer Wizard, then right-click on the printer in the Printers folder and choose Properties. In the Property sheet for the printer, click the Ports tab, click Add Port, select Hewlett Packard Network Port, and then click New Port. Enter the friendly name for the printer and select its MAC address from the list (or type it if the print device is offline).
Layer 2 of the Open Systems Interconnection (OSI) reference model, which converts frames of data into raw bits for the physical layer and is responsible for framing, flow control, error correction, and retransmission of frames. MAC addresses are used at this layer, and bridges and network interface cards (NICs) operate at this layer.
The data-link layer establishes and maintains the data link for the network layer above it. It ensures that data is transferred reliably between two stations on the network. A number of protocols can be implemented at this layer depending on whether you are establishing local area network (LAN) or wide area network (WAN) connections between stations. Data-link protocols are responsible for functions such as addressing, frame delimiting and sequencing, error detection and recovery, and flow control.
For LANs, the Project 802 standards of the Institute of Electrical and Electronics Engineers (IEEE) separate the data-link layer into two sublayers:
The logical link control (LLC) layer, the upper of the two layers, which is responsible for flow control, error correction, and resequencing functions for connection-oriented communication, but which also supports connectionless communication
The media access control (MAC) layer, the lower of the two layers, which is responsible for providing a method for stations to gain access to the medium
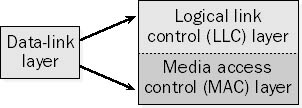
Graphic D-5. Data-link layer.
Examples of data-link protocols for local area networking include the following:
IEEE 802.3, which provides the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) access method for baseband Ethernet networks
IEEE 802.5, which provides the token-passing access method for baseband token ring implementations
For WANs, data-link layer protocols encapsulate LAN traffic into frames suitable for transmission over WAN links. Common data-link encapsulation methods for WAN transmission include the following:
Point-to-point technologies such as Point-to-Point Protocol (PPP) and High-level Data Link Control (HDLC) protocol
Multipoint technologies such as frame relay, Asynchronous Transfer Mode (ATM), Switched Multimegabit Data Services (SMDS), and X.25
A tool that simplifies data access to different kinds of data sources such as relational databases. Also known as the OLE DB Provider for AS/400 and VSAM, Data Provider is included with Microsoft SNA Server version 4. It gives Web applications written with Microsoft Active Server Pages (ASP) technology the ability to access record-level mainframe AS/400 and VSAM file systems.
Using Data Provider, you can write applications that access legacy file data on mainframes and minicomputers running Systems Network Architecture (SNA). You can also directly access AS/400 file structures and VSAM data sets using the IBM DDM protocol native to many IBM host systems without needing to install additional Microsoft software on the host system. You can also integrate unstructured legacy file data on host systems with data stored in a Microsoft Windows NT or Windows 2000 networking environment.
A digital communication device that works with a Channel Service Unit (CSU) to connect a local area network (LAN) to an external communication carrier service or a wide area network (WAN) link (such as a T1 line). Data Service Units (DSUs) provide a modem-like interface between data terminal equipment (DTE) such as a router and the CSU connected to the digital service line. DSUs also serve to electrically isolate the telco’s digital telecommunication line from the networking equipment at the customer premises.
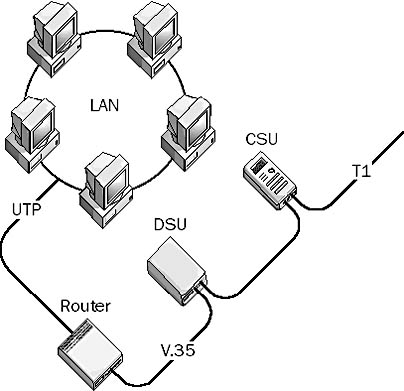
Graphic D-6. Data Service Unit (DSU).
For example, in T1 transmission technologies, the DSU converts network data frames that are received from the router’s RS-232, RS-449, or V.35 serial transmission interface into the standard DSX framing format, encoding scheme, and voltages of the T1 line. The DSU also converts the unipolar networking signal into a bipolar signal suitable for transmission over the digital line. The DSU is also responsible for handling signal regeneration and for controlling timing errors for transmission over the T1 line. DSUs usually provide other functions such as line conditioning of the T1 line, as well as remote diagnostic capabilities such as Simple Network Management Protocol (SNMP), which allows the telco central office (CO) to monitor the state of the line at the customer premises.
NOTE
DSUs are usually integrated with CSUs to create a single device called a CSU/DSU (Channel Service Unit/Data Service Unit). If these devices are separate, the telco usually supplies and configures the CSU, while the customer supplies the DSU. If the devices are combined, the telco usually supplies, configures, and maintains the CSU/DSU for the customer premises.
TIP
The DSUs (or CSU/DSUs) at either end of a digital data transmission line should be from the same manufacturer. If they are not, they might not communicate with each other correctly because different vendors employ different multiplexing and diagnostic technologies that are often incompatible with those of other vendors.
See also Channel Service Unit/Data Service Unit (CSU/DSU)
A unique name used to create a data connection to a database using open database connectivity (ODBC). The data source name (DSN) is used by applications that need to access or manage data in the database. All ODBC connections require that a DSN be configured to support the connection. When a client application wants to access an ODBC-compliant database, it references the database using the DSN.
Graphic D-7. Data source name (DSN).
You can configure a DSN for an ODBC-compliant database using the Microsoft Windows NT ODBC or the Windows 2000 Administrative Tools\Data Sources (ODBC) utility in Control Panel. You can create three kinds of DSNs:
A user DSN, which is visible only to the user who creates it and can be used only on the current machine.
A system DSN, which is visible to all users on the machine and is also accessible to Windows NT and Windows 2000 services. A system DSN is stored in the registry.
A file DSN, which can be shared by users who have the same ODBC drivers installed. A file DSN is stored in a file.
TIP
When you design Web applications that use Microsoft ActiveX Data Objects (ADO) for accessing database information, be sure to use either a file DSN or a system DSN because ADO does not work with user DSNs.
A type of networking device that you can use to monitor the flow of data in serial lines. Data taps provide an easy way to connect monitoring equipment such as data scopes to serial interfaces such as RS-232.
These serial connections are used for a variety of networking purposes, including connecting data terminal equipment (DTE) such as servers and routers to data communications equipment (DCE) such as modems and CSU/DSUs (Channel Service Unit/Data Service Units) for implementing wide area networks (WANs); connecting dumb terminals to asynchronous mainframe hosts; and connecting servers to plotters and other serial devices. Data taps generally display network traffic in binary, hexadecimal, or character format and are used for troubleshooting various kinds of network connections.
A data tap is essentially a three-way connector in which the third connector interfaces with the test equipment. For RS-232 serial lines, data taps come in a variety of configurations, with mixtures of male and female DB-9 and DB-25 connectors.
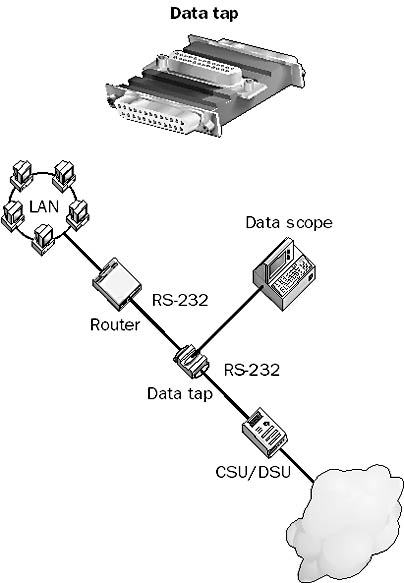
Graphic D-8. Data tap.
Any device that is a source of data transmission over a serial telecommunications link. Typically, data terminal equipment (DTE) can be a computer, a terminal, a router, an access server, or some similar device. The earliest form of DTE was the teletype machine.
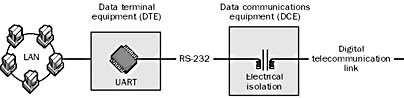
Graphic D-9. Data terminal equipment (DTE).
The term “DTE” specifically refers to a device that uses serial transmission such as the transmissions involving the serial port of a computer. Most serial interface devices contain a chip called a universal asynchronous receiver-transmitter (UART) that can translate the synchronous parallel data transmission that occurs within the computer’s system bus into an asynchronous serial transmission for communication through the serial port. The UART also performs other functions in a DTE:
Error detection, to ensure that data arrives at its destination uncorrupted
Clocking, to ensure that data is sent at the correct rate in order to be received at its destination
To connect a DTE to a telecommunications link, you use data communications equipment (DCE). The DCE provides termination for the telecommunications link and an interface for connecting the DTE to the link. An example of a DCE for connecting a DTE to the local loop Plain Old Telephone Service (POTS) connection is a modem.
See also data communications equipment (DCE)
See Digital Advanced Wireless System (DAWS)
Any connector used for connecting data terminal equipment (DTE). The letters “DB” stand for “data bus” and are followed by a number that indicates the number of lines or pins in the connector. DB connectors were formerly called D-series connectors. DB connectors can be used for either serial or parallel connections between devices. Common members of the DB family include the following:
DB-9, a 9-pin serial connector for connecting modems, serial printers, mouse devices, and so on
DB-15, a 15-pin connector for connecting such devices as Macintosh monitors and network interface cards (NICs) for 10Base5 drop cables
DB-25, a 25-pin connector for connecting Macintosh Small Computer System Interface (SCSI) devices, modems, serial printers, parallel cables, switch boxes, and so on
DB-37, a 37-pin connector for connecting such devices as routers and Channel Service Units (CSUs)
DB-60, a 60-pin connector for connecting such devices as Cisco routers
See also connector (device)
See database owner (DBO)
See data communications equipment (DCE)
A circuit-switched channel in Integrated Services Digital Network (ISDN) technologies that carries signaling information between the customer premises termination and the central office (CO) of the telecommunications service provider or telco. The letter “D” stands for “data” or “delta.”
How It Works
The D channel is used to signal the telco CO when connections need to be created or terminated. The D channel forms the “D” part of a 2B+D Basic Rate Interface ISDN (BRI-ISDN) line and carries signaling information at a rate of 16 Kbps. On a 23B+D Primary Rate Interface ISDN (PRI-ISDN) line, the D channel carries signaling information at the faster rate of 64 Kbps.
D channel communication uses a completely separate out-of-band communication network called the Signaling System 7 (SS7) network, as shown in the illustration. This telco network is dedicated solely to servicing system functions that are overhead as far as voice or data communication is concerned. The SS7 network on which D channel communication takes place makes possible the low latency of dial-up ISDN connections, which are typically 1 or 2 seconds (compared to a latency of 15 to 30 seconds for analog phone connections).
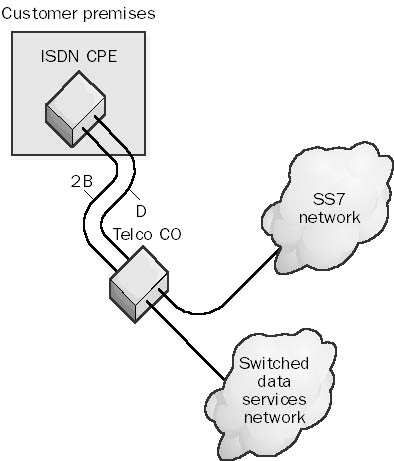
Graphic D-10. D channel.
NOTE
In ISDN voice communication, D channels are also used to activate special calling features such as line call forwarding and caller ID.
See also B channel, Integrated Services Digital Network (ISDN)
See Distributed Component Object Model (DCOM)
A Microsoft Windows NT, Windows 98, and Windows 2000 utility used to configure 32-bit Windows applications for Distributed Component Object Model (DCOM) communication between components of distributed applications on a network.
How It Works
You can use the DCOM Configuration Tool to configure DCOM applications to run across computers on a network. Computers can be configured to operate as DCOM clients (making calls to DCOM servers), DCOM servers, or both. Using this tool, you can configure the locations of components of distributed applications and the security settings for those components.
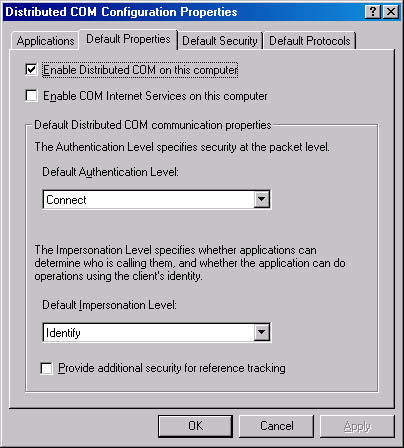
Graphic D-11. DCOM Configuration Tool.
To use the tool to configure a distributed application, you must specify the security and location properties of both the calling client application and the responding server application. For the client application, you specify the location of the server application that will be called by the client. For the server application, you select a user account that will have permission to start the application and the user accounts that will run it.
NOTE
Before you can use the DCOM Configuration Tool on Windows 98, you must be sure that user-level security is being used.
TIP
To start the tool, choose Run from the Start menu, and then type dcomcnfg.
See also Distributed Component Object Model (DCOM)
See digital data service (DDS)
In wireless networking, a location within the coverage area where a signal is not received. Dead spots are typically caused by physical barriers (such as buildings or concrete structures) that absorb or reflect radio or microwave frequencies. The receiving station must relocate or the barrier must be moved if the station is to receive a signal. Dead spots can also be caused by high levels of electromagnetic interference (EMI) from heavy machinery (such as motors and generators) or broad-spectrum sources of radiation (such as microwave ovens). In these cases, too, the solution is to relocate the receiver or eliminate the source of interference.
See also wireless networking
A mathematical way of representing power ratios, such as signal loss within a circuit or a portion of a network’s cabling system. A decibel is the ratio of two values that measure signal strength, such as voltage, current, or power. This ratio is expressed logarithmically using base 10 logarithms. In mathematical terms, this means that the decibel (dB) is defined as follows, where P1 and P2 are the power (signal strength) measurements:
dB = 10 log10 (P1/P2)
Decibels are used in network cabling systems for measuring signal losses. In addition, quantities such as attenuation and near-end crosstalk (NEXT) for fiber-optic cabling are expressed in units that contain decibels. In this scenario, P1 is the strength of the signal when it enters the cabling system, and P2 is its strength at some later point, after it has traversed segments of cable, repeaters, connectors, and other cabling system components. The following table shows signal strength ratios expressed both as ratios and as decibels for conversion purposes.
Signal Strength Ratios
| Signal Strength Ratio (P1:P2) | Decibels (dB) |
| 1:1 (no signal loss) | 0 dB |
| 2:1 (50 percent signal loss) | -3 dB |
| 4:1 (75 percent signal loss) | -6 dB |
| 10:1 (90 percent signal loss) | -10 dB |
| 100:1 (99 percent signal loss) | -20 dB |
| 1000:1 (99.9 percent signal loss) | -30 dB |
Example
The category 5 cabling version of unshielded twisted-pair (UTP) cabling has an attenuation rating of 30 dB/1000 feet. This means that after traveling 1000 feet along a UTP cable, the electrical strength of the signal typically diminishes by 99.9 percent and is only 0.1 percent of its original strength at the far end of the cable.
See also cabling, fiber-optic cabling, unshielded twisted-pair (UTP) cabling
A protocol suite developed by Digital Equipment Corporation (DEC). DECnet was originally designed in 1975 to allow PDP-11 minicomputers to communicate with each other.
DECnet conforms to the Digital Network Architecture (DNA) developed by DEC, which maps to the seven-layer Open Systems Interconnection (OSI) reference model for networking protocols. DECnet is essentially a peer-to-peer networking protocol for all DEC networking environments. DECnet supports various media and link-layer technologies, including Ethernet, Token Ring, and Fiber Distributed Data Interface (FDDI). The current release of DECnet is called Phase V.
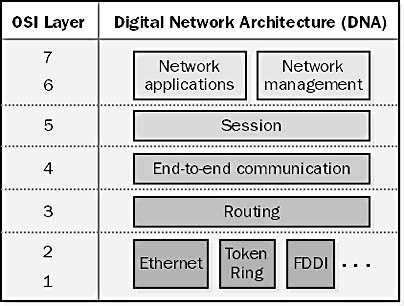
Graphic D-12. DECnet.
Any telecommunications line that is continuously available for the subscriber with little or no latency. Dedicated lines are also referred to as “leased lines.” Businesses often lease dedicated lines from telcos so that they can have continuous, uninterrupted communication with branch offices and with the Internet. The opposite of a dedicated line is a dial-up line, which costs less because it is used intermittently and requires fewer telco resources. However, dial-up lines suffer from the delaying effects of latency as well as less available bandwidth. Dial-up lines are generally local loop Plain Old Telephone Service (POTS) connections that use modems and provide backup services for more expensive leased lines.
Dedicated lines are allocated to the subscriber’s private domain, while dial-up lines are shared with all other subscribers in the Public Switched Telephone Network (PSTN) domain. Dedicated lines can be either point-to-point or multipoint communication paths.
The main advantages of dedicated lines are:
They involve minimal connection delays and minimal latency for establishing communication.
They provide a consistent level of service.
They are always available without any busy signals.
The main disadvantage of dedicated lines is that they cost more than dial-up lines.
See also dial-up line
A device on a TCP/IP internetwork that can forward Internet Protocol (IP) packets to another network, usually a router. In an internetwork, a given subnet might have several router interfaces that connect it to other, remote subnets. One of these router interfaces is usually selected as the default gateway of the local subnet. When a host on the network wants to send a packet to a destination subnet, it consults its internal routing table to determine whether it knows which router to forward the packet to in order to have it reach the destination subnet. If the routing table does not contain any routing information about the destination subnet, the packet is forwarded to the default gateway (one of the routers with an interface on the local subnet). The host assumes that the default gateway knows what to do with any packets that the host itself does not know how to forward.
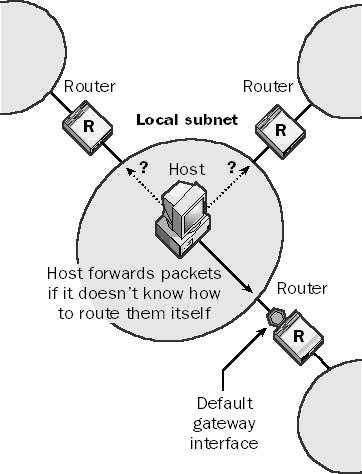
Graphic D-13. Default gateway.
When configuring a client machine on a TCP/IP internetwork, the client must know the IP address of the default gateway for its network. On Microsoft Windows NT, Windows 95, and Windows 98 clients, you configure this information on the TCP/IP property sheet for the client. The property to configure is called the Default Gateway Address. In Windows 2000, you can have a default gateway assigned automatically using Dynamic Host Configuration Protocol (DHCP).
A program established by the U.S. Undersecretary of Defense (Acquisition) to develop an integrated, global messaging system for transferring classified and unclassified data. The Defense Messaging System (DMS) will replace the existing Automatic Digital Network (AUTODIN) system currently in use by the U.S. Department of Defense.
Microsoft Exchange DMS, a version of Microsoft Exchange Server, complies with the DMS specification. It is suited for government agencies that are required to use DMS-compliant products and for companies that do defense business with the U.S. government. Exchange DMS technology can be purchased only through Lockheed Martin Federal Systems.
A feature supported by Active Directory in Microsoft Windows 2000. Delegation is part of the security framework of Active Directory. Along with other features such as the discretionary access control list (DACL), inheritance, and trust relationships, it enables Active Directory to be administered securely, protected from unauthorized access.
Delegation is the process of assigning permissions and rights to an object, container, or subtree of containers or organizational units (OUs) within Active Directory. These permissions and rights can be assigned for the following purposes:
Delegating management of a portion of Active Directory to a user or group of users by assigning permissions or rights to a portion of Active Directory
Protecting a portion of Active Directory from unauthorized access by denying permissions or rights to a portion of Active Directory
Using delegation, the network administrator can distribute the job of managing an Active Directory enterprise-level implementation among a group of individuals, each with the appropriate permissions and rights to manage her or his portion of the directory. For example, a user can be granted permissions and rights on the Users container so that he or she can create new users or modify the attributes of existing ones. In this fashion, the network administrator can be relieved of the tiresome duty of creating and configuring new user accounts by delegating the job to a junior administrator. Delegation is designed to relieve the network administrator of the burden of managing the entire Active Directory and is an important security management feature in Windows 2000.
NOTE
The Delegation of Control Wizard, which is part of the Active Directory Users and Computers administrative tool, can be used to delegate administration of portions of Active Directory to other administrators and users.
TIP
Always delegate administrative control at the level of organizational units, not at the level of individual objects. This allows you to better manage access to Active Directory because OUs are used to organize objects in the directory. One good idea is to delegate authority to those who are responsible for creating users, groups, computers, and other objects that commonly change in an enterprise.
Always assign permissions to groups instead of to individual users. Groups can be nested within one another and, together with inheritance of permissions, they provide a powerful tool for organizing the administration of Active Directory.
See also Active Directory
A wizard that you can run using the Active Directory Users and Computers administrative tool for networks in Microsoft Windows 2000. The Delegation of Control Wizard facilitates delegating control of different portions of Active Directory to other administrators and users. The wizard simplifies the process by allowing only the administrator to assign permissions at the level of organizational units (OUs). Assigning permissions to OUs rather than to particular directory objects ultimately simplifies the Active Directory administrator’s work.
How It Works
To start the wizard, open the Active Directory Users and Computers tool, select the OU you want to delegate control for, and choose Delegate Control from the Action menu. Specify the users or groups to whom you want to delegate control, the subset of object types in the OU for which this should take place, and the kinds of permissions you want to assign.
See also Active Directory, delegation
A media access control method for 100VG-AnyLan networks. 100VG-AnyLan is a high-speed form of Ethernet based on the IEEE standard 802.12 developed by Hewlett Packard. Demand priority is the method by which stations on a 100VG-AnyLan network gain access to the wire for transmitting data.
How It Works
A 100VG-AnyLan network based on the demand priority access method consists of end nodes (stations), repeaters (hubs), switches, routers, bridges, and other networking devices. A typical 100VG-AnyLan network consists of a number of stations plugged into a cascading star topology of repeaters (hubs). Because of timing, a maximum of five levels of cascading of the physical wiring is permitted. Hubs are connected using uplink ports. Each hub is aware only of the stations directly connected to it and any hubs that are uplinked from it.
The key feature of the demand priority access method, as shown on the illustration, is that the 100VG-AnyLan hubs control which computers are allowed to transmit signals on the network at any given moment.
Hubs can be thought of as servers and end nodes as computers (clients). With demand priority, a client (a computer with a 100VG-AnyLan network interface card installed in it) must first request access to the network media (cabling) before transmitting data. The server (hub) processes this request and decides whether to allow the client access to the media. If the hub decides to grant the client access to the wire, it sends the client a signal informing it of this decision. The client then takes over control of the media and transmits its data.
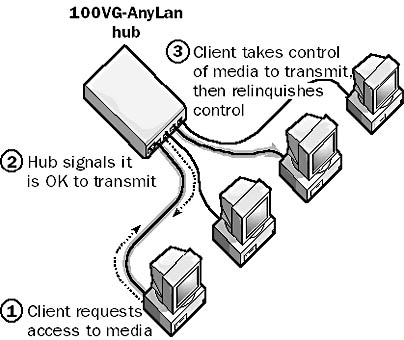
Graphic D-14. Demand priority.
Demand priority is considered a contention method, but it operates differently from the Carrier Sense Multiple Access with Collision Detection (CSMA/CD) access method used in Ethernet networks. Cables in a 100VG-AnyLan network are capable of transmitting and receiving data at the same time using all four pairs of twisted-pair cabling in a quartet signaling method. Each pair of wires in a twisted-pair cable transmits and receives data at 25 MHz, for a total bandwidth of 100 MHz. All contention on the network occurs at the hub. If two computers attempt to transmit signals at the same time, the hubs can either choose between the two signals based on priority or alternate between them if the priorities are equal. The hubs can do this because demand priority provides mechanisms for prioritizing transmission of different data types. Computers in demand priority networks can simultaneously transmit and receive data, and they do not need to listen to the network because the hubs control access to the wire.
See also 100VG-AnyLan, media access control method
A form of attack conducted against a system or network that occurs when a malicious user consumes so many resources that none are left for others. The resources attacked might include processors, disk space, memory, modems, telephone lines, and so on. A hacker might launch a denial of service attack using software that automates attempted access to shared resources on a network exposed through the Internet.
How It Works
Denial of service attacks are often launched by hackers who want to bring down a Web server on the Internet. A common example of an attack is the SYN attack, a protocol-level attack that is intended to render the Web server’s networking services unavailable. SYN flooding is a type of attack in which Transmission Control Protocol (TCP) connection request packets (SYN packets) are sent in large numbers to a Web server. These packets use a false or “spoofed” source IP address to hide the attacker. SYN packets are used to place the TCP ports in the SYN _RECEIVED, or “half-open,” state on the Web server and then do nothing with them until they time out. If enough of these ports are half-opened, the server cannot service requests from normal clients until the unused ports expire. Unfortunately, it takes time for the half-opened ports to time out because, when a SYN packet is received, the server generates a SYN-ACK packet to acknowledge the request and then waits for a final ACK from the requester before fully opening the port for a communication session. (This is called a TCP three-way handshake.) However, that final ACK is not received because the source address in the SYN packet was spoofed. The SYN-ACK packet is thus retransmitted several times at increasingly longer time intervals until, after a total time of 189 seconds (in the implementation of TCP/IP on Microsoft Windows platforms), the server finally gives up and closes the half-open port. For that time period, the requested port is unavailable to perform any other services.
TIP
If users try to connect to your Web server and receive error messages such as “The connection has been reset by the remote host,” a SYN attack might be under way on your machine. (When the maximum number of TCP ports are in use [open or half-open] on a machine, the machine usually responds to any further connection attempts with a reset.)
To determine whether such an attack is in progress, type netstat -n -p tcp at the command prompt to see whether there are a large number of ports in the half-open SYN_RECEIVED state. If so, try using a network protocol analyzer such as Network Monitor to further examine the situation. You might need to contact your Internet service provider (ISP) to investigate the problem more closely.
If your server is under a heavy SYN attack, one fix you can try on Windows NT platforms running Microsoft Internet Information Server (IIS) is to decrease the default timeout for terminating half-open TCP connections. Open the TcpMaxConnectResponseRetransmissions parameter in the registry and set it to 3, 2, or even 1 to reduce the timeout to 45, 21, or 9 seconds, respectively. However, if you set this parameter too low, legitimate connections might experience timeouts. Windows 2000 and Windows NT 4 Service Pack 3 have corrected this problem. A fix is available for Windows NT version 3.51 from Microsoft.
A technology for achieving extremely high data rates over fiber-optic cabling. Also known as wave division multiplexing (WDM), dense wavelength division multiplexing (DWDM) will likely replace time-division multiplexing (TDM) as the standard transmission method for high-speed fiber-optic backbones in the next few years.
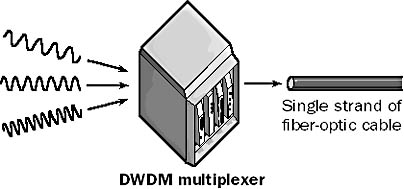
Graphic D-15. Dense wavelength division multiplexing (DWDM).
How It Works
DWDM modulates multiple data channels into optical signals that have different frequencies and then multiplexes these signals into a single stream of light that is sent over a fiber-optic cable. Each optical signal has its own frequency, so up to 80 data streams can be transmitted simultaneously over the fiber using only eight different light wavelengths. In addition, each data stream can employ its own transmission format or protocol. This means that, using DWDM, you can combine Synchronous Optical Network (SONET), Asynchronous Transfer Mode (ATM), TCP/IP, and other transmissions and send them simultaneously over a single fiber. At the other end, a multiplexer demultiplexes the signals and distributes them to their various data channels.
Devices that support DWDM are more costly because the laser light sources for generating signals over fiber must be highly stable.
See also time-division multiplexing (TDM)
See Data Encryption Standard (DES)
The ever-present background of the graphical user interface (GUI) for Microsoft Windows 95, Windows 98, Windows NT version 4, and Windows 2000 systems. The desktop is the user’s on-screen work area; its various icons and menus are arranged as if on top of a physical desk. Users can place items on the desktop, drag them around, move them into folders, and start and stop tasks using simple mouse actions such as clicking, double-clicking, dragging, and right-clicking.
With the Active Desktop of Windows 98 (or on Windows 95 or Windows NT 4 with Microsoft Internet Explorer version 4 installed and the Desktop Update feature selected), Web browser functions also appear on the desktop. Users can browse local and network file system objects along with content on the Internet using a familiar Web browser paradigm. Active Web content can be placed directly on the desktop and updated automatically.
See also Active Directory
A standard for managing desktop systems developed by the Desktop Management Task Force (DMTF). Using the Desktop Management Interface (DMI), information can be automatically collected from system components such as network interface cards (NICs), hard disks, video cards, operating systems, and applications that are compliant with the DMI standard. DMI was designed to be operating system–independent and protocol-independent and was designed for use on local systems that do not have a network installed. DMI can be mapped to Simple Network Management Protocol (SNMP). Note that DMI itself does not specify a protocol for managing systems over the network; instead, it must use an existing network management protocol such as SNMP to send and receive information over the network.
How It Works
DMI is similar in design to SNMP. Each component to be managed must have a Management Information Format (MIF) file that specifies the location of the component, name of vendor and model, firmware revision number, interrupt request line (IRQ), I/O port address, and so on. MIF files are formatted as structured ASCII flat-file databases; the Desktop Management Task Force has defined several standard MIFs including the Desktop System MIF file, the Adapter Card MIF file, and the Printer MIF file.
DMI service layer software running on the desktop collects information from DMI-enabled components and stores this information in the appropriate MIF file. The service layer thus acts as an intermediary between the DMI-enabled components and the DMI management application, and it coordinates shared access to the various MIFs installed on the desktop system. DMI management applications can then query the service layer on the desktop to obtain the various system components and applications from these MIF files. The service layer allows the management layer to interact with the MIFs by using commands such as
Get, which obtains information from a MIF
Event, which alerts the management application when certain events occur
Set, which modifies the contents of a MIF
One advantage of DMI over SNMP is that DMI management applications can access MIF files even when they have no prior information about them.
DMI management applications include Intel’s LANDesk and Microsoft Systems Management Server (SMS). SMS uses standard DMI 4.5 MIF files to expose inventory data for systems it manages and then stores this information in a Microsoft SQL Server database.
NOTE
The newer Web-Based Enterprise Management (WBEM) initiative from the DMTF proposes the Common Information Model (CIM) as a common abstraction layer for unifying the various existing data providers for system and network management, including DMI and SNMP. Microsoft has implemented WBEM into the Windows 2000 operating system as the Windows Management Instrumentation (WMI).
The address to which a frame or packet of data is sent over a network. The destination address is used by hosts on the network to determine whether the packet or frame is intended for them or for other hosts. The destination address is also used by routers to determine how to forward the packet or frame through an internetwork. The destination address can be one of the following:
The physical address, such as the MAC address of an Ethernet frame
The logical address, such as the IP address of an IP packet
Destination addresses can be either specific or general. Specific addresses point to a specific host on the network. A general address points the packet or frame to all hosts on the network or multicasts it to a specific multicast group of hosts on the network.
NOTE
The other kind of address in a packet or frame is the source address. This is the address of the host from which the packet originates (unless the source address is being spoofed).
TIP
You can see the destination address of a packet or frame by using a network sniffer device such as Network Monitor, a tool included with Microsoft Systems Management Server (SMS). Network Monitor displays destination addresses in both ASCII and hexadecimal form.
See also source address
Generally, any hardware component that can be driven by software.
In Microsoft Windows 2000, you can work with devices using the Device Manager, which you access through the System utility in Control Panel. In Windows NT, you can view, stop, and start devices using the Devices utility in Control Panel.
In Microsoft SQL Server version 6, a device is a file used to store SQL Server databases. Multiple SQL Server databases can be stored on a single device, and a single database can span multiple devices.
The master system device contains four databases:
The master system database, which is used for tracking system-wide information
The tempdb system database, which is used for temporary storage purposes
The model system database, which is a template for generating new databases
The pubs sample database, which is used in the examples in the SQL Server documentation
A Microsoft Windows 95 and Windows 98 troubleshooting tool that is part of the System utility in Control Panel. Device Manager is used for managing peripheral devices and their associated system resources.
You can use Device Manager to do the following:
View the name and manufacturer of a device
Identify devices that are disabled (displaying a red X) or in a problem state (displaying an exclamation point)
Display and modify the interrupt request line (IRQ), I/O port, and other resources for a device
Load a new driver for a device
Disable conflicting plug and play devices in order to free their resources
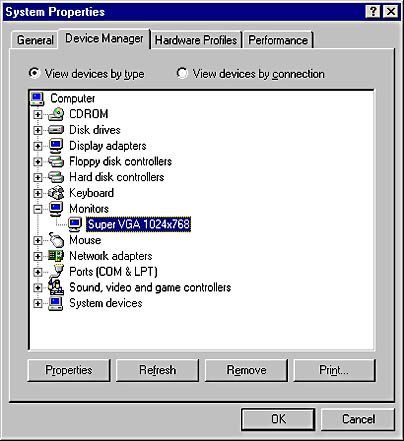
Graphic D-16. Device Manager.
NOTE
Windows 2000 also has a Device Manager tool that graphically displays the hardware installed on the computer and allows you to configure that hardware. You can start it by clicking the Device Manager button on the Hardware tab in Control Panel’s System utility.
See Distributed file system (Dfs)
See Dynamic Host Configuration Protocol (DHCP)
A host on a TCP/IP internetwork that is capable of having its IP address information dynamically assigned using Dynamic Host Configuration Protocol (DHCP). The term “DHCP client” can also describe the software component on a computer that is capable of interacting with a DHCP server to lease an IP address.
Microsoft Windows comes with DHCP client software that you can configure when you install the TCP/IP protocol suite. This software allows a machine to immediately take its place in TCP/IP internetworks using DHCP. Other operating systems might require that the DHCP client software be installed and configured separately.
Microsoft operating systems that can function as DHCP clients include the following:
Windows 2000
Windows NT
Windows 98
Windows 95
Windows for Workgroups with the Microsoft TCP/IP-32 add-on installed
Network Client 3 for MS-DOS
LAN Manager 2.2c
NOTE
On machines running Windows 2000, the DHCP client is DNS-aware and uses dynamic update for registering addresses, which allows the IP address and fully qualified domain name (FQDN) of client machines to be assigned and supported together.
TIP
Windows NT, Windows 95, and Windows 98 clients can release and renew their IP address leases using the ipconfig command. This command can also be useful for resolving IP address conflicts or for troubleshooting DHCP clients and servers.
See also DHCP server, Dynamic Host Configuration Protocol (DHCP)
A process for configuring a Dynamic Host Configuration Protocol (DHCP) server so that a particular host on the network always leases the same IP address. You can create a client reservation on a DHCP server if you want the server to always assign the same IP address to a specific machine on the network. You might do this to assign IP addresses to servers on the network because the IP addresses of servers should not change. (If they do, client machines might have difficulty connecting with them.) An alternative and more common way to assign a client reservation to a server is to manually assign a static IP address to the server.
How It Works
On Microsoft Windows 2000–based networks you can create DHCP client reservations using the DHCP console, while in Windows NT you use DHCP Manager. Enter the MAC address as the client’s unique identifier. When the client with that address contacts the DHCP server to request an IP address, the server leases the reserved address to the client.
See also DHCP console, DHCP Manager
The service in Microsoft Windows 2000 and Windows NT that implements the client component of the Dynamic Host Configuration Protocol (DHCP) on workstations and servers. You can use the DHCP client service to obtain IP addresses and other TCP/IP configuration information from a DHCP server (such as a Windows 2000 or Windows NT server running the DHCP Server service).
Microsoft Windows includes support for DHCP and provides client software that lets you manage a machine’s IP address over a network. This software runs as a service under Windows 2000 and Windows NT. DHCP simplifies the administration and management of IP addresses for machines on a TCP/IP network.
See also DHCP Server service, Dynamic Host Configuration Protocol (DHCP)
A Microsoft Windows 2000 administrative tool for managing the DHCP Server service on Windows 2000 Server. The DHCP console is the main tool used for managing and configuring all aspects of the Dynamic Host Configuration Protocol (DHCP) on a Windows 2000–based network and is implemented as a snap-in for the Microsoft Management Console (MMC).
You can use the DHCP console for the following standard DHCP administration tasks:
Creating a scope of IP addresses to lease to DHCP clients
Creating a set of scope options, which are passed on to clients
Configuring the lease duration for IP addresses leased to clients
Viewing and terminating active leases on a network
Creating reservations for servers that need specific IP addresses
Monitoring DHCP statistics
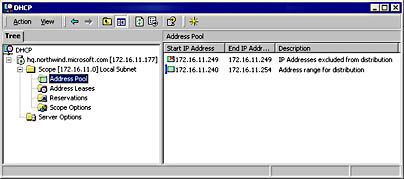
Graphic D-17. The DHCP console for Windows 2000 Server.
The DHCP console also includes the following advanced features, which are new to Windows 2000:
Automatic detection of rogue DHCP servers on the network
Automatic self-assignment of temporary IP addresses to clients if a lease cannot be obtained from a DHCP server
New DHCP options for multicast groups (class D IP addresses), superscopes for grouping together DHCP scopes for management purposes, and other vendor-specific functions
Integration of DHCP and Domain Name System (DNS), allowing clients to use dynamic update to update their host names to IP address mappings in DNS server zone files
See also Dynamic Host Configuration Protocol (DHCP)
The duration for which a DHCP server loans an IP address to a DHCP client. You can configure the lease duration using the Microsoft Windows NT administrative tool DHCP Manager or the Windows 2000 console snap-in.
TIP
If your TCP/IP network configuration doesn’t change often or if you have more than enough IP addresses in your assigned IP address pool, you can increase the DHCP lease considerably beyond its default value of three days. However, if your network configuration changes frequently or if you have a limited pool of IP addresses that is almost used up, keep the reservation period short—perhaps one day. The reason is that if the pool of available IP addresses is used up, machines that are added or moved might be unable to obtain an IP address from a DHCP server and thus will be unable to participate in network communication.
See also DHCP console, DHCP Manager
A Microsoft Windows NT administrative tool for managing the DHCP Server service on Windows NT Server. DHCP Manager is the main tool used for managing and configuring all aspects of the Dynamic Host Configuration Protocol (DHCP) on a Windows NT–based network. DHCP Manager is installed on a machine running Windows NT Server by using the Network utility in Control Panel to add the Microsoft DHCP Server service to the machine.
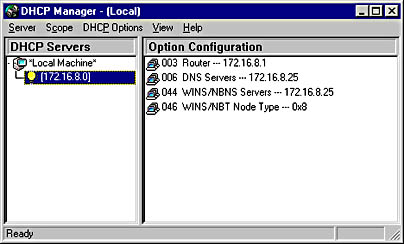
Graphic D-18. Administrative tool for Windows NT Server 4.0.
You can use DHCP Manager for the following tasks:
Creating a scope of IP addresses to lease to DHCP clients
Creating a set of scope options, which are passed on to clients
Configuring the lease duration for IP addresses leased to clients
Viewing and terminating active leases on a network
Creating reservations for servers that need specific IP addresses
See also Dynamic Host Configuration Protocol (DHCP)
Additional IP address settings that a DHCP server passes to DHCP clients. When a DHCP client requests an IP address from a DHCP server, the server sends the client at least an IP address and a subnet mask value. Additional information can be sent to clients if you configure various DHCP options. You can assign these options globally to all DHCP clients, to clients belonging to a particular scope, or to an individual host on the network.
You can configure a number of different DHCP options using the Microsoft Windows NT administrative tool DHCP Manager and the Windows 2000 snap-in DHCP console, but the options listed in the following table are the ones most commonly used by Microsoft DHCP clients. In Windows NT–based networks options 3, 6, 44, and 46 are the most commonly used, while in Windows 2000–based networks options 3, 6, and 15 are commonly used.
DHCP Options
| Number | Option | What It Configures |
| 003 | Router | Default gateway IP address |
| 006 | DNS Servers | IP addresses of DNS servers |
| 015 | DNS Domain Name | Parent domain of associated DNS servers |
| 044 | NetBIOS over TCP/IP Name Server | IP addresses of Windows Internet Name Service (WINS) server |
| 046 | NetBIOS over TCP/IP Node Type | Method of NetBIOS name resolution to be used by the client |
| 047 | NetBIOS over TCP/IP Scope | Restricts NetBIOS clients to communication with clients that have the same scope ID |
See also DHCP console, DHCP Manager
A TCP/IP host that is configured to allow a single DHCP server to lease IP address information to DHCP clients on multiple subnets. DHCP relay agents make it unnecessary to maintain a separate DHCP server on every subnet in an internetwork. You can configure Microsoft Windows NT and Windows 2000 servers to operate as DHCP relay agents.
How It Works
The DHCP relay agent is a machine with the DHCP Relay Agent service installed and configured to forward DHCP requests to a DHCP server on a different subnet (as shown in the illustration). The process happens as follows:
A DHCP client on the subnet where the DHCP relay agent is configured broadcasts a request for a lease from a DHCP server.
Since there is no DHCP server on the client’s subnet, the DHCP relay agent picks up the client’s request and forwards it directly to the DHCP server on another subnet.
The DHCP server responds to the request by offering a lease directly to the client.
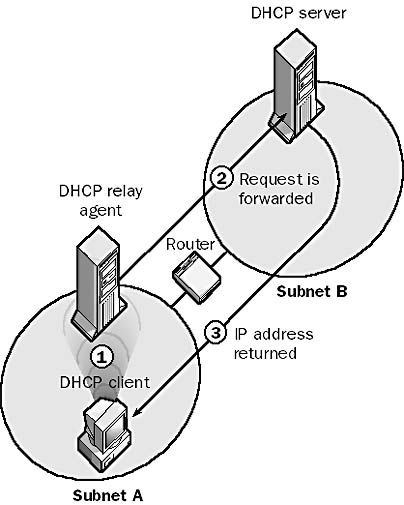
Graphic D-19. DHCP relay agent.
TIP
To configure a machine running Windows NT Server as a DHCP relay agent, you must do two things:
Install the DHCP Relay Agent service using the Services tab of the Network utility in Control Panel.
Configure the DHCP server that the agent will pass requests to. Do this on the DHCP Relay tab of the Microsoft TCP/IP Properties sheet of the TCP/IP protocol.
TIP
To configure a Windows 2000 server as a DHCP relay agent, follow these steps:
Open the Routing and Remote Access console from the Administrative Tools program group.
Expand the server node to display General beneath IP Routing in the console tree.
Right-click General, and select New Routing Protocol from the context menu.
Specify DHCP Relay Agent in the New Routing Protocol dialog box, and click OK.
Open the property sheet for DHCP Relay Agent under IP Routing in the console tree, specify the IP address of the DHCP server to which lease requests should be relayed, and click OK.
Right-click DHCP Relay Agent in the console tree, and select New Interface to specify a router interface on which relay will be enabled.
See also Dynamic Host Configuration Protocol (DHCP)
A range of IP addresses that a DHCP server can lease out to DHCP clients. You configure the DHCP scope using the Microsoft Windows NT administrative tool DHCP Manager or the Windows 2000 snap-in DHCP console. The IP addresses are leased for a specific Time to Live (TTL), usually three days. Information about scopes and leased IP addresses is stored in the DHCP database on the DHCP server. The values for IP address scopes created on DHCP servers must be taken from the available pool of IP addresses allocated to the network. Errors in configuring the DHCP scope are a common reason for problems in establishing communication on TCP/IP networks.
TIP
If non-DHCP clients have static IP addresses that fall within the range of the server’s DHCP scope, these static IP addresses must be excluded from the scope. Otherwise, two hosts might end up with the same IP address, one assigned statically and the other assigned dynamically, resulting in neither host being able to communicate on the network.
See also DHCP console, DHCP Manager
A server that dynamically allocates IP addresses to client machines using the Dynamic Host Configuration Protocol (DHCP). DHCP servers perform the server-side operation of the DHCP protocol. The DHCP server is responsible for answering requests from DHCP clients and leasing IP addresses to these clients.
DHCP servers should have static IP addresses. A DHCP server gives DHCP clients at least two pieces of TCP/IP configuration information: the client’s IP address and the subnet mask. Additional TCP/IP settings can be passed to the client as DHCP options.
NOTE
To have Microsoft Windows 2000 Server function as a DHCP server, install the DHCP Server service and manage it using the DHCP console snap-in for the Microsoft Management Console (MMC). To have Windows NT Server function as a DHCP server, install the DHCP Server service and configure it using the administrative tool DHCP Manager. Note that a DHCP server should generally not be a DHCP client—that is, it should have a static IP address.
TIP
If hosts on a TCP/IP network are randomly losing connectivity with the network one by one, the DHCP server might be down and unable to renew leases for IP addresses obtained by the clients. Without a valid IP address leased to them, DHCP clients cannot communicate over the network.
See also DHCP client, DHCP Server service, Dynamic Host Configuration Protocol (DHCP)
The service in Microsoft Windows 2000 and Windows NT that implements the server component of the Dynamic Host Configuration Protocol (DHCP) on Windows 2000 Server or Windows NT Server. The DHCP Server service is an optional networking component that can be installed on
Windows NT Server by using the Network utility in Control Panel, selecting the Services tab, and adding the Microsoft DHCP Server service. When this service is installed on a machine running Windows NT Server, the administrative tool DHCP Manager is also installed.
Windows 2000 Server by using the Add/Remove Programs utility in Control Panel, selecting Add/Remove Windows Components, and selecting Dynamic Host Configuration Protocol (DHCP) from Networking Services. When this service is installed on a machine running Windows 2000 Server, the DHCP console administrative tool is implemented as a snap-in for the Microsoft Management Console (MMC).
NOTE
The DHCP Server service should generally be installed only on a machine that has a manually assigned static IP address.
See also Dynamic Host Configuration Protocol (DHCP)
Any telecommunications link that is serviced by a modem. Dial-up lines are ordinary phone lines used for voice communication, while dedicated or leased lines are digital lines with dedicated circuits. Dial-up lines are generally much less expensive to use, but they have less available bandwidth.
Companies often use dial-up lines for occasional, low-bandwidth usage (such as remote access networking) or as a backup for more costly dedicated lines. Dial-up lines are shared with all subscribers in the Public Switched Telephone Network (PSTN) domain, while dedicated or leased lines are allocated solely to the subscriber’s private telecommunications domain.
See also dedicated line
See Network and Dial-up Connections
A Microsoft Windows NT utility accessed through Control Panel that shows status information for an active dial-up networking session. Dial-Up Networking Monitor is one of the tools included in Windows NT when Remote Access Service (RAS) is installed on the machine.
Dial-Up Networking Monitor shows the following information:
The condition of the selected RAS device
Device and connection statistics in bytes and frames in and out
Accumulated device errors and overruns
The networks and users your devices are connected to
Preferences for status icons and sounds
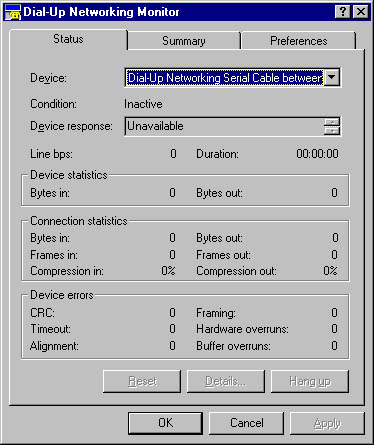
Graphic D-20. Dial-Up Networking Monitor.
See also Network and Dial-up Connections
See direct inward dialing (DID)
A backup type in which only files and folders that have changed since the last normal backup are backed up. Unlike an incremental backup, a differential backup does not clear the archive attribute for each file and folder. You can use differential backups in conjunction with normal backups to simplify and speed up the backup process. If a normal backup is done on a particular day of the week, differential backups can be performed on the remaining days of the week to back up the files that have changed since the first day of the backup schedule. Differential backups are faster than normal backups and use less tape or other storage media.
NOTE
Differential backups are cumulative (unlike incremental backups), so when you need to do a restore, you need only the normal backup and the most recent differential backup. Differential backups take longer to complete than incremental backups, but they are faster to restore data from.
See also backup type, incremental backup
See digital transmission
The digital version of the Advanced Mobile Phone Service (AMPS), the standard analog cellular phone technology common throughout North America and around the world. Digital Advanced Mobile Phone Service (D-AMPS) cellular systems, which have been used since 1992, build on the large installed base of AMPS cellular network installations. D-AMPS is cheaper and easier to implement than Code Division Multiple Access (CDMA) cellular technologies, but its transmissions are not as secure.
How It Works
D-AMPS uses the same 800 to 900–MHz frequency bands and 30-kHz carrier spacing that AMPS uses, although a dual-band 800/1900 MHz system has also been implemented. D-AMPS differs from AMPS technology by using Time Division Multiple Access (TDMA) technology as its media access technique. TDMA splits each 30 kHz–wide AMPS channel into three additional channels. This triples the number of cellular phone channels available under AMPS. D-AMPS is an easier upgrade path from AMPS than Global System for Mobile Communications (GSM), which also uses TDMA technology but in an incompatible format.
See also Advanced Mobile Phone Service (AMPS)
A proposed standard for a multimegabit packet-switching radio network from the European Telecommunications Standards Institute (ETSI). The Digital Advanced Wireless System (DAWS) will be compatible with the existing packet radio system called the Terrestrial Trunked Radio (Tetra), which enables terminals to communicate directly with each other in regions without cellular coverage.
DAWS is being developed in response to the rapid deployment of Global System for Mobile Communications (GSM) wireless cellular communication systems and the increasing demand for high-speed wireless mobile data services in response to the phenomenal growth of the Internet in recent years. The ultimate goal of the DAWS effort is to provide mobile wireless Asynchronous Transfer Mode (ATM) data communication services with full-terminal mobility over wide areas of roaming. ATM has been selected by ETSI as the technology of choice for the backbone of the future envisaged European Information Infrastructure (EII).
DAWS will be designed to support applications that require data rates in excess of the 2-Mbps rate supported by the International Mobile Telecommunications-2000 (IMT-2000) standards, with eventual planned support for full ATM rates of 155 Mbps envisioned. Examples include wireless networking, Internet browsing, video conferencing, file transfer, and Voice over IP (VoIP).
See also Terrestrial Trunked Radio (Tetra)
A technology for verifying the identity of the user or service you are communicating with. Digital certificates are issued by certificate authorities (CAs), which are public or private organizations that manage a public key infrastructure (PKI). The main function of a digital certificate is to associate a specific user with his or her public/private key pair.
Digital certificates are the networking equivalent of driver’s licenses, and they go hand in hand with encryption to ensure that communication is secure. Digital certificates verify the authenticity of the holder, and they can also indicate the holder’s privileges and roles within secure communication. They can be used like driver’s licenses for identification purposes or like bank cards (together with a password) to perform financial transactions in e-commerce and online banking. Digital certificates enable various rights, permissions, and limitations to be applied to their holders for various kinds of trusted communication purposes such as purchasing, government banking, benefits, and voting rights.
How It Works
A digital certificate consists of data that definitively identifies an entity (an individual, a system, a company, or an organization). Digital certificates are issued by and digitally signed with the digital signature of the CA (once the CA has verified the identity of the applying entity). In addition to identification data, the digital certificate contains a serial number, a copy of the certificate holder’s public key, the identity and digital signature of the issuing CA, and an expiration date. The CA also maintains a copy of the user’s public key in its centralized certificate storage facility.
Digital certificates are formatted according to an International Organization for Standardization (ISO) standard called X.509 v3. The X.509 standard specifies that a digital certificate must contain the following information fields:
Version number
Certificate serial number
Signature algorithm ID used
Name of certificate issuer
Validity period (for certificate expiration)
Subject name (name of certificate owner)
Public key information for subject
Unique identifier of certificate issuer
Unique identifier of subject
Extensions
Digital signature for all the above fields
Digital certificates and public key cryptography are used in the popular Secure Sockets Layer (SSL) protocol, which provides secure transactions over the Internet. Several types of digital certificates are involved in this process, including
CA certificate, which identifies the certificate authority, such as those based on Microsoft Certificate Server, and is used by Web browsers and Web servers to validate client and server certificates
Server certificate, which identifies a Web server such as Microsoft Internet Information Services (IIS)
Client certificate, which identifies a Web browser such as Microsoft Internet Explorer
NOTE
A digital certificate is not the same as a digital signature. A digital certificate is a file that certifies the owner’s identity, contains the owner’s public key, and can be used to support encrypted communication. The purpose of a digital certificate is to certify that the user has the right to use the public/private key pair that has been issued by the CA. A digital signature, on the other hand, contains identity information along with the message or document itself (which has been hashed using the private key of the sender), and it confirms the identity of the sender and ensures that the content of the message has not been modified in transit.
In other words, to send an encrypted transmission, a user signs the message with a digital signature. But in order to be able to do this at all, the user must first be issued a key pair and its associated digital certificate.
See also digital signature
A family of leased line data communication technologies that provides a dedicated synchronous transmission connection at speeds of 56 Kbps. Digital data service (DDS) is only one example of a type of digital line; others include Integrated Services Digital Network (ISDN) and T1. DDS can be used in either multipoint or point-to-point communications and requires dedicated digital lines. DDS lines can also be used to connect buildings on a campus, usually with a maximum distance of about 3 miles.
How It Works
“DDS” was originally a trademark for an AT&T all-digital service running at 56 Kbps, but the term has evolved into a general descriptor for a variety of digital services offered by different carriers under various names. DDS is usually available in both a dial-up version called switched 56 and a dedicated leased line service for continuous connections. The dial-up version can serve as a backup for the dedicated version.
Typically, DDS uses four wires to support digital transmission speeds of 56 Kbps, but it is actually a 64-Kbps circuit that uses 8 Kbps for sending signaling information. Some vendors provide a variant of DDS with a data transmission rate of a full 64 Kbps.
To use DDS services for wide area network (WAN) connectivity, route packets from your local area network (LAN) through a bridge or a router, which is connected by means of a V.35 or RS-232 serial interface to a CSU/DSU (Channel Service Unit/Data Service Unit). The CSU/DSU is connected to the four-wire termination of the DDS line by means of an M-block connector, a screw terminal block, or some other connection mechanism. The Channel Service Unit (CSU) converts the data signal into a bipolar signal suitable for transmission over the telecommunications link. The DDS lines themselves use four wires and support speeds of 64 Kbps, but 8 Kbps of bandwidth is usually reserved for signaling, so the actual data throughput is usually only 56 Kbps.
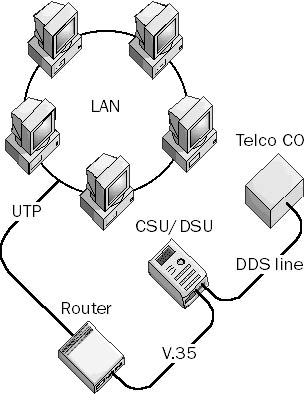
Graphic D-21. Digital data service (DDS).
DDS lines are dedicated lines with negligible connection establishment latency; they are always “on” and never “busy.”
See also telecommunications services
An umbrella term for various kinds of digital telecommunications services. The distinguishing feature of a digital line is that it is digital from end to end and does not employ any kind of analog modem technologies. As a result, digital lines have higher traffic-carrying capacities, less noise, and better error-handling features than analog lines. The term “digital line” can refer to circuits based on the following:
Digital data service (DDS)
Integrated Services Digital Network (ISDN)
T-carrier services such as T1 lines, fractional T1, and T3
Switched 56 services
Any type of modem used for synchronous transmission of data over circuit-switched digital lines. One example of a digital modem is an ISDN terminal adapter. Digital modems are not used for changing analog signals into digital signals because they operate on end-to-end digital services. Instead, they use advanced digital modulation techniques for changing data frames from a network into a format suitable for transmission over a digital line such as an Integrated Services Digital Network (ISDN) line. They are basically data framing devices, rather than signal modulators.
A paradigm for electronic connectivity between businesses that enables them to create efficient, integrated systems that are easy to use and manage. The digital nervous system can be viewed as the next evolutionary phase of the Information Age.
The idea of this business paradigm is that businesses connect to each other in a way that is similar to the organization of a living organism. Digital information—whether it is text, graphics, audio, or video—flows between businesses much like electrical impulses flow between parts of the body. A stimulus of information entering one business that is generated by another business produces a response. The greater the complexity and the more interconnected the nervous system, the higher the organism—and the same applies to business. Greater interflow of digital information can lead to the evolution of new forms of doing business. The Internet and its related paradigms “intranet” and “extranet” serve as examples of this evolution. These concepts grew naturally—almost organically—from the complex interconnectedness fostered by advances in software and networking.
On the Web
•
Microsoft Digital Nervous System home page : http://www.microsoft.com/dns
See DS0
An electronic signature that you can use to sign a document being transmitted by electronic means such as e-mail. Digital signatures validate the identity of the sender and ensure that the document they are attached to has not been altered by unauthorized parties during the transmission.
How It Works
Digital signatures are based on public key cryptography systems. In order for digital signatures to work, the sender must have both a digital certificate and a key pair issued by a certificate authority (CA) such as VeriSign, Inc. A digital signature for a particular document is created using a mathematical hash of the document, which is then encrypted using the sender’s private key. The resulting signature is attached to the document and transmitted. The receiver performs the same hash on the received document using the sender’s public key. If the two hashes match, it means that the message has been transmitted without corruption by the identified sender. Note that the particular content of a digital signature depends on the document being transmitted; it is different for each document sent.
See also digital certificate
A telecommunications technology for providing high-speed transmission to subscribers over the existing copper wire twisted-pair local loop between the customer premises and the telco’s central office (CO). The Digital Subscriber Line (DSL) technology was designed to provide high-speed data and video-on-demand services to subscribers at speeds much faster than Integrated Services Digital Network (ISDN). The essential advantage of using DSL is that it allows much faster data transmission rates over existing copper local loop telephone lines than traditional modems.
DSL standards are still evolving, and implementation is not yet widespread in most locations. In addition, DSL is competing with cable modem technologies to replace ISDN for high-speed Internet access.
How It Works
DSL is not a specific digital line technology but rather a form of digital modem technology that defines the signaling processes for high-speed, end-to-end digital transmission over the existing copper twisted-pair wiring of the local loop. DSL accomplishes this by using advanced signal processing and digital modulation techniques. However, with DSL, the digital signals are not converted to analog or vice versa; instead, the signals remain digital for the complete communication path from the customer premises to the telco’s CO.
Usually, a DSL modem and a signal splitter are installed at the customer premises to separate voice and data signals. DSL modems can use a variety of modulation methods, including carrierless amplitude and phase modulation (CAP) or discrete multitone (DMT) technology modulation, depending on the vendor’s implementation. At the telco’s CO, a Digital Subscriber Line Access Multiplexer (DSLAM) connects subscribers to a high-speed Asynchronous Transfer Mode (ATM) backbone.
DSL actually represents a family of related services commonly referred to as “xDSL,” which includes the following:
Asymmetric Digital Subscriber Line (ADSL), which allocates line bandwidth asymmetrically with downstream (CO to customer premises) data rates of up to 9 Mbps and upstream rates of up to 640 Kbps, depending on the implementation
High-bit-rate Digital Subscriber Line (HDSL), which supports high-speed, full-duplex communication up to T1 or E2 speeds over multiple twisted-pair lines
Symmetric Digital Subscriber Line (SDSL), which supports standard telephone communication and T1 or E1 data communication over a single twisted-pair line
Very High-rate Digital Subscriber Line (VDSL), which supports downstream speeds of up to 52 Mbps over short distances
Depending on the type of xDSL technology used, signal modulation by the DSL modem might use CAP, DMT, or some other modulation process. (CAP is currently the most popular implementation.)
Transmission of signals that vary discretely with time between two values of some physical quantity, one value representing the binary number 0 and the other representing 1. With copper cabling, the variable quantity is typically the voltage or the electrical potential. With fiber-optic cabling or wireless communication, variation in intensity or some other physical quantity is used. Digital signals use discrete values for the transmission of binary information over a communication medium such as a network cable or a telecommunications link. On a serial transmission line, a digital signal is transmitted 1 bit at a time.
The opposite of digital transmission is analog transmission, in which information is transmitted as a continuously varying quantity. An analog signal might be converted to a digital signal using an analog-to-digital converter (ADC) and vice versa using a digital-to-analog converter (DAC). ADCs use a method called “quantization” to convert a varying AC voltage to a stepped digital one.
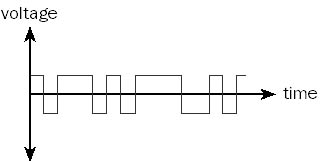
Graphic D-22. Digital transmission.
A cable consisting of multiple fiber-optic cables bundled together and enclosed in a protective sheath. Direct burial fiber-optic cabling is designed to be buried in trenches and contains a gel filling that protects the individual fibers from temperature and moisture variations. A strip of strengthening material runs axially down the cable to prevent excessive bending, which can fracture the individual fibers. Direct burial cabling can have steel-armor construction with heavy waterproof polyethylene jackets and can contain either multimode or single-mode fiber-optic strands.
Graphic D-23. Direct burial fiber-optic cabling.
TIP
Direct burial cabling is more cost-effective than single-fiber cabling for long outdoor cable runs between buildings or across a campus because it allows for future bandwidth upgrades.
See also fiber-optic cabling
A Microsoft Windows 95 and Windows 98 tool that enables file transfers between two computers running Windows 95 and/or Windows 98 using a serial null-modem cable or a standard parallel cable. You can use Direct Cable Connection to establish a temporary network connection for the purpose of transferring files between machines.
How It Works
One computer must be designated as the host (the server) and the other as the guest (the client). The desired resources must be shared on the host computer, and Dial-Up Networking must be installed on the guest computer.
TIP
The host computer can also act as a router that allows the guest computer to access resources on other computers on the host computer’s network.
A frame that is being sent by one station to a specific destination station on the network. On an Ethernet network, a directed frame is one that uses the hexadecimal MAC address of a specific target machine on the network as its destination address. The directed frame is picked up by the target machine and is ignored by all other machines on the network.
Directed frames are used for most network communication because they are the most efficient type of frame for communication. However, some services, such as network announcements, require that all stations on the network receive a frame. To send a frame to all stations on the network, you use a broadcast frame instead of a directed frame.
See also broadcast frame
An Internet Protocol (IP) packet that is being sent by one host on a TCP/IP network to a specific destination host on the network. A directed packet contains the IP address of a specific target host on the network as its destination address. The directed packet is picked up by the target host and is ignored by all other hosts on the network.
Directed packets are used for most network communication on a TCP/IP network because they are the most efficient method for communication. However, some services, such as network announcements, require that all hosts on the network receive a packet. To send a packet to all stations on the network, you use a broadcast packet instead of a directed packet.
See also broadcast packet
A service provided by a local exchange carrier (LEC) to a corporate client. Direct inward dialing (DID) uses a Private Branch Exchange (PBX) that allows outside callers to directly dial individuals within the company.
How It Works
The LEC allocates a block of phone numbers to the company, usually differing only in the last two, three, or four digits. For example, a company with 50 employees who each need a separate phone number could be assigned the numbers 555-1201 through 555-1250. Outside callers could dial the employees directly using these numbers, which are routed through perhaps only eight trunk lines that service the PBX, supporting a maximum of eight simultaneous calls. Inbound calls are routed by the PBX to the appropriate extension.
See Active Directory, directory database, directory service
A protocol for accessing information in a directory service based on the X.500 recommendations. The Directory Access Protocol (DAP) specifies how an X.500 Directory User Agent (DUA) communicates with a Directory System Agent (DSA) to issue a query. Using DAP, users can view, modify, delete, and search for information stored in the X.500 directory if they have suitable access permissions.
DAP is a complex protocol with a lot of overhead, which makes it generally unsuitable for implementations in a Microsoft Windows environment. A simpler version called Lightweight Directory Access Protocol (LDAP) is growing in popularity and can be used to access and update directory information in X.500 directories. LDAP is more suitable than DAP for implementation on the Internet and has mostly superseded DAP as an access protocol for X.500-based directories (which are now often called LDAP directories).
The central store of account and security information on a network. In Microsoft Windows NT and Windows 2000, the directory database resides on the domain controllers, which manage all security-related aspects of the network. In Windows NT, the directory database is generally called the Security Accounts Manager (SAM) database. In Windows 2000, the directory database is the database component of Active Directory.
The SAM database in Windows NT stores information about users, groups, and computers that participate in the domain. It also stores security policy information such as password expiration policies and audit policies. The SAM database stores its information in a privileged area of the registry.
NOTE
The practical upper limit for a SAM database is 40 MB, which corresponds to approximately 26,000 user and computer accounts. If an enterprise has more than 26,000 users, the Windows NT directory database can be partitioned (split) into two or more portions and trust relationships can be configured according to a multiple master domain model.
The process of exporting information from a directory service. Microsoft Exchange Server supports the exporting of information about recipients stored in its directory database. This information can be exported to a comma-delimited text file (.csv file), edited, and then imported into another system.
For example, you can import recipient information into a spreadsheet to print it out. Or you can export the information into a spreadsheet, use spreadsheet functions to mass-modify certain fields, and then use directory import for reimporting the modified account information back into Exchange. Using directory export/import is in fact the usual method in Exchange for modifying the properties of a large number of recipients at one time.
Graphic D-24. Directory export.
See also directory import
The hierarchy of all containers and leaf objects in a Microsoft Exchange Server directory, which is displayed and configured using the Exchange Administrator program. This hierarchy is based on the directory recommendations given by X.500.
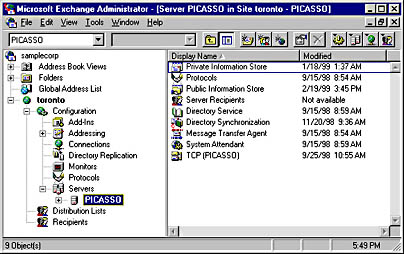
Graphic D-25. Directory hierarchy.
How It Works
The Exchange directory hierarchy begins at a root object called the Organization container, and then branches down into sites, servers, connectors, recipients, and other objects. To configure any object in the directory hierarchy, you use its property sheet.
Objects in the directory hierarchy of Exchange come in two types:
Containers, which can contain other directory objects. Containers usually also have configurable properties.
Leaf objects, which are end nodes in the directory tree and whose properties can be configured using their property sheets.
The process of importing information into a directory service. The information to be imported must be in a format that the importing system can understand, usually a delimited text file such as a .csv file. Microsoft Exchange Server allows recipient information to be imported into its directory database and allows recipients exported from other mail systems to be imported into Exchange. For example, you can use the Exchange Migration Wizard to extract mailbox information from a foreign mail system into a .csv file. You can then import this information into a spreadsheet program such as Microsoft Excel, modify it as needed, and import it into Exchange to create new mailboxes in your organization for users of the foreign mail system who are migrating to Exchange.
See also directory export
The replication of Microsoft Exchange Server directory information between Exchange servers within an Exchange organization. The Exchange directory database contains information about the various recipients in the organization and configuration information for all components of Exchange. Directory replication is a process that copies this information between Exchange servers so that all Exchange servers in an Exchange organization have easy access to this critical information.
How It Works
Directory replication in an Exchange organization gives each Exchange server a complete, up-to-date copy of all directory information for the entire organization. Directory replication occurs differently depending on whether Exchange servers are in the same site.
Within an Exchange site, intrasite replication of directory information takes place automatically and uses remote procedure calls (RPCs) between servers. You cannot configure this operation. Replication takes place approximately five minutes after a change is made to the directory. The server in which the change was made notifies other directories one at a time, and the other servers send the first server RPC messages requesting updates to the directory.
Between Exchange sites, intersite replication requires that you first establish messaging connectivity between sites using a connector such as the Site Connector. Then you must install and configure the Directory Replication Connector. Replication of directory changes takes place using standard e-mail messages communicated between the Exchange directory services on each machine. One server in each site is designated as a bridgehead server for requesting directory updates from the other site. You can schedule intersite directory replication to occur at off hours in busy networks or more frequently in networks in which frequent changes to recipients are made.
The process of replicating updates to Active Directory on different domain controllers in the network. Directory replication ensures that users have access to resources on the network by ensuring that information about users, groups, computers, file shares, printers, and other directory objects is current on all domain controllers in the network.
How It Works
Directory replication of Active Directory on a Microsoft Windows 2000–based network takes place in two ways, depending on whether the participating domain controllers are in the same site.
Within a site, intrasite replication between domain controllers uses remote procedure calls (RPCs) by means of a dynamically allocated port number. This replication takes place automatically every five minutes. Domain controllers within a site exchange update information in a ring fashion, from one domain controller to another. This ring topology is established by a periodically running process called the Knowledge Consistency Checker (KCC) and ensures a minimum of two replication paths between each pair of domain controllers and a maximum replication hop count of three hops to support efficient replication and fault tolerance.
Between sites, intersite replication can use RPCs if the local area network (LAN) or wide area network (WAN) connection supports them or some other method such as Simple Mail Transfer Protocol (SMTP) e-mail messages. Intersite replication uses a compressed format for more efficient use of slow WAN links and is easier to schedule and manage than intrasite replication.
TIP
To take advantage of the greater flexibility of intersite replication and to use it instead of intrasite replication, configure your domain controllers to belong to more than one physical site.
The replication of a tree of folders from one server to another using the Directory Replicator Service. You can use directory replication to create and manage identical directory structures on different Microsoft Windows NT servers and workstations. When a change is made to the master directory structure, such as modification of a file or addition of a directory, that change is replicated to the other computers.
One use for directory replication is to provide a means for load balancing file system information across several servers. This allows more clients to efficiently access the data stored in the replicated directory structure because identical data is stored on different machines. For example, you might replicate a database of customer information across several servers in your network to provide easier access. You can also use directory replication to copy logon scripts from a primary domain controller (PDC) to a set of backup domain controllers (BDCs). You can configure replication to occur between different computers in a domain or from one domain to another.
How It Works
The export server is the computer that contains the master copy of the directory tree to be replicated. This export server must be a machine running Windows NT Server. The computers that will replicate with the export server are called import servers. Import servers can be machines running Windows NT Server, Windows NT Workstation, or LAN Manager Server.
Prior to configuring directory replication, you must create a new user account as a security context within which the replicator service will run. This account should have a password that never expires and should be a member of the Replicator, Domain Users, and Backup Operators groups. The account should be accessible from both export and import machines. Use the Services utility in Control Panel to configure the Directory Replicator Service to start automatically upon system startup and to use your new account for logging on.
Server Manager is the administrative tool used for configuring replication in Windows NT. You can configure replication to occur either immediately after a change is made to the directory structure or after a stabilization period. When configuring replication, you select one of the following options:
Replicate the entire subtree of directories and files beneath a specific directory on the export server.
Replicate only specific files contained in the subtree by applying locks to its directories and files to prevent them from being exported.
By default, the export directory in which the master copy of the replicated data is contained is located in the following path:
%SystemRoot%\system32\repl\export
The default path to which the directory structure is imported on the import server follows:
%SystemRoot%\system32\repl\import
NOTE
Do not use directory replication as a substitute for a regular program of tape backups. The Directory Replicator Service can create a lot of network traffic and should not be used for backing up data across a network. If the data you are replicating contains large files that change frequently, replication traffic can cause network congestion unless you watch it carefully. Be especially careful when you replicate directory structures over slower WAN links to avoid congestion that interferes with other essential forms of traffic such as logon traffic.
TIP
The Directory Replicator Service on Windows NT can export only one directory tree from a given export server. It is a good idea to leave the default export location as it is and move the directory structure and information you want to replicate to this default export location. This allows you to also replicate logon scripts because by default these are located on a PDC in the location
%SystemRoot%\system32\repl\export\scripts
and on a BDC in the location
%SystemRoot%\system32\repl\import
Since these script directories are located within the default export and import paths, they can be replicated along with other data.
A Microsoft Windows NT and Windows 2000 service for replicating files and folders over the network. The Directory Replicator Service simplifies the task of updating key network configuration files needed by all users, such as system policies and logon scripts. You can also use directory replication to load balance between multiple servers when a large number of users need access to specific files or folders.
Graphic D-26. Directory Replicator Service.
How It Works
The Directory Replicator Service replicates files from an export computer to an import computer. The export computer must be running the Windows NT Server operating system, but the import computer can run Windows NT Server, Windows NT Workstation, or LAN Manager for OS/2 servers.
The files and folders to be replicated must be placed in subdirectories of the REPL$ administrative share located at %SystemRoot%\system32\repl\export. (The export folder is shared when the Directory Replicator Service is started using the Services utility in Control Panel.) These subdirectories are automatically exported to the %SystemRoot%\system32\repl\import directory on the import computer.
Use the Windows NT administrative tool Server Manager to configure directory replication.
A tool for locating, managing, and organizing network resources, which can include volumes, folders, files, printers, users, groups, and other objects. A directory service is a core component of a network operating system (NOS) and functions much like the yellow pages of a phone book. For example, if you look up “printers,” you’ll find a list of available printers and information for accessing them. However, for a directory service to function like a network yellow pages, it must be combined with a complementary entity, the directory database.
The directory database is the hierarchical database structure that contains the actual information about the various resources on the network. In other words, you need a directory database, which contains the directory information, and a directory service, which allows you to search for and locate information stored in the directory. For simplicity, however, the terms “directory” and “directory service” are often used to refer to the combination of directory and directory service.
Examples of directory services produced by different vendors and standards bodies include the following:
Windows NT Directory Services (NTDS) for Windows NT
Active Directory for Windows 2000
Novell Directory Services (NDS) for Novell NetWare version 4.x
X.500, an International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) standard for directory services
An enterprise-level directory service (a service suitable for an enterprise-level network with thousands of users that is spread over a large geographical area) has the following essential characteristics:
It is scalable so that it can grow to accommodate information and provide services as the enterprise itself grows.
It is extensible with a schema that can be modified by adding new classes, objects, and attributes.
It provides simple ways of finding directory objects that are based on industry standards such as X.500, Lightweight Directory Access Protocol (LDAP), and Domain Name System (DNS).
It can be administered from a single point on the network.
Active Directory for Windows 2000 satisfies all these conditions.
See also Active Directory, directory database
A log that contains events written by Active Directory on machines running Microsoft Windows 2000. The directory service log exists only on domain controllers because these are the only computers that have copies of Active Directory. The directory service log contains events such as informational, warning, and error events concerning operations that have been performed on or by Active Directory. These events reveal the state of Active Directory and can be used for diagnostic and troubleshooting purposes.
Information in the directory service log can be displayed using Event Viewer, a Windows 2000 administrative tool that runs as a snap-in for the Microsoft Management Console (MMC). Event Viewer for Windows 2000 supports a number of different kinds of logs in addition to the three supported in the Windows NT version of Event Viewer, namely the system log, security log, and application log. The actual types of event logs available in Windows 2000 Event Viewer depend on which optional networking components are installed on the machine.
An add-on utility for Microsoft Windows NT Server. Directory Service Manager for NetWare (DSMN) enables Windows NT domain controllers to manage account information on NetWare 2.x , 3.x , and 4.x servers. It does this by copying NetWare account information to the primary domain controller (PDC) and then propagating changes back to the bindery on the NetWare servers. DSMN also synchronizes accounts across all NetWare servers, allowing users to access any NetWare server using a single logon username. DSMN does not come with Windows NT but can be ordered separately from your Microsoft value-added reseller (VAR).
NOTE
DSMN supports NetWare 4.x servers only when they are running in bindery emulation mode, not in Novell Directory Services (NDS) mode.
A proposed specification based on XML (Extensible Markup Language) that will enable directory systems to share information. The Directory Service Markup Language (DSML) schema for XML provides mechanisms for accessing information in directories even if the format of the data is unknown. The DSML working group is open; it includes IBM, Novell, and Oracle and is supported by other directory vendors, including Microsoft. A related initiative is the Directory Interoperability Forum (DIF), whose aim is to establish a standard that will enable use of the Lightweight Directory Access Protocol (LDAP) for performing data queries across multiple directories. DSML and DIF are separate initiatives, but they might eventually merge or be subsumed within a wider objective.
On the Web
•
DSML working group : http://www.dsml.org
The process whereby the domain directory databases of backup domain controllers (BDCs) in a Microsoft Windows NT domain are synchronized with the master directory database on the primary domain controller (PDC). Accurate and reliable directory synchronization is the foundation for effective operation of Windows NT Directory Services (NTDS).
TIP
If directory synchronization must be performed over slow WAN links, you can adjust some registry parameters to make directory synchronization more efficient and prevent it from consuming excessive bandwidth. For more information, see the Microsoft Official Curriculum (MOC) course MS 689: Microsoft Windows NT Server 4.0 Enterprise Technologies.
See also domain controller
The process by which information stored in Microsoft Mail 3.x mail systems is replicated between postoffices. There is only one directory server postoffice in a Microsoft Mail 3. x mail system; other postoffices that participate in directory synchronization are called requestor postoffices. Requestor postoffices send their address list updates to the directory server postoffice, which then sends cumulative changes back to the requestor postoffice. Directory synchronization also ensures that the global address list is updated.
Any process used for exchanging directory information between directory services implemented by different vendors or on different platforms. For example, the exchange of directory information between Active Directory in Microsoft Windows 2000 and Novell Directory Services (NDS) in Novell NetWare takes place using directory synchronization. Directory synchronization is different from directory replication, which always takes place between directory services from the same vendor or on the same platform. For example, domain controllers in a Windows 2000–based network maintain Active Directory by exchanging directory updates using directory replication.
NOTE
Microsoft provides special directory synchronization agents that support the exchange of directory information between Active Directory and NDS. It also provides an agent for synchronizing Microsoft Exchange Server directory services with Active Directory. The Microsoft Exchange directory service is based on the Lightweight Directory Access Protocol (LDAP).
One of two popular spread spectrum transmission technologies for wireless networking, the other being frequency hopping. Direct sequencing can be used for both wireless local area network (LAN) connections and as part of a cellular telephone technology.
How It Works
Direct sequencing systems transmit data 1 bit at a time instead of packaging data into multibit packets, as in frequency hopping. Each bit of data is transmitted simultaneously over a range of frequencies in the 902 to 928–MHz frequency band. Spreading the data over multiple frequencies reduces signal loss due to noise and interference.
In direct sequencing, the transmitter feeds each bit of the data stream into a signal spreader that multiplies the input, creating a wideband signal. The wideband signal is then amplified and broadcast by using an antenna.
Graphic D-27. Direct sequencing.
Direct sequencing has a faster theoretical maximum data transmission rate than frequency hopping, but in practice the two methods provide similar throughput for wireless transmission of data because of protocol overhead in typical wireless communication systems.
See also spread spectrum, wireless networking
In Microsoft Windows 2000, an internal list attached to an object in Active Directory that specifies which users and groups can access the object and what kinds of operations they can perform on the object. In Windows 2000 and Windows NT, an internal list attached to a file or folder on a volume formatted using the NTFS that has a similar function.
How It Works
In Windows 2000, each object in Active Directory or a local NTFS volume has an attribute called Security Descriptor that stores information about
The object’s owner (the security identifier or the owner) and the groups to which the owner belongs.
The discretionary access control list (DACL) of the object, which lists the security principals (users, groups, and computers) that have access to the object and their level of access.
The system access control list (SACL), which lists the security principals that should trigger audit events when accessing the list.
The DACL for an object specifies the list of users and groups that are authorized to access the object and also what levels of access they have. The kinds of access that can be assigned to an object depend on the type of object under consideration. For example, a file object can have read access assigned to a user but a printer object cannot. (You can’t read a printer!)
The DACL for an object consists of a list of access control entries (ACEs). A given ACE applies to a class of objects, an object, or an attribute of an object. Each ACE specifies the security identifier (SID) of the security principal to which the ACE applies, as well as the level of access to the object permitted for the security principal. For example, a user or group might have permission to modify all or some of the attributes of the object, or might not even have permission to be aware of the object’s existence. In common parlance, DACLs are sometimes simply referred to as access control lists or ACLs, though this is not strictly correct.
NOTE
The owner of an object always has permission to modify its DACL by granting permissions to other users and groups.
See also access control, access control entry (ACE), access control list (ACL), system access control list (SACL)
A Microsoft Windows NT administrative tool used for managing hard drives.
You can use Disk Administrator to
Create, delete, and format partitions, volume sets, and stripe sets
Mark partitions as active
Assign drive letters and volume labels
Create mirror sets and stripe sets with parity
NOTE
In Windows 2000, the Disk Administrator tool is part of the Storage tools within the Computer Management tool.
Graphic D-28. Disk Administrator.
A utility included with Microsoft Windows 98 that helps you reclaim space on your hard drive by deleting files you no longer need. You can use Disk Cleanup to select the types of files to uninstall and to inspect and remove files in the Recycle Bin, temporary files, Internet cache files, and unneeded Microsoft ActiveX components. You can also use Disk Cleanup to remove optional Windows components that you no longer need, remove programs that you installed, and convert a FAT16 partition to FAT32.
NOTE
You can configure Disk Cleanup to automatically run when your disk is low on space.
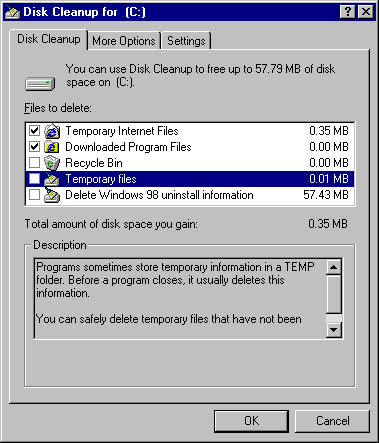
Graphic D-29. Disk Cleanup.
A utility included with Microsoft Windows 95, Windows 98, and Windows 2000 that can rearrange files on a hard drive to free up contiguous disk space and improve performance. The screen capture shows the Windows 95 and Windows 98 Disk Defragmenter at work.
How It Works
Disk Defragmenter examines a drive for fragmented files, which are files whose data is scattered over different parts of the drive. Fragmentation occurs as files are deleted and created on a drive. Fragmentation slows down read/write disk operations. Disk Defragmenter moves the pieces of fragmented files to a single, contiguous location on the drive. This allows the files to be accessed more efficiently.
Graphic D-30. Disk Defragmenter.
On machines running Windows 2000, you can use Disk Defragmenter to defragment FAT16, FAT32, and NTFS volumes.
NOTE
Disk Defragmenter does not move files that have both hidden and system attributes or mounted compressed volume files.
TIP
The Disk Defragmenter tool for Windows 2000 runs as a snap-in for Microsoft Management Console (MMC).
A fault tolerant disk technology supported by Microsoft Windows NT Server. Disk duplexing is essentially the same as disk mirroring, except that a separate disk drive controller is used for each mirrored drive to provide additional fault tolerance. This provides two levels of fault tolerance:
If one drive fails, the other contains a mirrored copy of the data.
If one controller fails, the other controller continues to function.
You can establish disk duplexing on Windows NT systems at the partition level. In terms of system recovery and management, there is no difference between disk mirroring and disk duplexing.
A Microsoft Windows NT and Windows 2000 command for starting and stopping disk performance counters for Performance Monitor (System Monitor in Windows 2000). Counters for the objects Logical Disk (partition) and Physical Disk (drive) are disabled by default because a performance hit of a few percent can occur if they are enabled. You must run the diskperf command prior to monitoring disk activity with Performance Monitor. On some disk subsystems, enabling these counters might produce a small decrease in system performance, so you should disable them when monitoring of the system is completed. You must reboot the system after running diskperf.
Example
diskperf –n sets the system to not use any disk performance counters.
For the full syntax of this command, type diskperf /? on the command line.
A feature of Microsoft Windows 2000 that administrators can use to track and control disk usage on a per-user basis for each NTFS file system volume that the user stores data on.
Depending on how disk quotas are configured, when a user exceeds the specified disk limit, one of two things can occur:
An event is logged to the system log.
Disk access is blocked and an event is logged. The user is presented with an “insufficient disk space” error.
How It Works
Support for disk quotas is built into the new version of NTFS on Windows 2000. Disk quotas are tracked independently for each NTFS volume even if several volumes are on the same physical disk. For purposes of managing disk quotas for users, disk space usage is based on file and folder ownership. Windows 2000 ignores compression when it calculates how much disk space a user is utilizing. Whatever is unallocated in a user’s disk quota is reported as free space for applications that allow the user to access disk space.
You use the Quota tab on the property sheet for an NTFS volume to enable disk quotas, set quota limits, and specify what happens when users exceed their quotas. To configure disk quotas for users, you essentially specify two values:
Quota limit: How much disk space the user is allowed to use
Quota threshold: The conditions under which an event should be logged to indicate that the user is nearing his or her quota limit
For example, if the quota limit for a user is set to 10 MB while the quota threshold is specified as 8 MB, an event is logged when the user stores more than 8 MB of data on the volume, and the user is prevented from storing more than 10 MB of data on the volume.
To view the status of disk quotas on an NTFS volume for which this feature has been enabled, open the volume’s property sheet and examine the traffic light icon. The light is
Red if quotas are disabled
Yellow if the NTFS file system is recalculating the status of quota compliance
Green if quotas are enabled
NOTE
Disk quotas are specified on a per-volume basis. That is, disk usage is tracked independently for different volumes.
Graphic D-31. Disk quotas.
TIP
If you want to track disk usage by user but don’t want to deny users access to a volume, you can enable disk quotas but specify that users can exceed their disk quota limit. Note also that enabling disk quotas incurs slight overhead in file system performance.
To use disk quotas on an NTFS volume, enable this feature when the volume is created and before any users have access to it. Begin by setting more restrictive settings for all users, and then relax these settings for users who need more disk space or work with large files.
In the Disk Management portion of the Computer Management tool of Microsoft Windows 2000, information about whether the disk is healthy or has a problem. The Status column can show the status indicators given in the following table. The letter “B” indicates that the status indicator can apply to basic disks, and “D” indicates dynamic disks.
Disk Status
| Disk Status | Description/Prescription |
| Online (BD) | The disk is accessible. There are no problems. |
| Online—Errors (D) | I/O errors detected. Try reactivating the disk to see whether the errors are transient. |
| Offline (D) | The disk is not accessible and might be corrupted, disconnected, or powered down. Try reactivating the disk, and check the cables and the controller. |
| Foreign (D) | The disk has been moved to this machine from another computer running Windows 2000. You must import the foreign disk before you can use it. |
| Unreadable (BD) | The disk is not accessible and might be corrupted, have I/O errors, or hardware failure. Try rescanning the disk or rebooting the system to see whether it recovers. |
| Unrecognized | The disk type is unknown, and the disk is probably from a different operating system, such as UNIX. |
| No Media | The drive is either a CD-ROM drive or some type of removable drive and has no media in it. |
Also called the Bellman-Ford algorithm, a routing algorithm in which every router maintains a database with one entry for each possible destination on the network. The Routing Information Protocol (RIP), which is supported by Microsoft Windows NT and Windows 2000, is one example of a dynamic routing protocol that uses the distance vector routing algorithm.
How It Works
When this algorithm is used by a routing protocol, each router advertises its routing table to its adjacent neighbors. Each advertisement contains the following information about each route in that routing table:
The hop count for the route (the distance)
The direction in which the route is located (the vector)
These advertisements are performed independently by all routers (that is, no synchronization exists between advertisements made by different routers). In addition, routers receiving advertisements do not generate acknowledgments, which reduces the overhead of routing protocol traffic.
Routers select the route with the lowest cost to each possible destination and add this to their own routing tables. These neighbors propagate the information to their neighbors hop by hop until information from all routers has spread throughout the entire internetwork.
Distance vector routing protocols (that is, protocols based on the distance vector routing algorithm) are simpler to understand and easier to configure than link state routing algorithm protocols. The main disadvantage of the distance vector routing algorithm is that changes are propagated very slowly throughout a large internetwork because all routing tables must be recalculated. This is called the Slow Convergence Problem. Other disadvantages are that routing tables can become extremely large, making distance vector routing protocols unsuitable for large internetworks, and that route advertising generates a large amount of traffic overhead.
The following table shows correspondence between routable network protocols and distance vector routing protocols.
Correspondence Between Protocols
| Network Protocol | Distance Vector Routing Protocol |
| IP | RIP or Interior Gateway Routing Protocol (IGRP) |
| IPX | RIP |
| AppleTalk | RTMP |
NOTE
Windows NT Server version 4 supports RIP version 1 for Internet Protocol (IP), RIP for Internetwork Packet Exchange (IPX), and Routing Table Maintenance Protocol (RTMP) for AppleTalk. Windows NT Server version 4 with Microsoft’s Routing and Remote Access Service (RRAS) installed supports RIP version 2 for IP.
See also link state routing algorithm
The native address format for recipients in Microsoft Exchange Server. Also, one of the addressing formats for objects within Active Directory in Microsoft Windows 2000. Distinguished names are part of the X.500 directory specifications and are used for locating and accessing objects using the Lightweight Directory Access Protocol (LDAP).
How It Works
In Active Directory for Windows 2000, every object in the directory has a unique name. Three kinds of names can be used to define a specific object in Active Directory:
A distinguished name, which specifies the complete path to the object through the hierarchy of containers
A relative distinguished name (RDN), which is the portion of the name that is an attribute of the object itself
A user principal name (UPN), which is the name used when a user logs on to the network
For example, consider a user object within Active Directory. A user object is an example of a leaf object because it cannot contain other objects. User objects such as Jeff Smith are identified using common names (CNs). A container is a directory object that can contain other objects. In Active Directory, containers are referred to as organizational units (OUs) because they are used to organize other objects into hierarchies of containers. For example, the user Jeff Smith would typically be contained within the Users container. At the top of the container hierarchy are the containers that represent different components of the domain itself. These components are called domain components (DCs). For example, if user Jeff Smith exists in the microsoft.com domain, the distinguished name for this user is represented by the path
DC=com,DC=microsoft,OU=Users,CN=Jeff Smith
In Microsoft Exchange Server, distinguished names are used to identify recipients. Exchange automatically creates a distinguished name for every recipient object in its directory database, including objects such as mailboxes, distribution lists, and public folders. For example, if a user Jeff Smith has a mailbox named JeffS located on an Exchange server in Redmond at the organization Microsoft, the distinguished name for this user would be represented internally as
O=Microsoft,OU=Redmond,CN=Recipients,CN=JeffS
The Message Transfer Agent (MTA) uses a recipient’s distinguished name to determine how to route messages to that recipient within an Exchange organization.
TIP
Exchange Server also automatically generates X.400 addresses for every object in the directory. Don’t delete these addresses, even if you have no X.400 Connectors installed in your sites, because if Exchange Server cannot use a recipient’s distinguished name for any reason, it uses the recipient’s X.400 address for message routing.
An application consisting of two or more parts that run on different machines but act together seamlessly. In the simplest scenario, the user interface part runs on a client machine, while the processor-intensive or storage-intensive part runs on a server. This type of distributed application is called a client/server application. Examples include the following:
Microsoft Exchange Server (back end) as a mail server with users running Microsoft Outlook (front end) on their client machines
Microsoft Access (front end) as an interface for accessing database information stored in Microsoft SQL Server (back end)
A Web application written using Active Server Pages (ASP) for Internet Information Services (IIS) (back end) that is accessed from a client machine running Microsoft Internet Explorer (front end)
NOTE
Microsoft Windows operating systems use interprocess communication (IPC) to enable seamless communication between the client and server parts of distributed applications.
A technology for component-based development of software that is network-aware. Using Distributed Component Object Model (DCOM), developers can create network-aware applications using Component Object Model (COM) components. DCOM works under various network transports, including TCP/IP.
How It Works
DCOM is a client/server protocol that provides distributed network services to COM, allowing DCOM-enabled software components to communicate over a network in a similar fashion to the method by which COM components communicate among themselves on a single machine. DCOM client objects make requests for services from DCOM server objects on different machines on the network using a standard set of interfaces.
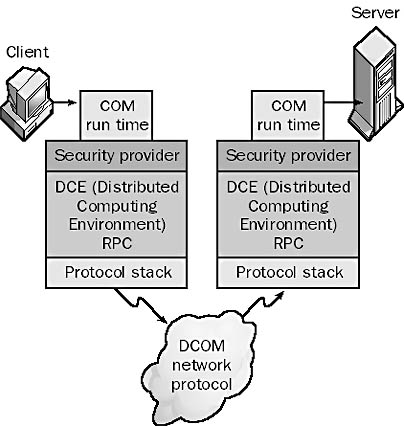
Graphic D-32. Distributed Component Object Model (DCOM).
The client object cannot call the server object directly. Instead, the operating system intercepts the DCOM request and uses interprocess communication mechanisms such as remote procedure calls (RPCs) to provide a transparent communication mechanism between the client and server objects. The COM run time provides the necessary object-oriented services to the client and server objects. The COM run time also uses the security provider and RPCs to create network frames that conform to the DCOM standard.
In Microsoft Windows NT and Windows 2000, DCOM requests are sent using RPCs. Windows NT and Windows 2000 use security features such as permissions to enable software components to securely and reliably communicate over the network.
DCOM was formerly known as “Network OLE.”
See also Component Object Model (COM)
A separately available add-on for the Microsoft Windows NT operating system and a component of the Windows 2000 operating system. The Distributed file system (Dfs) allows file servers and network shares to be logically organized into a single Dfs directory tree. This simplifies management of network resources and makes it easier for users to locate and access network resources. From the user’s perspective, the Dfs makes it appear that there is only one server containing a hierarchical tree of resources, while in fact these resources might be distributed across multiple servers in different locations.
The Dfs simplifies directory browsing, offers search tools that simplify locating network resources, and offers administrative tools for building and managing Dfs directory trees. It also eliminates the need for Windows 95, Windows 98, or Windows NT Workstation clients to form multiple persistent network connections, because users require only one persistent connection to the directory tree.
How It Works
In the Windows 2000 implementation, you first open the Dfs snap-in for Microsoft Management Console (MMC) to create a Dfs root node. You can then create Dfs child nodes under the root node. Each child represents a shared folder that can be located anywhere on the network. When users want to access a resource on the network, they navigate through the Dfs tree and do not need to know the particular server the resource is located on. Users must have Dfs client software installed on their machines. Dfs client software is included with Windows 2000, Windows NT, and Windows 98. An optional Dfs client can be downloaded for Windows 95 from the Microsoft Web site.
You can configure Dfs to operate in two ways:
Stand-alone Dfs stores the description of the Dfs file system topology on a single computer. If that computer fails, the entire Dfs system goes down, although users can still access resources the traditional way using mapped network drives or Universal Naming Convention (UNC) paths if they know which servers these resources are stored on and the names of the shares.
Fault tolerant Dfs stores the Dfs topology information in Active Directory on Windows 2000 domain controllers. This configuration is better for fault tolerance and file replication.
TIP
If a server containing Dfs shares fails, you can simply move the files to another machine, create new shares, and map the existing Dfs child nodes to the new shares. Your users won’t even know that anything has changed. If you assign a user permission to access a shared folder, that person automatically has permission to access it through the Dfs tree as well.
A fixed or free-standing miniature patch panel in an enclosure. Typically, horizontal cable runs are connected to the punchdown blocks within the distribution box, and drop cables are plugged into the RJ-45 ports of the box. You can thus use distribution boxes to provide central cabling points away from walls. Stations can then be plugged and unplugged from an accessible location in the work area instead of from the back of the workstations (after you bend down and crawl behind the machine) or from the land drops in the wall (which are often hidden behind desks or other obstacles).
TIP
Use distribution boxes for classrooms and work areas in which computers frequently need to be moved around and rearranged.
One of two types of groups within Active Directory in Microsoft Windows 2000. The other type is security groups. While security groups can be listed in discretionary access control lists (DACLs) for controlling access to resources or sending e-mail to users, distribution groups can be used only for e-mail purposes. By sending e-mail to a distribution group, you send e-mail to every member of that group.
Distribution groups can be converted to security groups and vice versa as long as the domain is in native mode. You cannot perform conversion if the domain is in mixed mode.
A grouping of recipients in Microsoft Exchange Server that you can use to send a single message to multiple users simultaneously. When a message is sent to a distribution list, it is sent to all recipients on the list. Distribution lists provide a convenient way of performing mass mailings to users. For example, a marketing department might create several hundred custom recipients for regular customers outside the Exchange organization. These custom recipients can then be included as members within a single distribution list. When the department wants to send e-mail to its customers announcing new products or services, the e-mail can be sent to the distribution list. A computer running Exchange Server (configured to expand distribution lists) makes sure that each custom recipient receives a copy of the message.
Generally, any server that contains the source files for a software product and that is used to perform remote installations. For example, if you want to perform remote installations of Microsoft Windows NT Workstation on client machines, you can copy the I386 and Drvlib folders from the CD onto a folder called NTWKS on your file server, and then share this folder.
TIP
When you copy files from the CD to a folder on the server, use the xcopy command or, if you are using Windows Explorer, be sure to first choose Options from the View menu and select Show All Files. Otherwise, some hidden files will not be copied, and installation will fail.
See Data Link Control (DLC)
See dynamic-link library (DLL)
See Desktop Management Interface (DMI)
See Defense Messaging System (DMS)
See distinguished name
See Microsoft Windows Distributed interNet Applications (DNA) Architecture
See Domain Name System (DNS)
A client machine configured to send name resolution queries to a DNS server. A DNS client is also called a resolver. When a client needs to resolve a remote host’s name into its IP address, it sends a request to the DNS server, which returns the IP address of the remote host. DNS client software, which is built into most machines that have TCP/IP installed, enables the machines to issue DNS queries to name servers. For example, on Microsoft Windows platforms, the DNS client software makes possible the use of DNS names for browsing the Internet using Microsoft Internet Explorer.
TIP
In Windows operating systems, you must configure the IP address of the DNS server in the client’s TCP/IP property sheet in order for the DNS client software to work properly. With dial-up networking connections to the Internet, this information can be communicated to the client machine during negotiation of the Point-to-Point Protocol (PPP) connection with the Internet service provider (ISP).
A snap-in for the Microsoft Management Console (MMC) in Microsoft Windows 2000 that enables administrators to manage Windows 2000 Servers running as DNS servers. You can use the DNS console to
Create and maintain the DNS database of host name to IP address mappings
Create and manage zones of authority
Create start of authority (SOA), name server (NS), address (A), CNAME, and other resource records in the DNS database
View DNS server statistics
Control how zones are stored and replicated between DNS servers
Configure how DNS servers will process DNS queries and handle dynamic updates
Configure security for specific zones and resource records
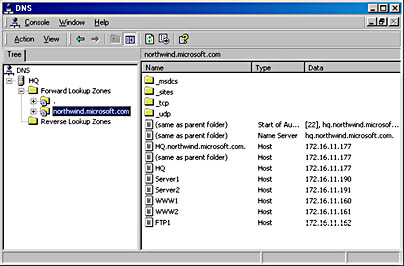
Graphic D-33. DNS console.
TIP
Windows 2000 Server includes a new command-line utility, dnscmd, which can be used for managing certain aspects of DNS servers. This utility can be run from the command prompt or scripted into batch files to automate certain aspects of DNS administration. To use this command you must install the Windows 2000 Support Tools from the \Support\Tools folder on the Windows 2000 product CD. Type dnscmd /? to see the syntax for this command.
See also DNS server, Domain Name System (DNS)
The collection of database files, or zone files, and associated files that contain resource records for a domain. These files are stored on a name server. DNS database files are typically flat-file database files in the form of simple ASCII files.
On a Microsoft Windows NT server with the Microsoft DNS Service installed, these database files are located in the \System32\DNS directory. The DNS database files in this directory are
The zone file, which has the extension .dns and contains the resource records that the DNS server manages
The reverse lookup file, which resolves IP addresses into host names
The cache file, which has the names and IP addresses of the root name servers for DNS
The boot file, which is used for startup configuration of the DNS server and is needed only for resolving the names of hosts that are located outside the zones for which the DNS server is authoritative
On a Windows 2000 DNS server, DNS database information can be either stored in the preceding standard text files or integrated into Active Directory, depending on how DNS is installed and configured on the machine. Using Active Directory for storing DNS database information has the benefits of Active Directory’s enhanced security features and multimaster replication, providing faster and more efficient replication of DNS zone information than using standard DNS text files.
See also Domain Name System (DNS)
A Microsoft Windows NT administrative tool for managing the Microsoft DNS Service on a Windows NT server. You can use DNS Manager to
Create and maintain the DNS database of host name to IP address mappings
Create and manage zones of authority
Create start of authority (SOA), name server (NS), address (A), CNAME, and other resource records in the DNS database
View DNS server statistics
See also DNS server, Domain Name System (DNS)
All domains and subdomains within the Domain Name System (DNS). DNS uses a namespace that is hierarchical in structure and is stored as a distributed database on servers called name servers. The term “namespace” can have two meanings:
The abstract space of fully qualified domain names (FQDNs) that are used to identify hosts on the Internet or on a private corporate TCP/IP internetwork
The physical space of DNS database files (zone files) that exist on name servers and that actually define or contain the abstract DNS namespace
Active Directory in Microsoft Windows 2000 requires that a DNS namespace be configured in a domain-based implementation of Windows 2000 in an enterprise.
See also Domain Name System (DNS)
One of three methods of requesting that name servers handle name lookups. DNS queries can occur between resolvers and name servers, and between name servers and other name servers. Queries can be answered by the queried name server from its local DNS database, from previously cached query results, or from a referral to another name server. The three basic kinds of DNS queries are recursive queries, iterative queries, and inverse queries.
For more information on these types of DNS queries, see their respective entries in this work.
See also Domain Name System (DNS), host name resolution
A server that is used to resolve host names or fully qualified domain names (FQDNs) into IP addresses on a TCP/IP network. A DNS server, which is also called a name server, accomplishes this by accepting DNS queries from DNS clients and by performing DNS queries among other DNS servers, depending on how the servers have been configured.
Microsoft Windows 2000 Server can function as a DNS server and is managed using an administrative tool, DNS console, which is a snap-in for the Microsoft Management Console (MMC). Windows NT Server can also function as a DNS server and is managed using an administrative tool, DNS Manager. Windows 2000 DNS servers include additional capabilities not supported by their Windows NT counterparts, such as dynamic update, which allows DNS servers to update their DNS database files automatically using Dynamic Host Configuration Protocol (DHCP).
Another feature of Windows 2000 is tight integration of DNS and Active Directory. For example, when a Windows 2000 client needs to locate a Windows 2000 domain controller, the NetLogon service uses the DNS server’s support for the SRV (service) resource record to allow registration of domain controllers in the local DNS namespace.
TIP
DNS servers can provide a simple means of load balancing connections to heavily used file or application servers such as Internet Information Services (IIS). The method is called Round Robin DNS, and it works as its name implies. Say you have three Web servers hosting identical content and you want to load balance incoming Hypertext Transfer Protocol (HTTP) requests across these servers. You can create three A records in the DNS zone file, each with the same host name but different IP addresses, one IP address for each Web server, as shown in this example:
www.northwind.microsoft.com 172.16.8.33 www.northwind.microsoft.com 172.16.8.34 www.northwind.microsoft.com 172.16.8.35
When a DNS client requests resolution of the name www.northwind.microsoft.com into its IP address, the DNS server returns all three IP addresses (.33, .34, .35), and the client chooses the first address (.33) and sends the HTTP request to the Web server associated with this address. The next time the DNS server receives the same name resolution request, it rotates the IP addresses in round-robin fashion (.34, .35, .33) and returns them to the client. The client picks the first address, which is now .34. This way, each DNS name resolution returns a different IP address and the load is balanced between the Web servers.
The drawback to using Round Robin DNS is that if a server fails, DNS will continue to return the address of the failed server.
See also DNS Manager, Domain Name System (DNS)
See zone
A built-in group on Microsoft Windows NT and Windows 2000 networks. The Domain Admins group simplifies administration of users on the network. It is a global group and does not have any preassigned system rights. The initial membership of the group is the sole user account called Administrator. Other user accounts that are added to this group gain rights and privileges equivalent to those of the Administrator account and can perform actions similar to those of the Administrator account. All network administrators in a given domain should be members of this group.
NOTE
On Windows 2000–based networks, the Domain Admins group is created by default in the Users organizational unit (OU) within Active Directory.
See also built-in group
A security technology introduced with Microsoft Internet Information Server version 4. Domain blocking allows Internet Information Server administrators to grant or deny access to content on the server based on a client’s IP address, subnet, or Internet domain name. This is a useful security feature for protecting machines running Internet Information Server from repeated attack by hackers. Domain blocking can be applied at various levels, including the following:
All virtual servers on the machine (master level)
A specific virtual server
A specific virtual directory
A specific file
A Microsoft Windows NT or Windows 2000 server that manages the domain security policy. Users and computers that need to obtain access to network resources within the domain must be authenticated by a domain controller in the domain. Windows NT domain controllers are the foundation of Windows NT Directory Services (NTDS), while Windows 2000 domain controllers are based on Active Directory.
In a Windows NT–based network, the domain controllers form a hierarchy. There are two types of Windows NT domain controller:
The primary domain controller (PDC), which contains a writable master copy of the domain directory database. A domain can have only one PDC, which is at the top of the domain controller hierarchy. All changes to directory information (such as user accounts or passwords) must be made on the PDC.
The backup domain controller (BDC), which contains read-only replicas of the domain directory database stored on the PDC. There can be zero or more BDCs per domain. BDCs provide redundancy and load balancing for the domain. Periodically, the BDCs in a domain undergo directory synchronization with the PDC to ensure that the BDCs contain an accurate copy of the domain directory database. This replication ensures the proper functioning of the NTDS.
A Windows 2000 domain controller is any Windows 2000 server with the optional Active Directory service installed. Windows 2000 domain controllers contain a complete, writable copy of the Active Directory information for the domain in which they are installed. Run the Active Directory Installation Wizard to promote any Windows 2000 member server to the role of a domain controller. A domain controller manages information in the Active Directory database and enables users to log on to the domain, be authenticated for accessing resources in the domain, and search the directory for information about users and network resources. A Windows 2000 domain controller contains a writable copy of the domain directory database.
Unlike in a Windows NT–based network, where domain controllers are in a hierarchy, all domain controllers in a Windows 2000–based network are equal, and changes to the domain directory database can be made at any domain controller. Replication of directory information between Windows 2000 domain controllers follows a multimaster model. In this configuration, each domain controller acts as a peer to all other domain controllers. In other words, there are no primary or backup domain controllers in Windows 2000, only domain controllers.
In a pure Windows 2000 networking environment, all domain controllers can be configured to run in native mode. If you have a mix of Windows NT 4 and Windows 2000 domain controllers, the Windows 2000 domain controllers must be configured to run in mixed mode.
NOTE
If you need to move a Windows NT domain controller to a new domain, you must reinstall Windows NT. Domain controllers cannot migrate from one domain to another because when you create a domain, a unique security identifier (SID) is created to identify the domain, and domain controllers have this SID hard-coded into their domain directory database.
You can use the administrative tool Active Directory Users and Computers to convert a Windows 2000 domain controller from mixed mode to native mode. However, domain controllers running in native mode cannot be changed to mixed mode. If you create a new domain controller for an existing Windows 2000 domain, this new domain controller is referred to as a replica domain controller. Replica domain controllers are typically created to provide fault tolerance and better support for users who access resources over the network.
TIP
To upgrade a Windows NT–based network to Windows 2000, upgrade the PDC first. This allows the domain to immediately join a domain tree, and administrators can administer the domain using the administrative tools of Windows 2000 and create and configure objects in Active Directory.
An important issue regarding domain controllers in Windows 2000–based networks is where to place them. After an administrator implements Active Directory and populates its initial information, most Active Directory–related traffic will come from users querying for network resources. The key to optimizing user queries is in how you locate the domain controllers and the global catalog servers on your network. Placing a domain controller at each physical site optimizes query traffic but increases replication traffic between sites. Nevertheless, the best configuration is usually to place at least one domain controller at each site with a significant number of users and computers.
See also Active Directory, domain modes
In Microsoft Windows 2000, a logical structure formed by combining two or more domain trees.
How It Works
Forests provide a way of administering enterprise networks for a company whose subsidiaries each manage their own network users and resources. For example, a company called CarPoint might have a domain tree with the root domain carpoint.com, while a subsidiary company called Expedia might have a domain tree with the root domain expedia.com. Note that these two companies do not share a contiguous portion of the DNS namespace; this is typical of trees in a forest. The two companies might want to administer their own users and resources but make those resources available to each other’s users. They can combine the two domain trees into a forest by establishing a two-way transitive trust between the root domains of the two trees.
Graphic D-34. Domain forest.
All trees in a forest must share a common directory schema and global catalog. The global catalog holds information about all objects in all domains of the forest and acts as an index of all users and resources for all domains in the forest. By searching the global catalog, a user in one domain can locate resources anywhere in the forest. The global catalog contains only a subset of the attributes of each object. This ensures fast searches for users trying to locate network resources.
A built-in group on Microsoft Windows NT and Windows 2000 networks. The Domain Guests group simplifies administration of users on the network. It is a global group and does not have any preassigned system rights. The initial membership of the Domain Guests group is the sole user account called Guest. Other user accounts that are added to this group gain the rights and privileges equivalent to those of the Guest account and can perform actions similar to those of the Guest account. Domain Guests are typically users who are given occasional, temporary access to network resources.
NOTE
On Windows 2000–based networks, the Domain Guests group is created by default in the Users organizational unit (OU) within Active Directory. Normally, the only member of this group is the Guest account, but on a Windows NT server with Internet Information Services (IIS) installed, additional guest accounts are created for use by IIS.
See also built-in group
A grouping of TCP/IP hosts in the hierarchical Domain Name System (DNS). Domains are the building blocks of DNS. A domain consists of a group of nodes in the DNS namespace. Domains are organized hierarchically in the DNS namespace, with the topmost domain called the root domain.
DNS domains can be classified as one of the following:
A parent domain, which contains other domains. An example of a parent domain is microsoft.com.
A child domain, or subdomain, which is contained within a parent domain. Examples of child domains in the microsoft.com parent domain are northwind.microsoft.com and marketing.microsoft.com.
NOTE
Domain names can include only the characters a–z, A–Z, and 0–9, the dash (-), and the period. A name that completely identifies a host in the DNS namespace is called a fully qualified domain name (FQDN).
See also Domain Name System (DNS)
A network security model for grouping computers together. Computers on a network based on Microsoft Windows NT or Windows 2000 that are in the same domain share a common directory database of security information such as user accounts, passwords, and password policies. Domain-based networks have the following features:
Centralized administration: The entire network can be administered from a single location.
Single-user logon: Users need only one user account to access any workstation on the network.
Universal resource access: Users can access any network resource for which they have the appropriate permissions.
Graphic D-35. This shows a Windows 2000 domain.
How It Works
Typically, the following computers are members of the domain:
Domain controllers, which maintain the database of directory information for the domain. On Windows NT servers, this database is called the Security Accounts Manager (SAM) database, while in Windows 2000 domains, this information is stored in Active Directory. Domain controllers periodically exchange directory information using directory replication so that the information in any given domain controller is kept up to date. (If the information stored in a domain controller is out of date, users might have trouble logging on with that particular domain controller or finding recently shared resources on the network.)
Member servers, which are stand-alone servers typically used for file and print services, Web services, or running applications such as Microsoft SQL Server. Member servers cannot authenticate users like domain controllers can.
Workstations or client computers, which participate in the security policies of the domain and are members of the domain, but are used as desktop machines for users instead of as network servers.
A Windows NT or Windows 2000 network can be installed as either a domain or a workgroup. The domain model is preferable because it allows computers to share a common security policy and a common domain directory database. Machines running Windows 98 and legacy Windows machines can also participate in domain security on Windows NT and Windows 2000 networks but are not considered full members of the domain because they have no computer accounts within the domain directory database.
A Windows NT domain requires only one primary domain controller (PDC) and can have a number of backup domain controllers (BDCs). By creating a PDC, you create a new domain. Windows NT member servers and workstations can join a domain. Other systems, such as computers running Windows 95 and Windows 98, can participate in a domain but are not considered members of the domain because they have no computer accounts in the domain directory database.
Windows 2000 domains use peer domain controllers, which are all equal in status. In Windows 2000, domains are core entities within Active Directory and act as a boundary for network security and for the replication of directory information over the network. If you establish a security policy in one domain, the settings, rights, and discretionary access control lists (DACLs) of that policy are limited to that domain. Domains are also the fundamental containers for all network objects within them. Domains contain users, groups, computers, and other directory objects. These objects can be grouped together using a hierarchy of organizational units (OUs).
NOTE
Domains can span geographical boundaries and networks; an enterprise can have branches in several continents with all machines belonging to a single domain. Alternatively, a single network or location can have multiple domains installed, with or without trust relationships between them.
NOTE
To change the name of a domain in Windows NT, you first change it on the PDC and then on the other machines in the domain. However, this can affect other software installed on the servers.
See also Active Directory, domain controller, trust relationship, workgroup
A type of group in a Microsoft Windows 2000–based network. Windows 2000 uses groups to organize users or computer objects for administrative purposes. Groups can have different scopes, or levels of functionality. The scope of a group can be a single domain, a group of domains connected by trust relationships, or the entire network.
Domain local groups are Windows 2000 groups whose scope is restricted to the specific domain in which they are defined. Domain local groups are used to provide users with access to network resources and to assign permissions to control access to these resources. Domain local groups have open membership, which means that you can add members from any domain to them.
To use a domain local group, you first determine which users have similar job responsibilities in your enterprise. Then you identify a common set of network resources in a domain that these users might need to access. Next, you create a domain local group for the users and assign the group appropriate permissions to the network resources. This procedure is called A-G-DL-P (access, group, domain local, permissions), which is a variation of the AGLP administration paradigm used in Windows NT–based networks.
TIP
If network resources within a domain are used only within the domain, you can group users in the domain using domain local groups. If your scope of resource usage is several domains linked by trust relationships, use global groups instead. If your network is a pure Windows 2000–based network and your domain controllers are running in native mode, you can use universal groups as well.
See also global group, universal group
One of the roles of machines running Microsoft Windows NT and Windows 2000 in supporting the computer browser service on a Windows NT–based or Windows 2000–based network. The domain master browser is a computer running Windows NT or Windows 2000 that collects the master list of domain resources on the network. It then distributes this list to master browsers on each subnet. If the domain has only one subnet, the domain master browser is also the master browser for that subnet.
NOTE
A Windows NT domain has only one domain master browser, which is always the primary domain controller (PDC).
See also Computer Browser service
A model for building an enterprise-level network using Microsoft Windows NT or Windows 2000 domains. Windows NT and Windows 2000 can be scaled for implementation in enterprise-level businesses that support thousands of users and cover geographically diverse regions. Choosing a correct domain model for implementing your Windows NT or Windows 2000 network can greatly simplify administration of your network. Some domain models are more suitable for smaller implementations, while others are better for larger networks.
Four main domain models can be implemented in a Windows NT network:
The single domain model, which keeps all machines in the network in a single domain and is usually implemented in smaller companies
The single master domain model, which separates resource domains from a master or accounts domain and is suitable for companies with a hierarchical organizational structure
The multiple master domain model, which uses multiple accounts or master domains and is suitable for large organizations that span different countries or continents
The complete trust model, which is used by very decentralized organizations or during the transition period when two companies merge
Because of its two-way transitive trusts between domains, Windows 2000 is capable of building more flexible domain structures. In addition to the single domain model, domains can be linked hierarchically in domain trees, and domain trees can be joined in domain forests. For more information on Windows 2000 domain models, see Microsoft Official Curriculum (MOC) course number 1561, Designing a Microsoft Windows 2000 Directory Services Infrastructure.
See also trust relationship
A mode of operation for domain controllers in Microsoft Windows 2000–based networks. Windows 2000 domain controllers are computers that contain a writable copy of Active Directory. You can convert a Windows 2000–based server to a domain controller by running the Active Directory Installation Wizard on that machine. You can run Windows 2000 domain controllers in either of two modes:
Mixed mode, which provides backward compatibility with Windows NT domain controllers (downlevel domain controllers). This mode supports networks with a mixture of Windows 2000 and Windows NT domain controllers and allows them to interoperate. Multimaster replication cannot be used in mixed mode environments.
Native mode, which interoperates only with other Windows 2000 domain controllers. Native mode should be used when there are no downlevel domain controllers on the network and the entire network has been upgraded to Windows 2000.
NOTE
By default, Active Directory is installed on a Windows 2000 server in mixed mode. You can change a domain controller from mixed mode to native mode, but not vice versa. Use the administrative tool Active Directory Users and Computers to perform the change.
A name for a domain within the Domain Name System (DNS), usually registered with the Internet Network Information Center (InterNIC)—for example, the microsoft.com domain owned by Microsoft Corporation.
Owning a domain name is essential in today’s business world, as the dot-com enterprise becomes the standard model for business. A company’s domain name typically reflects the company’s trademark name or logo. Because company names can be registered at the state or federal level, companies in different states or countries might want to register identical domain names. Unfortunately, the DNS was not established with consideration of these trademark issues, and the courtroom has become a common arena for resolving domain name ownership disputes.
See also fully qualified domain name (FQDN)
A hierarchical system for identifying hosts on the Internet or on a private, corporate TCP/IP internetwork. The Domain Name System (DNS) provides
A method for identifying hosts with friendly names instead of IP addresses
A distributed mechanism for storing and maintaining lists of names and IP addresses of hosts
A method for locating hosts by resolving their names into their associated IP addresses so that network communication can be initiated with the host
How It Works
The DNS namespace is hierarchical in structure, beginning with the root domain, which branches to top-level domains, then second-level domains, and so on to the individual host name.
For example, the fully qualified domain name (FQDN) barney.northwind.microsoft.com can be broken down as follows:
Host name: barney
Third-level domain: northwind (stands for Northwind Traders Ltd., a fictitious Microsoft subsidiary)
Second-level domain: microsoft (Microsoft Corporation)
Top-level domain: com (commercial domain)
The root domain has a null label and is not expressed in the FQDN.
Graphic D-36. Domain Name System (DNS).
The DNS is implemented as a distributed database using name servers located at various points on the Internet. Clients called resolvers can perform name lookups by contacting these name servers, which resolve host names into IP addresses. In Microsoft Windows NT and UNIX BIND name servers, the DNS database of host name to IP address mappings must be created manually by entering resource records for each host that needs to be resolved. In Windows 2000, the new dynamic update can be used to register host names automatically, and zone information can be stored and replicated using Active Directory.
Each name server on the Internet is responsible for a subset of the DNS namespace known as a zone of authority. Each zone of authority can consist of one or more domains and subdomains. The most important name servers on the Internet are the dozen or so root name servers, which are responsible for maintaining the infrastructure of the domain name system. These root name servers are maintained mostly by the Internet Network Information Center (InterNIC) and by U.S. military agencies (because the Internet evolved from the ARPANET project of the U.S. Defense Department in the 1970s).
A name server can function in one of four roles in the DNS:
Primary name server, which contains the master copy of the zone file for the zones it has authority over
Secondary name server, which obtains its zone files using a zone transfer from a master name server
Master name server, which can provide zone information to secondary name servers
Caching-only name server, which does not contain any zone information
NOTE
Although DNS is used mainly for the Internet, large private TCP/IP internetworks can also use DNS internally with their own name servers. The main advantage of doing this is that host names are friendlier than IP addresses. On smaller TCP/IP networks, hosts files can be used instead of DNS, while on Windows NT–based networks, Windows Internet Naming Service (WINS) is often used for NetBIOS name resolution. Windows NT Server has an installable service called the Microsoft DNS Service, which allows Windows NT servers to function as name servers called DNS servers.
The DNS is also an essential part of Active Directory in Windows 2000. Active Directory uses the DNS to resolve domain names into IP addresses. However, it can also use non-DNS naming conventions to locate objects in the directory. These other naming conventions include
The Lightweight Directory Access Protocol (LDAP) naming convention of distinguished names and relative distinguished names (RDNs). This includes LDAP Uniform Resource Locators (URLs).
User principal names for identifying users and groups.
Security Accounts Manager (SAM) account names for user accounts.
Universal Naming Convention (UNC) paths for shared network resources.
See also host name resolution
A hierarchical grouping of Microsoft Windows 2000 domains created by adding one or more child domains to an existing parent domain. Domain trees are used to make a domain’s network resources globally available to users in other domains.
How It Works
In a domain tree, all domains share their resources and security information to act as a single administrative unit. A user who logs on anywhere in a domain tree can access file, printer, and other shared resources anywhere in the tree if he or she has appropriate permissions. A domain tree has only one Active Directory, but each domain controller in a tree maintains only the portion of Active Directory that represents the objects in that particular domain.
Domains in a domain tree are joined using two-way transitive trusts. These trusts enable each domain in the tree to trust the authority of every other domain in the tree for user authentication. This means that when a domain joins a domain tree, it automatically trusts every domain in the tree.
For child domains to be part of a domain tree, they must share a contiguous namespace with the parent domain. The namespace of a Windows 2000 domain is based on the Domain Name System (DNS) naming scheme. For example, in the illustration, the child domains northwind.carpoint.com and adventure.carpoint.com share the same namespace as the parent domain carpoint.com. In this example, carpoint.com is also the name of the root domain—the highest-level parent domain in the tree. The root domain must be created first in a tree.
Graphic D-37. Domain tree.
All domains in a domain tree have their directory information combined into a single directory: Active Directory. Each domain provides a portion of its directory information to an index on the domain controllers. By searching this index, users can locate and access shared resources, applications, and even users anywhere in the domain tree.
NOTE
Two or more domain trees that do not share a contiguous namespace can be combined into a domain forest.
See also domain forest
One of three types of user accounts available on a Microsoft Windows 2000–based network. User accounts enable users to log on to domains or computers and access any resources in the domain for which they have appropriate permissions. This is in contrast to local user accounts, which are used only for logging on to a specific machine (such as a member server) and accessing resources on that machine.
Domain user accounts are created in Active Directory and stored in organizational units (OUs). Domain user account information is replicated to all domain controllers in a domain using directory replication. This replication enables the user to quickly and easily log on from any part of the domain.
You create domain user accounts using the administrative tool called Active Directory Users and Computers, a snap-in for the Microsoft Management Console (MMC). You can create domain user accounts in the default Users OU or in any other OU that you have created in Active Directory.
NOTE
Windows 2000 also includes a number of built-in accounts that simplify the task of administering users on a network. The two built-in user accounts are the Administrator and Guest accounts.
A built-in group on Microsoft Windows NT and Windows 2000 networks. The Domain Users group simplifies administration of users on the network. It is a global group and does not have any preassigned system rights. Its initial membership is empty until ordinary network users are created for the domain. User accounts that are added to this group gain the rights and privileges that are assigned to ordinary users in the network, such as the right to log on over the network. All ordinary users on the network should be members of this group.
NOTE
On Windows 2000–based networks, the Domain Users group is created by default in the Users organizational unit (OU) within Active Directory.
See also built-in group
See MS-DOS
The state of a network when some or all network communications are disrupted. Common reasons for networks being down include
Loose connectors on cables
Breaks or shorts in cables
Failed networking components
Indications that the network might be down include
Users complain that they can’t log on to the network or access certain network resources.
Alarm systems in Simple Network Management Protocol (SNMP) management software start sending administrative alerts or e-mail to administrators.
The uninterruptible power supply (UPS) unit in the wiring closet generates its annoying high-pitched tone.
An uninsulated wire included in shielded cabling that runs the length of some coaxial cabling or shielded twisted-pair (STP) cabling. The drain wire makes contact with the foil sleeve or mesh along the wire. The externally exposed portion of the drain wire should be connected to a secure ground connection. This ensures that the wire is properly grounded and that the shielding in the wire operates effectively. It also helps to maintain the two ends of the wire at the same voltage with respect to ground. If voltage differences form between the ends of a network cable, they can lead to a sudden voltage surge or discharge that can damage attached networking devices.
A Microsoft Windows 95 and Windows 98 utility for compressing file allocation table (FAT) volumes. You can use DriveSpace to free up disk space for users on workstations or for network shares on servers. DriveSpace uses disk compression techniques to pack more information onto a disk than is normally possible with uncompressed files.
How It Works
DriveSpace creates a read-only, hidden system file called a compressed volume file (CVF). This file, typically called drvspace.000, contains all the files and folders on the original uncompressed volume. A driver called drvspace.bin in the root of the active partition is used at boot time to mount the compressed drive.
Windows 95 OSR2 (OEM Service Release 2) and Windows 98 have an enhanced version of DriveSpace called DriveSpace3 that supports CVFs of up to 2 GB in size. To compress a drive, type drvspace at the command prompt. In the DriveSpace 3 dialog box shown on the screen, highlight the volume you want to compress. You have several ways to compress data with DriveSpace 3.
Graphic D-38. Disk Compression Settings dialog box.
Another name for a wall plate. For example, a network administrator might say, “This room has 24 drops, and 6 are still available.” This means that there are 24 wall plate connections on the walls of the room, and 18 of them have drop cables attached to them to connect them to computers in the room. The other end of the drops usually terminates at a patch panel in the wiring closet. Another name for a drop is a “LAN Drop.”
In standard Ethernet networks, a cable connecting a computer’s network interface card (NIC) to a transceiver attached to a thicknet cable. A drop cable is also called a “transceiver cable.”
More generally, a drop cable is any short cable connecting a computer’s NIC to a wall plate. Drop cables allow computers to be easily disconnected and reconnected from the network so that you can move them around in the room. Drop cables are generally needed because horizontal cabling connecting patch panels in wiring closets terminates at wall plates in the work areas, but computers in the work areas are distributed throughout the entire room. In a more permanent networking configuration, wall plates might be located on floors and very short drop cables might be used to connect the computers to the network.
A Microsoft Windows utility that intercepts software faults and provides the user with information on which software faulted and why.
In earlier versions of Windows, this information was terse and cryptic, but it was greatly expanded and reorganized in the version of Dr. Watson included with Windows 98, as shown in the screen capture. However, this information is usually not helpful to the person running the software. Dr. Watson is primarily of interest to the providers of the software to determine what caused the software to crash. A piece of software that frequently generates Dr. Watson messages can be considered buggy, and you should contact your software vendor for a fix or a replacement.
Graphic D-39. Watson.
Stands for Digital Signal Zero, a standard digital transmission rate for digital telecommunications. DS0 defines a transmission rate of 64 Kbps and can carry either a single voice channel or data.
Telecommunication carriers transmit digital signals in multiples of DS0 called DS1, DS2, and so on. These multiples differ depending on whether you are dealing with the T-carrier system of North America or the E-carrier system of Europe and other continents. The following table lists the common DS-series transmission rates and their T-series or E-series equivalents (when defined). For example, you can see that a T1 data transmission is equivalent to 24 DS0 transmissions multiplexed together and can transmit data at a rate of 1.544 Mbps.
DS-Series Transmission Rates
| DS Type | Multiple of DS0 | Data Rate | T-Series | E-Series |
| DS0 | 1 | 64 Kbps | N/A | N/A |
| DS1 | 24 | 1.544 Mbps | T1 | N/A |
| N/A | 32 | 2.048 Mbps | N/A | E1 |
| DS1C | 48 | 3.152 Mbps | N/A | N/A |
| DS2 | 96 | 6.312 Mbps | T2 | N/A |
| N/A | 128 | 8.448 Mbps | N/A | E2 |
| N/A | 512 | 34.368 Mbps | N/A | E3 |
| DS3 | 672 | 44.736 Mbps | T3 | N/A |
| N/A | 2048 | 139.264 Mbps | N/A | E4 |
| DS4 | 4032 | 274.176 Mbps | N/A | N/A |
| N/A | 8192 | 565.148 Mbps | N/A | E5 |
See Digital Subscriber Line (DSL)
See Directory Service Markup Language (DSML)
See Directory Service Manager for NetWare (DSMN)
See data source name (DSN)
See Data Service Unit (DSU)
See data terminal equipment (DTE)
See Dual Tone Multiple Frequency (DTMF)
A computer that can boot one of several operating systems by means of a startup menu. An example is a machine on which Windows 98 and then Windows NT has been installed. The user can utilize the Windows NT boot loader menu to choose which operating system to run at startup.
Windows NT supports dual booting with other operating systems, but this is neither recommended nor supported by Microsoft. Dual boot systems are typically used in hobbyist and test networks in which a variety of operating systems are used to test different networking functions, or when the number of available machines is fewer than needed to perform the tasks.
NOTE
The Windows NT boot loader menu can include up to 10 operating systems.
The audio signaling method used by Touch-Tone phones. Microsoft’s Telephony Application Programming Interface (TAPI) can recognize and interpret Dual Tone Multiple Frequency (DTMF) signals, allowing Microsoft Windows–based applications to integrate with telephony. Some networking vendors also supply hardware devices called DTMF/ASCII converters, which convert DTMF tones directly into different ASCII characters, which can then be fed as input into a program that routes telephone calls accordingly.
How It Works
Each DTMF signal generated by pressing a key on a Touch-Tone phone generates two simultaneous audible tones of different frequencies, as shown in the following table. DTMF was developed by AT&T; the term Touch-Tone was originally an AT&T trademark.
Frequencies of DTMF Signals
| 697 Hz | 770 Hz | 852 Hz | 941 Hz | |
| 1209 Hz | 1 | 4 | 7 | * |
| 1336 Hz | 2 | 5 | 8 | 0 |
| 1477 Hz | 3 | 6 | 9 | # |
A telecommunications term referring to bidirectional communication. In full-duplex communication, both stations send and receive at the same time, and usually two communication channels are required. However, you can also achieve full-duplex communication using a multiplexing technique whereby signals traveling in different directions are placed into different time slots. The disadvantage of this technique is that it cuts the overall possible transmission speed by half.
In half-duplex communication, only one station can transmit at any given time while the other station receives the transmission. The opposite of duplex communication is simplex communication, which can occur only in one direction.
See dense wavelength division multiplexing (DWDM)
In Microsoft Windows 2000, a new kind of disk management technology for hard disks. Dynamic disks are different from basic disks, which are disk systems that function similarly to earlier versions of Windows and are also supported by Windows 2000. You create and manage dynamic disks using the Disk Management portion of the Computer Management administrative tool.
How It Works
Dynamic disks use a Windows 2000–based disk management technology called dynamic storage, which creates a single partition for the entire physical disk. This dynamic disk can then be divided into a number of dynamic volumes, each consisting of one dynamic disk or portions of one or more dynamic disks. In other words, dynamic volumes can span several dynamic disks or several portions of a single dynamic disk. Dynamic disks cannot contain the partitions and logical drives that can be created on basic disks. You can create dynamic disks only on Windows 2000 machines; they cannot be accessed locally by MS-DOS and legacy Windows operating systems in a dual-boot configuration.
The main advantage of using dynamic disks is that you can resize and reconfigure them without rebooting the system. You can thus create and delete simple volumes, spanned volumes, striped volumes, mirrored volumes, and RAID-5 volumes on machines running Windows 2000 without needing to reboot the machine.
NOTE
You can use Disk Management to revert a dynamic disk to a basic disk, but you must first remove all volumes from the dynamic disk. Once the disk is reverted, you can create only partitions and logical drives on it.
See also basic disk
A standard Internet protocol that enables the dynamic configuration of hosts on an Internet Protocol (IP) internetwork. Dynamic Host Configuration Protocol (DHCP) is an extension of the bootstrap protocol (BOOTP).
How It Works
DHCP is a client-server protocol that uses DHCP servers and DHCP clients. A DHCP server is a machine that runs a service that can lease out IP addresses and other TCP/IP information to any client that requests them. For example, on Microsoft Windows NT or Windows 2000 servers you can install the Microsoft DHCP Server service to perform this function. The DHCP server typically has a pool of IP addresses that it is allowed to distribute to clients, and these clients lease an IP address from the pool for a specific period of time, usually several days. Once the lease is ready to expire, the client contacts the server to arrange for renewal.
DHCP clients are client machines that run special DHCP client software enabling them to communicate with DHCP servers. All versions of Windows include DHCP client software, which is installed when the TCP/IP protocol stack is installed on the machine.
DHCP clients obtain a DHCP lease for an IP address, a subnet mask, and various DHCP options from DHCP servers in a four-step process:
DHCPDISCOVER: The client broadcasts a request for a DHCP server.
DHCPOFFER: DHCP servers on the network offer an address to the client.
DHCPREQUEST: The client broadcasts a request to lease an address from one of the offering DHCP servers.
DHCPACK: The DHCP server that the client responds to acknowledges the client, assigns it any configured DHCP options, and updates its DHCP database. The client then initializes and binds its TCP/IP protocol stack and can begin network communication.
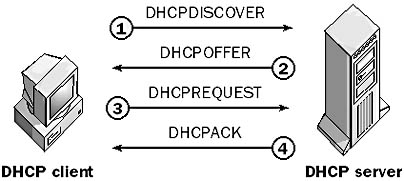
Graphic D-40. Dynamic Host Configuration Protocol (DHCP).
DHCP lease renewal consists only of steps 3 and 4, and renewal requests are made when 50 percent of the DHCP lease time has expired.
TIP
When you implement DHCP on a network, you should consider the following:
DHCP servers do not share their database of leased IP addresses, so if your network has more than one DHCP server, be sure that their DHCP scopes do not overlap.
Assign DHCP options to the DHCP server if clients need them.
Assign static IP addresses to non-DHCP clients, and exclude these addresses from the scope on the DHCP server if necessary.
Assign static IP addresses to all servers on your network or assign them DHCP client reservations on the DHCP server to ensure that they always lease the same IP address.
Configure DHCP relay agents if one DHCP server must serve hosts on several subnets.
A proposed World Wide Web Consortium (W3C) standard developed by Microsoft for creating interactive multimedia Web content. You can use Dynamic HTML to make Web pages look and behave more like typical desktop applications. Dynamic HTML supports features such as
Document Object Model (DOM), a standard whereby every element of a Web page is exposed for scripting. Each element on a Hypertext Markup Language (HTML) page can function as an object that can be modified using scripts and other programs. For example, Dynamic HTML can make the appearance of an object on a Web page change during an onmouseover or onclick event.
Cascading style sheet (CSS) positioning, which allows HTML content developers to control the style and layout of objects on a Web page using style sheets. These style sheets can then be cascaded to define different levels of precedence.
Dynamic Content and Dynamic Styles, which HTML content developers can use to dynamically change the content or style of every HTML element on a Web page based on mouse events or other forms of user interaction.
Data Binding, which integrates data with HTML elements. For example, table rows can be automatically generated from data records and data-bound fields.
A file containing executable routines that can be loaded on demand by an application. Dynamic-link libraries (DLLs) offer the advantage of providing standard services for many different calling applications, and they simplify and modularize application development by providing component-based services. DLLs are loaded into RAM only when needed by the calling application, which reduces the memory requirements of large applications. DLLs are files that have the extension .dll.
A feature of Microsoft Proxy Server version 2 that enables Proxy Server to do the following:
Determine dynamically whether to accept a packet from the Internet while minimizing the number of exposed ports in both directions and the length of time the port is open to the Internet
By default, drop all packets on an external interface
How It Works
Dynamic packet filtering involves two Proxy Server components:
The Packet Filter Driver, which talks directly to the external network interface
The Packet Filter Manager, which provides the high-level interface for interaction between Proxy Server services and the driver
In a typical scenario, a client with the Winsock Proxy client might attempt to connect to an Internet server using Telnet. The Winsock Proxy client intercepts the Telnet connection request and remotes the request to the Winsock Proxy server, which verifies that the client has proper Microsoft Windows NT permissions to use Telnet to access servers on the Internet and opens a local socket. The Winsock Proxy server then informs the Packet Filter Manager that an outbound connection request from the socket to a remote Telnet service has been approved, and the Packet Filter Manager orders the Packet Filter Driver to open the socket and the Winsock Proxy server to start a Telnet session on behalf of the client. When the Winsock Proxy determines that the client has closed the Telnet session, it tells the Packet Filter Manager to close the socket and thus blocks any further packets from the remote system.
A connector in Microsoft Exchange Server. You can use the Dynamic RAS Connector when a permanent network connection between two Exchange sites is unavailable. The Dynamic RAS Connector uses the Microsoft Windows NT Remote Access Service (RAS) to connect two sites.
The Dynamic RAS Connector is typically used in an Exchange implementation in one of the following ways:
To provide a backup messaging connectivity path between two remote Exchange sites in case their dedicated connection goes down. For example, two sites might have a T1 line connecting them and use Site Connector to establish messaging between them. If the T1 line goes down, the Dynamic RAS Connector can kick in and use a modem to provide temporary messaging services between the sites.
As an option for connecting low-traffic branch office sites to the main headquarters site of an Exchange organization.
A routing mechanism handled by a routing protocol, such as Routing Information Protocol (RIP) or Open Shortest Path First (OSPF) Protocol, that dynamically exchanges routing information among routers on an internetwork. Routers that use this method are called dynamic routers.
How It Works
For a dynamic router to function, a routing protocol must be installed on each router in the internetwork. The routing table of one router is manually seeded with routing information for the first hop, and then the routing protocol takes over and dynamically builds the routing table for each router. Routers periodically exchange their routing information so that if the internetwork is reconfigured or a router goes down, the routing tables of each router are modified accordingly. Hosts on a network need only be configured so that their default gateway address matches the IP address of the local router interface.
Dynamic routers are much simpler to administer than static routers, but they are sometimes less secure because routing protocol information can be spoofed. If the network is reconfigured or a router goes down, it takes time for this information to propagate between the various routers on the network. Routing protocols also create additional network traffic, and different routing protocols offer their own advantages and disadvantages.
NOTE
You can configure a multihomed Microsoft Windows NT server as a dynamic RIP router by selecting Enable IP Forwarding on the Routing tab of the TCP/IP property sheet, and then using the Services tab of the Network property sheet to add the RIP for Internet Protocol (IP) service to the server. Another example of a dynamic router is a multihomed computer running Windows NT Server and Microsoft’s Routing and Remote Access Service (RRAS) with either RIP or OSPF configured.
TIP
Dynamic routers cannot exchange information with static routers. To configure static and dynamic routers to work together on the same internetwork, you must add manual routes to the routing tables of both types of routers.
See also router, routing table, static routing
A variation of the Domain Name System (DNS) defined in Request for Comments (RFC) 2136 and supported by Active Directory in Microsoft Windows 2000. The dynamic update protocol provides support for dynamic updates of zone file information between domain controllers. Instead of using primary and secondary zones, Active Directory reuses zones.
How It Works
Dynamic update lies at the heart of Active Directory because domain names in Windows 2000 are also DNS names. For example, northwind.microsoft.com can be both a legal DNS name and the name of a Windows 2000 domain.
Ordinary DNS must be administered manually. Administrators must perform all changes to the DNS database or zone files manually. Zone files are propagated between DNS servers by zone transfers, which occur periodically.
Dynamic update lets computers running Windows 2000 with dynamically assigned IP addresses register both their host name and IP address information in the DNS database when they initialize on the network. Dynamic update can thus integrate the DNS and Dynamic Host Configuration Protocol (DHCP) services. Dynamic update also supports new types of server-to-server messages that allow individual resource records or sets of records to be added or deleted in a server’s zone.
When DNS is integrated with Active Directory for dynamic update, administrators must enable and manage the following zones:
The DNS root zone
DNS forward lookup zones
DNS reverse lookup zones
Dynamic update is similar to ordinary DNS in that zone update operations occur using primary or master servers only. Dynamic update, however, allows primary servers to receive updates initialed by a specified list of “authorized servers,” which can include secondary zone servers, domain controllers, and other servers that perform name registration services, such as Windows Internet Name Service (WINS) or DHCP servers.
NOTE
You can use the DNS Manager snap-in for the Microsoft Management Console (MMC) to enable Active Directory integration on an existing DNS server. The zone file information will be written into Active Directory.
In Microsoft Windows 2000, any volume created using the Disk Management portion of the Computer Management administrative tool. You can create dynamic volumes only on dynamic disks. Types of dynamic volumes include the following:
Simple volumes
Spanned volumes
Striped volumes
Mirrored volumes
RAID-5 volumes
See also basic volume